Abstract
Quantum mechanics offers the possibility of unconditionally secure communication between multiple remote parties. Security proofs for such protocols typically rely on bounding the capacity of the quantum channel in use. In a similar manner, Cramér-Rao bounds in quantum metrology place limits on how much information can be extracted from a given quantum state about some unknown parameters of interest. In this work we establish a connection between these two areas. We first demonstrate a three-party sensing protocol, where the attainable precision is dependent on how many parties work together. This protocol is then mapped to a secure access protocol, where only by working together can the parties gain access to some high security asset. Finally, we map the same task to a communication protocol where we demonstrate that a higher mutual information can be achieved when the parties work collaboratively compared to any party working in isolation.
Similar content being viewed by others
Introduction
Non-classical correlations have been shown to enable a range of quantum-enhanced tasks1,2. One such example is quantum metrology, which utilises quantum resources to achieve a better measurement sensitivity than is classically possible. This could be in the form of quantum probe states3,4,5,6,7,8, or quantum-enhanced measurements9,10,11,12. Indeed, the connection between entanglement and quantum enhanced sensing has been widely studied13,14,15,16,17,18. More recently, it has been shown that quantum metrology tasks can be used to witness steering19. The connection between Bell correlations20 and quantum sensing has also been investigated21,22.
Quantum resources also offer the promise of unconditionally secure communication. This can be done through quantum key distribution (QKD), which involves the sharing of a secret key between two parties in a manner such that no possible malicious evesdropper can access the key. The first such protocol was introduced by Bennett and Brassard in 1984, where information was encoded in the polarisation degree of freedom of photons23. An entanglement-based QKD protocol was later proposed by Artur Ekert in 199124. Over the subsequent decades, there has been much progress towards QKD networks in various scenarios25,26,27,28,29,30,31,32. A related area, which also uses the laws of quantum mechanics for its security, is that of secret sharing. This involves the sharing of either classical or quantum information between a number of trusted parties. There has been a great deal of work on the secret sharing of both classical and quantum information using both discrete variable (DV)33,34,35,36,37 and continuous variable (CV) systems38,39,40,41,42,43,44,45,46. Secret sharing can be used to ensure that only trusted parties gain access to highly confidential information such as bank accounts or missile launch codes.
In this work we design and implement a variant of conventional secret sharing protocols, allowing only certain sets of trusted parties to access confidential information. We use techniques from quantum metrology to bound the information which can be attained by the untrusted parties. Our protocol involves distributing a quantum state with unknown displacements among three parties. When considering quantum sensing, we will treat the unknown displacements as parameters to be estimated and when considering quantum communication, we will treat the unknown displacements as the secret information encoded in the quantum state. This enables us to draw a direct connection between these two tasks.
The layout of this paper is as follows. In ‘Preliminary material’, we introduce the preliminary material needed. In ‘Theoretical results’ and ‘Experimental results’, we present our theoretical and experimental results respectively. Finally, we conclude the paper in ‘Discussion’.
Results
Preliminary material
A CV quantum state can be described by observables in an infinite dimensional Hilbert space which have a continuous spectrum of possible eigenvalues47. Gaussian states are those with Gaussian measurement statistics. In our experiments, the variables of interest are the amplitude and phase quadratures of the electromagnetic field, denoted \(\hat{x}\) and \(\hat{p}\) respectively. These quadrature variables are defined in terms of the creation and annihilation operators, denoted \(\hat{a}\) and \({\hat{a}}^{{\dagger} }\) respectively, as \(\hat{x}=\hat{a}+{\hat{a}}^{{\dagger} }\) and \(\hat{p}=-{{{\rm{i}}}}(\hat{a}-{\hat{a}}^{{\dagger} })\). As the creation and annihilation operators satisfy \([\hat{a},{\hat{a}}^{{\dagger} }]=1\), the \(\hat{x}\) and \(\hat{p}\) quadrature operators satisfy \([\hat{x},\hat{p}]=2{{{\rm{i}}}}\). From the uncertainty principle48,49,50,51, the variances in both quadratures must satisfy
where \(\Delta {\hat{x}}^{2}\) is the variance in measuring the \(\hat{x}\) quadrature and similarly for \(\Delta {\hat{p}}^{2}\).
There do exist non-classical Gaussian states which can violate this uncertainty principle in certain settings. For example, by mixing two squeezed vacuum states on a 50:50 beam splitter one can create a two mode squeezed vacuum (TMSV) state. The two modes of this state are correlated in the \(\hat{x}\) quadrature and anti-correlated in the \(\hat{p}\) quadrature. With sufficiently high squeezing, low antisqueezing, and low loss, this state can be entangled or steerable in the \(\hat{x}\) and \(\hat{p}\) quadratures. With such states, it is possible to achieve a measurement sensitivity better than what is allowed by Eq. (1), see e.g. ref. 52. The non-classical correlations of the TMSV enable uniquely quantum mechanical tasks such as quantum teleportation53,54, quantum illumination55,56, quantum enhanced sensing52,57,58,59,60 and QKD61,62 to be carried out.
Theoretical results
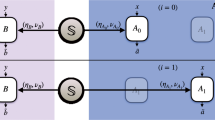
We consider the set-up shown in Fig. 1. The classical information that the dealer wishes to share with the three parties are displacements in the \(\hat{x}\) and \(\hat{p}\) quadratures, denoted as αx,i and αp,i, respectively (The rational behind using subscript i will become evident later in the manuscript). In an ideal experimental implementation of our protocol, the dealer prepares a TMSV state and introduces displacements on one arm. After mixing one mode of the TMSV on a second 50:50 beamsplitter with an ancilla vacuum state, the three parties in Fig. 1 share a continuous variable state with the mean vector \({\left(\begin{array}{cccccc}0&0&0&0&{\alpha }_{x,i}&{\alpha }_{p,i}\end{array}\right)}^{T}\) where the modes are ordered as \({\left(\begin{array}{cccccc}\langle {\hat{x}}_{C}\rangle &\langle {\hat{p}}_{C}\rangle &\langle {\hat{x}}_{B}\rangle &\langle {\hat{p}}_{B}\rangle &\langle {\hat{x}}_{A}\rangle &\langle {\hat{p}}_{A}\rangle \end{array}\right)}^{T}\), where \(\langle {\hat{i}}_{j}\rangle\) denotes the expectation value of the \(\hat{i}\) quadrature for party j. The corresponding covariance matrix is
where r is the squeezing parameter. We now wish to investigate various quantum information tasks which can be achieved with this state and the connection between these tasks.
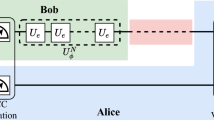
a Conceptual schematic of the experiment. Highly sensitive information, depicted here as access to a bank account, is shared among three parties in such a manner that only trusted groups of parties can access the information. b Experimental set-up. The dealer (e.g. the banker in a)) mixes two squeezed states on a 50:50 beamsplitter to generate a two-mode squeezed vacuum (TMSV) state. One mode is split on a second 50:50 beamsplitter and these modes are sent to parties B and C. The dealer implements a displacement (αx,i, αp,i) in the \(\hat{x}\) and \(\hat{p}\) quadratures on the final arm of their state before this mode is sent to party A. Depending on whether the parties work cooperatively or independently differing amounts of information can be extracted about the unknown displacements (αx,i, αp,i). AM and PM represent amplitude and phase modulators respectively.
Multiparameter estimation—simultaneous estimation of displacements in both quadratures
We first compute the theoretical limits on how precisely the displacements shown in Fig. 1 can be simultaneously estimated. This is done for one party working alone, parties working in pairs, and all three parties working together. For a single party working alone, we shall use the Holevo Cramér-Rao bound (HCRB) to evaluate the precision which can be achieved. This is done as the HCRB provides the ultimate limit on the variance which can be achieved in multiparameter estimation63,64. In general, the HCRB may require an entangling collective measurement on infinitely many copies of the probe state to be saturated65,66,67,68, suggesting that other Cramér-Rao bounds may be more experimentally relevant69,70,71. However, in the specific case of estimating Gaussian displacements, the HCRB can be saturated by linear measurements64. When considering two and three parties working together, we shall evaluate the precision attainable by a specific measurement strategy. This is done to allow us to compare the experimentally attained two and three party precisions to the ultimate theoretical limits on the precision attainable by a single party.
The average mean squared error (MSE) that the party or parties can achieve when estimating αx,i is given by
where we use a tilde to denote the estimated value and MSEp is defined similarly. When m parties work together, we will denote the average MSE with which αx,i and αp,i can be measured as \({v}_{{\alpha }_{x},m}\) and \({v}_{{\alpha }_{p},m}\) respectively. Clearly we have \({v}_{{\alpha }_{x},1}\ge {v}_{{\alpha }_{x},2}\ge {v}_{{\alpha }_{x},3}\).
One party MSE
From Fig. 1, it is evident that only party A will be able to access any information about the unknown displacements when working in isolation. Without any information from the other two parties, party A will receive a displaced thermal state, obtained by tracing out the first and second modes of the shared state in Eq. (2). In the ideal case, party A obtains a thermal state with variance \(\cosh (2r)\) in both quadratures. More generally, we may have a slight asymmetry between the two quadratures, and so we write the covariance matrix of the state accessible by party A as
where ni characterises the thermal variance. If n1 = n2, then this quantity represents the mean thermal photon number. Note that without loss of generality we can assume that v1 ≥ v2. In the methods section, we show that, for this state, the HCRB for estimating the amplitude and phase displacements simultaneously is
Note that this MSE is normalised for the number of probe states used. In the scenario shown in Fig. 1, this represents the smallest possible average sum of the MSE that party A can attain using an unbiased estimator.
Two party MSE
When considering two parties working together, we will not use the HCRB to bound the MSE. Rather, we shall directly compute the MSE attainable when using homodyne detection as this is what was implemented in our experiment. Let us consider the ideal case, with no loss or thermal noise. Note that when fitting to experimental data later in the manuscript we take such imperfections into account. In this scenario, parties A and B (also parties A and C) share the following covariance matrix
Interestingly, by recombining the measurement results of parties A and B (scaling the measurement results of party B by an optimised factor), it is possible to always achieve a MSE of \({v}_{{\alpha }_{x},2}={v}_{{\alpha }_{p},2}=1\), regardless of the squeezing level. In this case, the estimator used for the unknown Gaussian displacement is
where we use xj to denote the \(\hat{x}\) quadrature measurement results for party j and gB is a constant chosen to minimise the MSE. As gB depends on the experimental parameters, such as r, it must be optimised for every data point. Quantities for the \(\hat{p}\) quadrature are similarly defined.
For a fair comparison with the single party case, in the two party case we measure each quadrature with half of the total states, which increases the MSE by a factor of 2, giving
In any experimental implementation with imperfections, the variance achieved by any two parties can only be larger than this.
Three party MSE
As before, we consider the ideal case, with no loss or thermal noise. In this scenario, if all three parties measure the same quadrature, parties B and C can recombine their results, scaled by a factor \(\sqrt{2}\), so that all three parties effectively share an ideal two mode squeezed vacuum state. Hence, in this case, the estimator that is used is
where gBC is a constant optimised to minimise the MSE, and a similar estimator is used for αp. Note that when there are no experimental imperfections, the optimal value of gBC is \({g}_{BC}=\tanh (2r)\)72. However, with experimental imperfections gBC must be optimised for every data point. Using this information, it is easy to calculate that in the ideal case all three parties can achieve a MSE of
whic goes to 0 in the limit of infinite squeezing. A comparison of the MSE which can be attained by the different combinations of parties is shown in Fig. 2.
Secure access protocol
We are now in a position to introduce our secure access protocol. For this, we draw a comparison with existing quantum secret sharing protocols. Note that we are considering the sharing of classical information using quantum states, as opposed to sharing the quantum state itself. In conventional (k, n) secret sharing, the dealer encodes information in such a way that any k parties, out of the total n parties, can work together to reconstruct the information encoded by the dealer. The remaining n − k parties cannot access any information. In practice, however, such perfect secret sharing is hampered by experimental imperfections and the finite entanglement available. We consider the protocol secure, only if the groups of k parties acquire more information than the groups of n − k parties. Note that we can also consider approximate secret sharing, where k parties acquire some approximate information about the secret, as do the remaining n − k parties73,74.
Our protocol differs slightly from existing protocols. In the ith round of the protocol the dealer implements displacements αi = (αx,i, αp,i). In each round the parties, either working together or independently, estimate either αx,i or αp,i. As different measurements are needed to acquire information about αx,i and αp,i, the parties must announce at the end of the entire protocol which parameter they were trying to measure in each round, αx,i or αp,i. Any rounds in which the parties measured different parameters can then be discarded. We use (αx, αp) to denote the two-dimensional vector of αx,i and αp,i values that are not discarded. After the reconciliation step, if we have Mx remaining rounds of data in which αx,i was measured by all parties, the average MSE that the parties achieve is given by
and MSEp is defined similarly.
As discussed in the previous section, given a certain input state, the dealer can use bounds from quantum metrology to place limits on how small \({v}_{{\alpha }_{x},m}\) and \({v}_{{\alpha }_{p},m}\) can be. This allows the dealer to define a threshold average MSE vT, below which the protocol is declared secure. In our setting, if we wish to ensure that no single party can access the trusted information, we shall refer to a protocol as δ secure if
where Pr(X) is the probability of the event X occurring. Intuitively, δ represents the likelihood of any single party obtaining an average MSE below a certain threshold, or equivalently acquiring an amount of information about the displacements above a certain threshold. Although the MSE attainable by any party working independently (Eq. (5)) is larger than when the parties work together (Eqs. (8), (10)), this is only true statistically, i.e. on any given experimental run there is some finite probability that a party working alone predicts a value for α which is very close to the true value. Hence, in any practical setting with finite statistics, security can only be guaranteed up to some probability, Eq. (12). The MSE values attained follow a scaled χ2 distribution. When using N probe states to measure each quadrature, if the mean MSE is denoted μM, then the probability density of MSE’s which will be attained is given by
see ‘Methods’ section for the derivation.
Given the quantum state generated by the dealer, we can use the above equation to compute \(\Pr ({v}_{{\alpha }_{x},1}+{v}_{{\alpha }_{p},1}\le {v}_{{{{\rm{T}}}}})\) for all possible vT. From this definition alone, we can trivially choose vT = 0 to ensure that maximum security is achieved. However, in this case the protocol will never succeed, i.e. although any individual party cannot achieve an MSE of 0, with any practical resources, all of the parties working together also cannot achieve an MSE of 0. Thus, it is necessary to also define the success rate as
A good protocol should minimise δ and maximise Ps,2(3).
Attainable mutual information
Finally, let us consider how to quantify, the amount of classical information that the dealer can share with these three parties. Assume the dealer chooses the displacements α from a Gaussian distribution with variance Vdist. The parties involved in the protocol then attempt to estimate αx,i and αp,i as well as they possibly can. Averaging over all (αx, αp) allows the correlation matrix, between the dealer and any number of parties to be constructed as
where \({\sigma }_{i,j}=\langle {\tilde{\alpha }}_{i}{\tilde{\alpha }}_{j}\rangle -\langle {\tilde{\alpha }}_{i}\rangle \langle {\tilde{\alpha }}_{j}\rangle\) and we use the mode ordering \(({\tilde{\alpha }}_{x,D},{\tilde{\alpha }}_{p,D},{\tilde{\alpha }}_{x,p},{\tilde{\alpha }}_{p,p})\) where (in an abuse of notation) the second subscript now denotes whether we are considering either the dealer or the players estimate. Thus, the first two diagonal elements represent the variance of the parameters to be estimated, and the second two diagonal elements represent this variance plus the error associated with the imperfect measurement of the unknown displacements. The off-diagonal elements represent the correlation between the dealer’s estimate (i.e. the true value) and the estimate made by the players. Note that in this way multiple different covariance matrices can be constructed, between the dealer and any single party, between the dealer and any pair of parties, and between the dealer and all three parties. From these covariance matrices the mutual information between the dealer and the different parties can be constructed. Let us make the assumption that \({v}_{{\alpha }_{x},m}={v}_{{\alpha }_{p},m}={v}_{\alpha ,m}\). Then the mutual information can be calculated as
Therefore, to achieve a mutual information of c bits or more, we require a MSE less than or equal to
From this equation and Eq. (13), we can determine the probability of obtaining a mutual information above a certain value.
This allows us to compare the mutual information when different numbers of parties work together. We note that, due to the asymmetry of our scheme, when parties C or B work individually or as a pair, they can access no information. Hence, we will ignore these combinations going forward. In this sense, we are not implementing ‘real’ secret sharing, as not all subsets of two or more parties can access the secret information.
Experimental results
In this section, we will first describe our experimental set-up, and then verify that the quantum state we are using is entangled. We next present results for the sensing task described in the previous section. Finally, we connect these results to the secret sharing of classical information. Secret sharing using CV states has been investigated many times in the past38,39,40,41,42,43,44,45,46 and so the idea is not novel in and of itself. However, we shall analyse the security through the HCRB. For DV systems, the analogy between secure quantum sensing and quantum secret sharing was noted in ref. 75. In this work security was obtained by preparing check states with a certain probability, as opposed to measuring conjugate parameters as is the case here.
Experimental set-up
A schematic of the experimental set-up is shown in Fig. 1b). The dealer, generates two squeezed states and mixes them on a 50:50 beam splitter. Details on the squeezed light sources used can be found in ref. 76. One mode of this state is subject to a second 50:50 beam splitter from which the two output modes are respectively distributed to parties B and C. A displacement in each quadrature is implemented on the remaining mode, before this is distributed to party A. In practice this displacement is implemented through an auxiliary beam which is amplitude and phase modulated and then mixed with party A’s mode of the TMSV state on a 98:2 beam splitter. The aim of the three parties, either working together or independently, is to measure the displacements as accurately as possible. In our experiment, each party implements homodyne detection on either the \(\hat{x}\) or \(\hat{p}\) quadrature. However, in our security analysis, we do not place such restrictions on any party.
Entanglement-enabled metrology task
We next perform an entanglement witnessing task, to ensure that no party is intercepting the quantum state and sending on a different state. The requirement on a CV state to be entangled, see refs. 77,78, allows us to design an entanglement-enabled quantum metrology task. When all three parties work together, we can construct the following quantities \({x}_{-}={x}_{A}/\sqrt{2}-({x}_{B}-{x}_{C})/2\) and \({p}_{+}={p}_{A}/\sqrt{2}+({p}_{B}-{p}_{C})/2\), which are unbiased estimators for \(({\alpha }_{x},{\alpha }_{p})/\sqrt{2}\). In the ideal case, using these estimators, it is possible to achieve a MSE for estimating \(({\alpha }_{x},{\alpha }_{p})/\sqrt{2}\) of
see Methods for the derivation. If the initial two mode state created by the dealer is not entangled, then \({v}_{{\alpha }_{x}^{{\prime} }}+{v}_{{\alpha }_{p}^{{\prime} }}\ge 4\), where we use \({v}_{{\alpha }_{x}^{{\prime} }}\) to denote that we are considering the MSE in estimating \({\alpha }_{x}/\sqrt{2}\) and similarly for \({v}_{{\alpha }_{p}^{{\prime} }}\). We can therefore use this task to verify that we are using a non-classical resource. Our experimental results when using this estimator are shown in Fig. 3.
The experimental data corresponds to the MSE when estimating \(({\alpha }_{x},{\alpha }_{p})/\sqrt{2}\) using the estimator described in ‘Experimental results’—Entanglement-enabled metrology task. The orange shaded region shows MSE values smaller than 4 which indicates that the parties share an entangled state. The x−axis shows the effective squeezing parameter. The alpha values being estimated on average have ∣α∣ = 0.2. Each data point corresponds to at least 107 measurement results and statistical error bars based on one standard deviation are smaller than the marker size.
Quantum metrology results
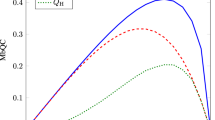
In Fig. 4 we present the MSE in estimating (αx, αp) for different combinations of parties working together. For two and three parties working together, the MSE is obtained directly from the experimental data. The experimental data differs significantly from the ideal theoretical precision (see Fig. 2) due to loss and anti-squeezing present in our experiment. For a single party working alone, the experimental data presented corresponds to the inferred HCRB. In reality, the homodyne detection which we implemented is not sufficient to reach the HCRB. Nevertheless, from the homodyne statistics we can infer the HCRB. We present the inferred HCRB, as opposed to the MSE obtained from homodyne detection, to place limits on the information which could have been extracted by any potentially omnipotent party working alone.
We show the MSE attained experimentally for simultaneously estimating the displacements (αx, αp). The solid blue line corresponds to the HCRB, Eq. (5), which sets the ultimate limit on the MSE which can be attained by any party working individually. The blue data points are the HCRB inferred from the experimentally reconstructed covariance matrix. The dashed green line and data points correspond to the MSE attainable when two parties work together. The upward and downward pointing green triangular data points correspond to parties A and C, and parties A and B working together respectively. The dot-dashed red line and data points correspond to the MSE when all three parties work together. The theoretical lines are based on fitting to a model. The shaded region represents 3% fluctuations in the optical loss on each arm and thermal noise fluctuations of 0.02 shot noise units on each arm. The displacements being estimated on average have ∣α∣ = 0.2. Each data point corresponds to at least 107 measurement results and statistical error bars based on one standard deviations are smaller than the marker size.
Secure access protocol
We now examine the security of our experiment in the sense of Eqs. (12) and (14). Figure 5 shows the probability density functions (PDFs) for the distribution of MSEs which could be obtained in all three scenarios (one, two and three parties working together) based on the rightmost data points in Fig. 4. The theoretical PDFs are obtained using Eq. (13) and the experimentally observed MSEs. The histograms show the experimental data analysed using different numbers of probe states. The slight deviation between the theoretical PDF and the observed PDF is potentially caused by the fact that the experimental MSEs in the \(\hat{x}\) and \(\hat{p}\) quadratures are not identical, which is assumed when deriving Eq. (13). It is evident that, as more probe states are used, the overlap of the distributions of MSE values attainable with multiple parties overlap less with the distribution of MSE values attainable by an individual party. Let us first compare the MSE attainable by all three parties working together to the MSE attainable by a single party. Choosing vT as the point where the two distributions are equally likely (vT = 5.5 when comparing the three-party MSE to the single party MSE and vT = 6.8 when comparing the two-party MSE to the single party MSE), using 10, 50 and 100 probe states for each quadrature, we can achieve a security given by δ = 0.18, δ = 0.013 and δ = 8 × 10−4 respectively. The corresponding success rates are Ps,3 = 0.87, Ps,3 = 0.989 and Ps,3 = 0.9993 respectively. When we compare the two party MSE to that of a single party, using 10, 50 and 100 probe states for each quadrature, we find δ = 0.39, δ = 0.22 and δ = 0.13 and Ps,2 = 0.68, Ps,2 = 0.81 and Ps,2 = 0.89 respectively.
The red, green and blue PDFs show the theoretical distribution of MSE values attainable when three parties work together, two parties work together and one party works alone respectively. N is the number of probe states used for estimating both αx and αp. The histograms show the corresponding experimental data based on 1.85 × 107/N data points. The theoretical PDFs are inferred from Eq. (13), using the rightmost experimental data points from Fig. 4.
Let us now consider a scenario where this type of protocol could be useful from a security viewpoint. One could imagine a trust fund bank account which we want to be accessible when either two or three parties work together and inaccessible when parties work individually. By distributing N quantum probe states with unknown displacements (αx,i, αp,i), a bank manager could only allow access to the bank provided the MSE was below some threshold. Depending on the threshold chosen, either two or three parties would be required to work together to access the bank account. In this manner either a (2,3) or (3,3) access structure can be created with security guaranteed up to the probabilities discussed above.
Mutual information
Finally, we shall discuss how this protocol could be extended to sharing a continuous stream of information. As discussed in ‘Theoretical results’, we can imagine that the dealer chooses (αx,i, αp,i) from a Gaussian distribution with variance Vdist. Then the correlation matrix between the dealer and any number of collaborating parties is given by Eq. (15). From this the mutual information between the dealers input and the final estimate of (αx, αp) can be calculated using Eq. (16). We emphasise that we have not actually implemented this protocol, as in our experiment, we do not change (αx,i, αp,i) in every run, rather we use a fixed value throughout the experiment. This is a technical limitation of our experiment which can be avoided and does not change any of the main results or conclusions. In Fig. 6a) and b) we show the mutual information which could have been attained in theory, based on the parameters in our experiment, had we drawn (αx,i, αp,i) from a Gaussian distribution.
a) The dot-dashed red, dashed green and solid blue lines show the mutual information which would be attainable for different input modulation variances when three parties work together, two parties work together and one party works alone respectively. In our experiment, we did not actually implement any random modulations. However, the plot is based on the experimental parameters of the rightmost data points in Fig. 4b) The mutual information which can be attained for Vdist = 2 as a function of the squeezing. This plot is also based on the experimental parameters. Note that the blue line assumes that any individual party is capable of reaching the HCRB. c) Probability of obtaining a mutual information of more than 1 bit, assuming Vdist = 4 based on the rightmost data points in Fig. 4.
Finally we investigate how the probability of attaining a mutual information above a certain value changes as a function of the number of probe states used. This is shown in Fig. 6c), based on the MSE values obtained experimentally. Note that in the experiment, \({v}_{{\alpha }_{x},m}\ne {v}_{{\alpha }_{p},m}\) (although this is approximately true), and so we use the average MSE in Fig. 6c).
Potential security flaws and issues
Before concluding, we point out some potential security loopholes and other potential issues. To guarantee security in the above protocols, all three parties will need verify that the state they share is entangled, as in Fig. 3. This is easily done by using a small subset of the data to verify entanglement. It will also be important to check that the parties are using unbiased estimators of (αx, αp), as otherwise it can be possible to violate the HCRB. This can be easily checked by the dealer using a small fraction of the experiments. We also note that party A could claim to have observed high loss on their mode. In this case, in order to ensure the estimates are unbiased, we need to scale the estimate by the inverse of the loss, which increases the MSE attainable. However, party A may not be telling the truth about the loss on their arm. Nevertheless, this issue can be avoided by aborting the protocol if the loss is too high. Additionally, in order to perform homodyne detection at remote stations, it will be necessary for the different parties to share a common phase reference. One approach for this is to distribute a local oscillator to the different parties, a well established technique previously demonstrated over distances greater than 200 km79. Alternatively, the parties could use a local local oscillator80. If the excess noise introduced by the use of a local local oscillator is sufficiently low, it would still be possible to demonstrate quantum-enhanced sensitivity.
Finally, it is important to point out that the HCRB sets a limit on the sum of the MSEs in the local estimation setting when parameters are a priori known to within some range. It stands to reason that by removing this information and assuming the parameters to be estimated are unknown no better estimation is possible. The HCRB also in general only applies in the limit of a large number of probe states. This isn’t an issue, as we can simply scale all the (αx,i, αp,i) down by a factor \(\sqrt{N}\), and send N copies of this state. Then we can use N large enough for the HCRB to be applicable. In this case, everything from above holds true. A problem with this is it requires N times more channel uses to send the same number of bits of information.
Discussion
We have theoretically and experimentally examined the role of quantum metrology in a secure access protocol and a quantum communication protocol. We envisage these results to be of importance to both the quantum metrology and secure quantum communication communities. In particular, the use of tools from quantum metrology to bound the security of quantum secret sharing may help to connect these two areas and may prompt the search for a more fundamental connection between these two areas. Along this line, Hayashi and Song have recently shown a connection between quantum secret sharing and symmetric private information retrieval81. Furthermore, as our multiparameter estimation involves multiple distinct parties, it may be of relevance for distributed quantum sensing82 or other scenarios where a remote parameter is being probed, such as gravitational field sensing83. Our sensing protocol may also be beneficial for the remote sensing of confidential information, such as medical information, as has been discussed for secure quantum enhanced sensing75,84,85,86,87,88,89,90,91 (see also Refs. 92,93). The fact that our protocol and the corresponding analysis naturally incorporates finite size effects, as discussed earlier, is another practical benefit compared to conventional quantum secure communication protocols, where finite size effects have to be added in94,95.
There are many ways to extend this research. In the limit of infinite squeezing, our protocol becomes perfectly secure. This suggests that in a DV setting it may be possible to demonstrate perfectly secure secret sharing, with the security guaranteed through quantum metrology. The results in this paper could be strengthened if the dealer implemented displacements on all three modes. Additionally, CV graph states, which have recently been shown to demonstrate an advantage for secret sharing in a quantum network setting96, may further enhance the performance of our protocol. It could also be beneficial to investigate the MSE which can be attained by a malicious party performing commonly considered attacks in QKD.
Methods
Holevo Cramér-Rao bound for simultaneous displacement estimation using an unbalanced thermal state
We consider the simultaneous estimation of a displacement in both the \(\hat{x}\) and \(\hat{p}\) quadratures using the Gaussian state with covariance matrix given in Eq. (4). We follow the approach of ref. 52, where the calculation of the HCRB for estimating Gaussian displacements64,97, was recast as a semi-definite programme. We now provide the solutions to both the primal and dual problem, verifying that our solution is correct. Rather than defining many new terms, we shall use all of the same terminology and definitions as ref. 52. We shall use the following basis.
which satisfies α(ej, ek) = δj,k. This lets us calculate
and
In order to write our solution, we need to define a basis for 2 × 2 real symmetric matrices. We shall use
and \({{\mathbb{A}}}_{j}=0\) for j = 4, 5, 6. We also define \({{\mathbb{B}}}_{j}=0\) for j = 1, 2, 3, \({{\mathbb{B}}}_{4}={{\mathbb{A}}}_{1}\), \({{\mathbb{B}}}_{5}={{\mathbb{A}}}_{2}\) and \({{\mathbb{B}}}_{6}={{\mathbb{A}}}_{3}\). Finally, we have b = [0, 0, 0, 1, 1, 0]. This allows us to provide the solution to the primal and dual problems.
Primal problem
The primal problem can be written as
subject to \({{{\rm{tr}}}}\{XB\}={b}_{j}\) where X is a positive Hermitian matrix. We define
where \({{\mathbb{I}}}_{d}\) is the d × d identity matrix, 0d is the d × d zero matrix and \({\mathbb{C}}={(1+{{{\rm{i}}}}{\mathbb{D}}/2)}^{-1}\).
The solution to the primal problem is given by.
where
and
where \(c=4{(1+{n}_{2})}^{2}/{v}_{2}\) and \(d=4{(1+{n}_{1})}^{2}/{v}_{1}\). The non-zero eigenvalues of X1 are
and
The only non-zero eigenvalue of X2 is given by c + d. Therefore all the eigenvalues of X are non-negative. It is easily verified that the other condition on X, \({{{\rm{tr}}}}\{XB\}={b}_{j}\), is satisfied by this solution. We can then verify that \({{{\rm{tr}}}}\{XC\}=4+2{n}_{1}+2{n}_{2}\).
Dual problem
By showing that the dual problem has the same solution, we confirm the optimality of our result. The dual problem can be written
subject to ∑j yj Bj ≥ C. A solution is given by
The matrix ∑j yj Bj − C is given by
where
and
We first consider Y1 and rewrite it as
which has eigenvalues
We can then substitute in from above, to see that there are two non-zero eigenvalues given by
which are clearly both positive. Similarly it is obvious that both eigenvalues of Y2 are positive. Finally, there is only one non-zero eigenvalue of Y3, given by
which is guaranteed to be positive. Therefore, the solution y satisfies the constraints, and gives the same solution as the primal problem. Hence, we can be sure our solution is optimal. Therefore, the HCRB for the simultaneous estimation of a displacement in the \(\hat{x}\) and \(\hat{p}\) quadrature with an unbalanced thermal state is given by
For equal variances in both quadratures this reduces to the known results of refs. 57,98,99
Probability density function for distribution of MSE values
We wish to derive the probability density function (PDF) for obtaining a certain MSE given N repetitions of the experiment with mean MSE of μM in each quadrature. The error in each estimate, xi or pi, will be randomly distributed following a normal distribution with zero mean and standard deviation of \(\sqrt{{\mu }_{{{{\rm{M}}}}}}\). The quantity we are interested in is the mean of this quantity squared
where \({\tilde{\mu }}_{{{{\rm{M}}}}}\) is the observed mean MSE. If \({\tilde{\mu }}_{{{{\rm{M}}}}}\) is repeatedly sampled, the distribution will follow a scaled χ2 distribution. Assuming that the MSE in both quadratures is the same, we can rewrite \({\tilde{\mu }}_{{{{\rm{M}}}}}\) as
The PDF for a χ2 distribution with k degrees of freedom is well known and given by
Recognising Eq. (42) as a scaled χ2 distribution with 2N degrees of freedom and using the change of variables formula for PDFs, with the function g(y) = yμM/N, we arrive at the PDF for the observed MSE values.
Derivation of Eq. 18
In this section, we show that the estimator described in ‘Experimental results’ for estimating \(({\alpha }_{x},{\alpha }_{p})/\sqrt{2}\), can achieve a MSE given by Eq. (18). To do this we will use the standard rules for adding random variables. Assume we have three random variables X, Y and Z which are drawn from the following multivariate normal distribution
Then it is known that the new variable aX + bY + cZ is normally distributed with mean aμX + bμY + cμZ and variance \({a}^{2}{\sigma }_{X}^{2}+{b}^{2}{\sigma }_{Y}^{2}+{c}^{2}{\sigma }_{Z}^{2}+2ab{\sigma }_{X,Y}+2ac{\sigma }_{X,Z}+2bc{\sigma }_{Y,Z}\). Using Eq. (2) we can calculate the variance of the random variables \({x}_{-}={x}_{A}/\sqrt{2}-({x}_{B}-{x}_{C})/2\) and \({p}_{+}={p}_{A}/\sqrt{2}+({p}_{B}-{p}_{C})/2\) to be e−2r. As we can only assign half of the resources to measuring x− and half for p+, we scale these variances by a factor of 2. Summing the variance, then shows that the MSE is given by \({v}_{{\alpha }_{x}^{{\prime} }}+{v}_{{\alpha }_{p}^{{\prime} }}=4{e}^{-2r}\), in agreement with Eq. (18).
Finally, it only remains to show that x− and p+ are unbiased estimators for \(({\alpha }_{x},{\alpha }_{p})/\sqrt{2}\). As the mean of xB, xC, pB and pC are 0, the mean of x− and p+ are equal to the mean of \({x}_{A}/\sqrt{2}\) and \({p}_{A}/\sqrt{2}\) respectively. Therefore, the estimator is unbiased.
Data availability
The data that support the findings of this study are available from the corresponding author upon reasonable request.
Code availability
The code that support the findings of this study is available from the corresponding author upon reasonable request.
References
Brukner, Č., Żukowski, M., Pan, J.-W. & Zeilinger, A. Bell’s inequalities and quantum communication complexity. Phys. Rev. Lett. 92, 127901 (2004).
Masanes, L. All bipartite entangled states are useful for information processing. Phys. Rev. Lett. 96, 150501 (2006).
Leibfried, D. et al. Toward Heisenberg-limited spectroscopy with multiparticle entangled states. Science 304, 1476–1478 (2004).
Kacprowicz, M., Demkowicz-Dobrzański, R., Wasilewski, W., Banaszek, K. & Walmsley, I. Experimental quantum-enhanced estimation of a lossy phase shift. Nat. Photonics 4, 357–360 (2010).
Daryanoosh, S., Slussarenko, S., Berry, D. W., Wiseman, H. M. & Pryde, G. J. Experimental optical phase measurement approaching the exact Heisenberg limit. Nat. Commun. 9, 1–6 (2018).
Pedrozo-Peñafiel, E. et al. Entanglement on an optical atomic-clock transition. Nature 588, 414–418 (2020).
Marciniak, Ch. D. et al. Optimal metrology with programmable quantum sensors. Nature 603, 604–609 (2022).
Guo, X. et al. Distributed quantum sensing in a continuous-variable entangled network. Nat. Phys. 16, 281–284 (2020).
Roccia, E. et al. Entangling measurements for multiparameter estimation with two qubits. Quantum Sci. Technol. 3, 01LT01 (2017).
Hou, Z. et al. Deterministic realization of collective measurements via photonic quantum walks. Nat. Commun. 9, 1–7 (2018).
Conlon, L. O. et al. Approaching optimal entangling collective measurements on quantum computing platforms. Nat. Phys. 1–7 (2023).
Conlon, L. O., Eilenberger, F., Lam, P. K. & Assad, S. M. Discriminating mixed qubit states with collective measurements. Commun. Phys. 6, 337 (2023).
Pezzé, L. & Smerzi, A. Entanglement, nonlinear dynamics, and the Heisenberg limit. Phys. Rev. Lett. 102, 100401 (2009).
Hyllus, P., Gühne, O. & Smerzi, A. Not all pure entangled states are useful for sub-shot-noise interferometry. Phys. Rev. A 82, 012337 (2010).
Krischek, R. et al. Useful multiparticle entanglement and sub-shot-noise sensitivity in experimental phase estimation. Phys. Rev. Lett. 107, 080504 (2011).
Strobel, H. et al. Fisher information and entanglement of non-Gaussian spin states. Science 345, 424–427 (2014).
Tóth, G. & Apellaniz, I. Quantum metrology from a quantum information science perspective. J. Phys. A Math. Theor. 47, 424006 (2014).
Tóth, G. & Vértesi, T. Quantum states with a positive partial transpose are useful for metrology. Phys. Rev. Lett. 120, 020506 (2018).
Yadin, B., Fadel, M. & Gessner, M. Metrological complementarity reveals the Einstein-Podolsky-Rosen paradox. Nat. Commun. 12, 1–8 (2021).
Bell, J. S. On the Einstein-Podolsky-Rosen paradox. Phys. Phys. Fiz. 1, 195 (1964).
Fröwis, F., Fadel, M., Treutlein, P., Gisin, N. & Brunner, N. Does large quantum Fisher information imply Bell correlations? Phys. Rev. A 99, 040101 (2019).
Niezgoda, A. & Chwedeńczuk, J. Many-body nonlocality as a resource for quantum-enhanced metrology. Phys. Rev. Lett. 126, 210506 (2021).
Bennett, C. H., Brassard, G. Quantum cryptography: public key distribution and coin tossing. In: Proc. International Conference on Computers, Systems & Signal Processing. 175–179 (1984).
Ekert, A. K. Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67, 661 (1991).
Vallone, G. et al. Experimental satellite quantum communications. Phys. Rev. Lett. 115, 040502 (2015).
Liao, S.-K. et al. Satellite-to-ground quantum key distribution. Nature 549, 43–47 (2017).
Liao, S.-K. et al. Satellite-relayed intercontinental quantum network. Phys. Rev. Lett. 120, 030501 (2018).
Stucki, D. et al. Long-term performance of the SwissQuantum quantum key distribution network in a field environment. New J. Phys. 13, 123001 (2011).
Sasaki, M. et al. Field test of quantum key distribution in the Tokyo QKD Network. Opt. Express 19, 10387–10409 (2011).
Dynes, J. et al. Cambridge quantum network. npj Quantum Inf. 5, 1–8 (2019).
Yin, J. et al. Entanglement-based secure quantum cryptography over 1,120 kilometres. Nature 582, 501–505 (2020).
Erkılıç, Ö. et al. Surpassing the repeaterless bound with a photon-number encoded measurement-device-independent quantum key distribution protocol. npj Quantum Inf. 9, 29 (2023).
Karlsson, A., Koashi, M. & Imoto, N. Quantum entanglement for secret sharing and secret splitting. Phys. Rev. A 59, 162 (1999).
Cleve, R., Gottesman, D. & Lo, H.-K. How to share a quantum secret. Phys. Rev. Lett. 83, 648 (1999).
Tittel, W., Zbinden, H. & Gisin, N. Experimental demonstration of quantum secret sharing. Phys. Rev. A 63, 042301 (2001).
Xiao, L., Long, G. L., Deng, F.-G. & Pan, J.-W. Efficient multiparty quantum-secret-sharing schemes. Phys. Rev. A 69, 052307 (2004).
Zhang, Z.-j & Man, Z.-x Multiparty quantum secret sharing of classical messages based on entanglement swapping. Phys. Rev. A 72, 022303 (2005).
Tyc, T. & Sanders, B. C. How to share a continuous-variable quantum secret by optical interferometry. Phys. Rev. A 65, 042310 (2002).
Lance, A. M. et al. Continuous variable (2, 3) threshold quantum secret sharing schemes. New J. Phys. 5, 4 (2003).
Lance, A. M., Symul, T., Bowen, W. P., Sanders, B. C. & Lam, P. K. Tripartite quantum state sharing. Phys. Rev. Lett. 92, 177903 (2004).
Lance, A. M. et al. Continuous-variable quantum-state sharing via quantum disentanglement. Phys. Rev. A 71, 033814 (2005).
Kogias, I., Xiang, Y., He, Q. & Adesso, G. Unconditional security of entanglement-based continuous-variable quantum secret sharing. Phys. Rev. A 95, 012315 (2017).
Zhou, Y. et al. Quantum secret sharing among four players using multipartite bound entanglement of an optical field. Phys. Rev. Lett. 121, 150502 (2018).
Grice, W. P. & Qi, B. Quantum secret sharing using weak coherent states. Phys. Rev. A 100, 022339 (2019).
Wu, X., Wang, Y. & Huang, D. Passive continuous-variable quantum secret sharing using a thermal source. Phys. Rev. A 101, 022301 (2020).
Liao, Q., Liu, H., Zhu, L. & Guo, Y. Quantum secret sharing using discretely modulated coherent states. Phys. Rev. A 103, 032410 (2021).
Weedbrook, C. et al. Gaussian quantum information. Rev. Mod. Phys. 84, 621 (2012).
Robertson, H. P. The uncertainty principle. Phys. Rev. 34, 163 (1929).
Heisenberg, W. Über den anschaulichen Inhalt der quantentheoretischen Kinematik und Mechanik. In Original Scientific Papers Wissenschaftliche Originalarbeiten, 478–504 (Springer, 1985).
Arthurs, E. & Kelly Jr, J. On the simultaneous measurement of a pair of conjugate observables. Bell Syst. Tech. J. 44, 725–729 (1965).
Arthurs, E. & Goodman, M. Quantum correlations: a generalized Heisenberg uncertainty relation. Phys. Rev. Lett. 60, 2447 (1988).
Bradshaw, M., Lam, P. K. & Assad, S. M. Ultimate precision of joint quadrature parameter estimation with a Gaussian probe. Phys. Rev. A 97, 012106 (2018).
Furusawa, A. et al. Unconditional quantum teleportation. Science 282, 706–709 (1998).
Zhao, J. et al. Enhancing quantum teleportation efficacy with noiseless linear amplification. Nat. Commun. 14, 4745 (2023).
Tan, S.-H. et al. Quantum illumination with Gaussian states. Phys. Rev. Lett. 101, 253601 (2008).
Bradshaw, M. et al. Optimal probes for continuous-variable quantum illumination. Phys. Rev. A 103, 062413 (2021).
Bradshaw, M., Assad, S. M. & Lam, P. K. A tight Cramér–Rao bound for joint parameter estimation with a pure two-mode squeezed probe. Phys. Lett. A 381, 2598–2607 (2017).
Assad, S. M. et al. Accessible precisions for estimating two conjugate parameters using Gaussian probes. Phys. Rev. Res. 2, 023182 (2020).
Steinlechner, S. et al. Quantum-dense metrology. Nat. Photonics 7, 626–630 (2013).
D’Ariano, G. M., Presti, P. L. & Paris, M. G. Using entanglement improves the precision of quantum measurements. Phys. Rev. Lett. 87, 270404 (2001).
Ralph, T. C. Continuous variable quantum cryptography. Phys. Rev. A 61, 010303 (1999).
Ralph, T. C. Security of continuous-variable quantum cryptography. Phys. Rev. A 62, 062306 (2000).
Holevo, A. S. Statistical decision theory for quantum systems. J. Multivar. Anal. 3, 337–394 (1973).
Holevo, A. S. Probabilistic and Statistical Aspects of Quantum Theory, vol. 1 (Springer Science & Business Media, 2011).
Kahn, J. & Guţă, M. Local asymptotic normality for finite-dimensional quantum systems. Commun. Math. Phys. 289, 597–652 (2009).
Yamagata, K. et al. Quantum local asymptotic normality based on a new quantum likelihood ratio. Ann. Stat. 41, 2197–2217 (2013).
Yang, Y., Chiribella, G. & Hayashi, M. Attaining the ultimate precision limit in quantum state estimation. Commun. Math. Phys. 368, 223–293 (2019).
Conlon, L. O., Suzuki, J., Lam, P. K. & Assad, S. M. The gap persistence theorem for quantum multiparameter estimation. arXiv preprint arXiv:2208.07386 (2022).
Nagaoka, H. A new approach to Cramér-Rao bounds for quantum state estimation. In Asymptotic Theory of Quantum Statistical Inference: Selected Papers, 100–112 (2005). Originally published as IEICE Technical Report, 89, 228, IT 89-42, 9-14 (1989).
Nagaoka, H. A generalization of the simultaneous diagonalization of Hermitian matrices and its relation to quantum estimation theory. In Asymptotic Theory of Quantum Statistical Inference: Selected Papers, 133–149 (World Scientific, 2005). Originally published as Trans. Jap. Soc. Indust. Appl. Math., 1, 43–56 (1991) in Japanese. Translated to English by Y. Tsuda.
Conlon, L. O., Suzuki, J., Lam, P. K., Assad, S. M. Efficient computation of the Nagaoka–Hayashi bound for multi-parameter estimation with separable measurements. npj Quantum Inf. 7, 110 (2020).
Reid, M. et al. Colloquium: the Einstein-Podolsky-Rosen paradox: from concepts to applications. Rev. Mod. Phys. 81, 1727 (2009).
Crépeau, C., Gottesman, D. & Smith, A. Approximate quantum error-correcting codes and secret sharing schemes. In Proc. Annual International Conference on the Theory and Applications of Cryptographic Techniques, 285–301 (Springer, 2005).
Ouyang, Y. et al. Approximate reconstructability of quantum states and noisy quantum secret sharing schemes. Phys. Rev. A 108, 012425 (2023).
Huang, Z., Macchiavello, C. & Maccone, L. Cryptographic quantum metrology. Phys. Rev. A 99, 022314 (2019).
Zhao, J. et al. A high-fidelity heralded quantum squeezing gate. Nat. Photonics 14, 306–309 (2020).
Simon, R. Peres-Horodecki separability criterion for continuous variable systems. Phys. Rev. Lett. 84, 2726 (2000).
Duan, L.-M., Giedke, G., Cirac, J. I. & Zoller, P. Inseparability criterion for continuous variable systems. Phys. Rev. Lett. 84, 2722 (2000).
Zhang, Y. et al. Long-distance continuous-variable quantum key distribution over 202.81 km of fiber. Phys. Rev. Lett. 125, 010502 (2020).
Hajomer, A. A. et al. Long-distance continuous-variable quantum key distribution over 100-km fiber with local local oscillator. Sci. Adv. 10, eadi9474 (2024).
Hayashi, M. & Song, S. Unified approach to secret sharing and symmetric private information retrieval with colluding servers in quantum systems. IEEE Trans. Info. Theor. 69, 6537–6563 (2023).
Liu, L.-Z. et al. Distributed quantum phase estimation with entangled photons. Nat. Photonics 15, 137–142 (2021).
Conlon, L. O. et al. Enhancing the precision limits of interferometric satellite geodesy missions. npj Microgravity 8, 1–10 (2022).
Xie, D., Xu, C., Chen, J. & Wang, A. M. High-dimensional cryptographic quantum parameter estimation. Quantum Inf. Process. 17, 1–10 (2018).
Shettell, N., Kashefi, E. & Markham, D. Cryptographic approach to quantum metrology. Phys. Rev. A 105, L010401 (2022).
Takeuchi, Y., Matsuzaki, Y., Miyanishi, K., Sugiyama, T. & Munro, W. J. Quantum remote sensing with asymmetric information gain. Phys. Rev. A 99, 022325 (2019).
Okane, H., Hakoshima, H., Takeuchi, Y., Seki, Y. & Matsuzaki, Y. Quantum remote sensing under the effect of dephasing. Phys. Rev. A 104, 062610 (2021).
Peng, X.-X. et al. Trusted quantum remote sensing based on self-testing of entangled states. Phys. Rev. A 105, 032615 (2022).
Shettell, N. & Markham, D. Quantum metrology with delegated tasks. Phys. Rev. A 106, 052427 (2022).
Moore, S. W. & Dunningham, J. A. Secure quantum remote sensing without entanglement. AVS Quantum Science 5.1 (2023).
Yin, P. et al. Experimental demonstration of secure quantum remote sensing. Phys. Rev. Appl. 14, 014065 (2020).
Giovannetti, V., Lloyd, S. & Maccone, L. Positioning and clock synchronization through entanglement. Phys. Rev. A 65, 022309 (2002).
Komar, P. et al. A quantum network of clocks. Nat. Phys. 10, 582–587 (2014).
Leverrier, A., Grosshans, F. & Grangier, P. Finite-size analysis of a continuous-variable quantum key distribution. Phys. Rev. A 81, 062343 (2010).
Scarani, V. & Renner, R. Quantum cryptography with finite resources: unconditional security bound for discrete-variable protocols with one-way postprocessing. Phys. Rev. Lett. 100, 200501 (2008).
Walk, N. & Eisert, J. Sharing classical secrets with continuous-variable entanglement: composable security and network coding advantage. Phys. Rev. X Quantum 2, 040339 (2021).
Holevo, A. Noncommutative analogues of the Cramér-Rao inequality in the quantum measurement theory. In Proc. Third Japan-ŤUSSR Symposium on Probability Theory, 194–222 (Springer, 1976).
Genoni, M. G. et al. Optimal estimation of joint parameters in phase space. Phys. Rev. A 87, 012107 (2013).
Bakmou, L. & Daoud, M. Ultimate precision of joint parameter estimation under noisy Gaussian environment. Phys. Lett. A 428, 127947 (2022).
Acknowledgements
This research was funded by the Australian Research Council Centre of Excellence CE170100012, Laureate Fellowship FL150100019 and the Australian Government Research Training Program Scholarship. This research is supported by A*STAR C230917010, Emerging Technology and A*STAR C230917004, Quantum Sensing.
Author information
Authors and Affiliations
Contributions
L.C., B.S., A.W., J.Z. and J.J. contributed to running the experiment and taking the experimental data. B.S. and L.C. modelled the supporting theory and performed the numerical analysis. L.C. wrote the manuscript. All authors contributed to discussions regarding the results in this paper. S.A. and P.K.L. supervised the project.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Conlon, L.O., Shajilal, B., Walsh, A. et al. Verifying the security of a continuous variable quantum communication protocol via quantum metrology. npj Quantum Inf 10, 35 (2024). https://doi.org/10.1038/s41534-024-00834-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41534-024-00834-9