Abstract
Quantum conference key agreement is an important cryptographic primitive for future quantum network. Realizing this primitive requires high-brightness and robust multiphoton entanglement sources, which is challenging in experiment and unpractical in application because of limited transmission distance caused by channel loss. Here we report a measurement-device-independent quantum conference key agreement protocol with enhanced transmission efficiency over lossy channel. With spatial multiplexing nature and adaptive operation, our protocol can break key rate bounds on quantum communication over quantum network without quantum memory. Compared with previous work, our protocol shows superiority in key rate and transmission distance within the state-of-the-art technology. Furthermore, we analyse the security of our protocol in the composable framework and evaluate its performance in the finite-size regime to show practicality. Based on our results, we anticipate that our protocol will play an important role in constructing multipartite quantum network.
Similar content being viewed by others
Introduction
Using quantum physics to process information and building a network with quantum nature in a connected world has established various benefits. Quantum computers offer algorithm speedups1,2,3,4, which are advantageous in interdisciplinary fields such as machine learning5,6. Quantum communication, especially quantum key distribution and entanglement-assisted point-to-point communication, provides information-theoretic security7,8. In addition, network protocols including blind quantum computation9,10, distributed quantum computation11, quantum secret sharing12,13,14, and quantum conference key agreement (QCKA)15,16,17,18,19,20 have emerged as important building blocks for multiuser applications as well.
Conference key agreement is a cryptographic primitive that shares information-theoretic secure keys among more than two authenticated users for group encryption and decryption15. This classical cryptographic primitive is vulnerable and no longer secure in the face of eavesdroppers with quantum resources. Multiple quantum key distribution links21,22,23,24,25,26,27,28,29,30,31 can be directly applied to protect against quantum eavesdroppers. However, repetitive use of quantum key distribution links restricts the communication efficiency in a fully connected quantum network. Alternatively, multipartite entangled states can be used to realize QCKA for achieving a genuine advantage over the point-to-point quantum communication protocols32. Several experimental works on multipartite quantum communication and distribution of the Greenberger-Horne-Zeilinger (GHZ) entanglement33,34 have been demonstrated35,36,37,38,39,40. Nevertheless, these works remain quite unpractical due to their low key rates and fragility of entanglement resources. To avoid requiring entanglement preparation beforehand, a scheme for distributing the postselected GHZ entanglement41 was proposed which combined the decoy-state23,24,25 and measurement-device-independent (MDI) idea26,27. However, with the increase in the number of users, this protocol is limited in terms of long-distance deployment due to universal limitations on channel loss42. In recent years, various multiparty quantum communication protocols have been proposed and analysed13,18,19,43 to enhance the key rate performance for long distance deployment. Whereas these protocols are measurement device dependent and cannot be directly extended to more than three participants. Furthermore, most works analysed the security of QCKA with infinite resources and calculated the secret key rate in the asymptotic limit, while few works consider finite-key effects43,44.
In all-photonic quantum repeater45, cluster states are utilized to demonstrate polynomial scaling of transmission efficiency with distance which is in fact the idea of spatial multiplexing and adaptive operation. Similarly, this idea is applied in adaptive MDI quantum key distribution protocol46, where both users send multiple single photon states simultaneously to the central relay who subsequently confirms the arrival of photons by applying quantum non-demolition (QND) measurement and pairs the arrived photons adaptively.
Inspired by the all-photonic quantum repeater45 and adaptive MDI quantum key distribution46, in this work, we propose an MDI-QCKA protocol with the principle of spatial multiplexing and adaptive operation. We investigate the performance of our protocol and the result shows it breaks universal limitations on key rate under at least ten users over the network without quantum memory. Compared with other existing QCKA protocols, our protocol outperforms under three users in terms of higher key rates and transmission distance which is >300 km within experimentally feasible parameter regime. Our protocol can be extended to any number of users flexibly and thus fits well in network deployment. On the other hand, our protocol is immune to all detection-side attacks because of its MDI nature. Furthermore, we establish the security analysis of our protocol in the composable framework and evaluate the performance in the finite-key regime. Based on our results, we believe our protocol manifests potential to be an important building block for practical multiparty applications for quantum networks in the future.
Results
Quantum conference key agreement protocol
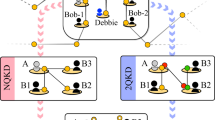
We propose an n-party MDI-QCKA protocol to establish postselected GHZ entanglement with spatial multiplexing and adaptive operation. Here we denote the ith user as Ai(i = 1, …, n) and the untrusted central relay as node C. In Fig. 1a, we show the overall structure of our protocol with n user nodes over network. In Fig. 1b, we show detailed process between Ai and the node C. Our protocol is described as follows.
-
(i) All n users \({({A}_{i})}_{i = 1}^{n}\) generate M single-photon states that are randomly selected from eigenstates of the Z and X basis. For instance, one selects from \(\{\left\vert H\right\rangle ,\left\vert V\right\rangle ,(\left\vert H\right\rangle +\left\vert V\right\rangle )/\sqrt{2},(\left\vert H\right\rangle -\left\vert V\right\rangle )/\sqrt{2}\}\) when using polarization encoding. \({({A}_{i})}_{i = 1}^{n}\) then transmit the M single-photon states to node C simultaneously using spatial multiplexing.
-
(ii) Node C performs QND measurements to confirm the arrival of single-photon states from \({({A}_{i})}_{i = 1}^{n}\).
-
(iii) After the QND measurements, the confirmed photons from every user form a group via optical switches. Node C then performs GHZ projection measurement on the group. Each user should successfully transmit at least one single photon through QND measurements. Otherwise this trial is considered to be failed.
-
(iv) Node C announces the group information and the GHZ projection results. Each Ai keeps information of states that are successfully projected onto the GHZ state and discards the rest.
-
(v) All n communication users \({({A}_{i})}_{i = 1}^{n}\) announce their preparing bases for the trials successfully projected onto the GHZ state. If the bases of all parties are the same, the round is kept. The process is repeated until enough rounds have been kept for key generation and parameter estimation.
-
(vi) The above process is repeated until m trials have been kept for key generation and k trials have been kept for parameter estimation. m trials of data for key generation are in the Z basis. k trials of data for parameter estimation are in the X basis.
-
(vii) If the test passes, all n users verify the correctness and proceed with error correction and privacy amplification. If we designate A1 as the conference key reference during error correction, then A1 performs a pairwise information reconciliation with each one of the remaining users. In this process, each one of the remaining users computes a guess of A1’s raw key. If the check passes, they obtains the final secret keys.
a Network structure of our protocol with n user nodes. b Detailed process between Ai and the node C. Ai prepares and transmits multiple quantum signals to the central node C through quantum channel. At node C the signals are confirmed by quantum non-demolition (QND) measurement and then routed to the Greenberger-Horne-Zeilinger (GHZ) analyser through optical switches. In this process, spatial multiplexing and adaptive operations are used to improve the efficiency of our protocol.
Security analysis
The security of our MDI-QCKA can be generalized directly from the analysis of quantum key distribution44. Without loss of generality, we designate A1 as the key reference to conduct classical postprocessing. In general, A1’s final key S1 can be quantum mechanically correlated with a quantum state held by the adversary. We can define the classical-quantum state describing the correlated system of A1’s final key S1 and eavesdropper E
where the sum is over all possible strings and \({\rho }_{{{{{{{{\rm{E}}}}}}}}}^{{{{{{{{{\bf{S}}}}}}}}}_{1}}\) is the joint state of eavesdropper given S1.
Ideally a QCKA protocol is secure if it is correct and secret. The correctness means every user holds identical bit strings. The secrecy requires \({\rho }_{{{{{{{{{\bf{S}}}}}}}}}_{1},{{{{{{{\rm{E}}}}}}}}}={\sum }_{{{{{{{{{\bf{S}}}}}}}}}_{1}}\frac{1}{| {{{{{{{{\bf{S}}}}}}}}}_{1}| }\left\vert {{{{{{{{\bf{S}}}}}}}}}_{1}\right\rangle \left\langle {{{{{{{{\bf{S}}}}}}}}}_{1}\right\vert \otimes {\sigma }_{{{{{{{{\rm{E}}}}}}}}}\), which means the joint system of the eavesdropper is decoupled from A1. However, these two conditions can never be met perfectly. Therefore, in practice we define an ϵc-correct and ϵs-secret QCKA protocol. A QCKA protocol is ϵc-correct if
where Si is the final key string of the ith user. A QCKA protocol is ϵs-secret if
D( ⋅ , ⋅ ) is the trace distance and ppass is the probability that the protocol does not abort. A QCKA protocol is called \({\epsilon }_{\sec }\)-secure with \({\epsilon }_{\sec }\le {\epsilon }_{{{{{{{{\rm{c}}}}}}}}}+{\epsilon }_{{{{{{{{\rm{s}}}}}}}}}\) if it is ϵc-correct and ϵs-secret.
Following the result of quantum key distribution47, the extractable amount of key l for a ϵc-correct and ϵs-secret QCKA is
where \({H}_{\min }^{\epsilon }({{{{{{{\bf{Z}}}}}}}}| E)\) is the conditional smooth min-entropy characterizing the average probability that the eavesdropper guesses A1’s raw key Z1 correctly using optimal strategy and leakEC is the amount of information leakage of error correction. ϵ and \(\bar{\epsilon }\) are positive constants proportional to ϵs. In a realistic scenario, following previous work44, the computable key length of our QCKA protocol is
where \(\mu (\lambda ,\epsilon )=\frac{\frac{(1-2\lambda )AG}{m+k}+\sqrt{\frac{{A}^{2}{G}^{2}}{{(m+k)}^{2}}+4\lambda (1-\lambda )G}}{2+2\frac{{A}^{2}G}{{(m+k)}^{2}}}\) with λ being the error rate observed in parameter estimation, \(A=\max \{m,k\}\) and \(G=\frac{m+k}{mk}\ln \frac{m+k}{2\pi mk\lambda (1-\lambda ){\epsilon }^{2}}\). q is the preparation quality quantifying the incompatibilities of two measurements. Detailed proof of the computable key length is shown in Supplementary Note 1.
Numerical simulation
Before analysing the performance of our protocol, we discuss the universal limitations on quantum communication over network and provide a benchmark for our protocol.
For point-to-point protocols, a fundamental upper limit on the secret key rate over a lossy optical channel not assisted by any quantum repeater is given by \({\log }_{2}(\frac{1+\eta }{1-\eta })\) with η being the transmissivity between two users48. A general methodology allowing to upperbound the two-way capacities of an arbitrary quantum channel with a computable single-letter quantity was devised in49, where the maximum rate achievable by any optical implementation of point-to-point quantum key distribution is given by \(-{\log }_{2}(1-\eta )\) for the lossy channel. For quantum communications over network scenarios, bounds have also been established under different scenarios50,51. Furthermore, Das et al. provided a unifying framework to upperbound the key rates of both bipartite and conference settings with different scenarios42.
In our work, to investigate the performance of our protocol, we consider a rate benchmark in a case where the untrusted central node is removed and all n users are linked by a star network43. In such scenario, one user is selected and he performs quantum key distribution with every other n − 1 users to establish bipartite secret keys with the same length due to the network symmetry. The selected user can encode the conference key with the established keys to conduct conference key agreement protocol. According to the secret-key capacity, the asymptotic rate is \(-{\log }_{2}(1-\eta )\) with \(\sqrt{\eta }\) being the transmissitivity of the channel from any ith user to the central relay. Therefore, in this scenario, the key rate is bounded by \(\frac{-{\log }_{2}(1-\eta )}{n-1}\). It should be noted that the above scenario does not necessarily yield the highest key rate in QCKA. We denote this bound as the direct transmission bound and use it as a benchmark to evaluate our protocol.
In the asymptotic limit, the key rate of QCKA is given by41
where QZ, is the gain of the Z basis since QCKA generates keys using data from the Z basis. \(\{{E}_{{{{{{{{\rm{Z}}}}}}}}}^{1,i},i=2,\ldots ,n\}\) are marginal error rates, which describe the bit error rates between the first user and the ith user. EX is the phase error rate. Without loss of generality, here we designate the first user as key reference.
The gain QZ is defined as the efficiency of successful GHZ projection. Specifically, we have \({Q}_{{{{{{{{\rm{Z}}}}}}}}}=\frac{\bar{N}}{M}\), where \(\bar{N}\) is the average number of postselected GHZ entangled states formed by successfully transmitted photons using M multiplexing. Intuitively, if we consider M multiplexing and the total efficiency from any ith user to the central node ηt including loss and success probability of GHZ projection, then \(\bar{N} \sim M{\eta }_{{{{{{{{\rm{t}}}}}}}}}\). Therefore, we have QZ ~ ηt. The approximate relation can be converted to an equation QZ = ηt under the asymptotic limit (M → ∞). We prove this equation when n = 3 in Supplementary Note 2. To guarantee that more than one postselected GHZ entangled state is generated on average, the number of multiplexing should satisfy \(M\ge {\eta }_{{{{{{{{\rm{t}}}}}}}}}^{-1}\), which implies that \(\bar{N} \sim M{\eta }_{{{{{{{{\rm{t}}}}}}}}}\ge 1\).
In Fig. 2, we plot the key rates of our QCKA as well as direct transmission bounds as a function of distance between any ith party and the central relay with different numbers of communication parties. The experimental parameters used in the numerical simulation is presented in Methods. Here we consider a symmetric structure where the distance between any user to the central relay is equal. We present key rates and bounds with n = 3, 10 users from top to bottom using solid and dash-dotted lines respectively. From the simulation results, our protocol overcomes the direct transmission bounds, which stems from the spatial multiplexing and adaptive operations of our protocol. Regardless of the increasing number of communication parties, a polynomial scaling of efficiency with distance can be realized while the bounds attenuate greatly as n increases. One can also notice that the key rates of our protocol decrease with increasing n due to the higher error rate when there are more users.
We show key rates of our protocol and corresponding bounds under different numbers of communication parties (n = 3, 10 from top to bottom). In the figure, key rates of our protocol and bounds are plotted with solid and dash-dotted lines, respectively. The fiber transmission distance denotes the distance between any ith party and the central relay.
To further investigate the performance of our work, we evaluate the key rate of our protocol and that of other preceding quantum communication protocols over quantum network under the same experimental parameters. In Fig. 3, we plot the key rate of our QCKA protocol, MDI-quantum cryptographic conferencing41, MDI star-network module52, and conference key agreement with single-photon interference43 under n = 3 and n = 6. Our work can reach >300 km when n = 3 and >290 km when n = 6, which shows the capability of intercity scale deployment. Therefore, the advantage of our work remains as n grows larger. For MDI-quantum cryptographic conferencing, since the gain attenuates exponentially with increasing n, the key rate decreases in a similar way. The key rate of conference key agreement with single-photon interference shows a performance approximate to that of our work. However, the conference key agreement with single-photon interference requires each party to prepare an entangled state \(\left\vert \phi \right\rangle =\sqrt{q}\left\vert 0\right\rangle \left\vert 0\right\rangle +\sqrt{1-q}\left\vert 1\right\rangle \left\vert 1\right\rangle\) where q is a parameter to be optimized in simulation. Preparing such entangled state is quite challenging within available technology. A single MDI star-network module can only reach ~1 km as shown in the inset of Fig. 3. Therefore, such modules should be linked together to achieve constant high-rate secure communication over long distances.
We plot key rates of QCKA from our work, measurement-device-independent (MDI)-quantum cryptographic conferencing41, conference key agreement with single-photon interference43, and MDI star-network module52. We plot the key rates of the protocols when (a) n = 3 and (b) n = 6. In this figure, we plot our protocol with solid line and other protocol with dashed lines. For a clear view, the key rate of MDI star-network module52 is depicted in the inset by restricting the transmission distance to (a) 1.2 km and (b) 0.5 km. The fiber transmission distance denotes the distance between any ith party and the central relay.
To make a comprehensive comparison between different protocols, as shown in Table 1, we present a table comparing the aforementioned QCKA protocols in different aspects. To be specific, we present the longest transmission distance and corresponding key rates of different protocols under n = 3, 6, 10 in the first six rows. In the last five rows, we compare the other five different aspects including measurement device independence, requirements on entanglement resource, phase stabilization, QND measurement, and whether the protocol is analyzed in the finite-size regime. From the table, one can observe that our QCKA protocol shows an advantage in the longest transmission distances and the corresponding key rates. In terms of security, all of the aforementioned protocols are measurement-device-independent. Only the conference key agreement with single-photon interference43 requires entanglement resources to conduct the protocol. Our protocol and MDI quantum cryptographic conferencing41 avoid requirements for phase stabilization. However, QND measurement is needed to confirm the arrival of transmitting photons in our protocol, which is still challenging in experiment. Except for MDI quantum cryptographic conferencing41, other protocols have been analyzed in the finite-size regime.
We investigate the performance of our QCKA protocol in the finite-size regime with the same parameters introduced in the asymptotic scenario. Furthermore, we fix ϵc = 10−15 corresponding to a realistic hash tag size in practice53. We also fix the total number of signals L to be 1012. Then the number of trials used for key generation can be calculated as m = pn ⋅ QZ ⋅ L, with p the probability of choosing the Z basis which can be optimized to maximize the key rate l/L. In our protocol, we assume the error correction leakage to be \({{{{{{{{\rm{leak}}}}}}}}}_{{{{{{{{\rm{EC}}}}}}}}}=fmh({E}_{{{{{{{{\rm{Z}}}}}}}}}^{{{{{{{{{\rm{A}}}}}}}}}_{1}{{{{{{{{\rm{A}}}}}}}}}_{i}})+{\log }_{2}\frac{2(n-1)}{{\epsilon }_{{{{{{{{\rm{c}}}}}}}}}}\)44, where we set f = 1.1 and \({E}_{{{{{{{{\rm{Z}}}}}}}}}^{{{{{{{{{\rm{A}}}}}}}}}_{1}{{{{{{{{\rm{A}}}}}}}}}_{i}}\) is the marginal error rate between A1 and Ai. Then following Eq. (5) we can obtain the result in the finite-size regime.
In Fig. 4, we plot the secret key rate of our QCKA protocol as a function of the distance between any ith user and the GHZ analyser. In Fig. 4, we can view that our QCKA protocol can reach >140 km, 60 km, and 40 km when n = 3, 5, 7, respectively. The results are meaningful to practical deployment of an intra- or inter- city quantum network. Therefore, we can anticipate our protocol to be essential in the network applications and important for the construction of a connected quantum world.
Discussion
In this work, we report an MDI-QCKA protocol for quantum network application. We analyse the security of the QCKA protocol with composably secure framework and provide a computable key length in the finite-size regime. The performance of the QCKA protocol under the GHZ analyser based on linear optical elements54 is investigated. Compared with the direct transmission bound of quantum communication over quantum network, our protocol shows great potential in deploying in large-scale quantum network55,56. We also show superiority of our work by directly comparing the key rate of our work with those of previous works in multiparty quantum communication41,43,52. Based on the results of this work, we can anticipate a wide usage of our work in multiparty applications of secure quantum network.
Here we remark on possible directions for future work. We have investigated our protocol under a model consisting of single photon sources, QND measurements, optical switches, and the GHZ analyser based on linear optical elements. Further study can be conducted on evaluating the performance of our protocol using other techniques. For instance, we investigate our protocol with the GHZ analyser based on linear optical elements which can only identify two of n GHZ states. Our protocol can be improved by utilizing the complete GHZ analyser which can identify all 2n GHZ states, such as GHZ state analysis taking into account nonlinear processes57,58 or entangled-state analysis for hyperentangled photon pairs59,60. On the other hand, in step (iii) of our protocol, large scale optical switches are needed to route the photons into the GHZ analyser, which may affect the transmittance and cause unwanted loss. Thus, future effort should be made towards realizing the protocol with reduced scale optical switches and one possible way is utilizing a Hadamard linear optical circuit together with single-mode on/off switches46. Investigation of the robustness of our protocol with the existence of multiple-photon components and imperfections in experimental setups should be conducted. Techniques in MDI quantum key distribution61,62 can be applied in our QCKA to further improve practicality. As we have stated, the all-photonic scheme utilizes cluster states to realize a polynomial scaling with distance which is in fact a result of spatial multiplexing. Therefore, with such spatial multiplexing idea, we can develop other protocols apart from quantum communication with enhanced efficiency. In addition, our work can be further developed to give anonymity to users63 over quantum network for more complex application scenarios.
Note Added.— Recently, we became aware of a relevant work by Carrara et al.64. The authors proposed a QCKA protocol using weack coherent pulses and linear optics and proved its security with multiparty decoy-state method. This protocol can also overcome bounds on the key rate at which conference keys can be established in quantum networks without a repeater.
Methods
Experimental parameters used in numerical simulation
In numerical simulation, we use efficiency ηsps to describe the probability of the single photon source generating single photons and set ηsps = 0.965. We consider the GHZ analyser based on linear optical elements54 capable of identifying two of the n-particle GHZ states. We present the working details of the analyser in Supplementary Note 3. Photons travel through optical fiber channels whose transmittance is determined by \(\sqrt{{\eta }_{{{{{{{{\rm{channel}}}}}}}}}}=\exp (-\frac{l}{{l}_{{{{{{{{\rm{att}}}}}}}}}})\), where the attenuation distance latt = 27.14 km and l is the distance from any ith user to the GHZ analyser. QND measurements are required to confirm the arrival of photons and the success probability of QND measurements is denoted by pQND. To simplify the simulation, we consider a QND measurement for a single photon based on quantum teleportation66, which uses the fact that the teleportation fails when the incoming state is the vacuum state. The QND measurement scheme consists of a Bell state measurement module based on linear optical elements and a parametric down-converter, which we expect is feasible in implementations. With ideal parameters we have pQND = 1/2. Furthermore, with the theoretical and experimental advances in QND measurement of single photons67,68,69, we expect the implementation of our protocol to be easier and more efficient in the foreseeable future. Active feedforward technique is needed to direct the arrived photons to the GHZ analyser via optical switches. We assume the active feedforward costs time τa = 67 ns70, which is equivalent to a lossy channel with the transmittance \({\eta }_{{{{{{{{\rm{a}}}}}}}}}=\exp (-{\tau }_{{{{{{{{\rm{a}}}}}}}}}c/{l}_{{{{{{{{\rm{att}}}}}}}}})\), where c = 2.0 × 108 m s−1 is the speed of light in an optical fiber. Single photon detectors in the GHZ analyser are characterized by an efficiency of ηd = 0.93 and a dark count rate of pd = 1 × 10−9 71, by which we can estimate the success probability of GHZ projection in the X(Z) basis \({Q}_{{{{{{{{\rm{X}}}}}}}}({{{{{{{\rm{Z}}}}}}}})}^{{{{{{{{\rm{GHZ}}}}}}}}}\). Based on the aforementioned assumption on experiment parameters, we analytically estimate the gain with
See Supplementary Note 4 for the concrete process of estimation of the marginal bit error rates and phase error rate.
Data availability
All data in this paper can be reproduced by using the methodology described.
Code availability
The code used to generate the data is available from the corresponding author upon reasonable request.
References
Arute, F. et al. Quantum supremacy using a programmable superconducting processor. Nature 574, 505–510 (2019).
Zhong, H.-S. et al. Quantum computational advantage using photons. Science 370, 1460–1463 (2020).
Zhong, H.-S. et al. Phase-programmable Gaussian Boson sampling using stimulated squeezed light. Phys. Rev. Lett. 127, 180502 (2021).
Wu, Y. et al. Strong quantum computational advantage using a superconducting quantum processor. Phys. Rev. Lett. 127, 180501 (2021).
Liu, Y., Arunachalam, S. & Temme, K. A rigorous and robust quantum speed-up in supervised machine learning. Nat. Phys. 17, 1013–1017 (2021).
Zhou, M.-G. et al. Experimental quantum advantage with quantum coupon collector. Research 2022, 9798679 (2022).
Gisin, N., Ribordy, G., Tittel, W. & Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 74, 145–195 (2002).
Bennett, C. H. & Wiesner, S. J. Communication via one- and two-particle operators on Einstein-Podolsky-Rosen states. Phys. Rev. Lett. 69, 2881–2884 (1992).
Broadbent, A., Fitzsimons, J. & Kashefi, E. Universal blind quantum computation. In 50th Annual IEEE Symposium on Foundations of Computer Science, 517–526 (IEEE, 2009).
Barz, S. et al. Demonstration of blind quantum computing. Science 335, 303–308 (2012).
Buhrman, H. & Röhrig, H. Distributed quantum computing. In Mathematical Foundations of Computer Science 2003 1–20 (Springer Berlin Heidelberg, 2003).
Hillery, M., Bužek, V. & Berthiaume, A. Quantum secret sharing. Phys. Rev. A 59, 1829–1834 (1999).
Gu, J., Cao, X.-Y., Yin, H.-L. & Chen, Z.-B. Differential phase shift quantum secret sharing using a twin field. Opt. Exp. 29, 9165–9173 (2021).
Jia, Z.-Y., Gu, J., Li, B.-H., Yin, H.-L. & Chen, Z.-B. Differential phase shift quantum secret sharing using a twin field with asymmetric source intensities. Entropy 23, 716 (2021).
Chen, K. & Lo, H.-K. Multi-partite quantum cryptographic protocols with noisy GHZ states. Quantum Inf. Comput. 7, 689–715 (2007).
Cao, X.-Y., Gu, J., Lu, Y.-S., Yin, H.-L. & Chen, Z.-B. Coherent one-way quantum conference key agreement based on twin field. New J. Phys. 23, 043002 (2021).
Zhao, S. et al. Phase-matching quantum cryptographic conferencing. Phys. Rev. Applied 14, 024010 (2020).
Li, Z. et al. Finite-key analysis for quantum conference key agreement with asymmetric channels. Quantum Sci. Technol. 6, 045019 (2021).
Cao, X.-Y. et al. High key rate quantum conference key agreement with unconditional security. IEEE Access 9, 128870–128876 (2021).
Fletcher, A. I. & Pirandola, S. Continuous variable measurement device independent quantum conferencing with postselection. Sci. Rep. 12, 17329 (2022).
Bennett, C. H. & Brassard, G. Quantum cryptography: public key distribution and coin tossing. Theor. Comput. Sci. 560, 7–11 (2014).
Ekert, A. K. Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67, 661–663 (1991).
Hwang, W.-Y. Quantum key distribution with high loss: toward global secure communication. Phys. Rev. Lett. 91, 057901 (2003).
Lo, H.-K., Ma, X. & Chen, K. Decoy state quantum key distribution. Phys. Rev. Lett. 94, 230504 (2005).
Wang, X.-B. Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett. 94, 230503 (2005).
Lo, H.-K., Curty, M. & Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108, 130503 (2012).
Braunstein, S. L. & Pirandola, S. Side-channel-free quantum key distribution. Phys. Rev. Lett. 108, 130502 (2012).
Lucamarini, M., Yuan, Z., Dynes, J. F. & Shields, A. J. Overcoming the rate–distance limit of quantum key distribution without quantum repeaters. Nature 557, 400–403 (2018).
Liu, W.-B. et al. Homodyne detection quadrature phase shift keying continuous-variable quantum key distribution with high excess noise tolerance. PRX Quantum 2, 040334 (2021).
Xie, Y.-M. et al. Breaking the rate-loss bound of quantum key distribution with asynchronous two-photon interference. PRX Quantum 3, 020315 (2022).
Zeng, P., Zhou, H., Wu, W. & Ma, X. Mode-pairing quantum key distribution. Nat. Commun. 13, 3903 (2022).
Epping, M., Kampermann, H., Macchiavello, C. & Bruß, D. Multi-partite entanglement can speed up quantum key distribution in networks. New J. Phys. 19, 093012 (2017).
Greenberger, D. M., Horne, M. A. & Zeilinger, A. Going Beyond Bell’s Theorem.In Bell’s Theorem, Quantum Theory, and Conceptions of the Universe, edited by M. Kafatos (Springer Netherlands, Dordrecht, 1989) pp. 69–72.
Mermin, N. D. Extreme quantum entanglement in a superposition of macroscopically distinct states. Phys. Rev. Lett. 65, 1838–1840 (1990).
Tittel, W., Zbinden, H. & Gisin, N. Experimental demonstration of quantum secret sharing. Phys. Rev. A 63, 042301 (2001).
Schmid, C. et al. Experimental single Qubit quantum secret sharing. Phys. Rev. Lett. 95, 230505 (2005).
Chen, Y.-A. et al. Experimental quantum secret sharing and third-man quantum cryptography. Phys. Rev. Lett. 95, 200502 (2005).
Gaertner, S., Kurtsiefer, C., Bourennane, M. & Weinfurter, H. Experimental demonstration of four-party quantum secret sharing. Phys. Rev. Lett. 98, 020503 (2007).
Erven, C. et al. Experimental three-photon quantum nonlocality under strict locality conditions. Nat. Photonics 8, 292–296 (2014).
Proietti, M. et al. Experimental quantum conference key agreement. Sci. Adv. 7, eabe0395 (2021).
Fu, Y., Yin, H.-L., Chen, T.-Y. & Chen, Z.-B. Long-distance measurement-device-Independent multiparty quantum communication. Phys. Rev. Lett. 114, 090501 (2015).
Das, S., Bäuml, S., Winczewski, M. & Horodecki, K. Universal limitations on quantum key distribution over a network. Phys. Rev. X 11, 041016 (2021).
Grasselli, F., Kampermann, H. & Bruß, D. Conference key agreement with single-photon interference. New J. Phys. 21, 123002 (2019).
Grasselli, F., Kampermann, H. & Bruß, D. Finite-key effects in multipartite quantum key distribution protocols. New J. Phys. 20, 113014 (2018).
Azuma, K., Tamaki, K. & Lo, H.-K. All-photonic quantum repeaters. Nat. Commun. 6, 6787 (2015).
Azuma, K., Tamaki, K. & Munro, W. J. All-photonic intercity quantum key distribution. Nat. Commun. 6, 10171 (2015).
Tomamichel, M., Lim, C. C. W., Gisin, N. & Renner, R. Tight finite-key analysis for quantum cryptography. Nat. Commun. 3, 634 (2012).
Masahiro, T., Saikat, G. & Wilde, M. M. Fundamental rate-loss tradeoff for optical quantum key distribution. Nat. Commun. 5, 5235 (2014).
Pirandola, S., Laurenza, R., Ottaviani, C. & Banchi, L. Fundamental limits of repeaterless quantum communications. Nat. Commun. 8, 15043 (2017).
Pirandola, S. End-to-end capacities of a quantum communication network. Commun. Phys. 2, 51 (2019).
Pirandola, S. General upper bound for conferencing keys in arbitrary quantum networks. IET Quantum Commun. 1, 22–25 (2020).
Ottaviani, C., Lupo, C., Laurenza, R. & Pirandola, S. Modular network for high-rate quantum conferencing. Commun. Phys. 2, 118 (2019).
Renner, R. Security of quantum key distribution. Int. J. Quantum Inf. 6, 1–127 (2008).
Pan, J.-W. & Zeilinger, A. Greenberger-Horne-Zeilinger-state analyzer. Phys. Rev. A 57, 2208–2211 (1998).
Cacciapuoti, A. S. et al. Quantum internet: Networking challenges in distributed quantum computing. IEEE Network 34, 137–143 (2020).
Illiano, J., Caleffi, M., Manzalini, A. & Cacciapuoti, A. S. Quantum internet protocol stack: a comprehensive survey. Comput. Netw. 213, 109092 (2022).
Qian, J., Feng, X.-L. & Gong, S.-Q. Universal Greenberger-Horne-Zeilinger-state analyzer based on two-photon polarization parity detection. Phys. Rev. A 72, 052308 (2005).
Xia, Y., Kang, Y.-H. & Lu, P.-M. Complete polarized photons bell-states and Greenberger-Horne-Zeilinger-states analysis assisted by atoms. J. Opt. Soc. Am. B 31, 2077–2082 (2014).
Sheng, Y.-B., Deng, F.-G. & Long, G. L. Complete hyperentangled-bell-state analysis for quantum communication. Phys. Rev. A 82, 032318 (2010).
Liu, Q. & Zhang, M. Generation and complete nondestructive analysis of hyperentanglement assisted by nitrogen-vacancy centers in resonators. Phys. Rev. A 91, 062321 (2015).
Zhou, Y.-H., Yu, Z.-W. & Wang, X.-B. Making the decoy-state measurement-device-independent quantum key distribution practically useful. Phys. Rev. A 93, 042324 (2016).
Gu, J. et al. Experimental measurement-device-independent type quantum key distribution with flawed and correlated sources. Sci. Bull. 67, 2167–2175 (2022).
Grasselli, F. et al. Secure anonymous conferencing in quantum networks. PRX Quantum 3, 040306 (2022).
Carrara, G., Murta, G. & Grasselli, F. Overcoming fundamental bounds on quantum conference key agreement. arXiv https://doi.org/10.48550/arXiv.2211.15559 (2022).
Christensen, B. G. et al. Detection-loophole-free test of quantum nonlocality, and applications. Phys. Rev. Lett. 111, 130406 (2013).
Kok, P., Lee, H. & Dowling, J. P. Single-photon quantum-nondemolition detectors constructed with linear optics and projective measurements. Phys. Rev. A 66, 063814 (2002).
Distante, E. et al. Detecting an itinerant optical photon twice without destroying it. Phys. Rev. Lett. 126, 253603 (2021).
Andersen, A. L. & Mølmer, K. Quantum nondemolition measurements of moving target states. Phys. Rev. Lett. 129, 120402 (2022).
Jiao, G.-F., Zhang, K., Chen, L. Q., Yuan, C.-H. & Zhang, W. Quantum non-demolition measurement based on an su(1,1)-su(2)-concatenated atom-light hybrid interferometer. Photon. Res. 10, 475–482 (2022).
Ma, X.-S., Zotter, S., Kofler, J., Jennewein, T. & Zeilinger, A. Experimental generation of single photons via active multiplexing. Phys. Rev. A 83, 043814 (2011).
Minder, M. et al. Experimental quantum key distribution beyond the repeaterless secret key capacity. Nat. Photonics 13, 334–338 (2019).
Acknowledgements
We gratefully acknowledge the supports from the National Natural Science Foundation of China (No. 12274223), the Natural Science Foundation of Jiangsu Province (No. BK20211145), the Fundamental Research Funds for the Central Universities (No. 020414380182), the Key Research and Development Program of Nanjing Jiangbei New Area (No. ZDYD20210101), the Program for Innovative Talents and Entrepreneurs in Jiangsu (No. JSSCRC2021484), and the Program of Song Shan Laboratory (Included in the management of Major Science and Technology Program of Henan Province) (No. 221100210800-02).
Author information
Authors and Affiliations
Contributions
All authors contributed to the scientific discussions and refinement of the manuscript. Z.-B.C. guided the work. H.-L.Y. and Y.F. conceived the idea of the work. C.-L.L., Y.F. and H.-L.Y. finished all theoretical simulation and manuscript preparation with the help of W.-B.L., Y.-M.X., B.-H.L., and M.-G.Z.
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing interests.
Peer review
Peer review information
Communications Physics thanks the anonymous reviewers for their contribution to the peer review of this work.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary information
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Li, CL., Fu, Y., Liu, WB. et al. Breaking universal limitations on quantum conference key agreement without quantum memory. Commun Phys 6, 122 (2023). https://doi.org/10.1038/s42005-023-01238-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s42005-023-01238-5
This article is cited by
-
Quantum sealed-bid auction protocol with post-confirmation based on blind signature
Quantum Information Processing (2024)
-
Further insights on constructing quantum circuits for Camellia block cipher
Quantum Information Processing (2023)
-
Semi-quantum Key Agreement Protocol Using W States
International Journal of Theoretical Physics (2023)
-
Anonymous quantum conference key agreement using the W state
Quantum Information Processing (2023)
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.