Abstract
Quantum secure metrology protocols harness quantum effects to probe remote systems with enhanced precision and security. Traditional QSM protocols require multi-partite entanglement, which limits its near-term implementation due to technological constraints. This paper proposes a QSM scheme that employs Bell pairs to provide unconditional security while offering precision scaling beyond the standard quantum limit. We provide a detailed comparative performance analysis of our proposal under multiple attacks. We found that the employed controlled encoding strategy is far better than the parallel encoding of multi-partite entangled states with regard to the secrecy of the parameter. We also identify and characterize an intrinsic trade-off relationship between the maximum achievable precision and security under the limited availability of resources. The dynamic scalability of the proposed protocol makes it suitable for large-scale network sensing scenarios.
Similar content being viewed by others
Introduction
High-resolution sensors are pivotal for applications ranging from autonomous transportation to smart health-care systems1. Such sensing networks carry sensitive information that must be transmitted securely. However, when operated using classical components, these networks suffer from two significant challenges namely, statistical errors which limit the achievable precision and the rise of computational resources that may compromise information security. Contrarily, this incapacity is circumvented by incorporating quantum resources which enhances the achievable accuracy and provide unconditional security2,3,4,5,6,7,8,9,10,11,12,13.
Quantum metrology protocols operated over quantum sensing networks typically consist of three fundamental steps: (i) the creation of an appropriate probe state, (ii) its evolution in the system of interest described by a physical parameter \(\phi\), and (iii) the measurement of the encoded state5,6,7,8,9,14. The encoded state is measured by employing suitable measurement settings, and the measurement results are processed to formulate an estimate of the parameter. The parameter \(\phi\), which describes the unknown system of interest, is induced by the action of the Hamiltonian generator H. The evolution of the state \(\rho _o\) to \(\rho _\phi\) can be described by the unitary map \(U_\phi = e^{-i\phi H}\). Using a set of measurement operators \(M_x\), the probability distribution post measurement is obtained by utilizing the Born rule \(P(x|\phi ) = \textrm{tr} [M_x\rho _\phi ]\). The associated quantum Fisher information (QFI) is
where L is the symmetric logarithmic derivative6,7. The Fisher information is directly related to the displacement of the probe state caused by even slight fluctuations of the parameter. An appropriate measure of the accuracy of our estimate is the units-corrected mean squared error of the estimate14,15
Using the theory of error propagation7, we reduce this problem to measurements on an observable O which is derived after v repetitions of the experiment as
Conventionally, quantum metrology leverages quantum entanglement to surpass the standard quantum limit (SQL) and achieve measurement precision up to the Heisenberg limit (HL)5,6,7,14. In addition, the quantum states have a non-deterministic nature leading to uncertainties in their characterization. Therefore, they are employed in quantum cryptography protocols to provide information-theoretic security2,3. The integration of aforementioned concepts is fundamental to quantum secure metrology (QSM) protocols, through which we can sense a remote system with precision beyond the SQL while ensuring the transmission of the sensing parameter with unconditional security10,11,12,13,16,17,18.
Efficient quantum metrology protocols for network sensing-based applications require robust entanglement generation and distribution. In the noisy intermediate-scale quantum (NISQ)19 era, constraints on quantum hardware limit the practical applicability of such protocols. Most of the proposed QSM protocols utilize multi-partite entangled states10,16,17,18. However, generating genuine N-partite entanglement is based on probabilistic or indirect methods20,21. As a consequence, it significantly increases the required resources to faithfully establish genuine multipartite entanglement over quantum sensing networks. A suitable alternative is a bipartite entangled state such as the Bell state22, whose generation is relatively trivial. They can be expressed as one of the four orthogonal states:
Recent proposals have pointed towards their deterministic creation23,24,25, which lead to achieving relatively higher entanglement generation rates. Furthermore, increasing the number of entangled particles subjects the state to superdecoherence26, thereby compromising its distribution by reducing the transfer fidelity27. Similarly, distribution mechanism of Bell states is relatively more robust and less expensive than multi-partite states. For practical implementation in the near future, QSM protocols have to be designed employing fewer entangled particles, an idea that our proposed protocol embodies.
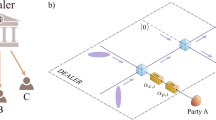
In this article, we propose a QSM protocol that involves two parties, Alice (source) and Bob (encoder), who perform QSM using Bell pairs. We utilize a controlled encoding strategy, eliminating the need for arbitrary states and additional gate operations to conceal the probe states from an eavesdropper. The security of our protocol is based on Bell’s theorem3,28,29 and does not require the need for a pre-shared key. We supplement our protocol with a security analysis for multiple attacks and prove its robustness against them. As we assume a resource-constrained setting, we characterize the trade-off relationship between the protocol’s maximum achievable precision and security. We show this trade-off mathematically and provide a bound on the allocation of resources to guarantee information security while providing a quantum advantage in precision. Such a case is relevant to real-world scenarios where the available resources are finite. Finally, we show that the proposed protocol may easily be extended to a multi-party scenario.
Methods
In this section, we will provide the quantum secure metrology (QSM) protocol along with a comprehensive performance analysis.
Quantum secure metrology (QSM)
The QSM protocol allows participants to estimate the parameter with enhanced precision while also ensuring its security. Firstly, we will discuss the system model of this protocol followed with detailed steps involved in its implementation.
System model
Our model consists of two participants, Alice and Bob, as illustrated in Fig. 1. They are connected via a quantum channel and communicate publicly through an authenticated classical channel (similar to quantum key distribution protocols). Both participants can perform local operations and classical communication (LOCC). Specifically, Alice is in charge of probe state preparation and parameter estimation. Herein, the Bell state is idealized as a metrological probe. Bob performs sequential parameter encoding on these probe states. In the following, we present our protocol.
Protocol
-
(1)
Probe state preparation and distribution: First stage of the protocol contains the following steps:
-
(a)
Alice generates \(\ell\) Bell pairs of the form
$$\begin{aligned} \left| \Phi _{AB} \right\rangle = \frac{\left| 0_A0_B \right\rangle + \left| 1_A 1_B \right\rangle }{\sqrt{2}}. \end{aligned}$$(4) -
(b)
She prepares two ordered sequences, \(S_j\), \(j \in \{A, B\}\). \(S_j\) contains the \(q_{j}^i\) particles of the \(\ell\) Bell pairs, where \(i \in \{ 1, 2, \cdots , \ell \}\).
-
(c)
She keeps the sequence \(S_A\) for herself and sends the sequence \(S_B\) to Bob via the quantum channel.
-
(a)
-
(2)
Verification: After receiving the sequence \(S_B\), Bob verifies the Bell pairs by the following method:
-
(a)
Bob randomly selects the particles from the sequence \(S_B\) with probability \(\left( 1 - P_E\right) /2\) . He also randomly selects the measuring basis either \(\sigma _x\) or \(\sigma _z\) for each particle.
-
(b)
Then he announces the selected basis and particle location to Alice via the classical authenticated channel.
-
(c)
Both parties measure their particles and Alice announces her measurement results.
-
(d)
Bob compares the measurement results. If he finds errors in the correlation, he will abort the protocol; otherwise, he will continue to the next step.
-
(a)
-
(3)
Sequential encoding: After the verification stage, Bob discards the particles that were used for verification. Bob performs the sequential encoding on the \(q_{B}^i\) according to the following rule:
$$\begin{aligned} U_{B}^i = {\left\{ \begin{array}{ll} U_{E}^{N}, \, \mathrm { with \, probability \,\,} P_E,\\ U_{I}, \, \mathrm { with \, probability \, \,} \frac{1 - P_E}{2}.\end{array}\right. } \end{aligned}$$Here,
$$\begin{aligned} U_E= & {} \left| 0 \right\rangle \left\langle 0 \right| + e^{\iota \phi } \left| 1 \right\rangle \left\langle 1 \right| \; \; \;\text {and,} \\ U_I= & {} \left| 0 \right\rangle \left\langle 0 \right| + \left| 1 \right\rangle \left\langle 1 \right| \end{aligned}$$where \(\phi\) is the encoded parameter. After the encoding process, Bob sends the particles back to Alice.
-
(4)
Secure parameter estimation:
-
(a)
Bob announced the location of the particle selected for security of the quantum channel.
-
(b)
Alice measure these probe states in the Bell basis and estimates the error rate. If she finds an error in the probe states, she will abort the protocol; otherwise, she will continue to the next step.
-
(c)
Alice performs the parameter estimation by measuring the encoded probe states in the Bell basis and calculates the quantum Crámer-Rao bound.
$$\begin{aligned} \delta ^{2}\phi \ge \frac{1}{P_E vN^2}. \end{aligned}$$(5)
-
(a)
Performance analysis
Below, we employ metrics such as correctness, security, and achievable precision for the performance analysis of the QSM protocol. We also augment a comparative analysis for the intrinsic precision-security trade-off in such experiments.
Correctness
In this subsection, we detail the correctness of our protocol. Alice and Bob securely share the Bell state of the form (4) in the first two steps of the protocol. Bob performs the sequential encoding by applying \(U_E^N\) on his particle \(q^i_B\) with probability \(P_E\). This will introduce the phase on the Bell state,
where
In the last step, Alice measures the sequentially encoded states using the Bell basis and estimates the parameter. We provide the proof of precision bound (5) in the precision section.
Security
In our security analysis section, we consider two scenarios: (1) the adversary attacks the protocol during the transmission of the probe state particle from Alice to Bob, (2) the adversary attacks the protocol when the probe state particle travels back to Alice from Bob.
In the first scenario, the adversary tries to capture the incoming probe state particle and sends a part of her custom-made probe state particle to Bob. After Bob’s encoding, when the probe state particle travels back to Alice, Eve can easily get the parameter value and encode the same parameter into the original probe state. This way, Eve can get the parameter value without being detected. Previously proposed protocol was vulnerable to this kind of attack10. However, during the verification steps, this attack will be detected. Bob will select probe state particles with the probability \(\left( 1 - P_E \right) /2\) from the sequence \(S_B\) and check the correlation with the Alice particles. If Eve performs such an attack, then the correlation between the measurement outcomes of Alice and Bob does not hold, which will abort the protocol.
In the second scenario, the adversary attacks the protocol when the encoded probe state particle travels back to Alice. The encoding is performed locally on the probe state particle. However, this encoding has a non-local effect and requires the whole probe state to decode the parameter. Eve has access to the only probe state particle that is similar to mixed state \(Tr_A\{\left| \Psi _{AB} \right\rangle \left\langle \Psi _{AB} \right| \} = I/2\) and can not get any information from this mixed state. The only option left for Eve is to disturb the protocol by encoding a random parameter. Eve can apply the unitary \(U_C\)
to the encoded probe state particle going towards Alice, which will compromise the encoded parameter. However, the parties involved will detect such an attack in our protocol. Bob encodes the parameter on the probe state with probability \(\left( 1 - P_E \right) /2\). Eve can not differentiate between encoded and decoy probe states in advance. When Bob applies the random unitary operation \(U_C\) on the decoy probe state, the decoy probe state evolves as follows
Bob announces the location of these decoy probe states, and Alice performs the Bell state measurement (BSM) and computes the error rate. If she finds errors in these decoy probe states, she will abort the protocol; otherwise, she will continue to the next step.
In both scenarios mentioned above, we can easily calculate the probability of detecting Eve \(P_d\). For every correlation check, the probability that Eve escapes undetected is 1/2, similar to the E91 protocol30. As previously mentioned, the parties can abandon the protocol if they detect Eve during the transmission of the probe state (from Alice to Bob or from Bob to Alice). The probability of the state being a decoy is \((1-P_E)/{2}\), and the number of probe states intercepted by Eve is l. Then, the probability of detecting Eve for one side transmission of the probe state will be
As l increases, \(P_D\) increases until it reaches unity in the asymptotic limit of l, as depicted in Fig. 2.
Precision
After validating the channel’s security, Alice receives the quantum state (6) and performs the parameter estimation process. The QFI attainable in this scenario is directly related to \(P_E\), which shows the number of resources employed for the parameter estimation. She measures the Bell observable \(B= \left| 0 \right\rangle \left\langle 1 \right| ^{\otimes 2}+\left| 1 \right\rangle \left\langle 0 \right| ^{\otimes 2}\). The expected value of the observable is
whereas the variance of the observable becomes
The results of the measurements are subjected to classical post-processing, and Alice gets an estimate \({\hat{\phi }}\). For v repetitions of the protocol, the number of resources used for parameter estimation becomes \(v' = P_E v\). We can substitute this value with expectation and variance of the observable in (3) to evaluate \(\delta ^2 \phi\) in (5).
Precision-security trade-off
Under the finite resource assumption, there is an intrinsic trade-off between achievable precision and security. The particles not utilized for parameter encoding are actually employed as decoy states. We can quantify this trade-off provided the precision does not exceed the HL and is equal to or less than the SQL to ensure a quantum advantage, which leads to
Figure 2 gives a detailed description of the precision-security trade-off relationship. As \(P_E\) increases, the number of resources delegated for the parameter estimation process increase, and thus the variance of the estimate decreases. As a consequence, the security of the protocol suffers since fewer resources are remained for the security checking phase. The values of \(P_E\) for \(P_E > 1/N\) would ensure a quantum advantage. Application-specific performance goals of secure quantum metrological scenarios may vary; conventionally, we can sacrifice one aspect at the expense of the other or analyze the trade-off to get the benefits of both.
Discussion
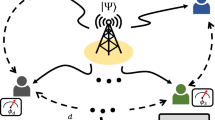
We have proposed a quantum secure metrology protocol that enables the secure estimation of a physical parameter by a remote party. The protocol provides a precision scaling beyond the SQL. We proved its robustness against multiple attacks in the security analysis. The controlled encoding strategy ensures the secrecy of the parameter. The allocation of quantum resources in terms of encoded and decoy states enables the detection of malicious parties in the channel. The resource allocation causes a precision security trade-off which we analyzed numerically and provided a bound on the allowable range of \(P_E\) values. Due to the inherent simplicity of the process, we can extend the protocol to multiple parties. Alice shares Bell states with K parties in such a setting, creating a distributed sensing network. Each participant \(B_i \in \{B_1, B_2,.......,B_K\}\) encodes their particle with the local parameter \(\phi _j \in \{\phi _1,\phi _2,.......,\phi _K\}\) and returns it to Alice, who performs multi-parameter estimation. Such topologies are extremely cost-effective as we can delegate the task of data processing to a single node in the network. Cluster sensing networks employing classical sensing nodes frequently use such schemes for applications such as spectroscopy and magnetometry31,32.
In practical implementations of QSM, the probe would have to pass through an imperfect quantum channel separating the source and the system. Our protocol allows for the global measurement of the state, which is crucial for gaining optimal results when employing entangled probes33,34,35. Performing these measurements is also practical, as recent works have proposed experimental implementations of deterministic Bell state analyzers36,37. However, generating deterministic N-partite GHZ state analyzers remains a challenge35. Thus, the practical performance of QSM protocols employing multi-partite probes will suffer not only the unfavorable generation and distribution of entanglement but also the non-realizable measurement techniques. Furthermore, we can observe the specific case proposed in our protocol as synonymous with the ancilla-assisted quantum metrology scheme, which yields higher QFI than the multi-partite case in the high noise regime34,38. Recent advances in quantum memories coupled with the relatively simple nature of biparite entanglement has also enabled efficient preservation of two spatially separated quantum particles39,40,41. These developments are vital in realizing practical QSM as the eavesdropping check during such protocols require the entangled states to retain a high degree of fidelity. We can also incorporate quantum repeaters in our protocol to enable state transfer among relatively distant nodes for large-scale sensing networks42,43,44,45. This idea is further aided by the advances in device-independent quantum key distribution as well as experimental realizations of high-fidelity long-distance secure quantum communication46,47. Furthermore, it is relatively trivial to perform entanglement purification and error correction to reduce the effect of noise in the channel when employing Bell states. For instance, the conception has also been utilized for creating interferometric telescopes48. Other issues in practical networks are side-channel attacks due to the imperfect isolation of private spaces possessed by both parties, Alice and Bob. This issue can be resolved by adopting alternate methods wherein virtual channels replace real channels, in turn, effectively culminating unwanted probing of private spaces held by the network recipients49.
Our work aims to accelerate the near-term deployment of QSM networks. Future works include characterizing its security and metrological performance in open dynamical systems with various noise models and eavesdropping attacks. Thus, the QSM formalism will create further opportunities for applications regarding the integrated paradigm of network security and network sensing.
Data availability
The datasets used and analyzed during the current study are available from the corresponding author upon reasonable request.
References
Rashid, B. & Rehmani, M. H. Applications of wireless sensor networks for urban areas: A survey. J. Netw. Comput. Appl. 60, 192–219 (2016).
Bennett, C. & Brassard, G. Quantum Cryptography: Public Key Distribution and Coin Tossing (ICCSS, 1984).
Ekert, A. K. Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67, 661–663 (1991).
Khan, A., Khalid, U., ur Rehman, J. & Shin, H. Quantum anonymous private information retrieval for distributed networks. IEEE Trans. Commun. 70, 4026–4037 (2022).
Giovannetti, V., Lloyd, S. & Maccone, L. Quantum-enhanced measurements: Beating the standard quantum limit. Science 306, 1330–1336 (2004).
Giovannetti, V., Lloyd, S. & Maccone, L. Advances in quantum metrology. Nat. Photon. 5, 222–229 (2011).
Tóth, G. & Apellaniz, I. Quantum metrology from a quantum information science perspective. J. Phys. A: Math. Theor. 47, 424006 (2014).
Khalid, U., Jeong, Y. & Shin, H. Measurement-based quantum correlation in mixed-state quantum metrology. Quantum Inf. Process. 17, 343 (2018).
Khalid, U., Rehman, J. & Shin, H. Metrologically resourceful multipartite entanglement under quantum many-body effects. Quantum Sci. Technol. 6, 025007 (2021).
Huang, Z., Macchiavello, C. & Maccone, L. Cryptographic quantum metrology. Phys. Rev. A 99, 022314 (2019).
Okane, H., Hakoshima, H., Takeuchi, Y., Seki, Y. & Matsuzaki, Y. Quantum remote sensing under the effect of dephasing. Phys. Rev. A 104, 062610 (2021).
Shettell, N., Hassani, M. & Markham, D. Private network parameter estimation with quantum sensors. arXiv:2207.14450 (2022).
Shi, M. et al. Quantum remote sensing with atom-light entangled interface. Quantum Front. 1, 1–9 (2022).
Giovannetti, V., Lloyd, S. & Maccone, L. Quantum metrology. Phys. Rev. Lett. 96, 010401 (2006).
Braunstein, S. L. & Caves, C. M. Statistical distance and the geometry of quantum states. Phys. Rev. Lett. 72, 3439–3443 (1994).
Xie, D., Xu, C., Chen, J. & Wang, A. M. High-dimensional cryptographic quantum parameter estimation. Quantum Inf. Process. 17, 1–10 (2018).
Shettell, N., Kashefi, E. & Markham, D. Cryptographic approach to quantum metrology. Phys. Rev. A 105, L010401 (2022).
Shettell, N. & Markham. Quantum metrology with delegated tasks. arXiv:2112.09199 (2021).
Preskill, J. Quantum computing in the NISQ era and beyond. Quantum 2, 79 (2018).
Bishop, L. S. et al. Proposal for generating and detecting multi-qubit GHZ states in circuit QED. New J. Phys. 11, 073040 (2009).
Borregaard, J., Søndberg, A. S. & Lodahl, P. Quantum networks with deterministic spin-photon interfaces. Adv. Quantum Technol. 2, 1800091 (2019).
Ghosh, S., Kar, G., Roy, A., Sen(De), A. & Sen, U. Distinguishability of Bell states. Phys. Rev. Lett. 87, 277902 (2001).
Wang, H. et al. On-demand semiconductor source of entangled photons which simultaneously has high fidelity, efficiency, and indistinguishability. Phys. Rev. Lett. 122, 113602 (2019).
Liu, J. et al. A solid-state source of strongly entangled photon pairs with high brightness and indistinguishability. Nat. Nanotechnol. 14, 586–593 (2019).
Kay, A. Generating quantum states through spin chain dynamics. New J. Phys. 19, 043019 (2017).
Monz, T. et al. 14-qubit entanglement: Creation and coherence. Phys. Rev. Lett. 106, 130506 (2011).
Zhong, Y. et al. Deterministic multi-qubit entanglement in a quantum network. Nature 590, 571–575 (2021).
Bell, J. S. On the Einstein Podolsky Rosen paradox. Phys. Phys. Fiz. 1, 195–200 (1965).
Deng, F.-G., Long, G. L. & Liu, X.-S. Two-step quantum direct communication protocol using the Einstein–Podolsky–Rosen pair block. Phys. Rev. A 68, 042317 (2003).
Boström, K. & Felbinger, T. Deterministic secure direct communication using entanglement. Phys. Rev. Lett. 89, 187902 (2002).
Fanian, F. & Kuchaki Rafsanjani, M. Cluster-based routing protocols in wireless sensor networks: A survey based on methodology.. J. Netw. Comput. Appl. 142, 111–142 (2019).
Shahraki, A., Taherkordi, A., Øystein, Haugen & Eliassen, F. Clustering objectives in wireless sensor networks: A survey and research direction analysis. Comput. Netw. 180, 107376 (2020).
Micadei, K. et al. Coherent measurements in quantum metrology. New J. Phys. 17, 023057 (2015).
Nichols, R., Bromley, T. R., Correa, L. A. & Adesso, G. Practical quantum metrology in noisy environments. Phys. Rev. A 94, 042101 (2016).
Piera, R. S., Walborn, S. P. & Aguilar, G. H. Experimental demonstration of the advantage of using coherent measurements for phase estimation in the presence of depolarizing noise. Phys. Rev. A 103, 012602 (2021).
Ralph, T. C., Söllner, I., Mahmoodian, S., White, A. G. & Lodahl, P. Photon sorting, efficient Bell measurements, and a deterministic controlled-Z gate using a passive two-level nonlinearity. Phys. Rev. Lett. 114, 173603 (2015).
Fan, L. & Cao, C. Deterministic CNOT gate and complete Bell-state analyzer on quantum-dot-confined electron spins based on faithful quantum nondemolition parity detection. J. Opt. Soc. Am. B 38, 1593–1603 (2021).
Huang, Z., Macchiavello, C. & Maccone, L. Noise-dependent optimal strategies for quantum metrology. Phys. Rev. A 97, 032333 (2018).
Zhu, T.-X. et al. On-demand integrated quantum memory for polarization qubits. Phys. Rev. Lett. 128, 180501 (2022).
Zhang, W. et al. Quantum secure direct communication with quantum memory. Phys. Rev. Lett. 118, 220501 (2017).
Sheng, Y.-B., Zhou, L. & Long, G.-L. One-step quantum secure direct communication. Sci. Bull. 67, 367–374 (2022).
Briegel, H.-J., Dür, W., Cirac, J. I. & Zoller, P. Quantum repeaters: The role of imperfect local operations in quantum communication. Phys. Rev. Lett. 81, 5932–5935 (1998).
Buterakos, D., Barnes, E. & Economou, S. E. Deterministic generation of all-photonic quantum repeaters from solid-state emitters. Phys. Rev. X 7, 041023 (2017).
Long, G.-L. et al. An evolutionary pathway for the quantum internet relying on secure classical repeaters. IEEE Network 36, 82–88 (2022).
Chung, J. et al. Design and implementation of the Illinois express quantum metropolitan area network. IEEE Trans. Quant. Eng. 3, 1–20 (2022).
Wang, S. et al. Beating the fundamental rate-distance limit in a proof-of-principle quantum key distribution system. Phys. Rev. X 9, 021046 (2019).
Zhang, W. et al. A device-independent quantum key distribution system for distant users. Nature 607, 687–691 (2022).
Gottesman, D., Jennewein, T. & Croke, S. Longer-baseline telescopes using quantum repeaters. Phys. Rev. Lett. 109, 070503 (2012).
Braunstein, S. L. & Pirandola, S. Side-channel-free quantum key distribution. Phys. Rev. Lett. 108, 130502 (2012).
Acknowledgements
This work was supported by the National Research Foundation of Korea (NRF) grant funded by the Korea government (MSIT) (NRF-2019R1A2C2007037, NRF-2022R1A4A3033401) and by the MSIT (Ministry of Science and ICT), Korea, under the ITRC (Information Technology Research Center) support program (IITP-2023-2021-0-02046) supervised by the IITP (Institute for Information & Communications Technology Planning & Evaluation).
Author information
Authors and Affiliations
Contributions
M.T.R. contributed the idea. M.T.R., A.K., U.K., J.R., and H.J. developed the theory and wrote the manuscript. H.S. improved the manuscript and supervised the research. All the authors contributed in analyzing and discussing the results and improving the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Rahim, M.T., Khan, A., Khalid, U. et al. Quantum secure metrology for network sensing-based applications. Sci Rep 13, 11630 (2023). https://doi.org/10.1038/s41598-023-38802-6
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-023-38802-6
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.