Abstract
Quantum key distribution using three states in equiangular configuration combines a security threshold comparable with the one of the Bennett-Brassard 1984 protocol and a quantum bit error rate (QBER) estimation that does not need to reveal part of the key. We implement an entanglement-based version of the Renes 2004 protocol, using only passive optic elements in a linear scheme for the positive-operator valued measure (POVM), generating an asymptotic secure key rate of more than 10 kbit/s, with a mean QBER of 1.6%. We then demonstrate its security in the case of finite key and evaluate the key rate for both collective and general attacks.
Similar content being viewed by others
Introduction
Quantum Key Distribution (QKD) allows two remote parties, Alice and Bob, to generate a secret shared string of bits, that can be used for symmetric cryptography or other cryptographic protocols. Unlike classical key distribution, whose security is based on the computational difficulty of solving certain classes of problems, the security of quantum key distribution comes from the impossibility for an eavesdropper (Eve) to acquire information about an exchanged state without perturbing it. This goal is obtained by using non-orthogonal states, as in the first QKD protocol, introduced by Bennett and Brassard in 1984 (BB84), that uses four different states of two mutually unbiased bases1. In 1992, Bennett showed that two non-orthogonal states are sufficient for QKD2. This protocol, however, has the drawback that the secure key rate is strongly affected by losses: indeed, Eve can extract information by increasing the losses and performing the so called unambiguous state discrimination (USD) attack3,4. The addition of a third state is sufficient to make the B92 protocol unconditionally secure independently from the noise in the quantum channel5,6: however, rates comparable to the BB84 protocols can be obtained only when four states are detected at the receiver.
The optimal three-state QKD protocol, introduced in 2000 by Phoenix-Barnett-Chefles (PBC00)7, uses states that form an equilateral triangle in the X-Z plane of the Bloch sphere. The symmetry of this protocol can indeed be exploited to obtain rates comparable with the BB84 protocol but requiring only three detectors instead of four. This protocol, however, still requires the public exchange of part of the sifted key in order to estimate the QBER. An improvement of this protocol, introduced by Renes in 2004 (R04)8, estimates the error rate from the number of inconclusive events, thus allowing to use all conclusive ones for key extraction. The unconditional security of the PBC00 has been demonstrated, in the asymptotic case, in 20059, for a bit error rate of up to 9.81%. The security of the PBC00 has been demonstrated also in the case of finite key10, using the framework introduced by Scarani and Renner11 and the postselection technique12. Their work, however, does not consider the security of the R04 protocol, therefore excluding one of the most interesting features of this class of symmetrical codes. Despite all these theoretical results, no experimental implementation of equiangular three state QKD protocols has been reported so far. The measurement apparatus proposed in the original work implements the trine measurement using an interferometric setup at the receiver7. This scheme requires careful alignment13,14 and is not assured to have the long term stability required by Quantum Key Distribution (a stability of about half an hour is reported in14 Clarke, et al.). A new experimental scheme implementing the trine measurement using only passive optical elements has been proposed in15 Saunders, et al. Using this apparatus, we demonstrate the feasibility of equiangular three state QKD and assess its key generation rate, both in the asymptotic limit of infinite key and taking into account finite key effects.
Results
Protocol
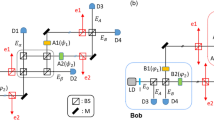
The R04 protocol uses three quantum states, {|ψ1〉, |ψ2〉, |ψ3〉}, placed in an equilateral triangle in the X-Z plane of the Bloch sphere, as shown in Fig. 1.
States used in the R04 protocol (above) and POVM {Πi} used for the measurement (below).
The states lie in the X-Z plane of the Bloch sphere. They are grouped into the sets S1 = {|ψ1〉, |ψ2〉}, S2 = {|ψ2〉, |ψ3〉} and S3 = {|ψ3〉, |ψ1〉}, where the first element of each set corresponds to bit 0 and the second to bit 1. The POVM is implemented by using a partially polarizing beam-splitter (pPBS), a half-wave plate (HWP) at 22.5° and a polarizing beam-splitter (PBS).
The states are grouped into three different sets, S1 = {|ψ1〉, |ψ2〉}, S2 = {|ψ2〉, |ψ3〉} and S3 = {|ψ3〉, |ψ1〉}. In each set, the first state is associated with the bit 0 and the second with the bit 1. Differently from other QKD protocols, each state brings no information about its associated bit before the information about the used set is disclosed.
We implemented an entanglement-based version of the protocol, using polarization-entangled photon pairs in the singlet state

where the subscripts A and B indicate if the photon is going to, respectively, Alice’s or Bob’s detection apparatus and |H〉 and |V〉 are the horizontal and vertical polarization states. In this state, photons A and B are anti-correlated in any measurement basis. Alice measures photon A using the POVM  , with
, with  ,
,  ,
,  . In our notation the state
. In our notation the state  is orthogonal to |ψi〉. When Alice obtains a detection in the state
is orthogonal to |ψi〉. When Alice obtains a detection in the state  (each with probability
(each with probability  ), she is sending to Bob the state |ψi〉 where |ψ1〉 = |H〉,
), she is sending to Bob the state |ψi〉 where |ψ1〉 = |H〉,  and
and  . This operation corresponds to the random preparation, with equal probability, of one of the three states {|ψ1〉, |ψ2〉, |ψ3〉}, as in the prepare-and-measurement scheme of the R04 described in9,16. Bob performs his measurements in the same POVM as Alice {Πi}. After all measurements, Bob and Alice compare the instants of their events, keeping only those where both have a detection within a fixed coincidence window.
. This operation corresponds to the random preparation, with equal probability, of one of the three states {|ψ1〉, |ψ2〉, |ψ3〉}, as in the prepare-and-measurement scheme of the R04 described in9,16. Bob performs his measurements in the same POVM as Alice {Πi}. After all measurements, Bob and Alice compare the instants of their events, keeping only those where both have a detection within a fixed coincidence window.
Even if they have already exchanged all symbols, Alice and Bob do not share any bit string yet, because each state can mean both 0 or 1. Alice uses a QRNG to choose the bit value for each symbol. The combination of the state and the bit value unambiguously determines the set Si used for that event (for example, if Alice sends |ψ2〉 and the QRNG gives 1, the set used for that event is S1). For each event, Alice tells Bob the corresponding set by sending him the value of the index i. Bob uses i to associate  (for i = 1),
(for i = 1),  (for i = 2) and
(for i = 2) and  (for i = 3) with bit 0 and
(for i = 3) with bit 0 and  (for i = 1),
(for i = 1),  (for i = 2) and
(for i = 2) and  (for i = 3) with bit 1. All other combinations are marked as inconclusive, since Bob is not able to determine the state sent by Alice. Bob tells Alice which events are inconclusive and they both discard them. They then estimate the quantum bit error rate (QBER) from the fraction of inconclusive events8,9 and use this information to distill the key using error correction and privacy amplification17.
(for i = 3) with bit 1. All other combinations are marked as inconclusive, since Bob is not able to determine the state sent by Alice. Bob tells Alice which events are inconclusive and they both discard them. They then estimate the quantum bit error rate (QBER) from the fraction of inconclusive events8,9 and use this information to distill the key using error correction and privacy amplification17.
Setup
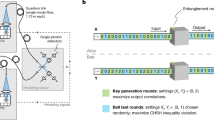
The experimental setup is shown in Fig. 2. Entangled photon pairs are produced by using a 30 mm periodically poled potassium titanyl phosphate (PPKTP) crystal in a polarization-based Sagnac interferometer18,19. The source is pumped with a continuous wave (CW) laser at 404.5 nm, with a power of 3.5 mW. The down-converted photons have a central wavelength of 809 nm, with 0.2 nm full width at half maximum (FWHM) and are collected into single-mode fibres. In this configuration, the setup has a mean coincidence rate of 29 kHz, with a 5% heralding ratio. The fraction of multi-pair over one-pair events, measured by putting one output of the source into a Hanbury-Brown-Twiss interferometer, is ~3.10−3. Among these events, only those which are partially correlated in the polarization degree of freedom are exploitable by Eve through the photon number splitting (PNS) attack11. The ratio of the number of these events to all multi-pair ones is  , where τc = 8 ps is the coherence time of down-converted photons and Δt = 1.5 ns is the coincidence window. The fraction of correlated multi-photon events over the total number of detection events is ∼1.5 · 10−5, thus the information leaked to Eve is negligible. A set of two quarter-wave plates (QWP) and one half-wave plate (HWP) is placed at the exit of the fibre at Bob’s side in order to compensate polarization rotations induced by fibre birefringence.
, where τc = 8 ps is the coherence time of down-converted photons and Δt = 1.5 ns is the coincidence window. The fraction of correlated multi-photon events over the total number of detection events is ∼1.5 · 10−5, thus the information leaked to Eve is negligible. A set of two quarter-wave plates (QWP) and one half-wave plate (HWP) is placed at the exit of the fibre at Bob’s side in order to compensate polarization rotations induced by fibre birefringence.
Experimental setup used for the experiment.
The light issued by a laser diode (LD) at 404.5 nm is collected into a polarization maintaining single mode fibre (PM-SMF) for spatial mode filtering. The polarization is adjusted by a PBS followed by a HWP and the beam is focused by a 200 mm lens (L) into the center of the interferometer. The interferometer is formed by a PBS, a dual-wavelength HWP (d-HWP) and a PPKTP crystal, where the down-conversion takes place. Photons exiting the interferometer are collected into single mode fibres (SMF), preceded by a long-pass filter (LPF) to filter out residual pump intensity. Fiber birefringence is compensated by two quarter-wave plates (QWP) and a half-wave plate (HWP). The receiver consists in an implementation of the POVM {Πi}, with output Ai and Bi corresponding to  for, respectively, Alice and Bob. All the output signals are timed by a common timetagger.
for, respectively, Alice and Bob. All the output signals are timed by a common timetagger.
The receiving apparatus implementing the POVM {Πi} consists of a partially polarizing beam-splitter (pPBS), that completely transmits the horizontal polarization and has a reflectivity of 66.7% for the vertical polarization, followed by a HWP at θ = 22.5° and a polarizing beam-splitter (PBS). Given an arbitrary input state |ϕ〉 = α|H〉 + β|V〉, with |α|2 + |β|2 = 1, the pPBS routes it to detector 1 with probability  . The state at the transmitting output of the pPBS,
. The state at the transmitting output of the pPBS,  , is transformed into
, is transformed into  by the HWP. Thus, the probabilities of a click at detectors 2 and 3 are, respectively,
by the HWP. Thus, the probabilities of a click at detectors 2 and 3 are, respectively,  and
and  . It is easy to check that the above probabilities can be also written as Pi = 〈ϕ|Πi|ϕ〉, with
. It is easy to check that the above probabilities can be also written as Pi = 〈ϕ|Πi|ϕ〉, with  : then, the above described apparatus implements the POVM {Πi}. Photons are detected using silicon single photon counting modules (SPCM), characterized by a dead time of 21 ns and a jitter of ~800 ps FWHM. Detection events are time-tagged with a resolution of 81 ps.
: then, the above described apparatus implements the POVM {Πi}. Photons are detected using silicon single photon counting modules (SPCM), characterized by a dead time of 21 ns and a jitter of ~800 ps FWHM. Detection events are time-tagged with a resolution of 81 ps.
Data acquisition
A two-hour continuous run of the apparatus has led to the exchange of about 109 symbols within a coincidence window of 1.5 ns. The events can be described as pairs (Ai, Bj), with i the number of the detector clicking at Alice’s side and j the one at Bob’s side. Event distribution is shown in Table 1 and Fig. 3. After the collection of all data, a QRNG20 is used to generate the bit value for each symbol. Coincidence events are then analyzed using the sifting procedure summarized in Table 2. The events of the form (Ai, Bi) are bit errors, while the others are either a “good” conclusive or an inconclusive result according to Alice’s choice. The string of conclusive results gives the sifted key, from which a secret key can be distilled using classical post-processing.
Secret key rate
Post-processing consists of a series of passages that transform a partially correlated, partially secret key into a new one Eve has negligible information of16,17. The effect of these tasks is a reduction of the number of bits and can be quantified using the secret fraction r, defined as the ratio between secure and conclusive bits16. In the asymptotic limit of infinitely long key, the key fraction of the R04 is given by9

where h(x) = −xlog2(x) − (1 − x)log2(1 − x) is the binary entropy, Q is the QBER and fEC = 1.1 is the efficiency of the error correction protocol21. The number of secure bits is given by Nconc r and, dividing it by the exposure time, the secret key rate is obtained.
Figure 4 shows the behavior of the QBER and of the key rate during a two-hour acquisition. The slight reduction in the sifted key rate is probably due to a misalignment in the fibre coupling of the entangled source. The losses can be estimated from the ratio of coincidences over single counts. The measured 5% heralding efficiency corresponds to a total loss level of13 dB, with a contribution of1.5 dB due to the POVM. The QBER is estimated as  , where I is the fraction of inconclusive results9. The QBER remains almost constant at a level below 2% for all the acquisition, thus confirming the stability of both the source and the POVM {Πi} during the acquisition. The visibility of the source in two mutually unbiased bases at the exit of the Sagnac interferometer, before fibre injection, has been measured to be between 97% and 98%: then the measured QBER level can be attributed almost completely to the source. A small contribution to the QBER is due to the small imbalances between the different channels of the POVM {Πi}. These values, estimated by computing the ratio between the raw counts at the different detectors, vary between 0.95 and 1.05, in line with what observed in the previous implementation of the POVM15.
, where I is the fraction of inconclusive results9. The QBER remains almost constant at a level below 2% for all the acquisition, thus confirming the stability of both the source and the POVM {Πi} during the acquisition. The visibility of the source in two mutually unbiased bases at the exit of the Sagnac interferometer, before fibre injection, has been measured to be between 97% and 98%: then the measured QBER level can be attributed almost completely to the source. A small contribution to the QBER is due to the small imbalances between the different channels of the POVM {Πi}. These values, estimated by computing the ratio between the raw counts at the different detectors, vary between 0.95 and 1.05, in line with what observed in the previous implementation of the POVM15.
Result obtained during 2 hour of continuous acquisition.
The time has been divided into 90 blocks of about 80 s each, with a mean number of 1.1 ⋅ 106 sifted bits. The QBER is estimated from inconclusive events, with Poissonian error bars. The secret key rate is estimated for the case of infinitely long key, using equation (2).
In a real scenario, the number of exchanged signals is always finite and the security analysis must take this fact into account. The finite key analysis of the R04 protocol is very similar to the one of the PBC0010, the only substantial difference lying in the estimation of the bit error rate. The PBC00 estimates it by comparing part of the sifted key through the public channel, while the R04 use the fraction of inconclusive results. The method is based on the fact that the choice between “good” conclusive and inconclusive results is given by a random event at Alice’s side after the exchange of all the qubits, therefore Eve has no way of differentiate between the two and their number is approximately equal9. Defining I the fraction of inconclusive results, the fraction of “good” conclusive ones can be written as (1 − Q)(1 − I). Using the Hoeffding bound22, the following inequality is valid with probability at least  :
:

where

and N is the number of exchanged symbols. This implies that, with the same probability, the QBER Q is less than  . The secret key fraction, in the case of collective attacks, is10,11
. The secret key fraction, in the case of collective attacks, is10,11

The security parameter of the obtained key is  , where the terms in the right side of the sum are the security parameters for parameter estimation, min-entropy calculation, error correction and privacy amplification respectively17. This result can be extended to the case of general attacks by exploiting the postselection technique12, giving10
, where the terms in the right side of the sum are the security parameters for parameter estimation, min-entropy calculation, error correction and privacy amplification respectively17. This result can be extended to the case of general attacks by exploiting the postselection technique12, giving10

with security parameter  .
.
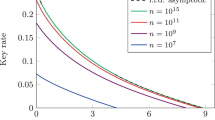
Figure 5 shows the secret key fraction of the R04 protocol in the finite key scenario. For each point, both the QBER and the number of conclusive events is evaluated on the first N exchanged symbols. The secret key fraction is calculated by using equations (5) and (6). For collective attacks, the chosen security parameter is  , with
, with  . The same value has been chosen for
. The same value has been chosen for  , therefore the term rcol of equation (6) is calculated using
, therefore the term rcol of equation (6) is calculated using  . The plots show that at least 104–105 signals are necessary to exchange a key, while already N = 106 (slightly more than half a minute at 29 kHz) gives a reasonable key fraction. The difference between the key fraction for collective and general attacks is more marked for lower values of N and tends to disappear for large number of exchanged symbols, where both approach the asymptotic key fraction.
. The plots show that at least 104–105 signals are necessary to exchange a key, while already N = 106 (slightly more than half a minute at 29 kHz) gives a reasonable key fraction. The difference between the key fraction for collective and general attacks is more marked for lower values of N and tends to disappear for large number of exchanged symbols, where both approach the asymptotic key fraction.
Discussion
In this work, we demonstrated the experimental feasibility of the equiangular three state QKD protocol R04. We showed that the scheme proposed by15 Saunders et al. for the POVM is suitable for applications in Quantum Key Distribution. State preparation was simplified by using an entanglement-based version of the protocol, with the same POVM at both Alice’s and Bob’s side. We also showed that the estimation of the bit error rate from inconclusive results is feasible in the finite key scenario. The implemented scheme was demonstrated to be stable and highly reliable, allowing a two-hour data acquisition without any significative change in the QBER value. The performance of the protocol is comparable with the BB84, despite the less efficient parameter estimation, both in the asymptotic limit and for finite key. Its simpler receiving apparatus, requiring only three single photon detectors, makes it a valid alternative to current implementations of QKD based on the BB84 protocol. Finally, this work extends the experimental investigation of equiangular spherical codes to a still uncovered area of quantum information: quantum key distribution.
Additional Information
How to cite this article: Schiavon, M. et al. Experimental realization of equiangular three-state quantum key distribution. Sci. Rep. 6, 30089; doi: 10.1038/srep30089 (2016).
References
Bennett, C. H. & Brassard, G. In Proceedings IEEE Int. Conf. on Computers, Systems and Signal Processing, Bangalore, India 175–179 (1984).
Bennet, C. H. Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68, 3121 (1992).
Tamaki, K., Koashi, M. & Imoto, N. Unconditionally secure key distribution based on two nonorthogonal states. Phys. Rev. Lett. 90, 167904 (2003).
Tamaki, K. & Lütkenhaus, N. Unconditional security of the Bennett 1992 quantum key-distribution protocol over a lossy and noisy channel. Phys. Rev. A 69, 032316 (2004).
Fung, C. H. F. & Lo, H.-K. Security proof of a three-state quantum-key-distribution protocol without rotational symmetry. Phys. Rev. A 74, 042342 (2006).
Lucamarini, M., Di Giuseppe, G. & Tamaki, K. Robust unconditionally secure quantum key distribution with two nonorthogonal and uninformative states. Phys. Rev. A 80, 32327 (2009).
Phoenix, S., Barnett, S. & Chefles, A. Three-state quantum cryptography. J. Mod. Opt. 47, 507 (2000).
Renes, J. M. Spherical code key distribution protocols for qubits. Phys. Rev. A 70, 052314 (2004).
Boileau, J.-C., Tamaki, K., Batuwantudawe, J., Laflamme, R. & Renes, J. M. Unconditional security of a three state quantum key distribution protocol. Phys. Rev. Lett. 94, 040503 (2005).
Mafu, M., Garapo, K. & Petruccione, F. Finite-key-size security of the Phoenix-Barnett-Chefles 2000 quantum-key-distribution protocol. Phys. Rev. A 90, 032308 (2014).
Scarani, V. & Renner, R. Quantum cryptography with finite resources: unconditional security bound for discrete-variable protocols with one-way postprocessing. Phys. Rev. Lett. 100, 200501 (2008).
Christandl, M., König, R. & Renner, R. Postselection technique for quantum channels with applications to quantum cryptography. Phys. Rev. Lett. 102, 020504 (2009).
Clarke, R. B. M., Chefles, A., Barnett, S. M. & Riis, E. Experimental demonstration of optimal unambiguous state discrimination. Phys. Rev. A 63, 040305(R) (2001).
Clarke, R. B. M. et al. Experimental realization of optimal detection strategies for overcomplete states. Phys. Rev. A 64, 012303 (2001).
Saunders, D. J. et al. The simplest demonstrations of quantum nonlocality. New J. Phys. 14, 113020 (2012).
Scarani, V. et al. The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301 (2009).
Scarani, V. & Renner, R. In Proceedings of TQC2008, Lecture Notes in Computer Science 5106 83–95 (2008).
Kim, T., Fiorenting, M. & Wong, F. N. C. Phase-stable source of polarization-entangled photons using a polarization Sagnac interferometer. Phys. Rev. A 73, 012316 (2006).
Fedrizzi, A., Herbst, T., Poppe, A., Jennewein, T. & Zeilinger, A. A wavelength-tunable fiber-coupled source of narrowband entangled photons. Opt. Express 15, 15377 (2007).
Vallone, G., Marangon, D. G., Tomasin, M. & Villoresi, P. Quantum randomness certified by the uncertainty principle. Phys. Rev. A 90, 52327 (2014).
Martinez-Mateo, J., Pacher, V., Peev, M., Ciurana, A. & Martin, V. Demystifying the information reconciliation protocol Cascade. Quantum Information & Computation vol. 15, no. 5&6, pp 453–477 (2015).
Hoeffding, W. Probability inequalities for sums of bounded random variables. J. Amer. Stat. Assoc. 58, 13 (1963).
Acknowledgements
We thank Davide G. Marangon and Nicola Laurenti for helpful discussions. This work has been carried out within the Strategic-Research-Project QUANTUMFUTURE of the University of Padova and the Strategic-Research-Project QUINTET of the Department of Information Engineering, University of Padova. M.S. acknowledges the Ministry of Research and the Center of Studies and Activities for Space (CISAS) “Giuseppe Colombo” for financial support. Figures 1 and 2 use elements from the ComponentLibrary by Alexander Franzen.
Author information
Authors and Affiliations
Contributions
All authors conceived the work. G.V. and M.S. derived the theoretical rate equations and M.S. realized the experiment. All authors contributed to the final manuscript.
Ethics declarations
Competing interests
The authors declare no competing financial interests.
Rights and permissions
This work is licensed under a Creative Commons Attribution 4.0 International License. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in the credit line; if the material is not included under the Creative Commons license, users will need to obtain permission from the license holder to reproduce the material. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/
About this article
Cite this article
Schiavon, M., Vallone, G. & Villoresi, P. Experimental realization of equiangular three-state quantum key distribution. Sci Rep 6, 30089 (2016). https://doi.org/10.1038/srep30089
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/srep30089
This article is cited by
-
Unbounded randomness from uncharacterized sources
Communications Physics (2022)
-
Certification of a non-projective qudit measurement using multiport beamsplitters
Nature Physics (2022)
-
Experimentally attacking quantum money schemes based on quantum retrieval games
Scientific Reports (2019)
-
Unconditional security of a K-state quantum key distribution protocol
Quantum Information Processing (2018)
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.