Abstract
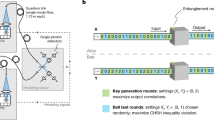
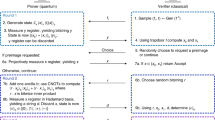
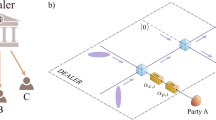
The ability to perform measurements in the middle of a quantum circuit is a powerful resource. It underlies a wide range of applications, from remote state preparation to quantum error correction. Here we apply mid-circuit measurements for a particular task: demonstrating quantum computational advantage. The goal of such a demonstration is for a quantum device to perform a computational task that is infeasible for a classical device with comparable resources. In contrast to existing demonstrations, the distinguishing feature of our approach is that the classical verification process is efficient, both in asymptotic complexity and in practice. Furthermore, the classical hardness of performing the task is based upon well-established cryptographic assumptions. Protocols with these features are known as cryptographic proofs of quantumness. Using a trapped-ion quantum computer, we perform mid-circuit measurements by spatially isolating portions of the ion chain via shuttling. This enables us to implement two interactive cryptographic proofs of quantumness, which when suitably scaled to larger systems, promise the efficient verification of quantum computational advantage. Our methods can be applied to a range of interactive quantum protocols.
This is a preview of subscription content, access via your institution
Access options
Access Nature and 54 other Nature Portfolio journals
Get Nature+, our best-value online-access subscription
$29.99 / 30 days
cancel any time
Subscribe to this journal
Receive 12 print issues and online access
$209.00 per year
only $17.42 per issue
Buy this article
- Purchase on Springer Link
- Instant access to full article PDF
Prices may be subject to local taxes which are calculated during checkout



Similar content being viewed by others
Data availability
All data supporting the findings of this study are available in the paper or Methods. The raw experimental data are available from the corresponding author upon reasonable request.
References
Nielsen, M. A. & Chuang, I. L. Quantum Computation and Quantum Information 10th edn (Cambridge Univ. Press, 2010).
Ryan-Anderson, C. et al. Realization of real-time fault-tolerant quantum error correction. Phys. Rev. X 11, 041058 (2021).
Cong, I., Choi, S. & Lukin, M. D. Quantum convolutional neural networks. Nat. Phys. 15, 1273–1278 (2019).
Mahadev, U. Classical verification of quantum computations. In 2018 IEEE 59th Annual Symposium on Foundations of Computer Science (FOCS) (ed. Rabani, Y.) 259–267 (IEEE, 2018).
Brakerski, Z., Christiano, P., Mahadev, U., Vazirani, U. & Vidick, T. A cryptographic test of quantumness and certifiable randomness from a single quantum device. In 2018 IEEE 59th Annual Symposium on Foundations of Computer Science (FOCS) (ed. Rabani, Y.) 320–331 (IEEE, 2018).
Gheorghiu, A. & Vidick, T. Computationally-secure and composable remote state preparation. In 2019 IEEE 60th Annual Symposium on Foundations of Computer Science (FOCS) (ed. Rabani, Y.) 1024–1033 (IEEE, 2019).
Aharonov, D., Ben-Or, M. & Eban, E. Interactive proofs for quantum computations 453–469. Preprint at https://arxiv.org/abs/1704.04487 (2017).
Goldwasser, S., Micali, S. & Rackoff, C. The knowledge complexity of interactive proof systems. SIAM J. Comput. 18, 186–208 (1989).
Lund, C., Fortnow, L., Karloff, H. & Nisan, N. Algebraic methods for interactive proof systems. In Proc. 31st Annual Symposium on Foundations of Computer Science Vol. 1 (ed. Yannakakis, M.) 2–10 (IEEE, 1990); https://doi.org/10.1109/FSCS.1990.89518
Shamir, A. IP = PSPACE. J. ACM 39, 869–877 (1992).
Brakerski, Z., Koppula, V., Vazirani, U. & Vidick, T. Simpler proofs of quantumness. In 15th Conference on the Theory of Quantum Computation, Communication and Cryptography (TQC 2020) (ed. Flammia, S. T.) 8:1–8:14 (Schloss Dagstuhl–Leibniz-Zentrum für Informatik, 2020).
Kahanamoku-Meyer, G. D., Choi, S., Vazirani, U. V. & Yao, N. Y. Classically verifiable quantum advantage from a computational Bell test. Nat. Phys. 18, 918–924 (2022).
Bell, J. S. On the Einstein Podolsky Rosen paradox. Physics 1, 195–200 (1964).
Hensen, B. et al. Loophole-free Bell inequality violation using electron spins separated by 1.3 kilometres. Nature 526, 682–686 (2015).
Shalm, L. K. et al. Strong loophole-free test of local realism. Phys. Rev. Lett. 115, 250402 (2015).
Giustina, M. et al. Significant-loophole-free test of Bell’s theorem with entangled photons. Phys. Rev. Lett. 115, 250401 (2015).
Arute, F. et al. Quantum supremacy using a programmable superconducting processor. Nature 574, 505–510 (2019).
Zhong, H.-S. et al. Quantum computational advantage using photons. Science 370, 1460–1463 (2020).
Wu, Y. et al. Strong quantum computational advantage using a superconducting quantum processor. Phys. Rev. Lett. 127, 180501 (2021).
Zhu, Q. et al. Quantum computational advantage via 60-qubit 24-cycle random circuit sampling. Sci. Bull. 67, 240–245 (2021).
Aaronson, S. & Arkhipov, A. The computational complexity of linear optics. In Proc. 43rd Annual ACM Symposium on Theory of Computing (ed. Fortnow, L.) 333–342 (Association for Computing Machinery, 2011).
Lund, A. P., Bremner, M. J. & Ralph, T. C. Quantum sampling problems, BosonSampling and quantum supremacy. Npj Quantum Inf. 3, 15 (2017).
Harrow, A. W. & Montanaro, A. Quantum computational supremacy. Nature 549, 203–209 (2017).
Boixo, S. et al. Characterizing quantum supremacy in near-term devices. Nat. Phys. 14, 595–600 (2018).
Bouland, A., Fefferman, B., Nirkhe, C. & Vazirani, U. On the complexity and verification of quantum random circuit sampling. Nat. Phys. 15, 159–163 (2019).
Aaronson, S. & Gunn, S. On the classical hardness of spoofing linear cross-entropy benchmarking. Theory Comput. Syst. 16, 1–8 (2020).
Hensinger, W. K. Quantum computer based on shuttling trapped ions. Nature 592, 190–191 (2021).
Bluvstein, D. et al. A quantum processor based on coherent transport of entangled atom arrays. Nature 604, 451–456 (2022).
Pino, J. M. et al. Demonstration of the trapped-ion quantum ccd computer architecture. Nature 592, 209–213 (2021).
Kielpinski, D., Monroe, C. & Wineland, D. J. Architecture for a large-scale ion-trap quantum computer. Nature 417, 709–711 (2002).
Wan, Y. et al. Quantum gate teleportation between separated qubits in a trapped-ion processor. Science 364, 875–878 (2019).
Regev, O. On lattices, learning with errors, random linear codes, and cryptography. J. ACM 56, 1–40 (2009).
Regev, O. The learning with errors problem. In 2010 IEEE 25th Annual Conference on Computational Complexity (ed. van Melkebeek, D.) 191–204 (IEEE, 2010).
Rabin, M. O. Digitalized Signatures and Public-key Functions as Intractable as Factorization. Technical Report (Massachusetts Institute of Technology, 1979).
Goldwasser, S., Micali, S. & Rivest, R. L. A digital signature scheme secure against adaptive chosen-message attacks. SIAM J. Comput. 17, 281–308 (1988).
Goldwasser, S., Micali, S. & Rivest, R. L. in Advances in Cryptology, Proceedings of CRYPTO ’84 (eds Blakley, R. R. & Chaum, D.) 467 (Springer, 1985).
Banerjee, A., Peikert, C. & Rosen, A. in Advances in Cryptology—EUROCRYPT 2012 (eds Pointcheval, D. & Johansson, T.) 719–737 (Springer, 2012).
Alwen, J., Krenn, S., Pietrzak, K. & Wichs, D. in Advances in Cryptology—CRYPTO 2013 (eds Canetti, R. & Garay, J. A.) 57–74 (Springer, 2013).
Clauser, J. F., Horne, M. A., Shimony, A. & Holt, R. A. Proposed experiment to test local hidden-variable theories. Phys. Rev. Lett. 23, 880 (1969).
Monroe, C. et al. Programmable quantum simulations of spin systems with trapped ions. Rev. Mod. Phys. 93, 025001 (2021).
Egan, L. et al. Fault-tolerant operation of a quantum error-correction code. Nature 598, 281–286 (2021).
Hirahara, S. & Gall, F. L. Test of quantumness with small-depth quantum circuits. Preprint at https://arxiv.org/abs/2105.05500 (2021).
Liu, Z. & Gheorghiu, A. Depth-efficient proofs of quantumness. Quantum 6, 807 (2022).
Huang, C. et al. Classical simulation of quantum supremacy circuits. Preprint at https://arxiv.org/abs/2005.06787 (2020).
Pan, F. & Zhang, P. Simulating the Sycamore quantum supremacy circuits. Preprint at https://arxiv.org/abs/2103.03074 (2021).
Gray, J. & Kourtis, S. Hyper-optimized tensor network contraction. Quantum 5, 410 (2021).
Pan, F., Chen, K. & Zhang, P. Solving the sampling problem of the Sycamore quantum supremacy circuits. Preprint at https://arxiv.org/abs/2111.03011 (2021).
Yong et al. Closing the ‘quantum supremacy’ gap: achieving real-time simulation of a random quantum circuit using a new Sunway supercomputer. In Proc. International Conference for High Performance Computing, Networking, Storage and Analysis (ed. de Supinski, B. R.) 1–12 (Association for Computing Machinery, 2021).
Liu, X. et al. Redefining the quantum supremacy baseline with a new generation Sunway supercomputer. Preprint at https://arxiv.org/abs/2111.01066 (2021).
Gao, X. et al. Limitations of linear cross-entropy as a measure for quantum advantage. Preprint at https://arxiv.org/abs/2112.01657 (2021).
Córcoles, A. D. et al. Exploiting dynamic quantum circuits in a quantum algorithm with superconducting qubits. Phys. Rev. Lett. 127, 100501 (2021).
Rudinger, K. et al. Characterizing midcircuit measurements on a superconducting qubit using gate set tomography. Phys. Rev. Appl. 17, 014014 (2022).
Skinner, B., Ruhman, J. & Nahum, A. Measurement-induced phase transitions in the dynamics of entanglement. Phys. Rev. X 9, 031009 (2019).
Li, Y., Chen, X. & Fisher, M. P. Quantum Zeno effect and the many-body entanglement transition. Phys. Rev. B 98, 205136 (2018).
Noel, C. et al. Measurement-induced quantum phases realized in a trapped-ion quantum computer. Nat. Phys. 18, 760–764 (2022).
Cetina, M. et al. Control of transverse motion for quantum gates on individually addressed atomic qubits. PRX Quantum 3, 010334 (2022).
Olmschenk, S. et al. Manipulation and detection of a trapped Yb+ hyperfine qubit. Phys. Rev. A 76, 052314 (2007).
Debnath, S. et al. Demonstration of a small programmable quantum computer with atomic qubits. Nature 536, 63 (2016).
Mølmer, K. & Sørensen, A. Multiparticle entanglement of hot trapped ions. Phys. Rev. Lett. 82, 1835–1838 (1999).
Solano, E., de Matos Filho, R. L. & Zagury, N. Deterministic Bell states and measurement of the motional state of two trapped ions. Phys. Rev. A 59, R2539–R2543 (1999).
Milburn, G., Schneider, S. & James, D. Ion trap quantum computing with warm ions. Fortschr. Phys. 48, 801–810 (2000).
Choi, T. et al. Optimal quantum control of multimode couplings between trapped ion qubits for scalable entanglement. Phys. Rev. Lett. 112, 190502 (2014).
Maunz, P. L. W. High Optical Access Trap 2.0 Technical Report (Office of Scientific and Technical Information, 2016); https://doi.org/10.2172/1237003
Barker, E. Recommendation for Key Management Part 1: General. Technical report NIST SP 800-57pt1r4 (National Institute of Standards and Technology, 2016); https://doi.org/10.6028/NIST.SP.800-57pt1r4
Boudot, F. et al. in Advances in Cryptology—CRYPTO 2020 (eds Micciancio, D. & Ristenpart, T.) 62–91 (Springer, 2020).
Lindner, R. & Peikert, C. in Topics in Cryptology—CT-RSA 2011 (ed. Kiayias, A.) 319–339 (Springer, 2011).
Acknowledgements
We are grateful to V. Uhlir for the design of the verifier and prover figures. This work is supported by the Army Research Office (ARO) through the LogiQ programme of the Intelligence Advanced Research Projects Activity; the National Quantum Information Science Research Centers, Office of Science, US Department of Energy (DoE); the Quantum Systems Accelerator; the Air Force Office of Scientific Research (AFOSR) Multidisciplinary University Research Initiatives (MURIs) on Quantum Measurement/Verification and Quantum Interactive Protocols (Grant No. FA9550-18-1-0161) and Dissipation Engineering in Open Quantum Systems; the Software-Tailored Architecture for Quantum Co-design Program of the National Science Foundation (NSF); the ARO MURI on Modular Quantum Circuits; the Accelerated Research in Quantum Computing Program, Advanced Scientific Computing Research, DoE (Award No. DE-SC0020312); the Young Investigator Program of the AFOSR (Award No. FA9550-16-1-0495); the Quantum Leap Challenge Institutes, NSF (Grant No. OMA-2016245); the Institute for Quantum Information and Matter, an NSF Physics Frontiers Center (NSF Grant PHY-1125565); the Gordon and Betty Moore Foundation (Grant No. GBMF-12500028); Dr Max Rössler and the Walter Haefner Foundation through the ETH Zürich Foundation; the NSF (Award No. DMR-1747426); a Vannevar Bush Faculty Fellowship; the Office of Advanced Scientific Computing Research under the Accelerated Research in Quantum Computing Program; the A. P. Sloan Foundation; and the David and Lucile Packard Foundation.
Author information
Authors and Affiliations
Contributions
D.Z., G.K.M., L.L., C.N., A.G., T.V., U.V., N.Y., M.C. and C.M. designed the research. D.Z., C.N., O.K., B.H., Q.W., A.R., L.F., D.B. and L.E. performed the experiments and collected the data. D.Z., G.K.M., L.L., C.N., L.E., A.G. and Y.N. compiled and optimized the circuit. D.Z., G.K.M. and L.L. analysed the data. All authors contributed to the preperation of the paper.
Corresponding author
Ethics declarations
Competing interests
C.M. is the chief scientist for IonQ, Inc. and has a personal financial interest in the company. The other authors declare no competing interests.
Peer review
Peer review information
Nature Physics thanks Robin Blume-Kohout and the other, anonymous, reviewer(s) for their contribution to the peer review of this work.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary information
Supplementary Information
The supplementary information includes these sections: Result data, Post-selection, Circuit construction of the factoring-based protocol, Circuit construction of the LWE-based protocol, Instances of LWE implemented and Additional instances of factoring-based protocols.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Zhu, D., Kahanamoku-Meyer, G.D., Lewis, L. et al. Interactive cryptographic proofs of quantumness using mid-circuit measurements. Nat. Phys. 19, 1725–1731 (2023). https://doi.org/10.1038/s41567-023-02162-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1038/s41567-023-02162-9