Abstract
In order to effectively assess all types of security risks in the important event, the important decision-making basis for security risk warning and emergency management of important event is provided by analyzing the coupling relationship and evolution mechanism between various risks. The criminal causes, management defects, security and emergency system construction are analyzed from the possibility of accidents and risks. The multi-source data risk assessment system based on five subsystems and its index set of human factors, management factors, site factors, event factors and audit factors are proposed. The weight of each index in the assessment system is determined by the method of information entropy, and then the risk grade of important event is determined according to the weight calculation function and the improved fuzzy matter element model. The verification with an example shows that: the risk assessment model is optimized by combining entropy weight with fuzzy matter-element model, the influence of weight data extreme value was weakened, the qualitative description and quantitative analysis of multi-source data could be combined, and the subjective error was reduced. The risk grade of important event is reasonably evaluated, and the assessment effect is basically consistent with the expert inspection analysis, which shows that the method had certain application value.
Similar content being viewed by others
Introduction
With the change of international and domestic forms, the important event involving political, economic, cultural, sports, entertainment and other industries have been increasing, such as G20 summits, APEC conferences, automobile exhibitions, football and other large-scale sports events, star concerts, etc. The political and cultural exchanges are promoted, and economic development also is promoted to a certain extent due to the holding of these important events1,2. However, the hidden dangers about how can it be resolved in all kinds of important event to become a priority issue for the organizational unit. The crowded stampede, fire and explosion, public security crimes, terrorist attacks, mass disturbances and a series of security issues are often happened due to the large number of people and the complex types involved3,4. Such as the hundreds of terrorist attacks are happened before and after the 2008 Beijing Olympic Games, In 2014, hundreds of people are killed and injured in a stampede on the Shanghai Bund, and the 2018 Venezuelan national celebration is attacked by drone explosive and so on. The lack of security risk prevention and emergency response capacity for the incidents are reflect from some extent. Through analysis, once the security issue was occurred in the process of organizing activities, the emergencies are difficult to be disposed due to the large number of personnel. In addition to causing casualties, equipment damage and other serious social hazards such as political and economic. Therefore, the organization of event are analyzed, all kinds of security risks are study, and the good job of risk assessment in advance is done, which has become a research hotspot for many event organization departments and scholars5. The security of important event is affected by many factors, and there are still a certain relationship between the factors. The quantitative and qualitative factors are fully consider by analyzed multi-source data. The security influencing factors and security risk index system of important event are established, which played an important role in the safety risk assessment mechanism of important event. For example, Zhang6 discussed the important influencing factors and significance of risk assessment for the security of important event, which find that security indicators can be effectively improved by the risk assessment. The possibility of terrorist attack is analyzed in subway and the specific index system of risk assessment is established by Matsika7. The many methods are used in security risk assessment at present, which mainly focused on using various mathematical models to analyze the multi-source data of the problems faced and obtain the safety risk indicators, such as fuzzy theory, entropy weight method, analytic hierarchy process and mutation theory. Svalin2 give the effectiveness of risk assessment and early warning of police force in emergency police cases from the point of view of risk prediction system construction, model construction and data acquisition. The method of neural network and expert reasoning is put forward to quantitatively analyze the risk factors affecting the security prevention system and improve the accuracy of the assessment model8. Shamala9 study the impact of information acquisition quality on safety risk assessment and how to effectively manage risk. Shen10 presented a novel approach for assessing the potential risk of serious crime events (e.g. terrorist attack), then analyze and prove its validity. However, the risk assessment of important event mainly focus on fire risk and food safety, which included static and dynamic risk, human and equipment factors. The research on security risk of specific activities was relatively few, and the assessment and detection index screening of human, object and equipment were vulnerable to subjective influence. The weighted quantitative analysis also depends on the professional knowledge level of the evaluator, and the judgment matrix standard is revised with strong subjectivity and lack of scientific theory and method11,12,13.
The superiority of combining entropy weight and fuzzy matter element in objective evaluation. In this paper, the dynamic model of public security risk assessment for important event is established by using entropy weight and fuzzy matter element model based on the relevant national standards, expert experience and field assessment. Then the multi-source data such as human factors, management factors, site equipment factors, event factors and audit factors are respectively empowering, the subjective factors are reduced and objective calculation accuracy is increased. The security risk index and the possible problems of the event are analyzed by taking the certain event as a column, and the preventive measures are put forward which is of great practical significance to the security risk assessment of the important event.
Risk assessment
Risk indicators
The security risk of important event is huge, which easy to be affected by various factors, and the relationship between the factors have certain coupling characteristics. The mutual influence between the factors are caused due to a certain factor changes, which lead to public security emergencies and easy to be uncontrolled14,15,16. Therefore, effective classification of influencing factors are of great significance. This paper summarize the influencing factors into five aspects: human, management, site equipment, events, related audit, and established four levels of assessment index system based on the possibility of security risk, security management defects and the construction of emergency security disposal system. The requirements of the standard are not only necessary to be met, but an index system to objectively reflect the composition and internal relationship of various factors in security assessment need to be established in line with the precise, comprehensive and practical criteria. And each assessment index can be divided into an orderly level to make it orderly, the availability of assessment index data and the maximum practical value of risk assessment mechanism are considered simultaneously.
Human factors A mainly caused by human factors risk indicators, select the composition of participants, important people, organizers, event management personnel ability as the main dimension indicators, so as to improve the composition of personnel and business level, improve the ability of personnel. According to the assessment results, the composition of personnel and the level of personnel operational capacity are improved.
The management and prevention factors B are the basic guarantee for the security operation of important events. The relevant schemes and technical means can be optimized by selecting the dimensions of plan formulation, emergency management, inspection and examination, technical and tool defense, specific execution.
The site and equipment factors C are the basic requirement for the security holding of important event, the site situation, the condition of the goods and the condition of the equipment are selected as the main assessment index. The site selection, the daily management and maintenance of the equipment can be effectively carried out according to the situation, and the old equipment can be optimized regularly.
Event risk factors D are an important trigger point of activity security risk, which mainly involve the dimensions of domestic and foreign situation, type and nature of event, social situation and attention of event. The risk can be reduced by social guidance and prevention according to assessment report.
Relevant audit factors E are the permitted basic condition of event, which mainly carry out by various qualification audits are formed from approval organs and organizational organs, event site maintenance and security, emergency disposal audit and other dimensions. The initial conditions for security risks are constituted by the elements.
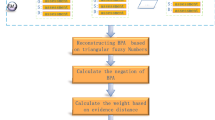
The risk element composition analysis process is shown in Fig. 1.
The achievements of relevant scholars in the research of security risk assessment are drawn on the basis of comprehensive analysis and investigation, and multi-layer factors set index are established according to the relevant security information of events and solicit expert suggestions, which included 4 level index and 63 basic influencing factors, as shown in Table 1.
Interactions of risk
The subfactors contained under a single, two or three main factors are staggered analyzed, the risk can be further identified to obtain the risk sources from different perspectives. For example, two-dimensional A1&D2 risk scenarios as shown in Fig. 2a, The new perspective of risk is created by the interaction between two subfactors of cultural education and event interactivity, That is, the cultural level and interaction of the participants are different requirements due to different scenarios and different content of important event. The serious consequences are easy to be caused if the two match improperly. Similarly, for a three-dimensional A1&D2&B2 risk scenarios as shown in Fig. 2b.The new three-dimensional perspective of risk is taken shape by the interaction between three sub-factors of cultural education, management system and event interactivity. For example, the interactions are different between different of interaction ways, academic qualifications and management methods, which required managers to conduct interaction and management training according to the actual personnel culture. Otherwise, some avoidable risks will be happen in the course of the activity.
According to this method, the risks caused by the interaction of multiple subfactors are identified. In addition, the side length of the geometry generated by the interaction can be measured by the probability or consequence of each subfactor in the coordinate system shown in Fig. 2. The area or volume of the resulting geometric can be used to measure the risk degree under the interaction of various factors in a risk scenario. Taking the probability measure as an example, when the dimension of the risk scenario are less than or equal to 3, we can obtain:
Mrisk is defined as the risk degree under the interaction of three factors in the risk scenario, mx, my, mz represent the side length of the geometry generated by the interaction in the risk coordinate system, that is, the posterior probability of a single risk factor. Specifically, mz = 1 when the Mrisk is the two-dimensional risk scenario.
Entropy weight and model
In the event of danger of a major event, the chain reaction of many factors are caused, which will lead to more serious problems are caused due to the superposition of each other. The multiple problems need to be considered at the same time when the risk grade assessment is considered, the judgment matrix with fuzzy consistency is select for analyze the multi-objective decision.
Index weight entropy weight
Entropy weight method is an objective assignment method, which mainly use the utility value of information to determine the index weight. The effective use of entropy weight function model to evaluate the security risk of important event is mainly used by the factors of affect the security of important event are effective differentiated and ranked, and the entropy value is determined. The calculation and analysis are carried out by comprehensive use of the order of the information obtained. The weight value of assessment index is mainly used as the initial calculation matrix \(X = \left\{ {X_{ij} } \right\}_{m \times n}\), m is the number of assessment object, the n is the number of assessment indexes. In order to reduce the difference of dimension, order of magnitude and quality of data index, the selected data index are normalized:
According to the analysis,\(0 \le y_{ij} \le 1\), the normalized data matrix can be obtained after calculation:
Clearly, according to the above formula, the entropy of item j is:
Among them, the constant k is 1/lnm, which is mainly related to the number of assessment objects. The efficiency value ej of the j index entropy value are determined. When the order degree of the system is higher, the ej value tends to 0, which will result in a higher value for comprehensive assessment. When order degree of the system is lower, the ej value tends to 1, which will result in a lower value for comprehensive assessment.
Therefore, the index utility value are effectively determined by the difference hj between index entropy ej and 1 in the assessment system, that is:
As the core of entropy method, the information utility value have important influence on the importance of assessment result. The weight of each index is estimated based on the characteristics of entropy method, and the weight of item j can be obtained after analysis:
Construction of fuzzy element model
In order to effectively distinguish between factors, the assessment model based on the ordered triplet R (M, c, v) are used as the basic element to describe things to construct fuzzy elements in the multi-objective decision-making system. Where M is the assessment object, the c is the M characteristic index, and the v is the fuzzy value. The assessment object M has n characteristics \(c_{1} ,c_{2} , \ldots ,c_{n}\) and corresponding fuzzy values \(v_{1} ,v_{2} , \ldots ,v_{n}\).Suppose R as the n dimension fuzzy object element, when there are m assessment objects, each object has the n dimension fuzzy value element. The n dimensional fuzzy object element of m object are compounded by the mixed expression forms, expressed as Rmn:
where Mi is the i object, \(i = 1,2, \ldots ,m\); c j is the j item characteristics, \(j = 1,2, \ldots ,n\); Xij is the fuzzy value corresponding to the j item characteristics of the i object, that is, membership degree.
The fuzzy value corresponding to each assessment index is determined, and the subordinate relation of each index is important to the influence degree of the assessment index. Because the eigenvalues of each index dimension are different, and the eigenvalue difference have certain influence on the assessment result. Comparative study showed that the eigenvalue of each assessment index have an important influence on the good rate, but the trend is different due to determined by the nature of index. In order to clarify the relationship between the good properties of each index and the membership degree, the following formulas are adopted:
Equations (8) and (9) are different trend indexes respectively. The two formulas are related to each other, but do not affect each other, because they are aimed at different objects. The composite entropy fuzzy matter are calculated based on the membership degree relation of the fuzzy value Xij of n dimension fuzzy matter matter of m object. According to the principle of superior subordinate degree, the corresponding composite elements are obtained:
Closeness-degree calculation
As an important basis to measure the security risk assessment index of major activities, the difference between the assessment object and the assessment standard value are determined by the size of matched value. Combined with the index data to analyze and calculate the closeness of the assessment object based on Euclid closeness-degree mathematical model ρHj. According to the results of the calculation, the order of the advantages and disadvantages of multiple assessment objects are carried out, and the calculating formula for the closeness-degree of compound fuzzy elements is constructed:
where M is the assessment object, \(\rho H_{j}\) is the closeness-degree. The computational formula of the j closeness-degree in fuzzy element matrix RρH as follows:
The entropy weight value and standard value of each assessment index of security risk assessment of important events are compared and analyzed. The formula as follows:
where Zj is the combined assessment values for j assessment subjects.
Assessment example building
In order to verify the above risk assessment model, the different events are selected to assessment comparative for effectively evaluated the security risk of different important events and analyzed the security risk assessment indexes of different important events. According to the index system, two kinds of events are selected for comprehensive assessment. The security risk status of different events are sorted, and the cause analysis is carried out.
The assessment objects
Several large-scale events held in recent years are selected as the assessment objects based on 63 assessment indicators in 5 aspects: human, management, site, event and audit. Two music festivals in Kunming (P1, 2018) and Zhangbei Grassland (P2, 2019), and two large-scale football matches in Beijing (P3, 2019) and Guangzhou (P4, 2019) are selected as assessment objects respectively.
Risk comparative analysis
Combined with fuzzy matter element model and entropy weight calculation weight method, the above four events are used as cases for security risk assessment. According to the combination of quantitative and qualitative, the specific measured value of major events are taken as the quantitative index value, and the weighted average of the expert assessment group combined with the data scoring are taken as the qualitative index value. After the assessment is completed, the assessment index value is normalized by the judgment matrix formula (8) or formula (9). After the processing is completed, the entropy value and entropy weight of the assessment object are processed according to formula (4) and formula (6). Then the calculated value is imported into formula (9) to obtain the functional membership degree of the corresponding index. The calculation results of entropy value and entropy weight are shown in Table 2.
By observing Table 2, the second level index of security risk of large-scale events such as music festival and football match are calculated and analyzed. The risk weight coefficient of human factors are about 0.3–0.4, the management and prevention factors are about 0.3–0.4, the site equipment are between 0.1 and 0.2, the event factors are about 0.2, and the audit factors are about 0.1. Among them, the human factors and management factors account for a large proportion, which is consistent with the design of human audit and management should be strengthened after major events were determined. The influencing factors in large-scale events are related to each other, which had obvious coupling relationship. The each assessment index should be paid the same attention due to each factor has certain risk.
In order to distinguish the security risk index system of important event, the objects assessment are carried out according to the criteria of excellent, good, medium and poor, and the corresponding objects closeness-degree are calculated according to formulas (12) and (13), as shown in Tables 3 and 4.
Table 4 shows the security risk assessment closeness results and the comprehensive assessment results of the four events. The security risk assessment value of event P3 was 0.1531, which the assessment result is good. While the calculation results of P1、P2 and P4 closeness are between 0.01732 and 0.2754, and the assessment results are medium. Compared with each other, the four events are in a relatively security state. The assessment results are basically consistent with the security inspection results, which reflected the security level of the events process. The security degree of P3 and P4 events are better than P1 and P2 due to the participants in football events are more fixed and the change is relatively small, and events are carried out in the relative fixed field, which is conducive to security analysis and risk reduction. Music festivals are more complex, open and fewer security facilities. Among them, the lower risk of P3 is partly due to the Beijing government's higher requirements and stricter security audit. Before and after the events are carried out according to combine the assessment results with the index weight, the common problems such as the participant review, inspection of the equipment operation itself are payed attention, and the inspection safety management is strengthened to reduce the sudden accidents.
Conclusion
The security risk index system and the assessment model with entropy weight method and material element model are constructed based on the causes of important events security accidents are analyzed. The subjectivity of the assessment process is reduced, the objective accuracy is improved, and the systematization of the assessment process is further optimized by the method. The practicability of the assessment model is verified by using examples.
Compared with the index system and entropy weight calculation results shows that: the weight of human factors and management factors in the process of holding important events are larger and more likely to induce security risks, so the construction of related systems such as personnel review and management should be strengthened. Because of the coupling of various factors, the awareness of security risk is strengthened, the supervision mechanism is improved, the ability of public security to deal with problems are strengthened, the quality of personnel and the level of technology are improved on the basis of effective assessment and improvement of hidden dangers of safety risks. So as to eliminate all kinds of security risks and hidden dangers.
References
Nordfjærn, T. & Rundmo, T. Transport risk assessments associated with past exposure to adverse security events in public transport. Transp. Res. F Traffic Psychol. Behav. 53, 14–23 (2018).
Svalin, K. et al. Police employees’ violence risk assessments: The predictive validity of the B-SAFER and the significance of protective actions. Int. J. Law Psychiatry 56, 71–79 (2018).
Wei, W. A. et al. Multi-hazard comprehensive risk assessment based on coupling incentive mechanism. China Saf. Sci. J. 29, 161–167 (2019).
Yang, Bo. Dynamic risk identification safety model based on fuzzy support vector machine and immune optimization algorithm. Saf. Sci. 118, 205–211 (2019).
Karasan, A. et al. A new risk assessment approach: Safety and Critical Effect Analysis (SCEA) and its extension with Pythagorean fuzzy sets. Saf. Sci. 108, 173–187 (2018).
Zhang, L. On the importance of risk assessment in security work of large-scale mass activities. Value Eng. 28, 176–178 (2015).
Matsika, E. et al. Development of risk assessment specifications for analyzing terrorist attacks vulnerability on metro and light rail systems. Transp. Res. Procedia 14, 1345–1354 (2016).
Munodawafa, F. & IsmailAwad, A. Security risk assessment within hybrid data centers: A case study of delay sensitive applications. J. Inf. Security Appl. 43, 61–72 (2018).
Shamala, P. et al. Integrating information quality dimensions into information security risk management (ISRM). J. Inf. Security Appl. 36, 1–10 (2017).
Shen, Q. & Zhao, R. Risk assessment of serious crime with fuzzy random theory. Inf. Sci. 180, 4401–4411 (2010).
Huimin, G. et al. Regional risk assessment methods in relation to urban public safety. Process Saf. Environ. Prot. 143, 361–366 (2020).
Liu, C. et al. An improved risk assessment method based on a comprehensive weighting algorithm in railway signaling safety analysis. Saf. Sci. 128, 312–321 (2020).
O’Connor, M., Pasman, H. J. & Rogers, W. J. Sam Mannan’s safety triad, a framework for risk assessment. Process Saf. Environ. Prot. 129, 202–209 (2019).
Gu, Z. et al. Epidemic risk assessment by a novel communication station based method. IEEE Trans. Netw. Sci. Eng. https://doi.org/10.1109/TNSE.2021.3058762 (2021).
Qiao, C. et al. Federated adaptive asynchronous clustering algorithm for wireless mesh networks. IEEE Trans. Knowl. Data Eng. https://doi.org/10.1109/TKDE.2021.3119550 (2022).
Qiu, J. et al. Automatic concept extraction based on semantic graphs from big data in smart city. IEEE Trans. Comput. Soc. Syst. 7, 225–233 (2020).
Acknowledgements
Thanks to the 14th Five-Year Plan Project of Hebei Higher Education Society (GJXHZ2021-43) and Education Reform Project of Chinese People's Police University (2020bkjg004; 2020yjsjg017) for its support.
Author information
Authors and Affiliations
Contributions
Q.W. wrote the main manuscript text and prepared all figures. All authors reviewed the manuscript.
Corresponding author
Ethics declarations
Competing interests
The author declares no competing interests.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Wang, Q. Research on security risk assessment mechanism of important event based on multi-source data. Sci Rep 12, 4123 (2022). https://doi.org/10.1038/s41598-022-08079-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-022-08079-2
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.