Abstract
Quantum key agreement enables remote participants to fairly establish a secure shared key based on their private inputs. In the circular-type multiparty quantum key agreement mode, two or more malicious participants can collude together to steal private inputs of honest participants or to generate the final key alone. In this work, we focus on a powerful collusive attack strategy in which two or more malicious participants in particular positions, can learn sensitive information or generate the final key alone without revealing their malicious behaviour. Many of the current circular-type multiparty quantum key agreement protocols are not secure against this collusive attack strategy. As an example, we analyze the security of a recently proposed multiparty key agreement protocol to show the vulnerability of existing circular-type multiparty quantum key agreement protocols against this collusive attack. Moreover, we design a general secure multiparty key agreement model that would remove this vulnerability from such circular-type key agreement protocols and describe the necessary steps to implement this model. The proposed model is general and does not depend on the specific physical implementation of the quantum key agreement.
Similar content being viewed by others
Introduction
The concept of the key agreement was first presented by Diffie–Hellman in 19761. It describes how two remote users can fairly generate a secured shared key based on their private inputs. In 1982, Ingemarsson et al.2 extended the two-party key agreement protocol to a multiparty or group key agreement protocol. After that, several multiparty key agreement schemes have been published3. However, future quantum computers with sufficient power could threaten the security of many of the current public-key cryptosystems whose security mainly relies on unproven mathematical assumptions4,5. For that reason, quantum applications in cryptography have attracted the attention of a lot of scientists and researchers to suggest and develop information-theoretically unconditional secure cryptosystems. One of the most common quantum cryptographic applications is quantum key distribution (QKD)6, in which remote participants can establish a shared random key securely even in the presence of an attacker with unlimited classical or quantum computing power. Subsequently, several quantum cryptographic applications have been introduced to solve various classical security issues7,8,9,10,11,12,13,14,15,16.
Recently, quantum key agreement (QKA) has attracted the attention of a lot of researchers17. QKA ensures fairness between the involved participants to generate a shared secure key based on their private inputs. Using the quantum teleportation protocol, Zhou et al.17, in 2004, presented the first two-party QKA scheme. In 2013, the two-party QKA was extended to multiparty QKA protocols18. Subsequently, several multiparty QKA protocols have been presented19,20,21,22. In general, as noted in18, there are three types of MQKA protocols; (1) the first type is the tree-type in which every party sends their secret data through independent quantum channels to all other parties23; (2) the second type is the complete-graph-type in which every participant sends a sequence of qubits to each of the others parties to encode her or his secret information, (3) while in the third type that is the circle-type (sometimes called travelling-mode)8,24, every party generates a random sequence of qubits and sends this sequence to another party who applies an encoding process producing a new evolved sequence of qubits and sends the new sequence to the next party; this process continues over all parties until the evolved sequence reaches the party who generates the first sequence. Compared to the other QKA types, the circle-type is more efficient and more easily achieves the property of fairness. For that reason, the QKA circle-type has been intensively investigated.
In 2016, Liu et al.18 pointed out that all existing circle-type multiparty quantum key agreement (CT-MQKA) protocols are vulnerable to collusive attack, and asked a challenging question about the possibility of designing a secure CT-MQKA protocol. In response to this question, several CT-MQKA protocols have been proposed to avoid collusive attacks. However, in this work, we show that many of the existing CT-MQKA protocols are also not secure against a collusive attack. We study, as an example, the security of Sun et al.’s19 MQKA protocol (named SCWZ protocol hereafter) to show the vulnerability of the existing CT-MQKA protocols to collusive attacks. Furthermore, we design a general secure model for CT-MQKA protocols and propose the necessary steps for this model.
The insecurity of existing CT-MQKA protocols
In this section, we show that many of the recently published works in CT-MQKA are not secure against collusive attacks19,20,21,25,26. In general, there are two main collusive attack strategies, which could be applied to the CT-MQKA protocols:
The first collusive attack strategy
The first collusive attack strategy has been pointed out in18,19. Any two dishonest participants \({P}_{i}\) and \({P}_{j}\) (where \(i>j\); \(i, j\in \{1, 2, \dots , n\}\) and \(n\) is the number of participants) in particular positions in the circle-type protocols can control the final key if their particular positions meet the following two conditions:
The second collusive attack strategy
The second collusive attack strategy can be described as follows. In the CT-MQKA schemes, any two dishonest participants \({P}_{i}\) and \({P}_{j}\) can steal the private inputs of an honest participant \({P}_{k}\) (\(i, j, k\in \{1, 2, \dots , n\}\)) without being detected, if their positions meet one of the two following conditions:
Note, in our previous work8, we mentioned that two malicious users may try to deduce the private information of an honest one. However, in this work, we formulate and describe the general situation in which two dishonest participants can steal the private information of the honest ones as indicated in Eqs. (3) and (4).
Review of SCWZ’s protocol
In SCWZ’s protocol19, there are \(n\) participants and each participant \({P}_{i}\) (\({i}=1,2,\dots ,{n}\)) has an \(m-bit\) key (\({K}_{i}\)). The participants want to generate a shared secret key \(K\) fairly, where \({K} = {K}_{1} \oplus {K}_{2} \oplus \cdots \oplus {K}_{n}\). The steps of the SCWZ’s protocol can be described as follows.
-
1)
Preparation phase. The server generates \(n\) sequences of random single-photons. Each sequence \({S}_{i}\) (\(i=1, 2, \dots ,n\)) contains \(m\) single-photons and each photon is selected randomly from the four states {\(\left|+\right.\rangle , \left|-\right.\rangle , \left|0\right.\rangle , \left|1\right.\rangle\)}, where \(\left|\pm \right.\rangle =\frac{1}{\sqrt{2}}(\left|0\right.\rangle \pm \left|1\right.\rangle )\). The server also generates \(n\) sequences of random single photons (called \({C}_{i}\)), which are used as decoy photons to check the existence of eavesdroppers. Each single decoy photon is randomly selected from the states {\(\left|+\right.\rangle , \left|-\right.\rangle , \left|+y\right.\rangle , \left|-y\right.\rangle\)}, where \(\left|\pm y\right.\rangle =\frac{1}{\sqrt{2}}(\left|0\right.\rangle \pm i\left|1\right.\rangle )\). The server then randomly inserts and distributes the single-photons of \({C}_{i}\) into \({S}_{i}\) getting a new sequence \({S}_{i}^{^{\prime}}\), and sends the new sequence (\({S}_{i}\)) to \({P}_{i}\).
-
2)
Detection phase. Upon receiving \({S}_{i}^{^{\prime}}\), each participant sends an acknowledgment to the server. Then the server announces the positions of \({C}_{i}\) and their measurement bases. Each \({P}_{i}\) measures \({C}_{i}\) based on the corresponding measurement bases and stores the results. \({P}_{i}\) then randomly announces half of the measurement results of \({C}_{i}\); the server, in turn, announces the initial states of the second half of \({C}_{i}\). Then both the server and \({P}_{i}\) collaborate to compute the error rate. They end the protocol if the error rate higher than a predefined value. Otherwise, they continue with the protocol.
-
3)
After \({P}_{i}\) gets the secure sequence \({S}_{i}\), each participant performs the next sub-steps:
-
A.
Encoding phase. \({P}_{i}\) encodes secret information (\({K}_{i}\)) onto \({S}_{i}\) by applying the unitary operation \(U=\left|0\right.\rangle \langle 1|-\left|1\right.\rangle \langle 0|\) when the classical bit of the secret \({K}_{i}\) is 1, and the unitary operation \(I=\left|0\right.\rangle \langle 0|+\left|1\right.\rangle \langle 1|\) when the classical bit \({K}_{i}\) is 0. \({P}_{i}\) then reorders the decoy states that were prepared and inserted by the server in Step (1) and reinserts them in random positions into the encoded sequence obtaining a new sequence (\({S}_{i}^{i+1}\)), and sends \({S}_{i}^{i+1}\) to \({P}_{i+1}\).
-
B.
Eavesdropping check phase. Upon receiving \({S}_{i}^{i+1}\), \({P}_{i+1}\) and \({P}_{i}\) check the security of the transmission by performing the same process indicated in step (2) between the server and \({P}_{i}\).
-
C.
Encoding phase. After checking the security of transmission, \({P}_{i+1}\) encodes secret information (\({K}_{i+1}\)) onto \({S}_{i}\) following the same rules as in step (A). \({P}_{i+1}\) then reorders the decoy states and reinserts them in random positions into the encoded sequence obtaining a new sequence (\({S}_{i}^{i+2}\)), and sends \({S}_{i}^{i+2}\) to \({P}_{i+2}\).
-
D.
Similarly, the rest of the participants (\({P}_{i+2}, {P}_{i+3}, \dots , {P}_{i-2}\)) perform the Eavesdropping check phase and the Encoding phase indicated in steps (B) and (C).
-
E.
Upon receiving \({S}_{i}^{i-2}\), \({P}_{i-1}\) and \({P}_{i-2}\) check the security of transmission. If the quantum channel between \({P}_{i-1}\) and \({P}_{i-2}\) is secure, \({P}_{i-2}\) discards the decoy photons to get \({S}_{i}\), and informs the server of this fact.
-
A.
-
4)
When all the \({P}_{i-1}\) receive \({S}_{i}\), they send an acknowledgment to the server, and the server announces the measurement bases of \({S}_{i}\) to all the \({P}_{i-1}\). After that, each \({P}_{i-1}\) uses the corresponding measurement bases to measure \({S}_{i}\) obtaining \({K}_{i}^{^{\prime}}\), where \(K_{i}^{\prime } = K_{i} \oplus K_{i + 1} \oplus \cdots \oplus K_{i - 2}\). Finally, \({P}_{i-1}\) can recover the final shared secret key \(K = K_{i}^{^{\prime}} \oplus K_{i - 1}\).
The collusive attack against CT-MQKA protocols
In this section, we show that the SCWZ’s protocol, as an example of CT-MQKA protocols, is insecure against a collusive attack. Although the authors of SCWZ’s protocol have presented a security analysis to prove the security of their protocol against the first model of the collusive attack, their protocol is not secure against the second security model of collusive attack. That is to say, any two dishonest participants \({P}_{i}\) and \({P}_{j}\) in particular positions meeting the conditions in (3) and (4) can easily steal the private key of honest participants (\({P}_{k}\)).
Without loss of generality, assume we have three participants \({P}_{1}\), \({P}_{2}\), and \({P}_{3}\) and they have three private keys, e.g., \({K}_{1}=1000\), \({K}_{2}=0101\), and \({K}_{3}=1001\), respectively. And the three participants intend to share a secret key (\(K\)), here \(K = K_{1} \oplus K_{2} \oplus K_{3} = 0100\). We also assume that \(P_{1}\) and \(P_{3}\) are two dishonest participants and they need to steal the private key of the honest one (\({P}_{2}\)); hence they can deduce the final key without being caught.
In SCWZ’s protocol, the server generates three random sequences, e.g., \({S}_{1}=\{\left|+\right.\rangle , \left|0\right.\rangle , \left|1\right.\rangle ,\left|-\right.\rangle \}\), \({S}_{2}=\{\left|0\right.\rangle , \left|1\right.\rangle , \left|0\right.\rangle , \left|1\right.\rangle \}\), and \({S}_{3}=\{\left|0\right.\rangle , \left|+\right.\rangle , \left|-\right.\rangle , \left|1\right.\rangle \}\) each one consists of four single-photons. Also, the server generates three random sequences \({C}_{1}\), \({C}_{2}\), and \({C}_{3}\) each one consists of four decoy single-photon states. Then the server randomly inserts the decoy state \({C}_{1}\) (\({C}_{2}\)/\({C}_{3}\)) into \({S}_{1}=\{\left|+\right.\rangle , \left|0\right.\rangle , \left|1\right.\rangle ,\left|-\right.\rangle \}\) (\({S}_{2}=\{\left|0\right.\rangle , \left|1\right.\rangle , \left|0\right.\rangle , \left|1\right.\rangle \}\)/\({S}_{3}=\{\left|0\right.\rangle , \left|+\right.\rangle , \left|-\right.\rangle , \left|1\right.\rangle \}\)) and sends it to \({P}_{1}\) (\({P}_{2}\)/\({P}_{3}\)). After checking the security of the transmission, each participant discards the decoys and encodes their private information based on the encoding rule mentioned in Step 3.A. Subsequently, each participant sends the sequence in a circle to the other participants to encode their private inputs until the sequence is returned to the participant.
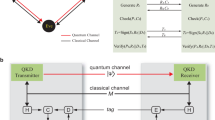
For simplicity, we show here the circle of \({S}_{1}\) (Fig. 1a) which will be used by the participant \({P}_{1}\) to get the final key (\(K\)). First, \({P}_{1}\) receives \({S}_{1}=\{\left|+\right.\rangle , \left|0\right.\rangle , \left|1\right.\rangle ,\left|-\right.\rangle \}\) from the server to encode her or his information and get the final key. Second, \({P}_{1}\) encodes a private input, i.e., \({K}_{1}=1000\) into \({S}_{1}\) getting the new sequence \({S}_{1}=\{ U\left|+\right.\rangle , I\left|0\right.\rangle , I\left|1\right.\rangle ,I\left|-\right.\rangle \}\). Third, \({P}_{1}\) inserts some decoy photons into \({S}_{1}\) and sends it to the dishonest \({P}_{3}\) instead of sending it to \({P}_{2}\). After checking the security of the transmission, \({P}_{3}\) discards the decoy states and gets \({S}_{1}=\{ U\left|+\right.\rangle , I\left|0\right.\rangle , I\left|1\right.\rangle ,I\left|-\right.\rangle \}\). At the same time, the dishonest \({P}_{1}\) generates a counterfeit sequence, e.g., \({S}_{1}^{^{\prime}}=\{ \left|0\right.\rangle , \left|0\right.\rangle , \left|-\right.\rangle ,\left|+\right.\rangle \}\) with decoy states and sends it to both \({P}_{2}\) and \({P}_{3}\). \({P}_{1}\) only tells \({P}_{3}\) that the sequence \({S}_{1}^{^{\prime}}\) is the counterfeit one. Since the honest participant (\({P}_{2}\)) does not have \({K}_{1}=1000\) and does not knows \({S}_{1}=\{\left|+\right.\rangle , \left|0\right.\rangle , \left|1\right.\rangle ,\left|-\right.\rangle \}\), she or he cannot know what the received new sequence looks like (i.e., \({S}_{1}=\{ U\left|+\right.\rangle , I\left|0\right.\rangle , I\left|1\right.\rangle ,I\left|-\right.\rangle \}\)).
Obviously, \({P}_{2}\) cannot distinguish between the genuine sequences and the counterfeit ones. So, \({P}_{2}\) encodes the private data, i.e., \({K}_{2}=0101\) into \({S}_{1}^{^{\prime}}\) getting \({S}_{1}^{^{\prime}}=\{ I\left|0\right.\rangle , U\left|0\right.\rangle , I\left|-\right.\rangle ,U\left|+\right.\rangle \}\) and sends \({S}_{1}^{^{\prime}}\) with decoy states to \({P}_{3}\). After checking the security of the transmission, \({P}_{3}\) discards the decoy qubits and gets \({S}_{1}^{^{\prime}}\). \({P}_{3}\) then requests the corresponding measurement bases of \({S}_{1}^{^{\prime}}\) from \({P}_{1}\) to get \({K}_{2}=0101\). Based on her or his private key, i.e., \({K}_{3}=1001\) and the private key of \({P}_{2}\), \({P}_{3}\) applies the corresponding unitary operations to the genuine sequence \({S}_{1}=\{ U\left|+\right.\rangle , I\left|0\right.\rangle , I\left|1\right.\rangle ,I\left|-\right.\rangle \}\) getting \({S}_{1}=\{U(I(U\left|+\right.\rangle )), I(U(I\left|0\right.\rangle )), I(I(I\left|1\right.\rangle )),U(U\left(I\left|-\right.\rangle \right))\}\) and sends it to \({P}_{1}\). Then the participants announce to the server that the quantum channels are secure. Finally, the server announces the measurement bases of \({S}_{1}\) to \({P}_{1}\) thus enabling \({P}_{1}\) to get \({\text{K}}\).
Similarly, if \({P}_{2}\) and \({P}_{3}\) (\({P}_{2}\) and \({P}_{1}\)) are the dishonest participants they can steal the private key of the honest participant \({P}_{1}\) (\({P}_{3}\)) in the circle while sending \({S}_{2}\) (\({S}_{3}\)), as shown in Fig. 1b (Fig. 1c). By applying the same attack strategy, most of the existing CR-MQKA protocols19,20,21,25,26 are vulnerable to this collusive attack.
The proposed secure CT-MQKA protocol
In this section, we give a general secure model of CT-MQKA against the collusive attack described above. Whereas our protocol can be implemented with photons, we describe it in more general terms here. The idea of adopting a semi-honest client–server model (or a third party) has been adopted in many previous QKA protocols to ensure the security of communication19,22,27,28,29. Suppose we have \(n\) participants who want to generate a shared secret key \(K\) fairly, where \(K = K_{1} \oplus K_{2} \oplus \cdots \oplus K_{n}\) with length \(m\). Every participant (\({P}_{i}\)) selects a private random classical key (\({K}_{i}^{^{\prime}}\)), where \(\left|{K}_{i}^{^{\prime}}\right|=\left|{K}_{i}\right|+nl\). Here, \(l\) is the number of decoy states used for checking the security of a quantum channel, and \(i=1, 2, \dots n\).
The general steps of this secure CT-MQKA model can be described as follows:
Step (1) The server generates \(n\) sequences \({S}_{i}\) (\(i\)= 1, 2, …, n), with each sequence containing \(m+nl\) single qubits. The server records the position of every single qubit. Every qubit is selected randomly from the four quantum states \(\left\{ {\left| + \right\rangle = \frac{1}{\sqrt 2 }\left( {\left| 0 \right\rangle + \left| 1 \right\rangle } \right),\left| - \right\rangle = \frac{1}{\sqrt 2 }\left( {\left| 0 \right\rangle - \left| 1 \right\rangle } \right),\left| 0 \right\rangle ,\left| 1 \right\rangle } \right\}\).
Step (2) The server also generates additional \(n\) sequences of random single qubits (called \({C}_{i}\)), which are used as decoy states to check the existence of eavesdroppers. Every single decoy qubit is randomly selected from the four quantum states {\(\left|+\right.\rangle , \left|-\right.\rangle , \left|0\right.\rangle , \left|1\right.\rangle\)}. The server inserts \({C}_{i}\) into \({S}_{i}\) producing a new sequence \({S}_{i}^{^{\prime}}\), and sends the new sequence (\({S}_{i}^{^{\prime}}\)) to \({P}_{i}\).
Step (3) Upon receiving \({S}_{i}^{^{\prime}}\), every participant sends an acknowledgment to the server.
Step (4) In this step, the server announces the positions of \({C}_{i}\) and their measurement bases. Every \({P}_{i}\) measures \({C}_{i}\) based on the corresponding measurement bases and stores the results. Randomly, \({P}_{i}\) selects half of the qubits in \({C}_{i}\) and announces their measurement results to the server. The server, in turn, announces the initial states of the second half of \({C}_{i}\). Both the server and \({P}_{i}\) collaborate to compute the error rate. They end the protocol if the error rate is higher than a predefined value. Otherwise, \({P}_{i}\) discards \({C}_{i}\) from \({S}_{i}^{^{\prime}}\) getting \({S}_{i}\) and continues to Step (5).
Step (5) After each \({P}_{i}\) gets the secure sequence \({S}_{i}\), they start to perform the next sub-steps.
-
a)
Encoding phase. \({P}_{i}\) encodes the secret information (\({K}_{i}^{{^{\prime}}}\)) onto \({S}_{i}\) by applying the unitary operation \(I=\left|0\right.\rangle \langle 0|+\left|1\right.\rangle \langle 1|\) when the classical bit \({K}_{i}^{{^{\prime}}}\) is 0, and the unitary operation \(U=\left|0\right.\rangle \langle 1|-\left|1\right.\rangle \langle 0|\) if the classical bit \({K}_{i}^{{^{\prime}}}\) is 1 as indicated in Table 1.
-
b)
Detecting the external attack phase. For detecting external eavesdroppers, \({P}_{i}\) generates a sequence of random single qubits (\({C}_{pi}\)) as in Steps (1) and (2), which are used as decoy qubits to check the existence of eavesdroppers in the quantum channel between \({P}_{i}\) and \({P}_{i+1}\) (note, the symbol \(+\) in “i + 1” represents the additional mod \(n\). \({P}_{i}\) inserts \({C}_{pi}\) into \({S}_{i}\) producing a new sequence \({S}_{i\mapsto i+1}\), and sends the new sequence (\({S}_{i\mapsto i+1}\)) to \({P}_{i+1}\). As in Step (4), \({P}_{i}\) and \({P}_{i+1}\) share the information of \({C}_{pi}\) and collaborate to compute the error rate. \({P}_{i}\) and \({P}_{i+1}\) end the protocol if the error rate is higher than a predefined value. Otherwise, \({P}_{i+1}\) discards \({C}_{pi}\) from \({S}_{i\mapsto i+1}\) obtaining \({S}_{i}\) and continues to the next process.
-
c)
Detecting the internal attack phase. Upon confirming that the communication between \({P}_{i}\) and \({P}_{i+1}\) is secure against external attackers, the server randomly selects \(l\) single-qubits as decoy qubits from \({S}_{i\mapsto i+1}\), by announcing their positions, and asks \({P}_{i}\) to publicly announce the unitary operations that were applied to the \(l\) qubits. Subsequently, the server announces the measurement bases of the \(l\) qubits to \({P}_{i+1}\). \({P}_{i+1}\) measures the \(l\) qubits using the corresponding measurement bases. Based on the measurement results, the measurement bases, and the applied unitary operations, \({P}_{i+1}\) can judge whether the \(l\) qubits are genuine or not. If not, \({P}_{i+1}\) ends the protocol. Otherwise, the participants do the following:
-
i)
\({P}_{i+1}\) discards the \(l\) qubits from \({S}_{i\mapsto i+1}\) that were selected by the server;
-
ii)
The server also discards the corresponding \(l\) qubits from \({S}_{i}\);
-
iii)
Every \({P}_{i}\) discards the corresponding classical bits from their private keys \({K}_{i}^{^{\prime}}\).
-
i)
-
d)
As in Step (5.a), \({P}_{i+1}\) encodes the secret information (\({K}_{i+1}^{^{\prime}}\)) onto \({S}_{i}\) and inserts some random decoy states (\({C}_{pi+1}\)) into \({S}_{i\mapsto i+1}\) producing \({S}_{i\mapsto i+2}\). Afterwards, \({P}_{i+1}\) sends \({S}_{i\mapsto i+2}\) to \({P}_{i+2}\).
-
e)
Upon \({P}_{i+2}\) receiving \({S}_{i\mapsto i+2}\), \({P}_{i+1}\) and \({P}_{i+2}\) collaborate to check the security of communication by performing Step (5.a–5.d).
-
f)
\({P}_{i+2}\) encodes her or his information and sends the new sequences to the next participants. This process continues until \({P}_{i}\) receives the secure quantum message (\({S}_{i\mapsto i-1}\)) from \({P}_{i-1}\); here, the symbol “−” in “i − 1” represents the subtraction mod \(n\).
Step (6): When all \({P}_{i}\) s receive \({S}_{i\mapsto i-1}\), they discard the decoy qubits getting \({S}_{i}\). Hence, each participant loses \(nl\) classical bits from \({K}_{i}^{^{\prime}}\) getting \({K}_{i}\) with length \(m\). After that, they send an acknowledgment to the server, and the server announces the measurement bases of \({S}_{i}\) to all the \({P}_{i}\) s. Finally, every \({P}_{i}\) uses the corresponding measurement bases to measure \({S}_{i}\) obtaining \(K\), where \(K={K}_{1} \oplus {K}_{2} \oplus \cdots \oplus {K}_{n}\).
Illustration of the proposed protocol
For simplicity, suppose we have three participants \({P}_{1}\), \({P}_{2}\), and \({P}_{3}\) and they want to generate a shared secret key \(K={K}_{1} \oplus {K}_{2} \oplus {K}_{3}\) with length \(m\) (e.g., \(m=3\)). \({P}_{1}\), \({P}_{2}\), and \({P}_{3}\) have three private keys \({K}_{1}^{^{\prime}}\), \({K}_{2}^{^{\prime}}\), and \({K}_{3}^{^{\prime}}\), respectively, with length \(m+nl\), e.g., \(m+nl=3+(3*3)=12\); here \(nl\) is the number of decoy states for checking the security of all quantum channels in one complete circle, and for the \(n\) circle it will be \(m+nl\). Here, there are three complete circles for three participants, and the number of decoy qubits for checking the security of all quantum channels is \(n*n$$l$$=9l\). Also, we assume that, \({K}_{1}^{^{\prime}}=000001101101\), \({K}_{2}^{^{\prime}}=111011101000\), and \({K}_{3}^{^{\prime}}=110011010110\).
The server generates a sequence of quantum states contains 12 random states (e.g., \({S}_{1}=\) \(\left|0\right.\rangle ,\left|0\right.\rangle , \left|0\right.\rangle , \left|1\right.\rangle \left|0\right.\rangle , \left|0\right.\rangle , \left|1\right.\rangle \left|0\right.\rangle , \left|1\right.\rangle ,\left|-\right.\rangle ,\left|+\right.\rangle , \left|-\right.\rangle\)) for the first circle and sends it to \({P}_{1}\). \({P}_{1}\) checks the security of the transmission with the server as in Step (4). Based on her/his private data (\({K}_{1}^{^{\prime}}\)), \({P}_{1}\) applies the unitary operations {\(I,I,I,I, I,U,U,I,U,U,I,U\)} to \({S}_{1}\) getting \({S}_{1\mapsto 2}=\left|0\right.\rangle , \left|0\right.\rangle , \left|0\right.\rangle , \left|1\right.\rangle \left|0\right.\rangle , -\left|1\right.\rangle , \left|0\right.\rangle \left|0\right.\rangle , \left|0\right.\rangle ,-\left|+\right.\rangle ,\left|+\right.\rangle , -\left|+\right.\rangle\). To secure the communication, \({P}_{1}\) inserts some decoy qubits into \({S}_{1\mapsto 2}\) and sends \({S}_{1\mapsto 2}\) to \({P}_{2}\). Subsequently, \({P}_{2}\) performs Step (5.b) to detect the external attack.
As in Step (5.c), the server chooses random \(l\) states (e.g., \(l=1\)) from \({S}_{1}\) and announce the position of \(l\) (e.g., the position of last state in \({S}_{1}\)) to \({P}_{1}\) and \({P}_{2}\). The server asks \({P}_{1}\) to announce the unitary operation that was applied to \(l\), and asks \({P}_{2}\) to announce the measurement result of the corresponding states in \({S}_{1\mapsto 2}\) (i.e., \(-\left|+\right.\rangle\)), respectively. Based on the announced information (\(\left|-\right.\rangle\), \(U\), \(-\left|+\right.\rangle\)), the server can judge whether \({P}_{2}\) has received genuine information or not.
Later, the server and \({P}_{2}\) discard the last sequence from \({S}_{1}\) and \({S}_{1\mapsto 2}\) getting newly updated sequences \({S}_{1}=(\left|0\right.\rangle , \left|0\right.\rangle , \left|0\right.\rangle , \left|1\right.\rangle \left|0\right.\rangle , \left|0\right.\rangle , \left|1\right.\rangle \left|0\right.\rangle , \left|1\right.\rangle ,\left|-\right.\rangle ,\left|+\right.\rangle\)) and \({S}_{1\mapsto 2}=(\left|0\right.\rangle , \left|0\right.\rangle , \left|0\right.\rangle , \left|1\right.\rangle \left|0\right.\rangle , -\left|1\right.\rangle , \left|0\right.\rangle \left|0\right.\rangle , \left|0\right.\rangle ,-\left|+\right.\rangle ,\left|+\right.\rangle\)), respectively. Also, all participants update their private keys by discarding the corresponding classical bits. The updated private keys of \({P}_{1}\), \({P}_{2}\), and \({P}_{3}\) become \({K}_{1}^{^{\prime}}=00000110110\), \({K}_{2}^{^{\prime}}=11101110100\), and \({K}_{3}^{^{\prime}}=11001101011\), respectively. They also consume two quantum states (e.g., the last two states) for checking the quantum channel between (\({P}_{2}\) and \({P}_{3}\)) and (\({P}_{3}\) and \({P}_{1}\)).
The updated private keys after completing one circle are as follows: \({K}_{1}^{^{\prime}}=000001101\), \({K}_{2}^{^{\prime}}=111011101\), and \({K}_{3}^{^{\prime}}=110011010\). And the updated private keys after completing the three circles are as follows: \({K}_{1}^{^{\prime}}=000\), \({K}_{2}^{^{\prime}}=111\), and \({K}_{3}^{^{\prime}}=110\). Now, \(\left|K\right|=\left|{K}_{1}\right|=\left|{K}_{2}\right|=\left|{K}_{3}\right|=\left|{K}_{1}^{^{\prime}}\right|=\left|{K}_{2}^{^{\prime}}\right|=\left|{K}_{2}^{^{\prime}}\right|\). Finally, each participant can get the final key \(K={K}_{1} \oplus {K}_{2} \oplus {K}_{3}=000 \oplus 111\oplus110=001\). Note that for simplicity, we assumed that the server frequently chooses the last qubit for checking the security of communication; but the selected positions should be completely random.
Applying the proposed model to SCWZ’s protocol
Taking SCWZ’s protocol19 as an example, we show in this section how to address the vulnerability of CT-MQKA protocols to the collusive attack.
In SCWZ’s protocol19, there are \(n\) participants and each participant \({P}_{i}\) (\(i=1, 2, \dots , n\)) has an m-bit key (\({K}_{i}\)). All participants want to fairly generate a shared secret key (\(K={K}_{1} \oplus {K}_{2} \oplus \cdots \oplus {K}_{n}\)). Also, there is a server that generates \(n\) sequences of random single-photons. Each sequence \({S}_{i}\) contains \(m\) random single-photons. The server generates additional \(n\) sequences of random single photons (\({C}_{i}\)), which are used as decoy photons to check the existence of eavesdroppers.
Based on our proposed model, SCWZ’s protocol should be modified as follows.
-
1-
Each participant (\({P}_{i}\)) should prepare the length of her/his private keys (\({K}_{i}\)) to be \(m+nl\).
-
2-
The length of the quantum sequences generated by the server should also be \(m+nl\).
-
3-
As in Step (5.b), \({P}_{i}\) should generate a sequence of random single-qubits (\({C}_{pi}\)) to check the security of the quantum channel between the sender (\({P}_{i}\)) and receiver (\({P}_{i+1}\)).
-
4-
To detect the collusive attack, the server randomly selects \(l\) single-qubits from the \(m+nl\) single-qubits and uses them as decoy qubits to check the security of quantum channels between every two participants, as proposed in Step (5.c).
-
5-
All participants update their keys by discarding the classical bits corresponding to the single qubits that were used as decoy qubits.
The security analysis
This section presents detailed security analyses for both external eavesdropping and internal attacks.
External attack
In the proposed protocol, the decoy qubit technique is used to prevent external eavesdroppers from attacking the protocol. To achieve that, a sequence of single decoy qubits is randomly selected from the states {\(\left|+\right.\rangle ,\boldsymbol{ }\left|-\right.\rangle ,\boldsymbol{ }\left|0\right.\rangle ,\boldsymbol{ }\left|1\right.\rangle\)} and randomly inserted into the secret message. The eavesdropper (Eve) cannot distinguish between the decoy-states and secret message states. Eve may try to entangle a secret message state with an auxiliary quantum state (\(\left|{\varvec{\epsilon}}\right.\rangle\)) by applying a unitary operation (\({{\varvec{U}}}_{{\varvec{\epsilon}}}\)) as follows:
In (5) and (6), \({\left|{\alpha }_{1}\right|}^{2}+{\left|{a}_{2}\right|}^{2}=1\) and \({\left|{\alpha }_{3}\right|}^{2}+{\left|{\alpha }_{4}\right|}^{2}=1\). Also, \(\left|{\epsilon }_{00}\right.\rangle\), \(\left|{\epsilon }_{01}\right.\rangle\), \(\left|{\epsilon }_{10}\right.\rangle\), and \(\left|{\epsilon }_{11}\right.\rangle\) are four ancilla states decided by Eve. To pass the external eavesdropping detection phase, Eve sets \({\alpha }_{2}={\alpha }_{3}=0\), if the targeted quantum state is \(\left|0\right.\rangle\) or \(\left|1\right.\rangle\), and \(\left({\alpha }_{1}\left|{e}_{00}\right.\rangle +{\alpha }_{2}\left|{e}_{01}\right.\rangle -{\alpha }_{3}\left|{e}_{10}\right.\rangle -{\alpha }_{4}\left|{e}_{11}\right.\rangle \right)= \left({\alpha }_{1}\left|{e}_{00}\right.\rangle -{\alpha }_{2}\left|{e}_{01}\right.\rangle +{\alpha }_{3}\left|{e}_{10}\right.\rangle -{\alpha }_{4}\left|{e}_{11}\right.\rangle \right)=0\), if the targeted quantum state is \(\left|+\right.\rangle\) or \(\left|-\right.\rangle\). But these malicious procedures cannot help Eve to extract any useful information from the private inputs. For example, if Eve sets \({\alpha }_{2}={\alpha }_{3}=0\), she gets \({\left|{\alpha }_{1}\right|}^{2}={\left|{\alpha }_{4}\right|}^{2}=1\), which means that \({\alpha }_{1}\left|{\epsilon }_{00}\right.\rangle ={\alpha }_{4}\left|{\epsilon }_{11}\right.\rangle\). So, Eve cannot reveal private inputs. Besides, the proposed CT-MQKA protocol is not open to the Trojan horse attack since all information is sent in a one-way manner30,31.
Internal attack
In the proposed model, internal attacks may be divided into three types of attacks: (1) Server’s attack; (2) Participant’s attack; (3) Collusive attack. Participant’s attack is similar to server’s attack in this work. Therefore, we only discuss here the server’s attack and collusive attack.
Server’s attack
In this work, we assume that the server is semi-honest. That is, it faithfully executes the operations delegated by participants and does not collude with other participants to steal sensitive information, but may try to get the information of secret keys. Participants employ the decoy photon method to secure the communications between every two participants. Hence, the server must adopt one of the external attack strategies if it wants to get sensitive information. However, we show in the “External attack” section that the proposed model is secure against external attacks. Accordingly, the malicious server may resort to guessing the required information or generate the final key as follows:
-
a)
Passing the security check. In Step (1), the server sends \({S}_{i}\) to \({P}_{i}\) as an initial quantum sequence for generating the final key. In Step (5), \({P}_{i}\) uses \({S}_{i}\) to encode her/his private data and inserts some decoy qubits for security check before sending them to \({P}_{i+1}\). To successfully pass the security check, the server must correctly guess the measurement bases of the decoy qubits and guess the initial bases to correctly resend \({P}_{i}\)’s qubits to \({P}_{i+1}\) without been caught. The probability of correctly guessing a measurement basis for each qubit is 50%, and the probability of correctly guessing an initial basis is also 50%. Therefore, the probability (\(pr\)) of passing the eavesdropping check is as follows:
$$pr={pr}_{1}\times {pr}_{2}\times \dots \times {pr}_{\text{n}}={\left(\frac{1}{2}\times \frac{1}{2}\right)}^{nl}\times {\left(\frac{1}{2}\times \frac{1}{2}\right)}^{nl}\times \dots \times {\left(\frac{1}{2}\times \frac{1}{2}\right)}^{nl}={\left(\frac{1}{2}\times \frac{1}{2}\right)}^{nl}.$$(9)here, \({pr}_{i}\) (\(i={1,2},\dots ,n\)) is the probability of correctly guessing the \(i\)th sequence of decoy qubits, and \(l\) is the length of each decoy qubit sequence.
-
b)
Guessing participants’ private keys. Since \(K={K}_{1} \oplus {K}_{2} \oplus \cdots \oplus {K}_{n}\), the server needs to correctly guess all participants’ private keys to get \(K\). The probability (\(pr\)) of correctly guessing the final key \(K\) is as follows:
$$pr={pr}_{1}\times {pr}_{2}\times \dots \times {pr}_{\text{n}}={{\left(\frac{1}{2}\right)}^{l}\times {\left(\frac{1}{2}\right)}^{l}\times \dots {\times \left(\frac{1}{2}\right)}^{l}=\left(\frac{1}{2}\right)}^{nl}.$$(10)here, \({pr}_{i}\) (\(i={1,2},\dots ,n\)) is the probability of correctly guessing \({K}_{i}\), and \(l\) is the length of \({K}_{i}\).
-
c)
Guessing the final key (\(K\)). The server may try to directly guess the final key (\(K\)). In that case, the probability (\(pr\)) is as follows:
$$pr={\left(\frac{1}{2}\right)}^{l},{\text{ where }}l{\text{ is the length of }}K.$$(11)In Eqs. (9–11), if \(l\) is large enough the probability of guessing the final key or required information is close to zero or negligible.
Collusive attack
A collusive attack is the most powerful internal attack in which two or more dishonest participants collude together to extract sensitive information or generate the final key alone without revealing their malicious behaviour. In this section, we show that the proposed model is immune to collusive attacks, such that any group of dishonest participants trying to perform a collusive attack (including the two attack strategies mentioned in the section The insecurity of existing CT-MQKA protocols) will be detected immediately.
Basically, dishonest participants rely on two important processes to successfully achieve the collusive attack; (1) sharing information about the carrier quantum states that will be used to encode the private data and generate the final key, (2) deceiving the honest participants to deduce their private data by sending forged data. In our protocol, a semi-honest server is used to prevent dishonest participants from sending forged data to the honest ones. The server generates \({S}_{i}\) with decoy qubits in Step (1) and sends it to \({P}_{i}\) in Step (2). In Step (5.b), \({P}_{i}\) sends her/his encoded sequence to \({P}_{i+1}\). To prevent the collusive attack, in Step (5. c), the server participates in checking the security of transmission to make sure that \({P}_{i}\) does not send forged qubits to \({P}_{i+1}\) by randomly selecting some qubits and asking the participants to divulge the related information. Accordingly, the protocol guarantees that the honest participant has received genuine data, and the dishonest participants cannot obtain useful information to generate the final key alone or steal the private inputs of honest participants.
Moreover, if the dishonest participants try to adopt guessing strategies they will be detected with high probability as indicated in Eqs. (9–11). Thus, we can say that the proposed model is secure against internal attacks.
Conclusion
In this work, we showed that most of the existing circular-type multiparty quantum key agreement protocols are insecure against a specific type of collusive attack. We analyzed the security of a recently proposed circular-type multiparty quantum key agreement protocol to demonstrate the vulnerability of such protocols. Then, we proposed a general secure quantum key agreement model to avoid the different types of collusive attacks. We showed that the proposed protocol could generate the final key correctly and that the proposed protocol is secure against all known collusive attack strategies.
References
Diffie, W. & Hellman, M. New directions in cryptography. IEEE Trans. Inf. Theory 22, 644–654 (1976).
Ingemarsson, I., Tang, D. & Wong, C. A conference key distribution system. IEEE Trans. Inf. Theory 28, 714–720 (1982).
Pieprzyk, J. & Li, C.-H. Multiparty key agreement protocols. IEE Proc. Comput. Digital Tech. 147, 229–236 (2000).
Bernstein, D. J. & Lange, T. Post-quantum cryptography. Nature 549, 188–194 (2017).
Alagic, G. et al. Status Report on the Second Round of the NIST Post-Quantum Cryptography Standardization Process (US Department of Commerce, 2020).
Bennet, C. & Brassard, G. in Proc. of IEEE Int. Conf. on Comp., Syst. and Signal Proc., Bangalore, India, Dec. 10–12 (1984).
Abulkasim, H., Farouk, A., Hamad, S., Mashatan, A. & Ghose, S. Secure dynamic multiparty quantum private comparison. Sci. Rep. 9, 1–16 (2019).
Abulkasim, H. et al. Improving the security of quantum key agreement protocols with single photon in both polarization and spatial-mode degrees of freedom. Quant. Inf. Process. 17, 316 (2018).
Wu, W., Cai, Q., Wu, S. & Zhang, H. Cryptanalysis of He’s quantum private comparison protocol and a new protocol. Int. J. Quant. Inf. 17, 1950026 (2019).
Qi, R. et al. Implementation and security analysis of practical quantum secure direct communication. Light Sci. Appl. 8, 1–8 (2019).
Li, L. & Li, Z. A verifiable multiparty quantum key agreement based on bivariate polynomial. Inf. Sci. 521, 343–349 (2020).
Abulkasim, H. & Alotaibi, A. Improvement on ‘Multiparty Quantum Key Agreement with Four-Qubit Symmetric W State’. Int. J. Theor. Phys. 58, 4235–4240 (2019).
Shi, R.-H. & Zhang, M. Privacy-preserving quantum sealed-bid auction based on grover’s search algorithm. Sci. Rep. 9, 1–10 (2019).
Bao, N. & Halpern, N. Y. Quantum voting and violation of Arrow’s impossibility theorem. Phys. Rev. A 95, 062306 (2017).
Chowdhury, A. et al. Quantum signature of a squeezed mechanical oscillator. Phys. Rev. Lett. 124, 023601 (2020).
Abulkasim, H. et al. Improved dynamic multi-party quantum private comparison for next-generation mobile network. IEEE Access 7, 17917–17926 (2019).
Zhou, N., Zeng, G. & Xiong, J. Quantum key agreement protocol. Electron. Lett. 40, 1149–1150 (2004).
Liu, B., Xiao, D., Jia, H.-Y. & Liu, R.-Z. Collusive attacks to “circle-type” multi-party quantum key agreement protocols. Quantum Inf. Process. 15, 2113–2124 (2016).
Sun, Z., Cheng, R., Wu, C. & Zhang, C. New fair multiparty quantum key agreement secure against collusive attacks. Sci. Rep. 9, 1–8 (2019).
Sun, Z., Wu, C., Zheng, S. & Zhang, C. Efficient multiparty quantum key agreement with a single d-level quantum system secure against collusive attack. IEEE Access 7, 102377–102385 (2019).
Liu, H.-N., Liang, X.-Q., Jiang, D.-H., Zhang, Y.-H. & Xu, G.-B. Multi-party quantum key agreement protocol with bell states and single particles. Int. J. Theor. Phys. 58, 1659–1666 (2019).
Liu, W.-J., Chen, Z.-Y., Ji, S., Wang, H.-B. & Zhang, J. Multi-party semi-quantum key agreement with delegating quantum computation. Int. J. Theor. Phys. 56, 3164–3174 (2017).
Shi, R.-H. & Zhong, H. Multi-party quantum key agreement with bell states and bell measurements. Quantum Inf. Process. 12, 921–932 (2013).
Wang, L. & Ma, W. Quantum key agreement protocols with single photon in both polarization and spatial-mode degrees of freedom. Quantum Inf. Process. 16, 130 (2017).
Liu, H.-N., Liang, X.-Q., Jiang, D.-H., Xu, G.-B. & Zheng, W.-M. Multi-party quantum key agreement with four-qubit cluster states. Quantum Inf. Process. 18, 242 (2019).
Huang, W. et al. Efficient multiparty quantum key agreement with collective detection. Sci. Rep. 7, 1–9 (2017).
Zhou, Y.-H., Zhang, J., Shi, W.-M., Yang, Y.-G. & Wang, M.-F. Continuous-variable multiparty quantum key agreement based on third party. Mod. Phys. Lett. B 34, 2050083 (2020).
Cao, H. & Ma, W. Multi-party traveling-mode quantum key agreement protocols immune to collusive attack. Quantum Inf. Process. 17, 219 (2018).
Huang, W.-C., Yang, Y.-K., Jiang, D., Gao, C.-H. & Chen, L.-J. Designing secure quantum key agreement protocols against dishonest participants. Int. J. Theor. Phys. 58, 4093–4104 (2019).
Li, X.-H., Deng, F.-G. & Zhou, H.-Y. Improving the security of secure direct communication based on the secret transmitting order of particles. Phys. Rev. A 74, 054302 (2006).
Deng, F.-G., Li, X.-H., Zhou, H.-Y. & Zhang, Z.-J. Improving the security of multiparty quantum secret sharing against Trojan horse attack. Phys. Rev. A 72, 044302 (2005).
Acknowledgements
This research was funded by the Natural Sciences and Engineering Research Council of Canada and NXM Labs Inc. NXM’s autonomous security technology enables devices, including connected vehicles, to communicate securely with each other and their surroundings without human intervention while leveraging data at the edge to provide business intelligence and insights. NXM ensures data privacy and integrity by using a novel blockchain-based architecture which enables rapid and regulatory-compliant data monetization. Ryerson University is in the “Dish With One Spoon Territory”. The Dish With One Spoon is a treaty between the Anishinaabe, Mississaugas and Haudenosaunee that bound them to share the territory and protect the land. Subsequent Indigenous Nations and peoples, Europeans and all newcomers, have been invited into this treaty in the spirit of peace, friendship and respect. Wilfrid Laurier University is located on the traditional territory of the Neutral, Anishnawbe and Haudenosaunee peoples. We thank them for allowing us to conduct research on their land.
Author information
Authors and Affiliations
Contributions
H.A. designed the scheme. H.A., A.M. and S.G. did security analysis and comparisons. All authors contributed to the writing and discussion of the paper.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Abulkasim, H., Mashatan, A. & Ghose, S. Secure multiparty quantum key agreement against collusive attacks. Sci Rep 11, 9456 (2021). https://doi.org/10.1038/s41598-021-88837-w
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-021-88837-w
This article is cited by
-
Multi-Party Quantum Key Agreement with Four-Qubit Cluster States Immune to Collusive Attack
International Journal of Theoretical Physics (2024)
-
New Semi-Quantum Key Agreement Protocol Based on the χ-Type Entanglement States
International Journal of Theoretical Physics (2022)
-
Multi-party Quantum Key Agreement Protocol with Authentication
International Journal of Theoretical Physics (2021)
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.