Abstract
In the emerging era of the internet of things (IoT), ubiquitous sensors continuously collect, consume, store, and communicate a huge volume of information which is becoming increasingly vulnerable to theft and misuse. Modern software cryptosystems require extensive computational infrastructure for implementing ciphering algorithms, making them difficult to be adopted by IoT edge sensors that operate with limited hardware resources and at low energy budgets. Here we propose and experimentally demonstrate an “all-in-one” 8 × 8 array of robust, low-power, and bio-inspired crypto engines monolithically integrated with IoT edge sensors based on two-dimensional (2D) memtransistors. Each engine comprises five 2D memtransistors to accomplish sensing and encoding functionalities. The ciphered information is shown to be secure from an eavesdropper with finite resources and access to deep neural networks. Our hardware platform consists of a total of 320 fully integrated monolayer MoS2-based memtransistors and consumes energy in the range of hundreds of picojoules and offers near-sensor security.
Similar content being viewed by others
Introduction
Information security is key to the sustainable growth and development of any modern society that thrives on global connectivity in this new era of the Internet of Things (IoT). Today, information is collected, stored, and communicated continuously by IoT sensors and edge devices that are found ubiquitously in our homes, workplaces, industrial manufacturing plants, transportation, health sectors, agricultural fields, and so on and so forth. However, with the increasing demand for edge devices, there is an escalating threat of tampering or physical intrusion of privacy by untrustworthy parities1,2. While the state-of-the-art cryptosystems offer powerful security solutions based on complex ciphering algorithms that can be implemented using hardware accelerators3,4,5,6,7,8,9,10,11, IoT edge devices have many restrictions in terms of computational capabilities due to limited hardware and energy resources. Furthermore, low-cost design needs, large-scale deployments, and the heterogeneous nature of IoT sensors limit the direct adoption of traditional security solutions, including the widely used public-key scheme. Due to inadequate security, IoT devices used in smart cars and smart homes have shown tremendous vulnerability in recent times12. Acknowledging these limitations, the United States National Institute of Standards and Technology (NIST) has proposed a multi-year effort, namely, the lightweight cryptography (LWC) standardization process to ensure confidentiality, integrity, and authenticity of data using efficient software modules. However, this effort emphasizes software solutions rather than providing hardware-based technological solutions. Therefore, it is timely to develop on-chip cryptographic primitives that require less computational resources and are integrated with IoT edge sensors.
Here, we exploit the optoelectronic sensing and in-memory compute capabilities of two-dimensional (2D) memtransistors based on photosensitive monolayer MoS2 to introduce near sensor and robust security solutions for IoT edge devices with minimal hardware investments and at frugal energy expenditure. Note that, unlike two-terminal memristors, 2D memtransistors are three-terminal devices, with their additional gate terminal allowing both non-volatile and analog programming of the conductance states as well as electrostatic control of the 2D channel. For our demonstration, we have fabricated an 8 × 8 crossbar array of fully integrated crypto engines to encode 8 × 8-pixel images. Each engine comprises five monolithically integrated MoS2 memtransistors (5T cell) to accomplish sensing and encoding functionalities. Our entire hardware platform utilizes a total of 320 MoS2 memtransistors, making it one of the very few experimental demonstration of medium scale integrated (MSI) circuits based on 2D materials and devices13. In addition, our hardware platform is “self-sufficient,” offering all-in-one IoT capabilities that include sensing, compute, storage, and security. Finally, our design inspiration for the 2D memtransistor-based crypto engine is derived from the organization of the peripheral and central nervous systems, which employ similar cell types, i.e., groups of neurons with different functionalities, that transduce external sensory information into electrical impulses to communicate among each other through successive encoding and decoding processes in the presence of a wide range of synaptic noises.
Note that our hardware platform is “self-sufficient,” offering all-in-one IoT capabilities that include sensing, compute, storage, and security. This is in sharp contrast to the state-of-the-art silicon-based complementary metal oxide semiconductor (CMOS) technology, which is limited in terms of memory and compute integration owing to the traditional von-Neumann computing architecture. Similarly, non von-Neumann platforms such as field programmable gate arrays (FPGAs) and memristive crossbar arrays lack sensing functionalities. In addition, two-terminal memristors are limited in computational capabilities and require CMOS peripherals, which increases area and energy overhead. In contrast, our proposed three-terminal memtransistor technology with the added feature of photosensitivity owing to the use of monolayer 2D material such as MoS2 offers a stand-alone and holistic solution for in-memory computing and sensing, which is critical for achieving integrated and energy/area efficient security solutions. Note that, beyond photodetectors14, MoS2 based FETs have been used as chemical sensors15, biological sensors15, touch sensors16, and radiation sensors17. Therefore, the sensing unit of our MoS2-based crypto engine is not limited to only optical stimuli. See Supplementary Table 1 for benchmarking of our work against earlier works on 2D materials18,19,20,21,22,23,24,25,26,27,28,29,30, memristors31,32,33,34,35,36,37, phase change materials38, and nano crystals39 that combine either “sensing and storage” or “sensing and compute” or “security and storage” but not all aspects in a single hardware platform.
Results
All-in-one 2D memtransistor-based hardware fabric
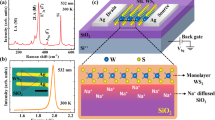
Figure 1a–c, respectively, show optical images of the fully integrated 8 × 8 crossbar array of the crypto engines, a representative crypto engine with five MoS2 memtransistors (5T cell) that combine sensing, storage, and encoding functionalities, and an individual MoS2 memtransistor, which is locally back-gated using a stack comprising atomic layer deposition (ALD) grown 50 nm Al2O3 on sputter deposited 40/30 nm Pt/TiN. All back-gate islands were placed on a commercially purchased SiO2/p++-Si substrate (see Supplementary Figs. 1–3 for enlarged optical images of the entire chip, 8 × 8 array of the crypto engines, and individual crypto engines). As we will discuss later, the Al2O3/Pt/TiN gate islands not only allow non-volatile programming of our MoS2 memtransistors but also enhance the photoresponse of MoS2 memtransistors owing to the phenomenon of gate-tunable persistent photoconductivity when subjected to the right polarity and magnitude of local back-gate biases. This, in turn, empowers our hardware platform to enable in-memory computing and near-sensor security, which are presently lacking for conventional silicon as well as emerging technologies.
Optical images of (a) the fully integrated 8 × 8 crossbar array of crypto engines, (b) a representative crypto engine with five MoS2 memtransistors (5T cell) that integrate sensing, storage, and encoding functionalities, and (c) an individual MoS2 memtransistor, which is locally back-gated using a stack comprising 50 nm Al2O3 on 40/30 nm Pt/TiN. All back-gate islands were placed on an SiO2/p++-Si substrate. Equivalent circuit diagrams for (d) the 8 × 8 crossbar array with column and row select lines and (e) each crypto engine. Herein, the MoS2 memtransistor used as \({{{{{{\rm{T}}}}}}}_{{{{{{\rm{PT}}}}}}}\) mimics sensory neurons and transduces optical information into persistent photoconductance (\({{{{{{\rm{G}}}}}}}_{{{{{{\rm{PT}}}}}}}\)), the MoS2 memtransistor used as \({{{{{{\rm{T}}}}}}}_{{{{{{\rm{WGNA}}}}}}}\) emulates noisy synapses, the MoS2 memtransistor used as \({{{{{{\rm{T}}}}}}}_{{{{{{\rm{SN}}}}}}}\) imitates spiking neurons converting noisy presynaptic information, i.e., \({{{{{{\rm{V}}}}}}}_{{{{{{\rm{PSV}}}}}}}\), into post-synaptic current spikes (\({{{{{{\rm{I}}}}}}}_{{{{{{\rm{PSC}}}}}}}\)), and the remianing 2 MoS2 memtransistors, \({{{{{{\rm{T}}}}}}}_{{{{{{\rm{PST}}}}}}}\) and \({{{{{{\rm{T}}}}}}}_{{{{{{\rm{EST}}}}}}}\), operate as the individual selector switches for the photosensing and the encoding operations, respectively. An example experimental demonstration of sensing and ciphering, where (f) the information, for example, an 8 × 8 pixelated image of the letter ‘N’ obtained by illuminating a blue light emitting diode (\({{{{{{\rm{I}}}}}}}_{{{{{{\rm{LED}}}}}}}\)) is presented to the corresponding 8 × 8 array of the crypto engines. Colormap of (g) post-illumination \({{{{{{\rm{G}}}}}}}_{{{{{{\rm{PT}}}}}}}\), (h) noisy \({{{{{{\rm{V}}}}}}}_{{{{{{\rm{PSV}}}}}}}\), and (i) encrypted \({{{{{{\rm{I}}}}}}}_{{{{{{\rm{PSC}}}}}}}\). j The information is revealed by a decoder through a voting process.
Figure 1d, e, respectively, show the circuit schematic for the crossbar architecture and for each crypto engine (see Supplementary Figs. 4, 5 for enlarged circuit schematics). In short, MoS2 memtransistors used as the photo transistor (\({T}_{{{{{{\rm{PT}}}}}}}\)) mimic sensory neurons and transduce optical information into persistent photoconductance (\({G}_{{{{{{\rm{PT}}}}}}}\)), whereas the MoS2 memtransistors used as the white Gaussian noise adder (\({T}_{{{{{{\rm{WGNA}}}}}}}\)) emulate noisy synapses. Note that \({T}_{{{{{{\rm{WGNA}}}}}}}\) are pre-programmed into random conductance states (\({G}_{{{{{{\rm{WGNA}}}}}}}\)). As such, \({T}_{{{{{{\rm{WGNA}}}}}}}\) superimpose white Gaussian noise of finite standard deviation (\({\sigma }_{{{{{{\rm{G}}}}}}}\)) on the signal transduced by \({T}_{{{{{{\rm{PT}}}}}}}\) and generate noisy voltage, \({V}_{{{{{{\rm{PSV}}}}}}}\). Finally, the MoS2 memtransistors used as the spiking neurons (\({T}_{{{{{{\rm{SN}}}}}}}\)) encrypt the noisy presynaptic information i.e., \({V}_{{{{{{\rm{PSV}}}}}}}\) into post-synaptic current spikes (\({I}_{{{{{{\rm{PSC}}}}}}}\)) using reconfigurable encoding threshold (\({V}_{{{{{{\rm{ET}}}}}}}\)). The remaining two MoS2 memtransistors, i.e., photo selector transistor (\({T}_{{{{{{\rm{PST}}}}}}}\)) and encoding selector transistor (\({T}_{{{{{{\rm{EST}}}}}}}\)) operate as the individual selector switches for the photosensing and the encoding operations, respectively.
In Fig. 1e, \({T}_{{{{{{\rm{PST}}}}}}}\) and \({T}_{{{{{{\rm{PT}}}}}}}\) are connected in series at the node \({N}_{3}\), \({T}_{{{{{{\rm{PT}}}}}}}\) and \({T}_{{{{{{\rm{WGNA}}}}}}}\) are connected in series at the node \({N}_{5}\), which is also connected to the local back-gate of \({T}_{{{{{{\rm{SN}}}}}}}\), and, finally, \({T}_{{{{{{\rm{EST}}}}}}}\) and \({T}_{{{{{{\rm{SN}}}}}}}\) are connected in series at the node \({N}_{10}\). The nodes \({N}_{2}\), \({N}_{4}\), \({N}_{6}\), and \({N}_{9}\), respectively, serve as the local back-gate terminals of \({T}_{{{{{{\rm{PST}}}}}}}\), \({T}_{{{{{{\rm{PT}}}}}}}\), \({T}_{{{{{{\rm{WGNA}}}}}}}\), and \({T}_{{{{{{\rm{EST}}}}}}}\), while node \({N}_{1}\) serves as the drain terminal of \({T}_{{{{{{\rm{PST}}}}}}}\), node \({N}_{8}\) serves as the drain terminal of \({T}_{{{{{{\rm{EST}}}}}}}\), and node \({N}_{7}\) serves as the common source terminal for \({T}_{{{{{{\rm{WGNA}}}}}}}\) and \({T}_{{{{{{\rm{SN}}}}}}}\). As shown in Fig. 1d, nodes \({N}_{2}\), \({N}_{4}\), \({N}_{6}\), and \({N}_{9}\) from the crypto engines in a given column are connected to common \({V}_{{{{{{\rm{N}}}}}}2}\), \({V}_{{{{{{\rm{N}}}}}}4}\), \({V}_{{{{{{\rm{N}}}}}}6}\) and \({V}_{{{{{{\rm{N}}}}}}9}\) lines, respectively, and nodes \({N}_{1}\), \({N}_{7}\), and \({N}_{8}\) from the crypto engines in a given row are connected to common \({V}_{{{{{{\rm{N}}}}}}1}\), \({V}_{{{{{{\rm{N}}}}}}7}\), and \({V}_{{{{{{\rm{N}}}}}}8}\) lines, respectively. This allows us to select any crypto engine corresponding to a given row and column. Note that the overlapping connections between the horizontal and vertical metal lines are separated lithographically by depositing an insulating layer of alumina (Al2O3) at the cross points as described in the Methods section.
Figure 1f–j shows an example experimental demonstration of sensing and ciphering. Note that the proposed security scheme aims at the “confidentiality” of the information. Information, for example, an 8 × 8 pixelated image of the letter ‘N’ (Fig. 1f) obtained by illuminating a blue light emitting diode (LED), is presented one-by-one to the corresponding 8 × 8 crossbar array of the crypto engines using the row and column select lines. Figure 1g shows the post-illumination photoconductance map obtained from the corresponding \({T}_{{{{{{\rm{PT}}}}}}}\), which is transformed into a noisy \({V}_{{{{{{\rm{PSV}}}}}}}\) map using the respective pre-programmed \({T}_{{{{{{\rm{WGNA}}}}}}}\), as shown in Fig. 1h, and presented to the corresponding \({T}_{{{{{{\rm{SN}}}}}}}\) to generate an encrypted \({I}_{{{{{{\rm{PSC}}}}}}}\) map as shown in Fig. 1i. The information is revealed by a decoder (Fig. 1j) through a voting process when a finite number (\(P\)) of 8 × 8 crypto engines communicate the encrypted information. As we will elucidate in the following sections, the decoding process requires an optimum number of voting mandate (\({M}_{{{{{{\rm{V}}}}}}}\)) that is determined by \(P\), \({V}_{{{{{{\rm{ET}}}}}}}\), and \({\sigma }_{{{{{{\rm{G}}}}}}}\) without the knowledge of which an eavesdropper requires a significant number of brute force trials (BFTs) for deciphering the information. In fact, the information remains concealed even if the eavesdropper has access to a trained deep neural network (DNN). The proposed attack model refers to wiretapping40.
Note that the monolayer MoS2 used in this study was grown epitaxially on a sapphire substrate using a metal-organic chemical vapor deposition (MOCVD) technique at 1000 0C by the 2D Crystal Consortium (2DCC). The monolayer film was then transferred using a PMMA-assisted wet transfer process41,42 from the growth substrate to the target application substrate, i.e., SiO2/p++-Si with predefined islands of Al2O3/Pt/TiN, for subsequent fabrication of the 8 × 8 crypto engines. Details on the fabrication of the back-gate islands, monolayer MoS2 synthesis, film transfer, fabrication of MoS2 memtransistors, and monolithic integration can be found in the Methods section. Each MoS2 memtransistor has a footprint (\(W\times L\)) of 5 µm × 1 µm. Given that we have used monolayer MoS2 as the channel material for the memtransistors, which are aggressively scalable, it is possible to reduce the hardware footprint even further.
While any ultra-thin-body semiconductor which is multifunctional, i.e., photosensitive and can be used to fabricate programmable field effect transistors (FETs) or memtransistors, is equally suitable for this demonstration, the use of MoS2 in our all-in-one IoT platform has several merits. First, MoS2 is the most advanced among other 2D materials in terms of scalable growth over a large area (wafer scale) as well as in terms of demonstration of high-performance FETs with on current > 250 µA/µm at ultra-short channel lengths43 with low device-to-device variability43,44,45, which are promising to meet the requirements set forth by the International Roadmap of Devices and Systems (IRDS)46. In addition, circuit and architecture level demonstrations of digital, analog, and radio frequency (RF) electronics based on 2D transistors are already available47,48,49,50,51, and emerging applications such as neuromorphic, optoelectronic, straintronic, hardware security, and biomimetic technologies exploiting the sensing, computing, and storage capabilities of 2D transistors have also been reported13,26,28,30,52,53,54,55,56,57,58,59,60,61. This work further advances the field of 2D material-based devices by demonstrating robust security features achievable under the same hardware infrastructure used for sensing, storage, and computing. Note that some of our earlier work has also shown the potential use of 2D materials in resolving rampant security vulnerabilities57,58,61,62.
Characterization of monolayer MoS2-based memtransistor
Figure 2a, b, respectively, show the transfer characteristics, i.e., source to drain current (\({I}_{{{{{{\rm{DS}}}}}}}\)) as a function of the local back-gate voltage (\({V}_{{{{{{\rm{BG}}}}}}}\)) at different drain biases (\({{{{{{\rm{V}}}}}}}_{{{{{{\rm{DS}}}}}}}\)), and output characteristics, i.e., \({I}_{{{{{{\rm{DS}}}}}}}\) versus \({V}_{{{{{{\rm{DS}}}}}}}\) for different \({{V}}_{{{{{{\rm{BG}}}}}}}\), of a representative MoS2 memtransistor. Figure 2c shows the device-to-device variation in the transfer characteristics of as-fabricated 64 MoS2 memtransistors used as \({T}_{{{{{{\rm{SN}}}}}}}\) corresponding to each of the 8 × 8 array of the crypto engines (see Supplementary Fig. 6a for the transfer characteristics of each of these 64 MoS2 memtransistors). Figure 2d shows the colormap of electron field effect mobility values (\({\mu }_{{{{{{\rm{FE}}}}}}}\)) extracted from the peak transconductance for these 64 MoS2 memtransistors with a mean of ~8 cm2V−1s−1 and a standard deviation of 3.1 cm2V−1s−1. Supplementary Fig. 6b–d, respectively, show similar colormaps on device-to-device variation in current on/off ratio (\({r}_{{{{{{\rm{ON}}}}}}/{{{{{\rm{OFF}}}}}}}\)), threshold voltage (\({V}_{{{{{{\rm{TH}}}}}}}\)) extracted at an iso-current of 100 nA/µm, and subthreshold slope (\({SS}\)) over 3 orders of magnitude change in \({I}_{{{{{{\rm{DS}}}}}}}\), with mean values of ~1 × 106, ~1.65 V, and ~355 mV/decade, respectively, and standard deviation values of ~1 × 106, ~0.42 V, and 85 mV/decade, respectively. Our \({\mu }_{{{{{{\rm{FE}}}}}}}\), \({r}_{{{{{{\rm{ON}}}}}}/{{{{{\rm{OFF}}}}}}}\), \({SS}\), and \({V}_{{{{{{\rm{TH}}}}}}}\) values and their corresponding device-to-device variations are on par with the state-of-the-art literature on large area grown MoS2. Also note that, in Fig. 2b, the on-state current in the representative MoS2 memtransistor reaches as high as ~30 μA/μm at \({V}_{{{{{{\rm{DS}}}}}}}\) = 5 V for an inversion charge carrier density of ~1 × 1013/cm2. While on-state performance has minimal impact on the operation of the crypto engine, these metrics confirm high-quality monolayer film growth using MOCVD, relatively damage-free film transfer, and clean device fabrication processes.
a Transfer characteristics, i.e., source to drain current (\({I}_{{{\rm{DS}}}}\)) versus back-gate voltage (\({V}_{{{\rm{BG}}}}\)) at different drain biases (\({V}_{{{\rm{DS}}}}\)), and (b) output characteristics, i.e., \({I}_{{{\rm{DS}}}}\) versus \({V}_{{{\rm{DS}}}}\) for different \({{V}}_{{{\rm{BG}}}}\), of a representative MoS2 memtransistor. c Transfer characteristics and (d) colormap of the distribution of electron field effect mobility values (\({\mu }_{{{\rm{FE}}}}\)) extracted from the peak transconductance of 64 as-fabricated MoS2 memtransistors used as spiking neurons (\({T}_{{{\rm{SN}}}}\)) corresponding to each of the 8 × 8 array of the crypto engines. e Post-programmed and (f) post-erased transfer characteristics of a representative MoS2 memtransistor when subjected to negative “Write” (\({V}_{{{\rm{P}}}}\)) and positive “Erase” (\({V}_{{{\rm{E}}}}\)) voltage pulses of different amplitudes applied to the local back-gate electrode, respectively, each for a duration of 100 ms. Non-volatile retention of 5 representative (g) post-programmed (\({G}_{{{\rm{P}}}}\)) and (h) post-erased (\({G}_{{{\rm{E}}}}\)) conductance states for 100 s. i Transfer characteristics for a representative monolayer MoS2 memtransistor before and after illumination from a blue LED with input currents ranging from \({I}_{{{\rm{LED}}}}\) = 0.02 mA (low-brightness) to \({I}_{{{\rm{LED}}}}\) = 20 mA (high-brightness) at different \({V}_{{{\rm{BG}}}}\) = \({V}_{{{\rm{illumin}}}}\) for \({t}_{{{\rm{illumin}}}}\) = 100 ms. j Colormap of the ratio of post-illumination conductance to dark conductance, \({r}_{{{\rm{PH}}}}\), extracted at \({V}_{{{\rm{BG}}}}\) = 0 V from (i) as a function of \({I}_{{{\rm{LED}}}}\) and \({V}_{{{\rm{illumin}}}}\). k Colormap of persistent photoconductivity (\({G}_{{{\rm{PH}}}}\)) measured at \({V}_{{{\rm{BG}}}}\) = 0 V when the MoS2 memtransistors used as sensory neurons (\({T}_{{{\rm{PT}}}}\)) corresponding to the 8 × 8 array of the crypto engines are exposed to 8 × 8 pixelated images of the letters ‘L’, ‘M’, ‘N’, and ‘P’, obtained through the LED illumination for \({t}_{{{\rm{illumin}}}}\) = 100 ms with \({V}_{{{\rm{illumin}}}}\)= −2 V. The bright pixels correspond to \({I}_{{{\rm{LED}}}}\) = 20 mA.
Next, we demonstrate the programming capability of our monolayer MoS2 memtransistors in any desirable conductance state with non-volatile memory retention characteristics. Figure 2e, f, respectively, show the post-programmed and post-erased transfer characteristics of a representative MoS2 memtransistor when subjected to negative “Write” (\({V}_{{{{{{\rm{P}}}}}}}\)) and positive “Erase” (\({V}_{{{{{{\rm{E}}}}}}}\)) voltage pulses of different amplitudes applied to the local back-gate electrode, each for a duration of \({\tau }_{{{{{{\rm{P}}}}}}/{{{{{\rm{E}}}}}}}\) = 1 s. The shift in the transfer characteristics can be attributed to charge trapping/detrapping at and near the MoS2/Al2O3 interface. A negative shift in the transfer characteristics with an increasing magnitude of \({V}_{{{{{{\rm{P}}}}}}}\) and positive shift with increasing magnitude of \({V}_{{{{{{\rm{E}}}}}}}\) are indicative of electron trapping and de-trapping in the local back-gate stack, respectively. Interestingly, the trapping and de-trapping processes were found to be non-volatile as evident from the retention measurements displayed in Fig. 2g, h for 5 representative post-programmed (\({G}_{{{{{{\rm{P}}}}}}}\)) and post-erased (\({G}_{{{{{{\rm{E}}}}}}}\)) conductance states, respectively, for 100 seconds. We also examined long-term memory retention for two representative analog conductance states for ~104 seconds, as shown in Supplementary Fig. 7. The memory ratio (\({MR}\)) between these two states was found to change from ~6 × 102 to ~2 × 102 following an exponential decay with a time constant of 7.6 × 103 s. The projected time before the \({MR}\) reaches 1, i.e., these two states become indistinguishable, was found to be ~14 h. The \({MR}\) can be reinstated by reprogramming the devices every few hours or as necessary. This will necessitate some peripheral timing circuits. Improving memory retention through the optimization of our back-gate stack can eliminate the need for extra peripherals. Similarly, Supplementary Fig. 8 shows the memory endurance for 2 × 103 cycles for two representative analog conductance states. \({MR}\) was found to change from ~7.5 to ~5 following a power-law decay with an exponent of ~ −0.1. The projected memory endurance before the \({MR}\) reaches 1 was found to be 5 × 108 cycles, which is comparable to the state-of-the-art FLASH memory devices.
Nevertheless, we exploit the analog nature of the conductance states achievable in MoS2 memtransistors for the realization of noisy synapses, i.e., \({T}_{{{{{{\rm{WGNA}}}}}}}\), with corresponding \({G}_{{{{{{\rm{WGNA}}}}}}}\) that follow random Gaussian distribution (in logarithmic scale). Supplementary Fig. 9 shows the device-to-device variation in the pre and post-programmed transfer characteristics and corresponding colormap of \(MR\) measured at \({V}_{{{{{{\rm{BG}}}}}}}\) = 0 V for 64 monolayer MoS2 memtransistors corresponding to our 8 × 8 array of the crypto engine when programmed with \({V}_{{{{{{\rm{P}}}}}}}\) = −10 V for \({t}_{{{{{{\rm{P}}}}}}}\) = 1 s. The mean and standard deviation values for \({MR}\) were found to be 2.8 × 105 and 8.7 × 105, respectively. Note that the inherent device-to-device variation in programming is significantly smaller compared to the look-up-table based variation introduced in the MoS2 memtransistors used as \({T}_{{{{{{\rm{WGNA}}}}}}}\) in the 8 × 8 array of the crypto engines. Finally, Supplementary Fig. 10 shows the programming and erasing energy expenditures (\({E}_{{{{{{\rm{P}}}}}}/{{{{{\rm{E}}}}}}}\)), which were found to be less than picojoules calculated based on \({E}_{{{{{{\rm{P}}}}}}/{{{{{\rm{E}}}}}}}=1/2{C}_{{{{{{\rm{G}}}}}}}{{V}_{{{{{{\rm{P}}}}}}/{{{{{\rm{E}}}}}}}}^{2}\), where \({C}_{{{{{{\rm{G}}}}}}}\) is the capacitance for the local back-gate.
Next, we demonstrate the adaptive photosensing capability of monolayer MoS2 memtransistors by exploiting the unique phenomenon of gate-tunable persistent photoconductivity. Figure 2i shows the transfer characteristics of a representative monolayer MoS2 memtransistor before and after illumination from a blue LED with input currents ranging from \({I}_{{{{{{\rm{LED}}}}}}}\)= 0.02 mA (low-brightness) to \({I}_{{{{{{\rm{LED}}}}}}}\) = 20 mA (high-brightness) at different \({V}_{{{{{{\rm{BG}}}}}}}\) = \({V}_{{{{{{\rm{illumin}}}}}}}\) for \({t}_{{{{{{\rm{illumin}}}}}}}\) = 1 s. Note that, instead of standard LASER illumination used to assess the photoresponsivity of monolayer MoS218, we have used an LED as the source of external optical stimuli since it represents a more realistic lighting ambience where most edge sensors will be deployed. Figure 2j shows the colormap of the ratio of post-illumination conductance to dark conductance, \({r}_{{{{{{\rm{PH}}}}}}}\), extracted at \({V}_{{{{{{\rm{BG}}}}}}}\) = 0 V from Fig. 2i as a function of \({I}_{{{{{{\rm{LED}}}}}}}\) and \({V}_{{{{{{\rm{illumin}}}}}}}\). Two distinctive types of photoresponse are seen in MoS2 memtransistors. For \({V}_{{{{{{\rm{illumin}}}}}}}\) > 0 V, i.e., illuminations in the on-state and in the subthreshold regime, \({r}_{{{{{{\rm{PH}}}}}}}\) = 1, whereas for \({V}_{{{{{{\rm{illumin}}}}}}}\) < 0 V, i.e., illuminations in the off-state, \({r}_{{{{{{\rm{PH}}}}}}}\) >> 1. This can be explained from the fact that during illumination in the on-state the photocarriers generated in the MoS2 channel are swept across by the applied \({V}_{{{{{{\rm{DS}}}}}}}\) and hence there is no persistent photocurrent beyond the optical exposure. However, for \({V}_{{{{{{\rm{illumin}}}}}}}\) < 0 V, persistent photoconductivity emerges as photocarriers get trapped at and near the MoS2/dielectric interface, leading to the shift in the post-illumination device characteristics. The detrapping process can take several hours. Higher \({I}_{{{{{{\rm{LED}}}}}}}\), more negative \({V}_{{{{{{\rm{illumin}}}}}}}\), and longer \({t}_{{{{{{\rm{illumin}}}}}}}\) naturally result in more photocarrier trapping and hence larger shifts in the device characteristics, leading to higher values of \({r}_{{{{{{\rm{PH}}}}}}}\). Supplementary Fig. 11 shows the colormap of \({r}_{{PH}}\) as a function of \({V}_{{{{{{\rm{illumin}}}}}}}\) and \({t}_{{{{{{\rm{illumin}}}}}}}\) for \({I}_{{{{{{\rm{LED}}}}}}}\) = 20 mA. Interestingly, \({r}_{{{{{{\rm{PH}}}}}}}\) values obtained for brighter LED illuminations at less negative \({V}_{{{{{{\rm{illumin}}}}}}}\) and shorter \({t}_{{{{{{\rm{illumin}}}}}}}\) can be obtained for dimmer LED illuminations at more negative \({V}_{{{{{{\rm{illumin}}}}}}}\) and for longer \({t}_{{{{{{\rm{illumin}}}}}}}\). This phenomenon of gate-tunable persistent photoconductivity can be exploited for adaptive sensing, which is a key requirement for edge sensors. Note that post-illumination MoS2 memtransistors can be reset back to their pre-illumination conditions by applying erase programming voltages, \({V}_{{{{{{\rm{E}}}}}}}\), to the local back-gate as described in the context of non-volatile memory capability of our all-in-one hardware platform.
Figure 2k shows the colormap of persistent photoconductivity (\({G}_{{{{{{\rm{PT}}}}}}}\)) measured at \({V}_{{{{{{\rm{BG}}}}}}}\) = 0 V when the \({T}_{{{{{{\rm{PT}}}}}}}\) corresponding to the 8 × 8 array of the crypto engines are exposed to 8 × 8 pixelated images of the letters, ‘L’, ‘M’, ‘N’, and ‘P’, obtained through LED illumination for \({t}_{{{{{{\rm{illumin}}}}}}}\) = 100 ms with \({V}_{{{{{{\rm{illumin}}}}}}}\) = −2 V. The bright pixels correspond to \({I}_{{{{{{\rm{LED}}}}}}}\) = 20 mA. Clearly, MoS2 memtransistors integrated with the crypto engines can accurately transcribe the optical information into an electrical response. See Supplementary Fig. 12 for the transcription of 8 × 8 pixelated images of the letters ‘L’, ‘M’, ‘N’, and ‘P’ for dimmer LED illuminations (\({I}_{{{{{{\rm{LED}}}}}}}\) = 2 mA) using different \({V}_{{{{{{\rm{illumin}}}}}}}\). This demonstration highlights the advantages of gate-tunability of persistent photoconductivity in achieving adaptation to the illumination levels similar to the rod and cone neurons found in the visual system of primates. Finally, Supplementary Fig. 13 shows the pre- and post-illumination transfer characteristics of 64 MoS2 memtransistors used as \({T}_{{{{{{\rm{PT}}}}}}}\) corresponding to each of the 8 × 8 crypto engines and the corresponding colormap of the ratio of post-illumination photoconductance to dark conductance (\({r}_{{{{{{\rm{PH}}}}}}}\)) measured at \({V}_{{{{{{\rm{BG}}}}}}}\) = 0 V. The mean and standard deviation values were found to be 1.6 × 104 and 3.1 × 104, respectively. The device-to-device variation in photoconductance had minimal effect on the encryption and decryption process. We would like to remind the readers that, here, “ information encryption” refers to the confidentiality of the encoded information.
Encryption using MoS2 memtransistor
Next, we illustrate the encryption process by utilizing the sensing, storage, and computing capabilities of MoS2 memtransistors demonstrated above and by using the circuit diagram shown in Fig. 1d, e. Supplementary Fig. 14 shows the input voltage waveforms applied to different nodes when any given crypto engine is selected for encoding. The encryption process comprises photosensing, information encoding, and erase cycles. \({V}_{{{{{{\rm{N}}}}}}1}\), \({V}_{{{{{{\rm{N}}}}}}2}\), \({V}_{{{{{{\rm{N}}}}}}6}\), and \({V}_{{{{{{\rm{N}}}}}}7}\) are held constant at 1 V, 5 V, 0 V and 0 V, respectively, throughout the encryption process. \({V}_{{{{{{\rm{N}}}}}}8}\) and \({V}_{{{{{{\rm{N}}}}}}9}\) are enabled only during the encoding cycle, with 1 V and 5 V applied to the respective nodes. Finally, \({V}_{{{{{{\rm{N}}}}}}4}\) cycles between \({V}_{{{{{{\rm{illumin}}}}}}}\) = −4 V, \({V}_{{{{{{\rm{encoding}}}}}}}\) = 0 V, and \({V}_{{{{{{\rm{erase}}}}}}}\) = 11 V during photosensing, encoding, and erase cycles, respectively. Note that \({V}_{{{{{{\rm{N}}}}}}2}\) = 5 V ensures that \({T}_{{{{{{\rm{PST}}}}}}}\) is biased in the deep on-state with orders of magnitude lower resistance than \({T}_{{{{{{\rm{PT}}}}}}}\) and \({T}_{{{{{{\rm{WGNA}}}}}}}\). Therefore, the \({V}_{{{{{{\rm{PSV}}}}}}}\) value obtained at node \({N}_{5}\) can be expressed using Eq. 1.
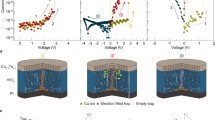
Here, \({G}_{{{{{{\rm{PT}}}}}}}\), and \({G}_{{{{{{\rm{WGNA}}}}}}}\) are, respectively, the conductance values of \({T}_{{{{{{\rm{PT}}}}}}}\) and \({T}_{{{{{{\rm{WGNA}}}}}}}\). Note that since both \({T}_{{{{{{\rm{PT}}}}}}}\) and \({T}_{{{{{{\rm{WGNA}}}}}}}\) are operated in their subthreshold regime, none of these memtransistors behave like a linear resistor, which is why the \({V}_{{{{{{\rm{PSV}}}}}}}\) value cannot be derived based on the standard model of a resistor divider network. Nevertheless, the 64 MoS2 memtransistors used as \({T}_{{{{{{\rm{WGNA}}}}}}}\) corresponding to each of the 8 × 8 crypto engines are randomly pre-programmed such that the \({V}_{{{{{{\rm{PSV}}}}}}}\) values obtained under dark condition follow a Gaussian distribution with a mean of 0.3 V and finite \({\sigma }_{{{{{{\rm{G}}}}}}}\) when measured using a back-gate voltage, \({V}_{{{{{{\rm{N}}}}}}6}\) = 0 V (see Supplementary Fig. 15 for the distribution of \({G}_{{{{{{\rm{WGNA}}}}}}}\) for different \({\sigma }_{{{{{{\rm{G}}}}}}}\)). While it can be argued that on-chip random number generators are more desirable solutions, these are often power-hungry and pose integration challenges. Instead, our approach offers inherent energy efficiency since the noise conductance values are already stored in \({T}_{{{{{{\rm{WGNA}}}}}}}\), reducing the energy burden during field operations although it adds area and storage overhead. Similarly, the 64 MoS2 memtransistors used as \({T}_{{{{{{\rm{PT}}}}}}}\) corresponding to each of the 8 × 8 crypto engines are pre-programmed such that the pre-illumination \({G}_{{{{{{\rm{PT}}}}}}}\) = 10 nS when measured using a back-gate voltage, \({V}_{{{{{{\rm{N}}}}}}2}\) = 0 V. To transcribe the LED illumination, \({T}_{{{{{{\rm{PT}}}}}}}\) is biased at \({V}_{{{{{{\rm{N}}}}}}2}\) = \({V}_{{{{{{\rm{illumin}}}}}}}\) = −2 V for \({t}_{{{{{{\rm{illumin}}}}}}}\) = 100 ms. If the pixel illumination is present (\({I}_{{{{{{\rm{LED}}}}}}}\) = 20 mA), the corresponding \({T}_{{{{{{\rm{PT}}}}}}}\) reaches \({G}_{{{{{{\rm{PT}}}}}}}\) ≈ 400 nS when measured post-illumination using \({V}_{{{{{{\rm{N}}}}}}2}\) = 0 V. Figure 3a shows the \({V}_{{{{{{\rm{PSV}}}}}}}\) values corresponding to each of the 64 crypto engines and Fig. 3b shows the corresponding colormaps for \({V}_{{{{{{\rm{PSV}}}}}}}\) for different values of \(\sigma\) when an 8 × 8 pixelated image of the letter ‘N’ is transduced using the corresponding \({T}_{{{{{{\rm{PT}}}}}}}\) and \({T}_{{{{{{\rm{WGNA}}}}}}}\). Under no-noise conditions, i.e., \({\sigma }_{G}\) = 0, \({V}_{{{{{{\rm{PSV}}}}}}}\) values, as expected, achieve two distinct levels, ~0.3 V and ~0.6 V, corresponding to dark and bright pixels in the image of the letter ‘N’ and the colormap of \({V}_{{{{{{\rm{PSV}}}}}}}\) shows accurate transduction of the optical information. For any finite \({\sigma }_{{{{{{\rm{G}}}}}}}\), both \({V}_{{{{{{\rm{PSV}}}}}}}\) levels become superimposed with random Gaussian noise. Higher \({\sigma }_{{{{{{\rm{G}}}}}}}\) values are translated into more variation in the two \({V}_{{{{{{\rm{PSV}}}}}}}\) levels in Fig. 3a and the corresponding colormaps in Fig. 3b, obscuring the sensed information.
a Pre-synaptic voltage, \({V}_{{{\rm{PSV}}}}\). b Colormaps of \({V}_{{{\rm{PSV}}}}\). c Post-synaptic current, \({I}_{{{\rm{PSC}}}}\). d Colormaps of \({I}_{{{\rm{PSC}}}}\) for different values of noise standard deviation, \({\sigma }_{{{\rm{G}}}}\), when an 8 × 8 pixelated image of the letter ‘N’ is sensed and transduced using the corresponding \({T}_{{{\rm{PT}}}}\), \({T}_{{{\rm{WGNA}}}}\), and \({T}_{{{\rm{SN}}}}\).
The final stage of the encryption process is performed by the MoS2 memtransistors used as \({T}_{{{{{{\rm{SN}}}}}}}\), which transforms the \({V}_{{{{{{\rm{PSV}}}}}}}\) into a corresponding \({I}_{{{{{{\rm{PSC}}}}}}}\). Note that \({V}_{{{{{{\rm{N}}}}}}9}\) = 5 V ensures that \({T}_{{{{{{\rm{EST}}}}}}}\) is biased in the deep on-state with orders of magnitude lower resistance than \({T}_{{{{{{\rm{SN}}}}}}}\), allowing \({I}_{{{{{{\rm{PSC}}}}}}}\) to be determined by \({T}_{{{{{{\rm{SN}}}}}}}\) and hence \({V}_{{{{{{\rm{PSV}}}}}}}\). Also, note that all 64 MoS2 memtransistors used as \({T}_{{{{{{\rm{SN}}}}}}}\) are pre-programmed such that their encoding threshold is at \({V}_{{{{{{\rm{ET}}}}}}}\) = 0.5 V (see Supplementary Fig. 16 for the transfer characteristics of a representative \({T}_{{{{{{\rm{SN}}}}}}}\)). This ensures that the \({V}_{{{{{{\rm{PSV}}}}}}}\) values obtained in Fig. 3a are primarily subthreshold with occasional threshold crossing events. In other words, for \({V}_{{{{{{\rm{PSV}}}}}}}\) < \({V}_{{{{{{\rm{ET}}}}}}}\), \({T}_{{{{{{\rm{SN}}}}}}}\) does not invoke any observable current response greater than the noise floor of the measurement (~1 pA/µm). Figure 3c shows the \({I}_{{{{{{\rm{PSC}}}}}}}\) values obtained from \({T}_{{{{{{\rm{SN}}}}}}}\) corresponding to each of the 8 × 8 crypto engines and Fig. 3d shows the corresponding colormaps for \({I}_{{{{{{\rm{PSC}}}}}}}\) for different \({\sigma }_{{{{{{\rm{G}}}}}}}\) for the letter ‘N’. As evident, for lower \({\sigma }_{{{{{{\rm{G}}}}}}}\) values, there are few if any threshold crossing events, resulting in sporadic bright pixels in the 8 × 8 encrypted image of the letter ‘N’, whereas for higher \({\sigma }_{{{{{{\rm{G}}}}}}}\) values, there are more frequent threshold crossing events, resulting in the greater number of bright pixels in the 8 × 8 encrypted image of the letter ‘N’. Nevertheless, the \({I}_{{{{{{\rm{PSC}}}}}}}\) map constitute the encoded information for the letter ‘N’. Note that, except for \({T}_{{{{{{\rm{PT}}}}}}}\), none of the other MoS2 memtransistors corresponding to the crypto engine are biased in their deep off-state and hence these memtransistors do not encounter any photogating effect.
Encryption strenth of encoded information
To analyze the strength of the encryption process, we define true positive (TP) as an event when a bright pixel in the encoded image corresponds to a bright pixel in the original image and false positive (FP) as an event when a bright pixel in the encoded image corresponds to a dark pixel in the original image. The likelihood of identifying the letter ‘N’ by an eavesdropper from the encrypted image will, therefore, be determined by the detectivity (\(D\)), which is defined as \(D={p}_{{{{{{\rm{TP}}}}}}}-{p}_{{{{{{\rm{FP}}}}}}}\), where \({p}_{{{{{{\rm{TP}}}}}}}\) is the probability of TP and \({p}_{{{{{{\rm{FP}}}}}}}\) is the probability of FP. Colormaps in Fig. 4a–c, respectively, show \({p}_{{{{{{\rm{TP}}}}}}}\), \({p}_{{{{{{\rm{FP}}}}}}}\), and \(D\) as a function of \({\sigma }_{{{{{{\rm{G}}}}}}}\) obtained by repeating the experiments \(P\) = 50 times, which represents the population strength, and Fig. 4d shows the corresponding population means. Note that the population means for \(D\) exhibit a non-monotonic behavior. At a low noise level, there is hardly any FP, i.e., low \({p}_{{{{{{\rm{FP}}}}}}}\), but the likelihood of detecting the letter ‘N’ remains low due to limited threshold crossing events for the original bright pixels, i.e., low \({p}_{{{{{{\rm{TP}}}}}}}\). At a high noise level, both bright and dark pixels corresponding to the original image cross the spiking threshold, resulting in high \({p}_{{{{{{\rm{TP}}}}}}}\) and \({p}_{{{{{{\rm{FP}}}}}}}\) and, therefore, low \(D\). However, at an intermediate noise, the detectivity reaches its maximum value. Figure 4e shows the number of brute force trials (BFTs) by the eavesdropper necessary to identify the letter ‘N’ as a function of \({\sigma }_{{{{{{\rm{G}}}}}}}\). Note that we computed BFT = \(1/{D}^{S}\), where \(S\) = 8 × 8 = 64 is the size of the image. The number of BFTs is found to be significantly high irrespective of \({\sigma }_{{{{{{\rm{G}}}}}}}\). Furthermore, the number of BFTs increases exponentially with \(S\) (see Supplementary Fig. 17). Therefore, the encryption can be considered to be secure from an eavesdropper with finite resources. Figure 4f shows the average energy expenditure by the crypto engines (\({E}_{{{{{{\rm{encrypt}}}}}}}\)) for the encryption of the letter ‘N” as a function of \({\sigma }_{{{{{{\rm{G}}}}}}}\) calculated using Eq. 2.
Here, \({I}_{{{{{{\rm{N}}}}}}1{{{{{\rm{N}}}}}}7,i}\) and \({I}_{{{{{{\rm{N}}}}}}8{{{{{\rm{N}}}}}}7,i}\) are the currents flowing through the sensing and encoding units, respectively. Note that the energy expenditure was found to be less than a few hundred picojoules per engine even for the highest \({\sigma }_{{{{{{\rm{G}}}}}}}\). See Supplementary Note 1 for the energy expenditure comparison with other competing technologies.
Colormaps of the likelihood, or probability, of (a) true positive (\({p}_{{{\rm{TP}}}}\)), (b) false positive (\({p}_{{{\rm{FP}}}}\)), and (c) detectivity (\(D={p}_{{{\rm{TP}}}}-{p}_{{{\rm{FP}}}}\)) as a function of \({\sigma }_{{{\rm{G}}}}\) for \(P\)= 50 encoders. d Corresponding population means. True positive (TP) is an event when a bright pixel in the encoded image corresponds to a bright pixel in the original image, and false positive (FP) is an event when a bright pixel in the encoded image corresponds to a dark pixel in the original image. e The number of brute force trials (BFTs) by the eavesdropper necessary to identify the letter ‘N’ as a function of \({\sigma }_{{{\rm{G}}}}\). Note that BFT = \(1/{D}^{S}\), where \(S\) = 8 × 8 = 64 is the size of the image. f The average energy expenditure for the encryption process as a function of \({\sigma }_{{{\rm{G}}}}\). g A deep neural network (DNN) trained to recognize the MNIST data set for digit classification. The training and testing sets consisted of 60,000 and 10,000 images, respectively. h Representative MNIST images with white Gaussian noise (WGN) of different standard deviations (\(\sigma\)) binarized at a threshold of 1.5, mimicking our MoS2 memtransistor-based encryption process. i Average inference accuracy for 10,000 encrypted images as a function of \(\sigma\) and the number of hidden layers (\({N}_{{{\rm{Layer}}}}\)). Irrespective of \(\sigma\), the inference accuracy remains low, indicating the robustness of our bio-inspired encryption to trained DNNs.
The encryption strength is also tested assuming that the eavesdropper has access to a trained artificial DNN, with the information being communicated being an encrypted MNIST data set for digit classification. DNNs have shown remarkable success in various applications ranging from image recognition and pattern classification to defeating professional players in the game of “Go”63. DNNs consist of one input layer, one output layer, and many hidden layers (\(N\)), with each containing a certain number of neurons. The neurons in a layer and its consecutive layer are connected by synapses and the strength of the synapses, i.e., synaptic weights, are trained using back-propagation algorithms. The deeper the network is, i.e., for higher \(N\), the more complex datasets that can be trained, and with better accuracy. Figure 4g shows the schematic of a DNN trained to recognize the MNIST data set. The input layer consists of 784 neurons where the normalized pixel values of the images (28 × 28 pixels) in the MNIST dataset are sent and the output layer consists of 10 neurons that correspond to digits from 0 to 9. Output neurons perform the
SoftMax activation function, and the winner is determined based on the maximum value. We have used \({N}_{{{{{{\rm{Layer}}}}}}}\) = 1, 2, 3, 4 hidden layers with 300, 200, 100, and 50 neurons in the corresponding layers, respectively. The gradient descent algorithm is used to train the DNN using 60,000 images with a learning rate of 0.003 and rectified linear unit (ReLU) as the activation function, and the remaining 10,000 images are used for testing the inference accuracy. Supplementary Fig. 18 shows the training and inference accuracy as a function of \({N}_{{{{{{\rm{Layer}}}}}}}\) and the number of epochs. Training accuracies of 100% and testing accuracies of >98% were achieved beyond 50 epochs irrespective of \({N}_{{{{{{\rm{Layer}}}}}}}\). Note that higher \({N}_{{{{{{\rm{Layer}}}}}}}\) values achieve better training and inference accuracies with a lesser number of epochs. Next, we added white Gaussian noise (WGN) to 10,000 MNIST testing images and binarized them at a threshold of 1.5, mimicking the encryption process of our MoS2 memtransistor-based crypto engines. Figure 4h shows some examples of encoded MNIST images for different standard deviations (\(\sigma\)) of the WGN. Figure 4i shows the inference accuracy for the encrypted images as a function of \(\sigma\) for different \({N}_{{{{{{\rm{Layer}}}}}}}\). Interestingly, the accuracy values are found to be significantly low irrespective of \(\sigma\) and \({N}_{{{{{{\rm{Layer}}}}}}}\), indicating the robustness of our proposed encryption scheme to trained DNNs.
Voting-based decryption process
In order to retrieve the information, we adopt a population voting-based algorithm. We assume that the encoded images of the letter ‘N’ are transmitted over different communication channels by \({P}\) encoders, each comprising 8 × 8 array of the crypto engines. The receiver at the other end receives \({P}\) encoded images and counts the number of votes corresponding to each pixel. In our experiments, this was accomplished by encoding the same information \({P}\) times by the same 8 × 8 array of the crypto engines but using different \({G}_{{{{{{\rm{WGNA}}}}}}}\) every time. Figure 5a shows the vote counts for each pixel when \({P}\) = 50 for different \({\sigma }_{{{{{{\rm{G}}}}}}}\). A vote is registered when the encoded pixel is bright, i.e., \({I}_{{{{{{\rm{PSC}}}}}}}\) > 350 pA. The vote is considered to be a true positive vote (TPV) if the corresponding pixel in the original image is also bright, whereas the vote is considered to be a false positive vote (FPV) if the corresponding pixel in the original image is dark. Figure 5b, c, respectively, show the probability distribution for TPVs (\({p}_{{{{{{\rm{TPV}}}}}}}\)) and FPVs (\({p}_{{{{{{\rm{FPV}}}}}}}\)) for \({P}\) = 50 for different \({\sigma }_{{{{{{\rm{G}}}}}}}\). At low noise levels, the probability of crossing the encoding threshold (\({V}_{{{{{{\rm{ET}}}}}}}\)) is low and hence only a few encoders fire simultaneously, resulting in lower expected number of encoders for TPV, i.e., \(\left\langle {N}_{{{{{{\rm{TPV}}}}}}}\right\rangle {=}\mathop{\sum }\nolimits_{{n}{=}{1}}^{{P}}{n}{{p}}_{{{{{{\rm{TPV}}}}}}}{(}{n}{)}\). The expected number of encoders for FPV, i.e., \(\left\langle {N}_{{{\rm{FPV}}}}\right\rangle =\!\mathop{\sum }\nolimits_{n=1}^{P}n{p}_{{{\rm{FPV}}}}(n)\), is even lower. Similarly, at high noise levels, the probability of crossing the threshold of the encoder is high and hence more encoders fire synchronously, resulting in larger \(\left\langle {N}_{{{{{{\rm{TPV}}}}}}}\right\rangle\) and \(\left\langle {N}_{{{{{{\rm{FPV}}}}}}}\right\rangle\). However, as seen in Fig. 5b, c, for any \({\sigma }_{{{{{{\rm{G}}}}}}}\), \(\left\langle {N}_{{{{{{\rm{TPV}}}}}}}\right\rangle\) is higher than \(\left\langle {N}_{{{{{{\rm{FPV}}}}}}}\right\rangle\). Supplementary Fig. 19 shows the decoding of the images of the letter ‘N’ for different \({\sigma }_{{{{{{\rm{G}}}}}}}\) for different number of mandated votes (\({M}_{{{{{{\rm{V}}}}}}}\)) to mark a pixel as bright for \({P}\) = 50. Figure 5d shows the corresponding colormap of the correlation coefficient (\({CC}\)) between the original and the decrypted image as a function of \({\sigma }_{{{{{{\rm{G}}}}}}}\) and \({M}_{{{{{{\rm{V}}}}}}}\). Note that, for a given \({\sigma }_{{{{{{\rm{G}}}}}}}\), there is an optimum range for \({M}_{{{{{{\rm{V}}}}}}}\), that allows accurate decryption of the encoded image, i.e., \({CC}\) = 1. Supplementary Fig. 20 shows similar results for \({CC}\) when different encoding population sizes (\({P}\)) are used. As expected, the optimum number of \({M}_{{{{{{\rm{V}}}}}}}\) for accurate decryption is found to be different for similar \({\sigma }_{{{{{{\rm{G}}}}}}}\). Therefore, without the prior knowledge of the \({\sigma }_{{{{{{\rm{G}}}}}}}\) and \({P}\) used by the biomimetic encoder, it is difficult to decode the information.
a Number of votes corresponding to each pixel of the encoded images of the letter ‘N’ received from \(P\) = 50 encoders for different \({\sigma }_{{{\rm{G}}}}\). A vote is registered when the encoded pixel is bright, i.e., \({I}_{{{\rm{PSC}}}}\) > 350 pA. The vote is a true positive vote (TPV) if the corresponding pixel in the original image is also bright, whereas the vote is a false positive vote (FPV) if the corresponding pixel in the original image is dark. Probability distribution for (b) TPVs (\({p}_{{{\rm{TPV}}}}\)) and (c) FPVs (\({p}_{{{\rm{FPV}}}}\)) corresponding to (a). Insets show the expected number of TPV, i.e., \(\left\langle {N}_{{{\rm{TPV}}}}\right\rangle =\mathop{\sum }\nolimits_{n=1}^{P}n{p}_{{{\rm{TPV}}}}(n)\), and FPV, i.e., \(\left\langle {N}_{{{\rm{FPV}}}}\right\rangle =\!\mathop{\sum }\nolimits_{n=1}^{P}n{p}_{{{\rm{FPV}}}}(n)\). d The colormap of the correlation coefficient (CC) between the original and the decrypted image images of the letter ‘N’ as a function of \({\sigma }_{{{\rm{G}}}}\) and \({M}_{{{\rm{V}}}}\) when encryption is done by \(P\) = 50 encoders with encoding thresholds of \({V}_{{{\rm{ET}}}}\)= 0.5 V. Here, \({M}_{{{\rm{V}}}}\) is the minimum number of votes required to mark a pixel as bright. e The colormap of CC between the original and decrypted images of the letter ‘N’ as a function of \({V}_{{{\rm{ET}}}}\) and \({M}_{{{\rm{V}}}}\) for \({\sigma }_{{{\rm{G}}}}=\) 0.4 V and \(P\) = 50. Without prior knowledge of \({\sigma }_{{{\rm{G}}}}\), \(P\), and \({V}_{{{\rm{ET}}}}\) it is difficult to determine \({M}_{{{\rm{V}}}}\) and hence decode the information.
The strength of encoding can be further enhanced by exploiting the programming capability of our MoS2 memtransistors. Here we reconfigure the encoding threshold (\({V}_{{{{{{\rm{ET}}}}}}}\)) in a manner similar to neuroplasticity in biological neurons allowing adaptation to changing environments and stimuli. Supplementary Fig. 21 shows the encryption of the letter ‘N’ by encoders with different \({V}_{{{{{{\rm{ET}}}}}}}\) for different \({{\sigma }}_{{{{{{\rm{G}}}}}}}\). As obvious, if \({{V}}_{{{{{{\rm{PSV}}}}}}}{ > }\,{{V}}_{{{{{{\rm{ET}}}}}}}\), the encryption process is pointless, or, in other words, the communication is insecure. For \({{V}}_{{{{{{\rm{ET}}}}}}}\) values slightly greater than \({{V}}_{{{{{{\rm{PSV}}}}}}}\), there are more threshold crossing events even for low \({{\sigma }}_{{{{{{\rm{G}}}}}}}\), whereas for \({{V}}_{{{{{{\rm{ET}}}}}}}\) values further from \({{V}}_{{{{{{\rm{PSV}}}}}}}\), there are limited threshold crossing events even for high \({{\sigma }}_{{{{{{\rm{G}}}}}}}\). Figure 5e shows the colormap of \({CC}\) between the original and decrypted images of the letter ‘N’ as a function of \({{V}}_{{{{{{\rm{ET}}}}}}}\) and \({{M}}_{{{{{{\rm{V}}}}}}}\) for \({{\sigma }}_{{{{{{\rm{G}}}}}}}=\) 0.8 V and \({P}\) = 50 (see Supplementary Fig. 22 for similar results with different \({{\sigma }}_{{{{{{\rm{G}}}}}}}\)). Clearly, the optimum \({{M}}_{{{{{{\rm{V}}}}}}}\) for accurate decryption is found to be different for different \({{V}}_{{{{{{\rm{ET}}}}}}}\). Therefore, not only \({{\sigma }}_{{{{{{\rm{G}}}}}}}\) and \({P}\), but also prior knowledge of \({V}_{{{{{{\rm{ET}}}}}}}\) is required for decoding the information, which makes the system more robust from the eavesdropper. However, to achieve on-field reconfiguration capability, some peripheral circuits will be necessary for our integrated crypto engines, for example, the clocking signal for the MoS2 memtransistor based \({T}_{{{{{{\rm{PT}}}}}}}\), the gate-voltages necessary to randomly program the MoS2 memtransistor based \({{T}}_{{{{{{\rm{WGNA}}}}}}}\), and the gate voltages necessary to program the encoding threshold for the MoS2 memtransistor based \({{T}}_{{{{{{\rm{SN}}}}}}}\). Finally, the reader may be interested in knowing the impact of environmental noise, temperature, etc., on the encryption process. We have found that the device-to-device variation is dominant compared to environmental noise and that it has insignificant impact on the encryption process. Similarly, small variations in temperature are expected to have minimal impact on the proposed crypto engine.
Discussion
In conclusion, we have experimentally demonstrated a monolithically integrated and multi-pixel all-in-one hardware IoT platform based on programmable and multifunctional MoS2 memtransistors which is capable of sensing, storing, and securing information. Since a single material and similar device structures are used for our demonstration, the hardware investment is minimal. The average energy expenditure by each crypto engine was also found to be low, in the range of a few hundred picojoules, as we have primarily exploited the subthreshold regime of memtransistor operation. The encrypted information is found to be secure from an adversary with access to advanced machine learning capabilities such as trained DNNs. The decryption of the encrypted information relies on population voting. Overall, our platform shows the capability of near-sensor security by exploiting in-memory bio-inspired computing.
Methods
Fabrication of local back-gate islands
The local back-gate islands were fabricated on a commercially-bought substrate (285 nm SiO2 on p++-Si). The substrate was spin-coated with a bilayer photoresist consisting of Lift-Off-Resist (LOR 5A) and Series Photoresist (SPR 3012), which were then baked at 185 °C for 2 minutes and 95 °C for 1 minute, respectively. The bilayer photoresist was then exposed using a Heidelburg Maskless Aligner (MLA 150) to define the islands and developed using MF CD26 microposit, followed by a de-ionized (DI) water rinse for 75 and 60 seconds respectively. The local back-gate island electrodes (20/50 nm TiN/Pt) were deposited using reactive sputtering. The photoresist was then removed using acetone and Photo Resist Stripper (PRS 3000) and cleaned using 2-propanol (IPA) and DI water. An atomic layer deposition (ALD) process was then implemented to grow 50 nm Al2O3 uniformly across the entire substrate, including the island regions. To access the individual Pt back-gate electrodes, etch patterns were defined using the same bilayer photoresist (LOR 5A and SPR 3012) used previously. The bilayer photoresist was then again exposed using the MLA 150 and developed using MF CD26 microposit. The 50 nm Al2O3 was subsequently dry etched using a BCl3 reactive ion etch chemistry at 5 °C for a total of 80 s; this process was split into four 20 s etches to minimize heating in the substrate and thus ensure a uniform etch rate/depth. The photoresist was then removed to give access to the individual Pt electrodes.
Monolayer MoS2 Film Growth
Monolayer MoS2 was obtained from the Pennsylvania State University 2D Crystal Consortium (2DCC)64. It was deposited on an epi-ready 2” c-sapphire substrate by metal-organic chemical vapor deposition (MOCVD). An inductively heated graphite susceptor equipped with wafer rotation in a cold-wall horizontal reactor was used to achieve uniform monolayer deposition as previously described65. Molybdenum hexacarbonyl (Mo(CO)6) and hydrogen sulfide (H2S) were used as the precursors. Mo(CO)6 was maintained at 10 °C and 950 Torr in a stainless-steel bubbler, which was used to deliver 0.036 sccm of the metal precursor for the growth, while 400 sccm of H2S was used. MoS2 deposition was carried out at 1000 °C and 50 Torr in H2 ambient, and monolayer growth was achieved in 18 min. The substrate was first heated to 1000 °C in H2 and maintained for 10 min before the growth was initiated. After growth the substrate was cooled in H2S to 300 °C to inhibit decomposition of the MoS2 films.
MoS2 film transfer to local back-gate islands
To fabricate the MoS2 memtransistors, the as-grown monolayer MoS2 film was transferred from the sapphire growth substrate to the SiO2/p++-Si substrate with local back-gate islands using a PMMA (polymethyl-methacrylate) assisted wet transfer process. PMMA 495 A6 resist was spun onto the growth substrate at 4000 RPM for 45 s and allowed to sit overnight to ensure good PMMA/MoS2 adhesion. The edges of the spin-coated film were then scratched using a razor blade and the substrate was immersed into a 2 M NaOH solution kept at 90 °C. Capillary action served to draw the NaOH solution to the PMMA/substrate interface, separating the hydrophobic PMMA/MoS2 from the hydrophilic sapphire substrate. Note that scratching the edges of the film served to aid this process via removing any PMMA beading that may have been formed at the edge of the substrate during spinning and shortening the distance for the solution to penetrate. The detached film was retrieved from the NaOH bath using a clean glass slide and rinsed three times in separate DI water baths (15 min each). It was then retrieved from the final bath using the prepared SiO2/p++-Si substrate with local back-gate islands and baked at 50 °C and 70 °C for 10 min each to remove moisture and promote adhesion. Finally, the PMMA supporting layer was removed using an acetone bath and the substrate was cleaned using IPA.
Fabrication of monolayer MoS2 memtransistor
To define the channel regions for the memtransistors, the sample was first spin-coated with PMMA 950 A6 at 4000 RPM for 45 s and then baked at 180 °C for 90 s. Electron-beam (e-beam) lithography was used to pattern the resist, which was developed using a 1:1 mixture of 4-methyl-2-pentanone (MIBK) and IPA for 60 s and pure IPA for 45 s. The defined channels were separated via dry etching using a sulfur hexafluoride (SF6) reactive ion etch chemistry at 5 °C for 30 s. Following the etch step, the sample was rinsed in acetone for 30 min to remove the remaining photoresist, followed by an IPA bath to clean the sample. To define the source and drain contacts, sample was spin-coated with methyl methacrylate (MMA) and baked at 150 °C for 90 s before applying PMMA A3, which was baked 185 °C for 90 s. Both resists were spun at 4000 RPM for 45 s. E-beam lithography was used to pattern the source and drain contacts, and development was again performed using a 1:1 mixture of MIBK and IPA for 60 s and pure IPA for 45 s. Note that this development process allowed for the formation of a significant undercut in the bilayer resist, making subsequent metal deposition/liftoff easy. 40 nm of nickel (Ni) and 30 nm of gold (Au) were deposited using e-beam evaporation. Finally, lift-off of the evaporated material was performed by immersing the sample in acetone for 30 min and in IPA for 15 min. In the final design, each local back-gate island contained one memtransistor to allow for individual gate control.
Monolithic integration
Each crypto engine of our multi-pixel (8 × 8) hardware consists of 5 MoS2 memtransistors, as shown using the circuit schematic in Fig. 1d. To define the connections between the respective nodes of \({T}_{{{{{{\rm{PST}}}}}}}\), \({T}_{{{{{{\rm{PT}}}}}}}\), \({T}_{{{{{{\rm{WGNA}}}}}}}\), \({T}_{{{{{{\rm{EST}}}}}}}\), and \({T}_{{{{{{\rm{SN}}}}}}}\), the substrate was spin-coated with MMA and PMMA, followed by e-beam lithography and development using a 1:1 mixture of MIBK and IPA, e-beam evaporation of 60 nm of Ni and 30 nm of Au, and, finally, rinsing away the resist using acetone and IPA. All column-select metal lines were defined during this lithography step. The row-select lines were also defined except for the regions, where they crossover the column-select lines. To electrically isolate the column- and row-select lines, the substrate was again spin-coated with MMA and PMMA, followed by e-beam lithography and e-beam evaporation 80 nm of insulating alumina (Al2O3) at the cross-points. Finally, another lithography step was performed, followed by the deposition of 60 nm of Ni and 30 nm of Au to connect the row-select lines bridging over the cross-points.
Electrical characterization
Electrical characterization of the fabricated devices was performed using n automated probe station (Cascade SUMMIT200) under atmospheric conditions using a Keysight B1500A parameter analyzer. We have used our automated probe station for the readout, i.e., the probes move from one set of select lines to the next to collect the data. The entire encryption process is, therefore, automated without the need for any human intervention making the demonstration real-time. See Supplementary Video 1 for a representative recording.
Data availability
Relevant data supporting the key findings of this study are available within the article and the Supplementary Information file. All raw data generated during the current study are available from the corresponding authors upon request.
Code availability
The codes used for plotting the data are available from the corresponding authors on reasonable request.
References
Verton, D. & Brownlow, J. Black ice: The invisible threat of cyber-terrorism. (Osborne, 2003).
Alfaleh, F., Alfehaid, H., Alanzy, M. & Elkhediri, S. in 2019 2nd International Conference on Computer Applications & Information Security (ICCAIS). 1-4 (IEEE).
Katz, J. & Lindell, Y. Introduction to modern cryptography. (CRC press, 2014).
Diffie, W. & Hellman, M. New directions in cryptography. IEEE Trans. Inf. Theory 22, 644–654 (1976).
Rompel, J. in Proceedings of the twenty-second annual ACM symposium on Theory of computing. 387–394 (ACM).
Alom, M. Z. & Taha, T. M. in 2017 International Joint Conference on Neural Networks (IJCNN). 3830–3837 (IEEE).
Banerjee, U. & Chandrakasan, A. P. in 2021 IEEE Custom Integrated Circuits Conference (CICC). 1–2 (IEEE).
Benaissa, M. Throughput/area-efficient ECC processor using Montgomery point multiplication on FPGA. IEEE Trans. Circuits Syst. II: Express Briefs 62, 1078–1082 (2015).
Choi, P., Lee, M.-K., Kim, J.-H. & Kim, D. K. Low-complexity elliptic curve cryptography processor based on configurable partial modular reduction over NIST prime fields. IEEE Trans. Circuits Syst. II: Express Briefs 65, 1703–1707 (2017).
Khan, Z. U. & Benaissa, M. High-Speed and Low-Latency ECC Processor Implementation Over GF ($2^{m}) $ on FPGA. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 25, 165–176 (2016).
Bai, X., Jiang, L., Dai, Q., Yang, J. & Tan, J. in 2017 IEEE Symposium on Computers and Communications (ISCC). 682–688 (IEEE).
Sha, K., Wei, W., Yang, T. A., Wang, Z. & Shi, W. On security challenges and open issues in Internet of Things. Future Gener. Computer Syst. 83, 326–337 (2018).
Das, S. et al. Transistors based on two-dimensional materials for future integrated circuits. Nat. Electron. 4, 786–799 (2021).
Yin, Z. et al. Single-layer MoS2 phototransistors. ACS nano 6, 74–80 (2012).
Wang, L. et al. Functionalized MoS2 nanosheet‐based field‐effect biosensor for label‐free sensitive detection of cancer marker proteins in solution. Small 10, 1101–1105 (2014).
Park, M. et al. MoS2‐based tactile sensor for electronic skin applications. Adv. Mater. 28, 2556–2562 (2016).
Arnold, A. J., Shi, T., Jovanovic, I. & Das, S. Extraordinary radiation hardness of atomically thin MoS2. ACS Appl. Mater. Interfaces 11, 8391–8399 (2019).
Mennel, L. et al. Ultrafast machine vision with 2D material neural network image sensors. Nature 579, 62–66 (2020).
Lopez-Sanchez, O., Lembke, D., Kayci, M., Radenovic, A. & Kis, A. Ultrasensitive photodetectors based on monolayer MoS2. Nat. Nanotechnol. 8, 497–501 (2013).
Ge, R. et al. Atomristor: Nonvolatile resistance switching in atomic sheets of transition metal dichalcogenides. Nano Lett. 18, 434–441 (2018).
Liu, C. et al. A semi-floating gate memory based on van der Waals heterostructures for quasi-non-volatile applications. Nat. Nanotechnol. 13, 404–410 (2018).
Wang, M. et al. Robust memristors based on layered two-dimensional materials. Nat. Electron 1, 130–136 (2018).
Seo, S. et al. Artificial optic-neural synapse for colored and color-mixed pattern recognition. Nat. Commun. 9, 5106 (2018).
Lee, D. et al. Multibit MoS2 photoelectronic memory with ultrahigh sensitivity. Adv. Mater. 28, 9196–9202 (2016).
Tian, H. et al. A dynamically reconfigurable ambipolar black phosphorus memory device. ACS Nano. 10, 10428–10435 (2016).
Sebastian, A., Das, S. & Das, S. An annealing accelerator for ising spin systems based on in-memory complementary 2D FETs. Adv. Mater. 34, 2107076 (2022).
Subbulakshmi Radhakrishnan, S., Sebastian, A., Oberoi, A., Das, S. & Das, S. A biomimetic neural encoder for spiking neural network. Nat. Commun. 12, 2143 (2021).
Jayachandran, D. et al. A low-power biomimetic collision detector based on an in-memory molybdenum disulfide photodetector. Nat. Electron. 3, 646–655 (2020).
Schranghamer, T. F., Oberoi, A. & Das, S. Graphene memristive synapses for high precision neuromorphic computing. Nat. Commun. 11, 5474 (2020).
Das, S., Dodda, A. & Das, S. A biomimetic 2D transistor for audiomorphic computing. Nat. Commun. 10, 3450 (2019).
Jiang, H. et al. A provable key destruction scheme based on memristive crossbar arrays. Nat. Electron. 1, 548–554 (2018).
Nili, H. et al. Hardware-intrinsic security primitives enabled by analogue state and nonlinear conductance variations in integrated memristors. Nat. Electron 1, 197–202 (2018).
Zhang, R. et al. Nanoscale diffusive memristor crossbars as physical unclonable functions. Nanoscale 10, 2721–2726 (2018).
Wang, Z. et al. Memristors with diffusive dynamics as synaptic emulators for neuromorphic computing. Nat. Mater. 16, 101–108 (2017).
Yao, P. et al. Face classification using electronic synapses. Nat. Commun. 8, 15199 (2017).
Ohno, T. et al. Short-term plasticity and long-term potentiation mimicked in single inorganic synapses. Nat. Mater. 10, 591–595 (2011).
Jiang, H. et al. A novel true random number generator based on a stochastic diffusive memristor. Nat. Commun. 8, 882 (2017).
Feldmann, J., Youngblood, N., Wright, C. D., Bhaskaran, H. & Pernice, W. H. All-optical spiking neurosynaptic networks with self-learning capabilities. Nature 569, 208–214 (2019).
Yin, L. et al. Synaptic silicon-nanocrystal phototransistors for neuromorphic computing. Nano Energy 63, 103859 (2019).
Wyner, A. D. The wire‐tap channel. Bell Syst. Tech. J. 54, 1355–1387 (1975).
Zhang, F., Erb, C., Runkle, L., Zhang, X. & Alem, N. Etchant-free transfer of 2D nanostructures. Nanotechnology 29, 025602 (2018).
Schranghamer, T. F., Sharma, M., Singh, R. & Das, S. Review and comparison of layer transfer methods for two-dimensional materials for emerging applications. Chem. Soc. Rev. 50, 11032–10054 (2021).
Smets, Q. et al. in 2019 IEEE International Electron Devices Meeting (IEDM). 23.22. 21-23.22. 24 (IEEE).
Lanza, M., Smets, Q., Huyghebaert, C. & Li, L. J. Yield, variability, reliability, and stability of two-dimensional materials based solid-state electronic devices. Nat. Commun. 11, 5689 (2020).
Sebastian, A., Pendurthi, R., Choudhury, T. H., Redwing, J. M. & Das, S. Benchmarking monolayer MoS2 and WS2 field-effect transistors. Nat. Commun. 12, 693 (2021).
Ashokbhai Patel, K., Grady, R. W., Smithe, K. K. H., Pop, E. & Sordan, R. Ultra-scaled MoS2 transistors and circuits fabricated without nanolithography. 2D Mater. 7, https://doi.org/10.1088/2053-1583/ab4ef0 (2019).
Wachter, S., Polyushkin, D. K., Bethge, O. & Mueller, T. A microprocessor based on a two-dimensional semiconductor. Nat. Commun. 8, 14948 (2017).
Yu, L. et al. Design, modeling, and fabrication of chemical vapor deposition grown MoS2 circuits with E-Mode FETs for large-area electronics. Nano Lett. 16, 6349–6356 (2016).
Sanne, A. et al. Radio frequency transistors and circuits based on CVD MoS2. Nano Lett. 15, 5039–5045 (2015).
Yu, L. et al. High-performance WSe2 complementary metal oxide semiconductor technology and integrated circuits. Nano Lett. 15, 4928–4934 (2015).
Tosun, M. et al. High-gain inverters based on WSe2 complementary field-effect transistors. ACS Nano. 8, 4948–4953 (2014).
Sebastian, A., Pannone, A., Radhakrishnan, S. S. & Das, S. Gaussian synapses for probabilistic neural networks. Nat. Commun. 10, 1–11 (2019).
Dodda, A. et al. Stochastic resonance in MoS2 photodetector. Nat. Commun. 11, 4406 (2020).
Arnold, A. J. et al. Mimicking Neurotransmitter release in chemical synapses via hysteresis engineering in MoS2 transistors. ACS Nano. 11, 3110–3118 (2017).
Nasr, J. R. et al. Low-power and ultra-thin MoS2 photodetectors on glass. ACS Nano. 14, 15440–15449 (2020).
Das, S. Two Dimensional Electrostrictive Field Effect Transistor (2D-EFET): A sub-60mV/decade steep slope device with high ON current. Sci. Rep. 6, 34811 (2016).
Wali, A., Ravichandran, H. & Das, S. A machine learning attack resilient true random number generator based on stochastic programming of atomically thin transistors. ACS Nano 15, 17804–17812 (2021).
Oberoi, A., Dodda, A., Liu, H., Terrones, M. & Das, S. Secure Electronics Enabled by Atomically Thin and Photosensitive Two-Dimensional Memtransistors. ACS Nano 15, 19815–19827 (2021).
Dodda, A. & Das, S. Demonstration of Stochastic Resonance, Population Coding, and Population Voting Using Artificial MoS2 Based Synapses. ACS Nano 15, 16172–16182 (2021).
Liu, H. et al. Spontaneous chemical functionalization via coordination of Au single atoms on monolayer MoS2. Sci. Adv. 6, eabc9308 (2020).
Wali, A. et al. Satisfiability Attack-Resistant Camouflaged Two-Dimensional Heterostructure Devices. ACS Nano 15, 3453–3467 (2021).
Dodda, A. et al. Graphene-based physically unclonable functions that are reconfigurable and resilient to machine learning attacks. Nat. Electron. 4, 364–374 (2021).
Liu, W. et al. A survey of deep neural network architectures and their applications. Neurocomputing 234, 11–26 (2017).
2DCC. 2d-crystal-consortium, https://www.mri.psu.edu/2d-crystal-consortium/user-facilities/thin-films/list-thin-film-samples-available
Xuan, Y. et al. Multi-scale modeling of gas-phase reactions in metal-organic chemical vapor deposition growth of WSe2. J. Crys Growth 527, https://doi.org/10.1016/j.jcrysgro.2019.125247 (2019).
Acknowledgements
Authors would like to acknowledge Shiva Subbulakshmi Radhakrishnan for his help with the DNN simulation. The work of A.D. and S.D. was partially supported by Army Research Office (ARO) through Contract Number W911NF1920338 and National Science Foundation (NSF) through a CAREER Award under grant no. ECCS-2042154. Authors also acknowledge the materials support from the National Science Foundation (NSF) through the Pennsylvania State University 2D Crystal Consortium–Materials Innovation Platform (2DCCMIP) under NSF cooperative agreement DMR-2039351.
Author information
Authors and Affiliations
Contributions
S.D. conceived the idea and designed the experiments. S.D., and A.D. performed the experiments, analyzed the data, discussed the results, agreed on their implications. N.T., and J.M.R. synthesized the MOCVD grown monolayer MoS2. All authors contributed to the preparation of the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Peer review
Peer review information
Nature Communications thanks Patrick Schaumont and the other anonymous reviewers for their contribution to the peer review of this work. Peer reviewer reports are available.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary information
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Dodda, A., Trainor, N., Redwing, J.M. et al. All-in-one, bio-inspired, and low-power crypto engines for near-sensor security based on two-dimensional memtransistors. Nat Commun 13, 3587 (2022). https://doi.org/10.1038/s41467-022-31148-z
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41467-022-31148-z
This article is cited by
-
Recent Advances in In-Memory Computing: Exploring Memristor and Memtransistor Arrays with 2D Materials
Nano-Micro Letters (2024)
-
The Roadmap of 2D Materials and Devices Toward Chips
Nano-Micro Letters (2024)
-
A memristor fingerprinting and characterisation methodology for hardware security
Scientific Reports (2023)
-
Ferroelectric-defined reconfigurable homojunctions for in-memory sensing and computing
Nature Materials (2023)
-
A two-dimensional mid-infrared optoelectronic retina enabling simultaneous perception and encoding
Nature Communications (2023)
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.