Abstract
Quantum key agreement is an important topic that the shared key must be negotiated equally by all participants, and any nontrivial subset of participants cannot fully determine the shared key. To date, the embed modes of subkey in all the previously proposed quantum key agreement protocols are based on either BB84 or entangled states. The research of the quantum key agreement protocol based on quantum search algorithms is still blank. In this paper, on the basis of investigating the properties of quantum search algorithms, we propose the first quantum key agreement protocol whose embed mode of subkey is based on a quantum search algorithm known as Grover’s algorithm. A novel example of protocols with 5 – party is presented. The efficiency analysis shows that our protocol is prior to existing MQKA protocols. Furthermore it is secure against both external attack and internal attacks.
Similar content being viewed by others
Introduction
Since the first quantum key distribution (QKD) protocol known as BB841 was proposed by Bennett and Brassard in 1984, quantum cryptography has been attracted more and more attention, and many kinds of schemes such as QKD2,3,4, quantum secret sharing (QSS)5,6,7,8,9, quantum direct communication(QDC)10,11,12,13, quantum privacy comparison (QPC)14,15, have been proposed. Especially, QKD has received wide attention because of its numerous applications in quantum communication. Different from the classic cryptography schemes, quantum protocols that are based on the principles of quantum mechanics, could provide unconditionally security. Hence, quantum cryptography is innately superior to the classic cryptography.
Anther very important topic named Quantum key agreement(QKA)16,17,18,19,20,21,22,23,24,25,26,27,28,29 also received widespread concerns. Compared with QKD protocols in which one participant distributes a predetermined secret key to the other participants, QKA protocols require that all participants need to negotiate mutually and equally to derive a common secret key, and any nontrivial subset of participants could not fully determine the target key. Furthermore, any unauthorized users cannot extract the key through illegal means. Hence, the justice and fairness can be better reflected in the procession of QKA protocols because all participants are involved in the selection of the target key K and their contribution to it are equal. In 2004, the firstly QKA protocol (ZZX protocol)16 based on Einstein - Podolsky - Rosen (EPR) pairs was proposed by Zhou, Zeng and Xiong. However, in 2009, Tsa and Hwang17 pointed out that ZZX protocol is not a fair QKA because one party could fully determine the target key without being detected, and they proposed an improvement one (TH protocol)18. Unfortunately, TH protocol is also not a really QKA because the shared key is produced based on random measurement results without negotiation. In 2004, based on maximally entangled states, Hsueh and Chen also proposed a QKA protocol (HC protocol)28. In 2011, Chong, Tsai and Hwang18 claimed that HC protocol is susceptible to eavesdropping attack and internal attacks. In 2010, Chong and Hwang proposed the first successful QKA protocol (CH protocol)19 based on BB84 by using the technique of delayed measurement. In 2013, Liu, Gao, Huang and Wen proposed the first secure multiparty quantum key agreement (MQKA) protocol (LGHW protocol)20 by utilizing single particles. In the same year, Sun, Zhang and Wang et al.29 improved the LGHW protocol and the efficiency is improved obviously. Subsequently, several QKA and MQKA21,22,23,24,25,26,27 protocols were proposed.
Furthermore, quantum search algorithms (QSA)30 are also a research focus in quantum theory, and are famous for the Grover’s algorithm. The target could be probabilistic found in an unsorted database by executing the Grover’s algorithm which is faster than the best known classical search algorithms. Grover’s algorithm plays an important role in quantum computation and quantum communication. Recently, based on the ideas of QSA, some quantum protocols, liking QSS6, QPC14 and QDC31,32, have been proposed.
As far as I know, all existing QKA protocols are based on either BB84 or entangled states, and the QKA protocol based on QSA has not yet appeared. The research of the QKA protocol based on QSA still is blank. This study proposes a MQKA protocol based on QSA for the first time. In the proposed scheme, the idea of quantum dense coding is used. Each participant encodes his or her secret key by a unitary operation, and makes a two-particle quantum measurement to extract the common key. The security and efficiency analysis shows that our protocol is prior to existing MQKA protocols. The rest of our paper is structured as follows. Section 2 introduces some notions and properties of QSA. Section 3 describes the presented protocol in detail, the correctness of it is showed, and a novel example with 5-party protocol is presented. Section 4 analyzes the proposed scheme and compares it to other schemes. Finally, the conclusion of this paper is given in section 5.
Results
Preliminaries
Here we tackle some notations and properties of the Quantum Search Algorithm (QSA) with two quantum particles input. Owing to that Grover’s QSA is one of the most famous of all the QSAs, we only discuss the notations and properties of it.
The Grover’s QSA can be described as follows. Let the database be a two-particle quantum state |S〉 = |+ +〉, and w ∈ {00, 01, 10, 11} be the search target. One can perform two specific unitary operations on |S〉 = |+ +〉 repeatedly to find the target. Here, we firstly give some notations adopted in this article.
Let w ∈ {00, 01, 10, 11}, define |Sw〉 as follows:

Two specific unitary operations can be described as follows.


where w ∈ {00, 01, 10, 11} and S ∈ {+ +, − +, + −, − −}.
Grover’s QSA possesses two special properties as follows.
Property 1. Ref. 32 Let wi ∈ {00, 01, 10, 11} (i = 1, 2, 3, 4). Then  if and only if
if and only if  .
.
Property 2. Ref. 14 Let v, w1, w2 ∈ {00, 01, 10, 11}. Then  if and only if
if and only if  .
.
The following Theorem 1 and Theorem 2 generalize the Property 1 and property 2 from |S00〉 to |Sw〉 with any w ∈ {00, 01, 10, 11} separately.
Theorem 1. Let w, wi ∈ {00, 01, 10, 11} (i = 1, 2, 3, 4), then  if and only if
if and only if  . More generally, let n be an odd positive integer, and w, v, wi ∈ {00, 01, 10, 11} (i = 1, 2, …, n), then
. More generally, let n be an odd positive integer, and w, v, wi ∈ {00, 01, 10, 11} (i = 1, 2, …, n), then  if and only if
if and only if  .
.
Proof. (1)Firstly, we show that  if and only if
if and only if  .
.
If
 and w1 = w2, then w3 = w4, and it is obviously that
and w1 = w2, then w3 = w4, and it is obviously that  . Similarly to the cases w1 = w3 and w2 = w3.
. Similarly to the cases w1 = w3 and w2 = w3.If
 , and w1, w2 and w3 are different from each other, then |w1〉, |w2〉, |w3〉 and |w4〉 are orthogonal to each other because of the relation
, and w1, w2 and w3 are different from each other, then |w1〉, |w2〉, |w3〉 and |w4〉 are orthogonal to each other because of the relation  . In this case, we can get
. In this case, we can get
Hence,

If
 , let us show that
, let us show that  .
.
Denote  . From (a) and (b), we can easily get
. From (a) and (b), we can easily get  . Suppose the equation
. Suppose the equation  holds, then
holds, then  or
or  .
.
In the former case, we have

a contradiction to the fact that  for any v ∈ {00, 01, 10, 11}. The same conclusion of the second case can be got similarly. Hence,
for any v ∈ {00, 01, 10, 11}. The same conclusion of the second case can be got similarly. Hence,  .
.
From (a), (b) and (c), we can get  if and only if
if and only if  .
.
(2) Secondly, we show that  if and only if
if and only if  . We will give the proof by using the mathematical induction to the odd positive integer n.
. We will give the proof by using the mathematical induction to the odd positive integer n.
n = 1, the result is trivial.
Suppose that the result is correct in the case of n = k, where k is a positive odd integer. That is to say,
 if and only if
if and only if  ,where
,where  . When n = k + 2, we have
. When n = k + 2, we have

where  .
.
Hence,  if and only if
if and only if  .
.
Theorem 2. Let w, v, w0, w1 ∈ {00, 01, 10, 11}. Then  if and only if
if and only if  .
.
The correctness of Theorem 2 could be verified for each value of the tuples (w, v, w0, w1) ∈ {00, 01, 10, 11}4 one by one.
From Theorem 1 and Theorem 2, we can get Theorem 3 at once.
Theorem 3. Let n be an odd positive integer, and w, v, wi ∈ {00, 01, 10, 11}, where i = 0, 1, …, n. Then  if and only if
if and only if  .
.
Theorem 4. Let w, w0, w1, w2 ∈ {00, 01, 10, 11}. Then  if and only if
if and only if  . More generally, let n be a positive even integer, and w, wi ∈ {00, 01, 10, 11} (i = 0, 1, …, n), then
. More generally, let n be a positive even integer, and w, wi ∈ {00, 01, 10, 11} (i = 0, 1, …, n), then  if and only if
if and only if  .
.
Proof. (1)Firstly, we show that  if and only if
if and only if  .
.
If w1 = w2, the result is trivial.
If
 ,suppose {w1, w2, w3, w4} = {00, 01, 10, 11},then |w1〉, |w2〉, |w3〉 and |w4〉 are orthogonal to each other. In this case, we can get
,suppose {w1, w2, w3, w4} = {00, 01, 10, 11},then |w1〉, |w2〉, |w3〉 and |w4〉 are orthogonal to each other. In this case, we can get

Now, we show that there exists w0 ∈ {00, 01, 10, 11} such that  .
.

Hence, we can select a proper w0 ∈ {00, 01, 10, 11} such that  , and we can easily get the relation
, and we can easily get the relation  from Table 1.
from Table 1.
 with Different w, w2 and w1.
with Different w, w2 and w1.(2)From (1) and Theorem 1, we can easily get the correction of the proposition that  if and only if
if and only if  , by using the mathematical induction similar to the proof of (2) in Theorem 1.
, by using the mathematical induction similar to the proof of (2) in Theorem 1.
The Proposed QKA Protocol
Suppose that there are N (N ≥ 2) participants P0, P1, P2, …, and PN−1, and each of them generate a random sequence with length 2n as his or her secret key firstly.

where the element  . Next, P0, P1, P2, …, and PN−1 want to negotiate a common key
. Next, P0, P1, P2, …, and PN−1 want to negotiate a common key  . Here,
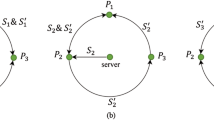
. Here,  denotes the bitwise Exclusive OR. Now, The detailed description of the proposed MQKA protocol can be seen in Fig. 1 and the following explanation.
denotes the bitwise Exclusive OR. Now, The detailed description of the proposed MQKA protocol can be seen in Fig. 1 and the following explanation.
The Detailed Description of MQKA
Step 1 Initialization Phase
Each participant Pi selects two random sequences SI and VI with length 2n, and prepares a two-particle quantum state sequence Si,i+1 according to the random sequence SI.

where si,j, vi,j ∈ {0, 1} and the definition of  can be seen in equation (1), i = 0, 1, …, N − 1; j = 1, 2, …, 2n; t = 1, 2, …, n.
can be seen in equation (1), i = 0, 1, …, N − 1; j = 1, 2, …, 2n; t = 1, 2, …, n.
Next, Pi performs unitary operations  (t = 1, 2, …, n) on every state
(t = 1, 2, …, n) on every state  , and the resulted sequence be denoted as Si→i+1. He also generates kn (k is the detection rate) decoy particles from {|0〉, |1〉} or {|+〉, |−〉} randomly, and gets a new sequence
, and the resulted sequence be denoted as Si→i+1. He also generates kn (k is the detection rate) decoy particles from {|0〉, |1〉} or {|+〉, |−〉} randomly, and gets a new sequence  by inserting them into the sequence Si→i+1. Meanwhile, Pi records the initial states and corresponding positions of every checking particles, and then sends the sequence
by inserting them into the sequence Si→i+1. Meanwhile, Pi records the initial states and corresponding positions of every checking particles, and then sends the sequence  to the next participant Pi+1,where + denotes modulo N addition.
to the next participant Pi+1,where + denotes modulo N addition.
In addition, it is important to note that the decoy particles could be inserted into Si→i+1 randomly. For example, suppose  and the decoy sequence is
and the decoy sequence is  with the position (1, 3, 4, 6, 8, 10, 11, 15), then
with the position (1, 3, 4, 6, 8, 10, 11, 15), then 
 (
( denotes decoy particle). Next, the particles in
denotes decoy particle). Next, the particles in  is transmitted one after another.
is transmitted one after another.
Step 2 Eavesdropping Checking Phase
After confirming that all Pi+1 have received the sequence  , Pi and Pi+1 can calculate the error probability by comparing the measurement results with the initial states of decoy particles. If the error ratio exceeds the predetermined threshold value, Pi declares that the communication is invalid. Otherwise, and the process continues to Step 3.
, Pi and Pi+1 can calculate the error probability by comparing the measurement results with the initial states of decoy particles. If the error ratio exceeds the predetermined threshold value, Pi declares that the communication is invalid. Otherwise, and the process continues to Step 3.
Step 3 Encoding Phase
By deleting the decoy states from  , Pi+1 can get the sequence Si→i+1. Then according to the private key Ki+1, Pi+1 performs unitary operations
, Pi+1 can get the sequence Si→i+1. Then according to the private key Ki+1, Pi+1 performs unitary operations  (t = 1, 2, …, n) on every two-particle state in Si→i+1, and denotes the resulted sequence as Si→i+2. Here the definition of
(t = 1, 2, …, n) on every two-particle state in Si→i+1, and denotes the resulted sequence as Si→i+2. Here the definition of  can be seen in equation (2). Next, Pi+1 will get a new sequence
can be seen in equation (2). Next, Pi+1 will get a new sequence  by inserting the decoy particles into Si→i+2 similar to Step 1, and send it to Pi+2.
by inserting the decoy particles into Si→i+2 similar to Step 1, and send it to Pi+2.
Step 4 Encoding Recursively Phase
After confirming that Pi+2 have received the sequence  , Pi+1 and Pi+2 execute eavesdropping checking mentioned in Step 2. If the error ratio exceeds the predetermined threshold value, Pi declares that the communication is invalid. Otherwise, the process continues. Pi+2 execute Encoding Phase similar to Pi+1 in Step3.
, Pi+1 and Pi+2 execute eavesdropping checking mentioned in Step 2. If the error ratio exceeds the predetermined threshold value, Pi declares that the communication is invalid. Otherwise, the process continues. Pi+2 execute Encoding Phase similar to Pi+1 in Step3.
Pi+3, …, Pi−1 execute eavesdropping checking mentioned in Step 2 and Encoding Phase similar to Pi+1 in Step3.
Step 5 Extracting Common Key Phase
When Pi has received the sequence  from Pi−1, he firstly does eavesdropping checking with Pi−1. Then he will obtains the sequence Si→i by deleting the decoy particles from
from Pi−1, he firstly does eavesdropping checking with Pi−1. Then he will obtains the sequence Si→i by deleting the decoy particles from  . Next, Pi performs unitary operation
. Next, Pi performs unitary operation  on the corresponding two-particle state in the sequence Si→i according the sequence
on the corresponding two-particle state in the sequence Si→i according the sequence  , and takes measurements on every resulted two-particle state with basis {00, 01, 10, 11} if N is odd, or {+ +, − +, + −, − −} if N is even.
, and takes measurements on every resulted two-particle state with basis {00, 01, 10, 11} if N is odd, or {+ +, − +, + −, − −} if N is even.
If N is odd, denote the sequence of measured result as
 . Then Pi computes
. Then Pi computes
If N is even, denote the sequence of measured result as
 . Then Pi computes
. Then Pi computes


where  .
.
The 2n – bit sequence [Ki] is the target common key [K] of the N participants.
Correctness of The Proposed Protocol
Now, we show that  .
.
In fact, the sequence WI defined in step 5 can be got by using Theorem 3 or Theorem 4 separately. Namely, after performed unitary operations  on every two-particle state of sequence Si→i, the t-th two-particle state of the resulted sequence can be represented as
on every two-particle state of sequence Si→i, the t-th two-particle state of the resulted sequence can be represented as

i.e., Pi, Pi+1, …, and Pi−1 perform unitary operations defined by equation (2) on the two-particle state  separately, and Pi performs the operation defined by equation (3) at last.
separately, and Pi performs the operation defined by equation (3) at last.
If N is odd, then we can get the conclusion that the t – th two-particle state mentioned in (4) will be in {|00〉, |01〉, |10〉, |11〉}, and the state of (4) equals
 by using Theorem 3. Furthermore, we can also get
by using Theorem 3. Furthermore, we can also get
Then,

Hence,

If N is even, then we can get the conclusion that the t – th two-particle state mentioned in (4) will be in {|+ +〉, |− +〉, |+ −〉, |− −〉}, and the state of (4) equals
 by using Theorem 4. Furthermore, we can also get
by using Theorem 4. Furthermore, we can also get

Then,

Hence,

From (i) (ii), we can know that all participants obtain the target common key sequence successfully, i.e.

An Example of The Proposed Protocol with N = 5
In the following, we will give an example of five-party quantum key agreement protocol without considering eavesdropping checking. Suppose P0, P1, P2, P3, and P4 want to negotiate a common sequence with length 6 as the target key. Firstly, they select their private key separately as follows.

Next,they run the protocol.
Step 1 Initialization Phase
Pi selects two random sequences VI and SI with length 2n, and prepares a two-particle quantum state sequence Si,i+1 according to the random sequence SI.


Next, P0 performs unitary operations  on every state
on every state  (t = 1, 2, 3), and the resulted sequence be denoted as S0→1. P1, P2, P3 and P4 perform the same operations similarly. P0 (or P1 or P2 or P3 or P4) sends S0→1 (or S1→2 or S2→3 or S3→4 or S4→0) to P1 (or P2 or P3 or P4 or P0).
(t = 1, 2, 3), and the resulted sequence be denoted as S0→1. P1, P2, P3 and P4 perform the same operations similarly. P0 (or P1 or P2 or P3 or P4) sends S0→1 (or S1→2 or S2→3 or S3→4 or S4→0) to P1 (or P2 or P3 or P4 or P0).
Step 2 Encoding Phase and Encoding Recursively Phase
P1 (or P2 or P3 or P4 or P0) encodes S0→1 (or S1→2 or S2→3 or S3→4 or S4→0) by using a unitary operation according to his private key.

The encoding procession continues until P0 has received the sequence S0→0 Encoded by K1, K2, K3, and K4) separately. S0→0, S1→1, S2→2, S3→3 and S4→4 can be represented as follows.

Step 3 Extracting Common Key Phase
P0 (or P1 or P2 or P3 or P4) performs unitary operations decided by S0,1 (or S1,2 or S2,3 or S3,4 or S4,0) on S0→0 (or S1→1 or S2→2 or S3→3 or S4→4), and takes measurements on every two-particle state of the resulted sequence with basis {|00〉, |10〉, |01〉, |11〉} because N = 5 is odd. Then the measurement results of P0 (or P1 or P2 or P3 or P4) will be

At last, P0 computes  , and it is easy to verify that
, and it is easy to verify that  . P1, P2, P3 and P4 can also obtain the target common key sequence
. P1, P2, P3 and P4 can also obtain the target common key sequence  similar to P0.
similar to P0.
Security Analysis of The Proposed Protocol
In this section, we will show that the proposed MQKA protocol is secure against external and internal attacks. The external attacks contains intercept-resend attack and entangling attack. Without loss of generality, we only consider the circumstance that there are only three participants named P0, P1 and P2 in the proposed scheme, and it is similar to other cases. Here, we suppose that an eavesdropper named Eve wants to eavesdrop the target common key of P0, P1 and P2 without being detected.
Firstly, let us discuss the intercept-resend attack. Suppose that P0 prepares a two-particle quantum state sequence S0→1 according to a random sequence S0 with length 2n. P0 inserts 2n decoy particles into it and sends the new sequence  to P1. If Eve intercepts the sequence and re-sends a fake sequence prepared beforehand instead of
to P1. If Eve intercepts the sequence and re-sends a fake sequence prepared beforehand instead of  , then she wants to obtain the operations performed by P1 through the fake sequence. However, Eve will be detected with probability
, then she wants to obtain the operations performed by P1 through the fake sequence. However, Eve will be detected with probability  in the eavesdropping check phase by P0 and P1 because she does not know about the positions and basis of decoy particles. Hence, Eve will be detected with probability converging to 1 when n is large enough. Similar to the intercept-resend attack in the channel between P1 and P2 or P2 and P0.
in the eavesdropping check phase by P0 and P1 because she does not know about the positions and basis of decoy particles. Hence, Eve will be detected with probability converging to 1 when n is large enough. Similar to the intercept-resend attack in the channel between P1 and P2 or P2 and P0.
Secondly, let us discuss the entangling attack. Suppose Eve intercepts a transmitting particles to the sequence  , and performs a unitary operation Ue on the intercepted particles to entangle an ancillary particles |E〉 prepared beforehand. The unitary operation Ue can be defined by the following equations:
, and performs a unitary operation Ue on the intercepted particles to entangle an ancillary particles |E〉 prepared beforehand. The unitary operation Ue can be defined by the following equations:

where |e00〉, |e01〉, |e10〉 and |e11〉 are pure states decided by the unitary operation Ue, and the amplitude a, b, c and d satisfy |a|2 + |b|2 = 1 and |c|2 + |d|2 = 1. Then it is easy to get:

If the decoy particle belongs to {|0〉, |1〉}, in order to pass the eavesdropping checking phase, Eve has to set b = c = 0 which implies that a = d = 1. Then Eve cannot distinguish |e00〉 from |e11〉, and cannot get any useful information. Hence the entangling attack cannot work in the proposed scheme.
Thirdly, let us discuss the internal attack. Without loss of generality, suppose the dishonest participants, P1 and P2, want to cooperate to determine the target common key alone by illegal means. In the encoding procession P0 → P1 → P2 → P0, P0 does not leaks any information. In the encoding procession P1 → P2 → P0 → P1, P0 encodes the two-particle states by his private key in the last step, and meanwhile, he has already obtained the information of the  and
and  private keys from S0→0. So we only need to consider the encoding procession P2 → P0 → P1 → P2. Firstly, P2 sends S2 → 0 to P0. Meanwhile, he also sends his private information S2 and V2 to P1. Secondly, after the eavesdropping checking phase between P0 and P1, P1 perform unitary operations defined by equation (3) according to the
private keys from S0→0. So we only need to consider the encoding procession P2 → P0 → P1 → P2. Firstly, P2 sends S2 → 0 to P0. Meanwhile, he also sends his private information S2 and V2 to P1. Secondly, after the eavesdropping checking phase between P0 and P1, P1 perform unitary operations defined by equation (3) according to the  private information S2. Next, P1 takes measurements on the two-particle state in the resulted sequence with the basis
private information S2. Next, P1 takes measurements on the two-particle state in the resulted sequence with the basis  . At last, P1 eavesdrops
. At last, P1 eavesdrops  private key successfully from the value of the measurement results, S2 and V2. Even so, P1 and P2 still can not determine the target common key alone. In fact, it is obvious that the only way to the P0 to get the target key sequence is to compute
private key successfully from the value of the measurement results, S2 and V2. Even so, P1 and P2 still can not determine the target common key alone. In fact, it is obvious that the only way to the P0 to get the target key sequence is to compute  , and the information of V0 and S0 is only known to P0. Suppose that P1 and P2 embed new private key in the procession P0 → P1 → P2 → P0, then the behavior of them only affects the value of W0 because of that P1 and P2 know nothing about V0 and S0. Therefore, the final key [K0] of P0 will be different from the final key [K1] and [K2]. Hence, P0, P1 and P2 can not obtain the target common key sequence. In a word, P1 and P2 cannot determine the target common key alone by illegal means, and the proposed protocol is secure against internal attack.
, and the information of V0 and S0 is only known to P0. Suppose that P1 and P2 embed new private key in the procession P0 → P1 → P2 → P0, then the behavior of them only affects the value of W0 because of that P1 and P2 know nothing about V0 and S0. Therefore, the final key [K0] of P0 will be different from the final key [K1] and [K2]. Hence, P0, P1 and P2 can not obtain the target common key sequence. In a word, P1 and P2 cannot determine the target common key alone by illegal means, and the proposed protocol is secure against internal attack.
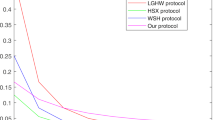
Efficiency Comparison with Existing Protocol
In this section, we will compare the proposed MQKA protocols with five existing MQKA protocols in the following four aspects: number of qubit measurements, number of unitary operations, qubit efficiency and security against internal attack. The five existing MQKA protocols are “LGHW protocol”20, “SZ protocol”21, “SZWYZL protocol”26, “SYW protocol”28, and “SZWLL protocol”29. The qubit efficiency can be defined as  , where c is the length of target common key sequence, q is the number of qubits used in transmission and security checking, and “b” is the number of used classical bits. We only compare the internal attack because the internal attackers are the most powerful attackers in the multi-party protocols usually. Suppose the five protocols just mentioned will produce 2 – bit target common key sequence, i.e., c = 2. The parameter comparison can be seen in Table 2.
, where c is the length of target common key sequence, q is the number of qubits used in transmission and security checking, and “b” is the number of used classical bits. We only compare the internal attack because the internal attackers are the most powerful attackers in the multi-party protocols usually. Suppose the five protocols just mentioned will produce 2 – bit target common key sequence, i.e., c = 2. The parameter comparison can be seen in Table 2.
LGHW protocol. The protocol is secure from internal attack, because it is based on BB84 and all participants transmit their privacy secret only once. However, the efficiency
 is too low and the number of measurements is larger than others.
is too low and the number of measurements is larger than others.SZ protocol. The efficiency and the number of measurements are both not good. More important, it is susceptible to internal attacks owing to an attack strategy20 proposed by Liu, et al.
SZWYZL protocol. Any participant’s modification can be detected by others because the protocol is based on cluster states. Hence, it is secure from internal attack. Besides, I think the efficiency analysed by authors in ref. 26 is not objective. In fact, the efficiency
 is not good, and the number of measurements and unitary operations are also high.
is not good, and the number of measurements and unitary operations are also high.SYW protocol. The protocol is similar to SZWYZL protocol, so it is secure for internal attack. The parameters of efficiency, the number of measurements and unitary operations, are all better than SZWYZL protocol.
SZWLL protocol. The protocol is an improvement on LGHW protocol, and it is much more efficient than any other secure protocols. However, it is susceptible to internal attacks. Without loss of generality, we consider three-party protocol. Suppose the dishonest participants, P1 and P2, want to cooperate to obtain the private key of P0. Consider the message encoding phase in the procession P2 → P0 → P1 → P2. Firstly, P2 pre-agreed a common final key [K] with P1, and tells the original state of each photon in the sequence S2 to P1. Secondly, after eavesdropping check between P1 and P0, P1 takes measures on
 with basis {|0〉, |1〉}, and obtains the privacy k0 according to S2. Thirdly, P1 sends k1 and k0 to P2. At last, P2 encodes
with basis {|0〉, |1〉}, and obtains the privacy k0 according to S2. Thirdly, P1 sends k1 and k0 to P2. At last, P2 encodes  according to
according to  . Hence, P0, P1 and P2 obtain the final key [K] only determined by P1 and P2 only.
. Hence, P0, P1 and P2 obtain the final key [K] only determined by P1 and P2 only.Our protocol. Firstly, our protocol is secure against internal attack. Secondly, The number of measurements is better than LGHW protocol and SZWYZL protocol, but worse than SYW protocol. The unitary operations is not better than LGHW protocol, SZWYZL protocol and SYW protocol. However, the efficiency of our protocol is better than any other secure protocols.
Discussion
In this paper, we propose the first multiparty QKA protocol based on a quantum search algorithm known as Grover’s algorithm. Firstly, we generalize the properties of quantum search algorithms. Secondly, using the generalized properties of QSA, we propose a multiparty QKA protocol. Next, a 5-party protocol novel example is presented. At last, the security and efficiency analysis shows that our protocol is prior to existing MQKA protocols.
Additional Information
How to cite this article: Cao, H. and Ma, W. Multiparty Quantum Key Agreement Based on Quantum Search Algorithm. Sci. Rep. 7, 45046; doi: 10.1038/srep45046 (2017).
Publisher's note: Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
Bennett, C. H. & Brassard, G. Quantum cryptography: public-key distribution and coin tossing [C]. Proceedings of IEEE International Conference on Computer System and Signal Processing 175–179 (1984).
Lo, H. K. & Chau, H. F. Unconditional security of quantum key distribution over arbitrarily long distances[J]. Science 283, 2050C2056 (1999).
Lo, H. K., Ma, X. & Chen, K. Decoy state quantum key distribution. Phys. Rev. Lett. 94, 230504 (2005).
Li, H. Statistical-fluctuation analysis for quantum key distribution with consideration of after-pulse contributions. Phys. Rev. A. 92, 062344 (2015).
Hillery, M., Buzek, V. & Berthiaume, A. Quantum secret sharing. Phys. Rev. A. 59, 1829–1834 (1999).
Hsu, L. Y. Quantum secret-sharing protocol based on Grover??s algorithm. Phys. Rev. A 68, 022306 (2003).
Yang, Y., Jia, X. et al. Verifiable quantum (k, n)-threshold secret sharing. Quantum Inf Process 11, 1619–1625 (2012).
Liao, C., Yang, C. & Hwang, T. Dynamic quantum secret sharing scheme based on GHZ state. Quantum Inf Process 13, 1907–1916 (2014).
Qin, H. W. & Dai, Y. W. d-Dimensional quantum state sharing with adversary structure. Quantum Inf Process 15, 1689C1701 (2016).
Deng, F. G. & Long, G. L. Secure direct communication with a quantum one-time pad. Phys. Rev. A. 69, 052319 (2004).
Tseng, H. Y., Tsai, C. W. & Hwang, T. Controlled deterministic secure quantum communication based on quantum search algorithm. Int. J. Theor. Phys. 51, 2447–2454 (2012).
Li, Y. & Nie, Li. Asymmetric bidirectional controlled teleportation by using six-qubit cluster state. Int. J. Theor. Phys. 55, 1–9 (2016).
Costa, D., Almeida, N. G. & Villas-Boas, C. J. Secure quantum communication using classical correlated channel. Quantum Inf Process 15, 4303–4311 (2016).
Zhang, W. W., Li, D. et al. Quantum private comparison based on quantum search algorithm. Int. J. Theor. Phys. 52, 1466–1473 (2013).
Guo, F. Z. & Gao, F. Quantum private comparison protocol based on entanglement swapping of d-level bell states. Quantum Inf Process 12, 2793–2802 (2013).
Zhou, N., Zeng, G. & Xiong, J. Quantum key agreement protocol. Electronics Letters 40, 1149–1150 (2004).
Tsai, C. & Hwang, T. On quantum key agreement protocol. Technical Report (C-S-I-E, NCKU, Taiwan), ROC (2009).
Chong, S. K., Tsai, C. W. & Hwang, T. Improvement on Quantum key agreement protocol with maximally entangled states? Int. J. Theor. Phys. 50, 1793–1802 (2011).
Chong, S. K. & Hwang, T. Quantum key agreement protocol based on BB84. Opt. Commun. 283, 1192–1195 (2010).
Liu, B., Gao, F. et al. Multiparty quantum key agreement with single particles. Quantum Inf Process 12, 3411–3420 (2013).
Shi, R. H. & Zhong, H. Multi-party quantum key agreement with bell states and bell measurements. Quantum Inf Process 12, 921–932 (2013).
Shen, D. S., Ma, W. P. & Wang, L. Two-party quantum key agreement with four-qubit cluster states. Quantum Inf Process 13, 2313C2324 (2014).
Xu, G. B., Wen, Q. Y. et al. Novel multiparty quantum key agreement protocol with GHZ states. Quantum Inf Process 13, 2587–2594 (2014).
Huang, W., Wen, Q. Y. et al. Quantum key agreement with epr pairs and single-particle measurements. Quantum Inf Process 13, 649C663 (2014).
Shukla, C., Alam, N. & Pathak, A. Protocols of quantum key agreement solely using bell states and bell measurement. Quantum Inf Process 13, 2391C2405 (2014).
Sun, Z., Zhang, C. et al. Multi - party quantum key agreement by an entangled six - qubit state. Int. J. Theor. Phys. 55, 1920–1929 (2016).
Hsueh, C. C. & Chen, C. Y. Quantum key agreement protocol with maximal entangled states. Proceedings of the 14th Information Security Conference (National Taiwan University of Science and Technology, Taipei ISC 2004), 236C242 (2004).
Sun, Z., Yu, J. & Wang, P. Efficient multi-party quantum key agreement by cluster states. Quantum Inf Process 15, 373–384 (2016).
Sun, Z., Zhang, Cai. et al. Improvements on ?ltiparty quantum key agreement with single particles? Quantum Inf Process 12, 3411–3420 (2013).
Grover, L. K. Quantum mechanics helps in searching for a needle in a haystack. Phys. Rev. Lett. 79, 325 (1997).
Wang, C., Hao, L. et al. Quantum direct communication based on quantum search algorithm. Int. J. Quantum Inf 8, 443–450 (2010).
Tseng, H. Y., Tsai, C. W. & Hwang, T. Controlled deterministic secure quantum communication based on quantum search algorithm. Int. J. Theor. Phys 51, 2447–2454 (2012).
Acknowledgements
This work is partially supported by National Science Foundation of China under grant No. 61373171, The 111 Project under grant No. B08038, and The Key Project of Science Research of Anhui Province (Quantum key agreement protocol based on entangled state).
Author information
Authors and Affiliations
Contributions
Cao, H. designed the scheme. Cao, H. and Ma, W. did security analysis and efficiency comparison. All authors wrote and reviewed the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing financial interests.
Rights and permissions
This work is licensed under a Creative Commons Attribution 4.0 International License. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in the credit line; if the material is not included under the Creative Commons license, users will need to obtain permission from the license holder to reproduce the material. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/
About this article
Cite this article
Cao, H., Ma, W. Multiparty Quantum Key Agreement Based on Quantum Search Algorithm. Sci Rep 7, 45046 (2017). https://doi.org/10.1038/srep45046
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/srep45046
This article is cited by
-
Multi-Party Quantum Key Agreement with Four-Qubit Cluster States Immune to Collusive Attack
International Journal of Theoretical Physics (2024)
-
Quantum teleportation with one classical bit
Scientific Reports (2022)
-
Efficient Multiparty Quantum Key Agreement Using Block-Based Single Particles
International Journal of Theoretical Physics (2022)
-
Quantum Secure Multi-Party Summation Based on Grover’s Search Algorithm
International Journal of Theoretical Physics (2021)
-
Quantum Key Agreement Protocol Based on Quantum Search Algorithm
International Journal of Theoretical Physics (2021)
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.


 and w1 = w2, then w3 = w4, and it is obviously that
and w1 = w2, then w3 = w4, and it is obviously that  . Similarly to the cases w1 = w3 and w2 = w3.
. Similarly to the cases w1 = w3 and w2 = w3. , and w1, w2 and w3 are different from each other, then |w1〉, |w2〉, |w3〉 and |w4〉 are orthogonal to each other because of the relation
, and w1, w2 and w3 are different from each other, then |w1〉, |w2〉, |w3〉 and |w4〉 are orthogonal to each other because of the relation  . In this case, we can get
. In this case, we can get

 , let us show that
, let us show that  .
. if and only if
if and only if  ,where
,where  . When n = k + 2, we have
. When n = k + 2, we have ,suppose {w1, w2, w3, w4} = {00, 01, 10, 11},then |w1〉, |w2〉, |w3〉 and |w4〉 are orthogonal to each other. In this case, we can get
,suppose {w1, w2, w3, w4} = {00, 01, 10, 11},then |w1〉, |w2〉, |w3〉 and |w4〉 are orthogonal to each other. In this case, we can get
 . Then Pi computes
. Then Pi computes . Then Pi computes
. Then Pi computes by using Theorem 3. Furthermore, we can also get
by using Theorem 3. Furthermore, we can also get


 by using Theorem 4. Furthermore, we can also get
by using Theorem 4. Furthermore, we can also get is too low and the number of measurements is larger than others.
is too low and the number of measurements is larger than others. is not good, and the number of measurements and unitary operations are also high.
is not good, and the number of measurements and unitary operations are also high. with basis {|0〉, |1〉}, and obtains the privacy k0 according to S2. Thirdly, P1 sends k1 and k0 to P2. At last, P2 encodes
with basis {|0〉, |1〉}, and obtains the privacy k0 according to S2. Thirdly, P1 sends k1 and k0 to P2. At last, P2 encodes  according to
according to  . Hence, P0, P1 and P2 obtain the final key [K] only determined by P1 and P2 only.
. Hence, P0, P1 and P2 obtain the final key [K] only determined by P1 and P2 only.