Abstract
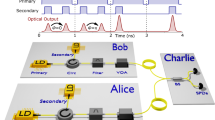
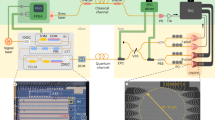
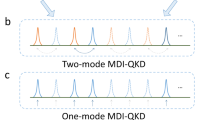
Security in quantum cryptography1,2 is continuously challenged by inventive attacks3,4,5,6,7 targeting the real components of a cryptographic set-up, and duly restored by new countermeasures8,9,10 to foil them. Owing to their high sensitivity and complex design, detectors are the most frequently attacked components. It was recently shown that two-photon interference11 from independent light sources can be used to remove any vulnerability from detectors12,13. This new form of detection-safe quantum key distribution (QKD), termed measurement-device-independent13 (MDI), has been experimentally demonstrated13,14,15,16,17,18,19 but with modest key rates. Here, we introduce a new pulsed laser seeding technique to obtain high-visibility interference from gain-switched lasers and thereby perform MDI-QKD with unprecedented key rates in excess of 1 megabit per second in the finite-size regime. This represents a two to six orders of magnitude improvement over existing implementations and supports the new scheme as a practical resource for secure quantum communications.
This is a preview of subscription content, access via your institution
Access options
Subscribe to this journal
Receive 12 print issues and online access
$209.00 per year
only $17.42 per issue
Buy this article
- Purchase on Springer Link
- Instant access to full article PDF
Prices may be subject to local taxes which are calculated during checkout



Similar content being viewed by others
References
Gisin, N., Ribordy, G., Tittel, W. & Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 74, 145–195 (2002).
Scarani, V. et al. The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301–1350 (2009).
Gerhardt, I. et al. Full-field implementation of a perfect eavesdropper on a quantum cryptography system. Nature Commun. 2, 349 (2011).
Lydersen, L. et al. Hacking commercial quantum cryptography systems by tailored bright illumination. Nature Photon. 4, 686–689 (2010).
Xu, F., Qi, B. & Lo, H.-K. Experimental demonstration of phase-remapping attack in a practical quantum key distribution system. New J. Phys. 12, 113026 (2010).
Zhao, Y., Fung, C.-H. F., Qi, B., Chen, C. & Lo, H.-K. Quantum hacking: experimental demonstration of time-shift attack against practical quantum-key-distribution systems. Phys. Rev. A 78, 042333 (2008).
Qi, B., Fung, C.-H. F., Lo, H.-L. & Ma, X. Time-shift attack in practical quantum cryptosystems. Quantum Inf. Comput. 7, 73–82 (2007).
Sasaki, T., Yamamoto, Y. & Koashi, M. Practical quantum key distribution protocol without monitoring signal disturbance. Nature 509, 475–478 (2014).
Yuan, Z. L., Dynes, J. F. & Shields, A. J. Avoiding the blinding attack in QKD. Nature Photon. 4, 800–801 (2010).
Fung, C.-H. F., Tamaki, K., Qi, B., Lo, H.-K. & Ma, X. Security proof of quantum key distribution with detection efficiency mismatch. Quantum Inf. Comput. 9, 131–165 (2009).
Hong, C. K., Ou, Z. Y. & Mandel, L. Measurement of subpicosecond time intervals between two photons by interference. Phys. Rev. Lett. 59, 2044–2046 (1987).
Braunstein, S. L. & Pirandola, S. Side-channel-free quantum key distribution. Phys. Rev. Lett. 108, 130502 (2012).
Lo, H.-K., Curty, M. & Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108, 130503 (2012).
Rubenok, A., Slater, J. A., Chan, P., Lucio-Martinez, I. & Tittel, W. Real-world two-photon interference and proof-of-principle quantum key distribution immune to detector attacks. Phys. Rev. Lett. 111, 130501 (2013).
Liu, Y. et al. Experimental measurement-device-independent quantum key distribution. Phys. Rev. Lett. 111, 130502 (2013).
Ferreira da Silva, T., et al. Proof-of-principle demonstration of measurement-device-independent quantum key distribution using polarization qubits. Phys. Rev. A 88, 052303 (2013).
Tang, Z. et al. Experimental demonstration of polarization encoding measurement-device-independent quantum key distribution. Phys. Rev. Lett. 112, 190503 (2014).
Tang, Y.-L. et al. Measurement-device-independent quantum key distribution over 200 km. Phys. Rev. Lett. 113, 190501 (2014).
Valivarthi, R. et al. Measurement-device-independent quantum key distribution: from idea towards application. J. Mod. Optic. 62, 1141–1150 (2015).
Scarani, V. & Kurtsiefer, C. The black paper of quantum cryptography: real implementation problems. Theor. Comput. Sci. 560, 27–32 (2014).
Fröhlich, B. et al. A quantum access network. Nature 501, 69–72 (2013).
Pirandola, S. et al. High-rate measurement-device-independent quantum cryptography. Nature Photon. 9, 397–402 (2015).
Comandar, L. C. et al. Room temperature single-photon detectors for high bit rate quantum key distribution. Appl. Phys. Lett. 104, 021101 (2014).
Lo, H.-K. & Preskill, J. Security of quantum key distribution using weak coherent states with nonrandom phases. Quantum Inf. Comput. 8, 431–458 (2007).
Yuan, Z. L. et al. Robust random number generation using steady-state emission of gain-switched laser diodes. Appl. Phys. Lett. 104, 261112 (2014).
Yuan, Z. L. et al. Interference of short optical pulses from independent gain-switched laser diodes for quantum secure communications. Phys. Rev. Appl. 2, 064006 (2014).
Rarity, J. G., Tapster, P. R. & Loudon, R. Non-classical interference between independent sources. J. Opt. B 7, S171–S175 (2005).
Zhou, Y.-H., Yu, Z.-W. & Wang, X.-B. Making the decoy-state measurement-device-independent quantum key distribution practically useful. Preprint at http://arxiv.org/abs/1502.01262 (2015).
Choi, I. et al. Field trial of a quantum secured 10 Gb/s DWDM transmission system over a single installed fiber. Opt. Express 22, 23121–23128 (2014).
Ma, X., Fung, C. H. F. & Razavi, M. Statistical fluctuation analysis for measurement-device-independent quantum key distribution. Phys. Rev. A 86, 052305 (2012).
Curty, M. et al. Finite-key analysis for measurement-device-independent quantum key distribution. Nature Commun. 5, 3732 (2014).
Xu, F., Curty, M., Qi, B. & Lo, H.-K. Practical aspects of measurement-device-independent quantum key distribution. New J. Phys. 15, 113007 (2013).
Comandar, L. C. et al. Gigahertz-gated InGaAs/InP single-photon detector with detection efficiency exceeding 55% at 1550 nm. J. App. Phys. 117, 083109 (2015).
Acknowledgements
The authors acknowledge useful discussions with M. Curty. L.C.C. acknowledges personal support via the Engineering and Physical Sciences Research Council funded Centre for Doctoral Training in Photonic Systems Development and Toshiba Research Europe.
Author information
Authors and Affiliations
Contributions
Measurements and calculations were performed by L.C.C. and M.L., respectively. The system was readied by B.F., J.F.D., A.W.S., L.C.C. and S.W.-B.T. Z.L.Y. and A.J.S. conceived the experiment and guided the work. L.C.C. and M.L. wrote the manuscript with contributions from the other authors. All authors discussed experiments, results and the interpretation of results.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing financial interests.
Supplementary information
Supplementary information
Supplementary information (PDF 1060 kb)
Rights and permissions
About this article
Cite this article
Comandar, L., Lucamarini, M., Fröhlich, B. et al. Quantum key distribution without detector vulnerabilities using optically seeded lasers. Nature Photon 10, 312–315 (2016). https://doi.org/10.1038/nphoton.2016.50
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1038/nphoton.2016.50