Abstract
While the objective of conventional quantum key distribution (QKD) is to secretly generate and share the classical bits concealed in the form of maximally mixed quantum states, that of private quantum channel (PQC) is to secretly transmit individual quantum states concealed in the form of maximally mixed states using shared one-time pad and it is called Gaussian private quantum channel (GPQC) when the scheme is in the regime of continuous variables. We propose a GPQC enhanced with squeezed coherent states (GPQCwSC), which is a generalization of GPQC with coherent states only (GPQCo) [Phys. Rev. A 72, 042313 (2005)]. We show that GPQCwSC beats the GPQCo for the upper bound on accessible information. As a subsidiary example, it is shown that the squeezed states take an advantage over the coherent states against a beam splitting attack in a continuous variable QKD. It is also shown that a squeezing operation can be approximated as a superposition of two different displacement operations in the small squeezing regime.
Similar content being viewed by others
Introduction
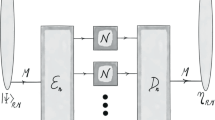
The notion of private quantum channel (PQC) or quantum one-time pad1 is very useful in quantum information processing, such as superdense coding2, quantum data hiding3, quantum state sharing protocol4 (for improving their efficiency) and the proof of additivity counter-example of the classical capacity on quantum channels5,6. The PQC is briefly introduced as follows. If the two communicating parties, Alice and Bob, share a classical secret key (e.g., via quantum key distribution procedure), then PQC can be used to transmit an arbitrary unknown quantum state from Alice to Bob securely. The intermediate state in PQC is close to the maximally mixed state, so the state exhibits almost maximum entropy. The receiver Bob always decrypts the encoded state by using the unitary inverse operations from the pre-shared secret key, whereas no third party (not having the key) can obtain the original quantum state. Private quantum channel which belongs to a completely positive and trace preserving-map, represents the transformation of any quantum states into the maximally mixed state. It is different from the private capacity of quantum channels7,8,9 that is the maximally transmitted rate of classical secret information on quantum channels. A discrete version of private quantum channel was first proposed by Ambainis et al.1 in 2000 and the optimality of PQC was proved that we need exactly d2 unitary operations to encrypt a d-dimensional quantum state10,11. In the case of approximate encryption, it is sufficient to have the number of unitary operations being less than d log d3,12,13.
Then, it is natural to ask how we can realize the PQC in continuous variable (CV) systems. Previously Brádler proposed CV private quantum channel (PQC) using coherent states that are obtained by displacement operations on the vacuum state14, where he defined a CV maximally mixed state in Gaussian regime and then constructed GPQC via the conformation method of coherent states. Generally a single-mode Gaussian state is parametrized as a combination of displacement, squeezing operations and a thermal field15. Specifically squeezed states, which were considered in CV quantum key distribution16,17,18,19,20, are crucial for a security demonstration of quantum key distribution using coherent states21. Moreover squeezed coherent states are useful for enhancing the security of quantum cryptography22,23 and for improving phase sensitivities of interferometers24.
In this paper, we generalize the Gaussian private quantum channel (GPQC) with a combination of displacement and squeezing operations. Explicitly, we construct GPQC in terms of the displacement and the squeezing elements,  whereas Brádler’s GPQC is represented only by the displacement element,
whereas Brádler’s GPQC is represented only by the displacement element,  . Then, we study a subsidiary example of GPQC with squeezed coherent states (GPQCwSC), especially for an eavesdropping attack. In the limit of small squeezing, furthermore, we show that the squeezed coherent states can approach a non-Gaussian regime by replacing the squeezing operation with a non-Gaussian operation, i.e., a superposition operation of two different displacements.
. Then, we study a subsidiary example of GPQC with squeezed coherent states (GPQCwSC), especially for an eavesdropping attack. In the limit of small squeezing, furthermore, we show that the squeezed coherent states can approach a non-Gaussian regime by replacing the squeezing operation with a non-Gaussian operation, i.e., a superposition operation of two different displacements.
Gaussian private quantum channel (GPQC): coherent states
Gaussian private quantum channel (GPQC) was introduced by Brádler in 2005, where he defined a maximally mixed state as 1b in Gaussian regime14. Similarly to the discrete case (identity over the dimension: 1/d), the CV maximally mixed state in phase space has a broad Gaussian shape (because equiprobable mixture depends only on the radius at some boundary). Brádler’s main proposition is that the Hilbert-Schmidt distance dHS between the CV maximally mixed state and PQC-encryption of arbitrary coherent states is very close for sufficiently large N (N: number of input displacement operations),

where ΓN denotes the mixture of all conformations of coherent states that will be defined in Eqs (3) and (4). Also note that  for any matrices ρ1,2 and it is symmetric,
for any matrices ρ1,2 and it is symmetric,  . By using the unitary invariance of the distance, we can prove the statement on an arbitrary coherent state
. By using the unitary invariance of the distance, we can prove the statement on an arbitrary coherent state  : for
: for  and CV private quantum channel
and CV private quantum channel  ,
,  where
where  is a displaced CV maximally mixed state from 1b to the position of
is a displaced CV maximally mixed state from 1b to the position of  . The proof is a bit complex but straightforward (See details in Ref.14).
. The proof is a bit complex but straightforward (See details in Ref.14).
Now we review the (Brádler’s) CV maximally mixed state14. A CV maximally mixed state can be chosen as an integral performed over all possible single mode states within the boundary circle of radius r ≤ b in a coherent state  . If r > b, the occurrence probability is 0. The coherent state is created by applying the displacement operator
. If r > b, the occurrence probability is 0. The coherent state is created by applying the displacement operator  to the vacuum state
to the vacuum state  as
as  . Then, we have the CV maximally mixed state
. Then, we have the CV maximally mixed state

where the normalization constant is C = πb2.
The purpose of GPQC is to encrypt an input coherent state into a high entropy state. Thus the encryption should be close to the maximally mixed state in Hilbert-Schmidt distance. In order to do that, we introduce a notion of conformation through vacuum displacements. Note that  for
for  , where p and q are positive integers. For some fixed p, an input coherent state is described by
, where p and q are positive integers. For some fixed p, an input coherent state is described by  . From the Ref. 14, the general and slightly modified p-conformation
. From the Ref. 14, the general and slightly modified p-conformation  is given by the following equations
is given by the following equations


where  for m = n mod p and 0 for otherwise. The Eq. (4) is followed by the absorption of the phase term into
for m = n mod p and 0 for otherwise. The Eq. (4) is followed by the absorption of the phase term into  ’s and
’s and  ’s. This is equivalent to the Brádler’s original p-conformation. The conformation technique provides an equiprobable positioning of vacuum states at some fixed radius rp, so the uniformity of the distribution of CV quantum states is strengthened.
’s. This is equivalent to the Brádler’s original p-conformation. The conformation technique provides an equiprobable positioning of vacuum states at some fixed radius rp, so the uniformity of the distribution of CV quantum states is strengthened.
Finally we review the mixture of all p-conformations (p = 1, …, N). Suppose that N ≥ 1 and define  , then
, then

where  . As an encrypted state of GPQC, the ΓN represents the output state of PQC over (uniformly chosen) M unitary operations, where the input state is in vacuum state
. As an encrypted state of GPQC, the ΓN represents the output state of PQC over (uniformly chosen) M unitary operations, where the input state is in vacuum state  . One of the M CV states is fixed by pre-shared classical secret key between Alice and Bob as (classical) one-time pad and then it is sent to Bob. The Brádler’s proposition states that ΓN is sufficiently close to the CV maximally mixed state. Encoding an arbitrary coherent state
. One of the M CV states is fixed by pre-shared classical secret key between Alice and Bob as (classical) one-time pad and then it is sent to Bob. The Brádler’s proposition states that ΓN is sufficiently close to the CV maximally mixed state. Encoding an arbitrary coherent state  is essentially equivalent to the vacuum state encryption for the unitary invariance of the distance:
is essentially equivalent to the vacuum state encryption for the unitary invariance of the distance:  . Also note that, for any completely positive and trace-preserving (CPT) map
. Also note that, for any completely positive and trace-preserving (CPT) map  ,
,  (See Eq. (9) in Ref. 14). Therefore we derive Brádler’s main result as Eq. (1) by combining the above properties of CV maximally mixed state, p-conformation and its mixture.
(See Eq. (9) in Ref. 14). Therefore we derive Brádler’s main result as Eq. (1) by combining the above properties of CV maximally mixed state, p-conformation and its mixture.
Results
Gaussian private quantum channel: squeezed coherent states
To construct a GPQCwSC, we examine a single-mode squeezed vacuum state. A single-mode squeezing operation is defined by  , where ξ = reiϕ. When we apply the squeezing operator to the vacuum state, we produce a squeezed vacuum state such that
, where ξ = reiϕ. When we apply the squeezing operator to the vacuum state, we produce a squeezed vacuum state such that

Then, applying a displacement operation, we obtain a coherent squeezed state  which forms an overcomplete set, i.e.,
which forms an overcomplete set, i.e.,  25. It is a main ingredient of the squeezed CV conformation.
25. It is a main ingredient of the squeezed CV conformation.
For simplicity, we consider a squeezed coherent state, instead of the coherent squeezed state. It is reasonable that squeezed coherent states are transformed into coherent squeezed states by the relation,  25. Generally, a squeezed coherent state represents squeezing of a coherent state26,
25. Generally, a squeezed coherent state represents squeezing of a coherent state26,

where  and ϕ = arg(ξ), the argument of the squeezing parameter ξ. Hm(·) denotes the mth-degree complex Hermite polynomials. By exploiting the Eq. (6), we can derive a squeezed conformations and its mixture in the following section. Then we prove that, for sufficiently large N and for any squeezing of a coherent state
and ϕ = arg(ξ), the argument of the squeezing parameter ξ. Hm(·) denotes the mth-degree complex Hermite polynomials. By exploiting the Eq. (6), we can derive a squeezed conformations and its mixture in the following section. Then we prove that, for sufficiently large N and for any squeezing of a coherent state  , there exists a CPT map
, there exists a CPT map  such that
such that  (See following second section.)
(See following second section.)
General squeezed conformations
Now, we show the explicit calculation of the squeezed p-conformation. Let us apply the squeezing operation to the coherent state  ,
,

where  and v = eiϕsinhr (p and q are positive integers). Using the following relations:
and v = eiϕsinhr (p and q are positive integers). Using the following relations:  and 2 sinh r · cosh r
and 2 sinh r · cosh r  , then we derive the formula
, then we derive the formula

where  and c.c. denotes the complex conjugate of the argument of Hm. The definition of K determines the position of squeezed coherent states and the squeezing angles, as shown in Fig. 1.
and c.c. denotes the complex conjugate of the argument of Hm. The definition of K determines the position of squeezed coherent states and the squeezing angles, as shown in Fig. 1.
Then, we can find the squeezed p-conformation

where  and the constant κm,n is defined by
and the constant κm,n is defined by

For some fixed squeezing r and the argument ϕ, the (complex) Hermite polynomials are orthogonal to each other for m ≠ n such that the value of κm,n becomes a constant. The κm,n converges to  as r → 0. Therefore, the factor for some p,
as r → 0. Therefore, the factor for some p,  , is the main component in Eq. (9).
, is the main component in Eq. (9).
We finally consider the mixture of all squeezed p-conformations for 0 ≤ p ≤ N. Suppose N ≥ 1 and define  , then
, then

where  . Alice equiprobably chooses one from the set of M displacement operators
. Alice equiprobably chooses one from the set of M displacement operators  and the squeezing parameter r > 0. (Once again note that, for some fixed p and r, the squeezing argument ϕ depends on θpq for all q.) Alice sends the encrypted state through a quantum channel towards Bob who performs the inverse operations to decrypt the state.
and the squeezing parameter r > 0. (Once again note that, for some fixed p and r, the squeezing argument ϕ depends on θpq for all q.) Alice sends the encrypted state through a quantum channel towards Bob who performs the inverse operations to decrypt the state.
The point is that we encrypt an arbitrary input state, i.e., an arbitrary coherent state  . Then, we can write down a general encryption CPT map
. Then, we can write down a general encryption CPT map  with M unitary elements as in Ref. 14
with M unitary elements as in Ref. 14

From the above equation, we propose that the corresponding Hilbert-Schmidt (HS) distance is equivalent to one of Eq. (11),  by the unitary invariance of the HS distance, whereas the states are not the same as
by the unitary invariance of the HS distance, whereas the states are not the same as  .
.
The proof of the main proposition and the number of secret bits
Here we prove our main proposition. The proposition is as follow: For sufficiently large N in any squeezing of an arbitrary coherent state  , there exists CPT map
, there exists CPT map  such that
such that


where the HS distance between ib and  becomes quite close in sufficiently large N. The Eq. (12) is obtained from the unitary invariance of the HS distance. The Eq. (13) is derived via the unitary invariance of squeezing operations in the HS distance (Eq. (14) below) and it is followed by the norm convexity (Eq. (15)). Explicitly speaking, in the case of ξ > 0, we assert that
becomes quite close in sufficiently large N. The Eq. (12) is obtained from the unitary invariance of the HS distance. The Eq. (13) is derived via the unitary invariance of squeezing operations in the HS distance (Eq. (14) below) and it is followed by the norm convexity (Eq. (15)). Explicitly speaking, in the case of ξ > 0, we assert that 

where the second equality also holds by the unitary invariance in the HS distance, i.e., for all unitary  and
and  ,
, 
 . In general, the last equality is not exactly equal to zero, but, asymptotically converges to 0, i.e.,
. In general, the last equality is not exactly equal to zero, but, asymptotically converges to 0, i.e.,  27.
27.
Therefore, by using the norm convexity and the above equations (within the symmetric property of the HS distance) we derive

Thus, it implies that 1b approximately equals to the sum of the squeezed coherent states and therefore completes the proof.
In addition, we mention the total number of unitary operations L and corresponding secret bits. The number of total displacement is  and just one (pre-fixed) squeezing operation is required. From this reason, L = M + 1. Thus, we have the number of secret bits of
and just one (pre-fixed) squeezing operation is required. From this reason, L = M + 1. Thus, we have the number of secret bits of  for
for  . It is interesting to note that if we use the approximate random unitary channels such as in Refs. 3,12,13, then it is expected to construct PQC with only about
. It is interesting to note that if we use the approximate random unitary channels such as in Refs. 3,12,13, then it is expected to construct PQC with only about  -bits of secret keys. There is no advantage in the key efficiency, but the accessible information can be slightly improved as follow.
-bits of secret keys. There is no advantage in the key efficiency, but the accessible information can be slightly improved as follow.
Holevo bound on the GPQCwSC
One of important principles of the von Neumann entropy states that quantum operations never increase the quantum mutual information. By using this property, we propose that our GPQCwSC is stronger (i.e., tight upper bound) than the Brádler’s GPQC in the language of accessible information.
Formally, Brádler’s protocol14 with coherent states consists of a set of  where
where  denotes the set of all coherent states
denotes the set of all coherent states  ,
,  is the probability distribution of
is the probability distribution of  ,
,  is the CPT map with
is the CPT map with  displacement operations and
displacement operations and  is the (displaced) CV maximally mixed state. Similarly, let us express our GPQCwSC as a set of
is the (displaced) CV maximally mixed state. Similarly, let us express our GPQCwSC as a set of  where squeezing elements are added and the set
where squeezing elements are added and the set  emphasizes the squeezing with displacement operations. Then we assert that
emphasizes the squeezing with displacement operations. Then we assert that 

where the Holevo information  . The B and E are corresponding to input and output distributions of the channel
. The B and E are corresponding to input and output distributions of the channel  between Bob and Eve and the maximum of the accessible information (by Eve) is taken over all input ensemble
between Bob and Eve and the maximum of the accessible information (by Eve) is taken over all input ensemble  in the channel. Note that the quantum mutual information is defined by
in the channel. Note that the quantum mutual information is defined by  for any quantum system A and B, where
for any quantum system A and B, where  is the von Neumann entropy. This fact directly comes from ‘the principle of quantum operation’ about the entropy: For any quantum operation Q,
is the von Neumann entropy. This fact directly comes from ‘the principle of quantum operation’ about the entropy: For any quantum operation Q,  . If we substitute Q to a squeezing operation
. If we substitute Q to a squeezing operation  and define
and define  and
and  for some ensembles
for some ensembles  and
and  , respectively, then we have
, respectively, then we have

This provides a better upper bound on the accessible information  than the Brádler’s analysis. In other words, the amount of eavesdropping information on the encrypted state via the GPQCwSC is less than that by the Brádler’s GPQC.
than the Brádler’s analysis. In other words, the amount of eavesdropping information on the encrypted state via the GPQCwSC is less than that by the Brádler’s GPQC.
Subsidiary example of GPQC
We introduce a simple example that squeezed coherent states can take an advantage over coherent states in CV quantum key distribution, where the scheme is in a preliminary procedure of GPQC. To distribute quantum keys, we consider the BB84 protocol28. In discrete variable systems, Alice and Bob share keys with single photon states in mutually unbiased bases. In continuous variable (CV) systems, correspondingly, Alice and Bob share keys with Gaussian states in uncertainty relation of field quadratures. Then, in the limit of small squeezing, we show that the squeezed coherent state scheme can approach even a non-Gaussian regime by replacing a squeezing operation with a superposition operation of two different displacements.
Simple eavesdropping attack in CV quantum key distribution
As a simple eavesdropping attack, we assume that Eve performs a beam splitting attack. As an input state, we compare a squeezed coherent state with a coherent one. For an input squeezed coherent state, Eve transforms the input state by a 50:50 beam splitter,

where the subscript B (E) represents Bob (Eve) and the transformation of the squeezing operation is given by Ref. 29. When Eve performs a measurement to get an information of the input state  , the state
, the state  sent to Bob is disturbed by the non-local effect of the two-mode squeezing operation
sent to Bob is disturbed by the non-local effect of the two-mode squeezing operation  , except the uncertainty of the field quadrature. For an input coherent state, there is no non-local effect after the beam splitting attack. For the beam splitting attack, thus, Alice and Bob detect the existence of Eve much easier with the input squeezed coherent state than the input coherent one.
, except the uncertainty of the field quadrature. For an input coherent state, there is no non-local effect after the beam splitting attack. For the beam splitting attack, thus, Alice and Bob detect the existence of Eve much easier with the input squeezed coherent state than the input coherent one.
Non-Gaussian regime
We show that the squeezed coherent state can approach even a non-Gaussian regime. In the limit of small squeezing, we describe a non-Gaussian regime by a truncation of the squeezing parameter,  . However the truncation operation is not implemented by reducing the squeezing parameter in experiment. In order to apply the truncation operation to coherent states, we consider a superposition operation of two different displacements. Since an even coherent state is quite similar to a squeezed vacuum state, we derive the corresponding parameters in the limit of
. However the truncation operation is not implemented by reducing the squeezing parameter in experiment. In order to apply the truncation operation to coherent states, we consider a superposition operation of two different displacements. Since an even coherent state is quite similar to a squeezed vacuum state, we derive the corresponding parameters in the limit of  ,
,

where  and ξ = reiϕ. When
and ξ = reiϕ. When  , the even coherent state is approximated to the squeezed vacuum state. Note that, for
, the even coherent state is approximated to the squeezed vacuum state. Note that, for  , the even coherent state is close to a Gaussian state but it is a non-Gaussian state30. Therefore, the variables r and ϕ in the squeezing parameter can be replaced by the ones β and φ in the even coherent state.
, the even coherent state is close to a Gaussian state but it is a non-Gaussian state30. Therefore, the variables r and ϕ in the squeezing parameter can be replaced by the ones β and φ in the even coherent state.
We need to know if the uncertainties of the field quadratures are maintained by replacing the squeezed vacuum state with the even coherent state. Because CV quantum key distribution is secured via uncertainties of field quadratures16,17,18. Using the quadrature operator  , we derive the quadrature variance of the squeezed vacuum state as
, we derive the quadrature variance of the squeezed vacuum state as

where the quadrature variance is approximated for  . According to the phase parameter ϕ, the quadrature variance oscillates between
. According to the phase parameter ϕ, the quadrature variance oscillates between  and
and  . The quadrature variance of the even coherent state is given by
. The quadrature variance of the even coherent state is given by

where the quadrature variance is approximated for  . According to the phase parameter φ, the quadrature variance oscillates between
. According to the phase parameter φ, the quadrature variance oscillates between  and
and  . For the quadrature variances, thus,
. For the quadrature variances, thus,  corresponds to r. Therefore, we find that the uncertainties of the field quadratures are maintained in the substitution of the even coherent state for the squeezed vacuum state. Note that, for the beam splitting attack, the even coherent state also plays a role of a squeezing operator by generating an entangled state with a beam splitter.
corresponds to r. Therefore, we find that the uncertainties of the field quadratures are maintained in the substitution of the even coherent state for the squeezed vacuum state. Note that, for the beam splitting attack, the even coherent state also plays a role of a squeezing operator by generating an entangled state with a beam splitter.
Now we see how to realize the non-Gaussian operation with an optical implementation of a superposition operation of two different displacements, as shown in Fig. 2. Previously the displacement operation was implemented by a beam splitter with high reflectivity31, where the displacement amplitude is described with the multiplication  of an amplitude of coherent lights (γ) and the transmission coefficient of the beam splitter (T). In Fig. 2, the superposition operation of two different displacements is implemented by a beam splitter with high reflectivity (T → 0), where
of an amplitude of coherent lights (γ) and the transmission coefficient of the beam splitter (T). In Fig. 2, the superposition operation of two different displacements is implemented by a beam splitter with high reflectivity (T → 0), where  represents β in the superposition operation of two different displacements. Note that the input even coherent state can be generated by a nonlinear Kerr medium32,33,34 in all-optical systems.
represents β in the superposition operation of two different displacements. Note that the input even coherent state can be generated by a nonlinear Kerr medium32,33,34 in all-optical systems.
Discussion
We have constructed GPQCwSC by an equiprobable combination of squeezed coherent states in a continuous-variable regime generalizing GPQCo and shown that GPQCwSC tightens the upper bound on accessible information. We have also presented a simple intuitive understanding of the well-known fact that the squeezed state scheme has better security than the coherent state scheme in continuous variable QKD. A class of non-Gaussian operations, superpositions of two different displacements, is shown to be an approximation of small squeezing operations. With these results, we pursue an all-optical implementation of PQC feasible with available optical technology. As some non-Gaussian states are more robust against decoherence than Gaussian states35,36,37, we look forward to investigating non-Gaussian quantum communications compared to GPQC with decoherence.
Additional Information
How to cite this article: Jeong, K. et al. Gaussian private quantum channel with squeezed coherent states. Sci. Rep. 5, 13974; doi: 10.1038/srep13974 (2015).
References
Ambainis, A., Mosca, M., Tapp, A. & de Wolf, R. Private quantum channels. IEEE 54th Annual Symposium on Foundations of Computer Science p. 547 (2000), Redondo Beach, California. (2000, November 12–14).
Harrow, A., Hayden, P. & Leung, D. Superdense Coding of Quantum States. Phys. Rev. Lett. 92, 187901 (2004).
Hayden, P., Leung, D., Shor, P. W. & Winter, A. Randomizing Quantum States: Constructions and Applications. Commun. Math. Phys. 250, 371 (2004).
Chi, D. P. & Jeong, K. Approximate Quantum State Sharings via Pair of Private Quantum Channels. J. Quant. Info. Sci. 4, 64 (2014).
Hayden, P. & Winter, A. Counterexamples to the Maximal p-Norm Multiplicativity Conjecture for all p >1. Commun. Math. Phys. 284, 263 (2008).
Hastings, M. B. Superadditivity of communication capacity using entangled inputs. Nature Phys. 5, 255 (2009).
Pirandola, S., García-Patrón, R., Braunstein, S. L. & Lloyd, S. Direct and Reverse Secret-Key Capacities of a Quantum Channel. Phys. Rev. Lett. 102, 050503 (2009).
Takeoka, M., Guha, S. & Wilde, M. M. Fundamental rate-loss tradeoff for optical quantum key distribution. Nature Commun. 5, 5235 (2014).
Li, K., Winter, A., Zou, X. & Guo, G. Private Capacity of Quantum Channels is Not Additive. Phys. Rev. Lett. 103, 120501 (2009).
Nagaj, D. & Kerenidis, I. On the optimality of quantum encryption schemes. J. Math. Phys. 47, 092102 (2006).
Bouda, J. & Ziman, M. Optimality of private quantum channels. J. Phys. A: Math. Theor. 40, 5415 (2007).
Dickinson, P. A. & Nayak, A. Approximate Randomization of Quantum States With Fewer Bits of Key. Quantum Computing Back Action, IIT Kanpur, AIP Conf. Proc.864, 18 (2006), Springer, New York. (2006, March 6–12).
Aubrun, G. On Almost Randomizing Channels with a Short Kraus Decomposition. Commun. Math. Phys. 288, 1103 (2009).
Brádler, K. Continuous-variable private quantum channel. Phys. Rev. A 72, 042313 (2005).
Marian, P., Marian, T. A. & Scutaru, H. Quantifying Nonclassicality of One-Mode Gaussian States of the Radiation Field. Phys. Rev. Lett. 88, 153601 (2002).
Ralph, T. C. Continuous variable quantum cryptography. Phys. Rev. A 61, 010303(R) (2000).
Ralph, T. C. Security of continuous-variable quantum cryptography. Phys. Rev. A 62, 062306 (2000).
Hillery, M. Quantum cryptography with squeezed states. Phys. Rev. A 61, 022309 (2000).
Gottesman, D. & Preskill, J. Secure quantum key distribution using squeezed states. Phys. Rev. A 63, 022309 (2001).
Cerf, N. J., Lévy, M. & Van Assche, G. Quantum distribution of Gaussian keys using squeezed states. Phys. Rev. A 63, 052311 (2001).
Grosshans, F. et al. Quantum key distribution using gaussian-modulated coherent states. Nature 421, 238 (2003).
Lu, Y. J., Zhu, L. & Ou, Z. Y. Security improvement by using a modified coherent state for quantum cryptography. Phys. Rev. A 71, 032315 (2005).
Yin, Z.-Q., Han, Z.-F., Sun, F.-W. & Guo, G.-C. Decoy state quantum key distribution with modified coherent state. Phys. Rev. A 76, 014304 (2007).
Caves, C. M. Quantum-mechanical noise in an interferometer. Phys. Rev. D 23, 1693 (1980).
Barnett, S. M. & Radmore, P. M. Methods in Theoretical Quantum Optics. Oxford University Press (1997).
Vogel, W. & Welsch, D.-G. Quantum Optics. WILEY-VCH Verlag GmbH & Co. KGaA (2006).
Dodonov, V. V., Man’ko, O. V., Man’ko, V. I. & Wünsche, A. Energy-sensitive and “lassical-like” Distances between Quantum States. Phys. Scr. 59, 81 (1999).
Bennett, C. H. & Brassard, G. Quantum cryptography: Public key distribution and coin tossing. Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, pp. 175–179, 8 (1984), Bangalore, India. IEEE Computer Society Press, New York. (1984, December 10-12).
Kim, M. S., Son, W., Bužek, V. & Knight, P. L. Entanglement by a beam splitter: Nonclassicality as a prerequisite for entanglement. Phys. Rev. A 65, 032323 (2002).
Genoni, M. G. & Paris, M. G. A. Quantifying non-Gaussianity for quantum information. Phys. Rev. A 82, 052341 (2010).
Lvovsky, A. I. & Babichev, S. A. Synthesis and tomographic characterization of the displaced Fock state of light. Phys. Rev. A 66, 011801(R) (2002).
Mecozzi, A. & Tombesi, P. Distinguishable quantum states generated via nonlinear birefringence. Phys. Rev. Lett. 58, 1055 (1987).
Yurke, B. & Stoler, D. Quantum behavior of a four-wave mixer operated in a nonlinear regime. Phys. Rev. A 35, 4846 (1987).
Gerry, C. C. Generation of optical macroscopic quantum superposition states via state reduction with a Mach-Zehnder interferometer containing a Kerr medium. Phys. Rev. A 59, 4095 (1999).
Sabapathy, K. K., Ivan, J. S. & Simon, R. Robustness of Non-Gaussian Entanglement against Noisy Amplifier and Attenuator Environments. Phys. Rev. Lett. 107, 130501 (2011).
Lee, J., Kim, M. S. & Nha, H. Comment on “Role of Initial Entanglement and Non-Gaussianity in the Decoherence of Photon-Number Entangled States Evolving in a Noisy Channel”. Phys. Rev. Lett. 107, 238901 (2011).
Nha, H., Lee, S.-Y., Ji, S.-W. & Kim, M. S. Efficient Entanglement Criteria beyond Gaussian Limits Using Gaussian Measurements. Phys. Rev. Lett. 108, 030503 (2012).
Acknowledgements
We are grateful to K. Brádler for comments. This work was partly supported by the IT R&D program of MOTIE/KEIT [10043464]. S.Y.L. acknowledges support from FQXI and the National Research Foundation and Ministry of Education in Singapore.
Author information
Authors and Affiliations
Contributions
K.J. identified and proposed the study. All the authors carried out the calculations and the analysis of results.
Ethics declarations
Competing interests
The authors declare no competing financial interests.
Rights and permissions
This work is licensed under a Creative Commons Attribution 4.0 International License. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in the credit line; if the material is not included under the Creative Commons license, users will need to obtain permission from the license holder to reproduce the material. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/
About this article
Cite this article
Jeong, K., Kim, J. & Lee, SY. Gaussian private quantum channel with squeezed coherent states. Sci Rep 5, 13974 (2015). https://doi.org/10.1038/srep13974
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/srep13974
This article is cited by
-
Maximally entangled states in discrete and Gaussian regimes
Quantum Information Processing (2019)
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.



 of ξ depends on
of ξ depends on  .
. : (a) non-squeezed (r = 0), (b) ϕ = 0, (c)
: (a) non-squeezed (r = 0), (b) ϕ = 0, (c)  and (d)
and (d)  cases, respectively.
cases, respectively.