Abstract
Identifying the most influential spreaders is an important issue in understanding and controlling spreading processes on complex networks. Recent studies showed that nodes located in the core of a network as identified by the k-shell decomposition are the most influential spreaders. However, through a great deal of numerical simulations, we observe that not in all real networks do nodes in high shells are very influential: in some networks the core nodes are the most influential which we call true core, while in others nodes in high shells, even the innermost core, are not good spreaders which we call core-like group. By analyzing the k-core structure of the networks, we find that the true core of a network links diversely to the shells of the network, while the core-like group links very locally within the group. For nodes in the core-like group, the k-shell index cannot reflect their location importance in the network. We further introduce a measure based on the link diversity of shells to effectively distinguish the true core and core-like group and identify core-like groups throughout the networks. Our findings help to better understand the structural features of real networks and influential nodes.
Similar content being viewed by others
Introduction
The most influential nodes can maximize the speed and scope of information spreading compared with other nodes in a network1. Locating these influential nodes is important in improving the use of available resources2 and controlling the spread of information3. A critical issue is how to determine and distinguish the spreading capability of a node. Centrality is usually used to measure the relative importance of nodes within the network, such as degree centrality4, betweenness centrality5, closeness centrality6, eigenvector centrality7, PageRank centrality8 and its variance9. Nodes with high centrality are considered more influential in the spreading process10,11,12,13,14. Among these measures, degree centrality is a simple and effective way, although it is based only on local link information15,16. The merit of degree is challenged by a recent study12, in which the authors pointed out that the most influential spreaders do not correspond to the nodes with largest degree, but are those located in the core of the network as identified by the k-shell decomposition17. This means the higher coreness of a node, the more influential it is in the spreading dynamics.
The k-shell decomposition decomposes a network into hierarchically ordered shells by recursively pruning the nodes with degree less than current shell index (see Methods for details). This procedure assigns each node with an index kS, representing its coreness in the network. A large kS value means a core position in the network, while a small kS value defines the periphery of the network12. Because of a low computational complexity of O(N + E)18, where N is the network size and E is the number of edges in the network, this method is extensively used for large-scale network analysis. Generally speaking, it is used to efficiently visualize the structure of large-scale networks19,20, analyze the core structure of networks21,22,23,24,25 and capture the essential structural properties of real networks26. Since the publication of Ref. 12, the coreness is widely used to quantify the importance of a node in a spreading process27,28,29. For example, in a economic crisis network, nodes with the highest coreness are most likely to spread a crisis globally30, while in a rumor spreading, nodes with high coreness act as firewalls to prevent the diffusion of a rumor to the whole system31. Even nodes with low coreness are considered as bridge elements, which can effectively control the disease in small world networks through an acquaintance-based vaccination strategy32. Many works extended the k-shell decomposition method, either modify it for a better ranking33,34,35,36,37 or generalize it to weighted networks38,39, dynamical networks40 and multiplex networks41.
In all these studies, the k-shell decomposition is used as a powerful tool to analyze the network structure and identify important nodes. Despite its effectiveness, researchers have noticed that the k-shell method has some defects28,42. For example, when there is a lack of the complete network structure, one can not apply the k-shell decomposition to the network. In tree structure and BA model network, the capability of finding influential spreaders is limited due to the low resolution of kS index. Here, from the perspective of spreading efficiency of cores that have been identified by the k-shell decomposition, we study on whether in different real networks do the core nodes have a higher spreading influence than other nodes. In a common belief, it is. But through intensive computer simulations, we find that it is not the case. In some networks core nodes have the largest spreading efficiency, while in others core nodes have relatively low spreading efficiency. What is the reason for the obvious distinct results? No work has focused on this question to our knowledge. In Refs. 12, 37, the authors pointed out that the performance of centrality measure relates somehow to the infection probability when evaluating the spreading capability of nodes. We find that although the infection probability will cause some fluctuations, the specific structure of real networks is the origin of the distinct performance of coreness in predicting spreading efficiency: in the first case, the core of a network has a link diversity to other shells of the network, while in the latter case the core is linked very locally. We respectively call them true core and core-like group. Then, we propose a measure of information entropy to locate core-like groups in real networks. These findings will help us in understanding the real network structures.
Results
We first calculate the imprecision of coreness and degree in identifying influential spreaders and discover the true core and core-like group in real networks. We then analyze the structural features of the true core and core-like group and uncover their difference. Finally we successfully locate the core-like groups throughout the network by defining a measure of link entropy.
Calculating the imprecision function of coreness and degree in the SIR spreading process
We use a classic Susceptible-Infected-Recovered (SIR) spreading model to simulate the spreading process43,44 and record the spreading capability (or spreading efficiency) of each node, which is defined as the average size of infected population M for each node as spreading origin (see Methods for details). To evaluate whether the structural centrality of coreness is an effective index to measure the spreading capability of nodes compared with degree, we calculate the imprecision function  and
and  proposed in Ref. 12. The imprecision function is defined as
proposed in Ref. 12. The imprecision function is defined as

where p is the fraction of network size  ,
,  and Meff(p) are the average spreading efficiencies of pN nodes with highest coreness kS (degree k) values and largest spreading efficiency, respectively. This function quantifies how close to the optimal spreading is the average spreading of the pN nodes with largest kS (k) values. The smaller the
and Meff(p) are the average spreading efficiencies of pN nodes with highest coreness kS (degree k) values and largest spreading efficiency, respectively. This function quantifies how close to the optimal spreading is the average spreading of the pN nodes with largest kS (k) values. The smaller the  value, the more accurate the kS (k) index is a measure to identify the most influential spreaders.
value, the more accurate the kS (k) index is a measure to identify the most influential spreaders.
The imprecision functions of nine real networks are shown in Fig. 1. Contrary to common belief, the coreness ks does not perform consistently well in all networks. We divide them into three groups. In Router, Emailcontact and AS networks, the kS imprecision is lower than the k based method. In Fig. 1 (a)–(c), the imprecision  is very low, under 0.06 in the demonstrated range of
is very low, under 0.06 in the demonstrated range of  and is much lower than
and is much lower than  . This means the coreness predicts the outcome of spreading more reliably than degree. However, the imprecision
. This means the coreness predicts the outcome of spreading more reliably than degree. However, the imprecision  for the next three networks (i.e., Email, CA-Hep and Hamster) is much higher than the imprecision
for the next three networks (i.e., Email, CA-Hep and Hamster) is much higher than the imprecision  . In Fig. 1 (d)–(f), the values of
. In Fig. 1 (d)–(f), the values of  is above 0.2 for all the three networks and is much higher than
is above 0.2 for all the three networks and is much higher than  . This is completely contrary to the case of the first three networks. As for the last three networks of PGP, Netsci and Astro networks, things are more complicated shown in Fig. 1 (g)–(i). In PGP, the kS method acts better than k when p < 0.015. Then there is a sudden rise in
. This is completely contrary to the case of the first three networks. As for the last three networks of PGP, Netsci and Astro networks, things are more complicated shown in Fig. 1 (g)–(i). In PGP, the kS method acts better than k when p < 0.015. Then there is a sudden rise in  and it becomes higher than the imprecision of degree. In Netsci, when p ≤ 0.026, the imprecision of kS is much lower than that of k. There is a fast rise of the
and it becomes higher than the imprecision of degree. In Netsci, when p ≤ 0.026, the imprecision of kS is much lower than that of k. There is a fast rise of the  at p = 0.027 and at p = 0.05 the kS imprecision exceeds k imprecision (see Fig. S1 in Supporting Information (SI) for large p plots). In Astro, the sudden rise of kS imprecision occurs at p = 0.015 and the value of
at p = 0.027 and at p = 0.05 the kS imprecision exceeds k imprecision (see Fig. S1 in Supporting Information (SI) for large p plots). In Astro, the sudden rise of kS imprecision occurs at p = 0.015 and the value of  goes up to around 0.18. This indicates a complex performance of coreness as a measure of spreading efficiency.
goes up to around 0.18. This indicates a complex performance of coreness as a measure of spreading efficiency.
The imprecision of kS and k as a function of p for nine real networks.
The kS imprecision (black squares) and k imprecision (red circles) are compared in each network. p is the proportion of nodes calculated, ranging from 0.003 to 0.029. See Fig. S1 for large p plots in SI.
Discovering true core and core-like group in real networks
To find out the reason for the distinct performance of coreness in predicting spreading efficiency is the origin of our research interest in this paper. In the following, we first explore the structural characteristics of the first two groups of networks and then explain the performance of coreness in the last three networks. As we know, the k-shell decomposition tends to assign many nodes with identical kS value, although their spreading capabilities may be different. When we calculate the imprecision function at a certain p, nodes with the same kS value are chosen randomly. This will cause some fluctuation in the kS imprecision curve (fraction of nodes in high shells is shown in the SI table S1). Given this fluctuation, we change to calculate

where  is the average spreading efficiency of the nodes with coreness
is the average spreading efficiency of the nodes with coreness  (nodes in kS-core) and Meff(kS) is the average spreading efficiency of n nodes with highest spreading efficiency, where n equals to the number of nodes with coreness
(nodes in kS-core) and Meff(kS) is the average spreading efficiency of n nodes with highest spreading efficiency, where n equals to the number of nodes with coreness  . To compare with k performance, we have
. To compare with k performance, we have

where Mk(kS) is the average spreading efficiency of n nodes with highest degree and n is as above. The imprecision of kS is supposed to be low if the nodes in high shells are efficient spreaders. The results are shown in Fig. 2. In the first three networks (a)–(c), the  is very low and much lower than the imprecision of degree εk(kS) for large kS, which means most of nodes in high shells (shells with large kS value) are efficient spreaders. In the next three networks (d)–(f), the
is very low and much lower than the imprecision of degree εk(kS) for large kS, which means most of nodes in high shells (shells with large kS value) are efficient spreaders. In the next three networks (d)–(f), the  is much higher than the εk(kS) for the innermost core (the shell with the maximum kS value) and the absolute value is even greater than 0.4, which means many nodes in the innermost core are not influential spreaders. From the perspective of dynamic spreading, we call the innermost core of the first three networks a true core and presumably call that of the other three networks a false core, or core-like group. This poor kS performance is obviously different from the fluctuation of imprecision caused by the resolution of kS index we mentioned above.
is much higher than the εk(kS) for the innermost core (the shell with the maximum kS value) and the absolute value is even greater than 0.4, which means many nodes in the innermost core are not influential spreaders. From the perspective of dynamic spreading, we call the innermost core of the first three networks a true core and presumably call that of the other three networks a false core, or core-like group. This poor kS performance is obviously different from the fluctuation of imprecision caused by the resolution of kS index we mentioned above.
The imprecision of kS and k as a function of kS for six real networks.
The kS imprecision (black squares) and k imprecision (red circles) are compared in each network. Each square represents the kS imprecision of nodes in kS-core and each circle represents the k imprecision of n highest degree nodes, where n equals to the number of nodes in kS-core. kS is an integer representing the shell index, ranging from the smallest kS value to the largest kS value in the network.
Exploring the cause of poor coreness imprecision from structural features
In order to find out the reason for the poor performances of coreness in the spreading process, we first look into the structural properties of the studied real networks. The features of the studied real networks are listed in Table 1. From Table 1, we see that the degree heterogeneity Hk of the first group is sufficiently larger than that of the second group. The degree heterogeneity is defined as Hk = ⟨k2⟩/⟨k⟩2 that evaluates the heterogeneity of degree sequence of a network, where ⟨k2⟩ and ⟨k⟩ are the second moment and first moment of degree respectively. In addition, the degree assortativity r of the first group is negative, which implies that nodes of large degrees are inclined to connecting to nodes of small degrees. As nodes in high shells always have large degrees and nodes in low shells (shells with small kS value) have small degrees, negative assortativity implies a good connection between high shell nodes and low shell nodes. On the contrary, the assortativity of the second group is positive or close to zero, which implies nodes of large degrees are inclined to connect to each other or connect randomly.
 ), epidemic threshold (λc), infection probability in the SIR spreading in the main text (λ)
), epidemic threshold (λc), infection probability in the SIR spreading in the main text (λ)To evaluate whether the difference of Hk and r between the two groups of networks results in the distinct performance of kS imprecision, we randomize the networks using two rewiring schemes (see Methods for details). In the first one, degrees of nodes are preserved after each single rewiring but correlations between the degrees of connected nodes are destroyed45. This keeps the Hk unchanged with the original real networks while other structural features destroyed. As is shown in Fig. S2 in SI, the coreness performance is greatly improved: the kS imprecision is very low and basically lower than or close to the k imprecision in degree-preserving randomized networks. This indicates that the relatively small Hk value of the second group of networks is not the reason of poor kS imprecision. Next, in the second scheme the rewiring preserves both the degrees of nodes and the joint degree-degree distribution of connected nodes, P(k, k′), so that the degree-degree correlations of all nodes are preserved. This keeps both Hk and r unchanged as the original real networks, but as shown in Fig. S3, the kS imprecision is very low and in general lower than the k imprecision. This implies that the small Hk value and positive r are not the cause of poor kS imprecision in the second groups of networks. So, what is the real origin of the poor coreness performance?
Analyzing the connectivity between shells
We move to explore the complex connectivity between shells of the studied real networks. Specifically, we consider the link patterns from each shell to its upper shells (shells with greater kS index), equal shell (the shell with equal kS index) and lower shells (shells with smaller kS index). We define the link strength of node i to its upper shells by the proportion function

where  is the number of links originating from node i to nodes in upper shells, ki is the total number of links of node i, that is the degree of node i. Large
is the number of links originating from node i to nodes in upper shells, ki is the total number of links of node i, that is the degree of node i. Large  indicates more links to the upper shells. Similarly, the link strengths of node i to its equal shells and lower shells are quantified by
indicates more links to the upper shells. Similarly, the link strengths of node i to its equal shells and lower shells are quantified by  ,
,  respectively. The link strengths of kS-shell to its upper (equal, lower) shells are the average link strength of nodes in that shell, that is
respectively. The link strengths of kS-shell to its upper (equal, lower) shells are the average link strength of nodes in that shell, that is

where  consists of nodes with coreness kS,
consists of nodes with coreness kS,  is the number of nodes in kS-shell and
is the number of nodes in kS-shell and  .
.
From Fig. 3 (a)–(c) for the first group of networks,  generally decreases with kS, this is because the number of nodes in upper shells decreases monotonously with the increase of kS.
generally decreases with kS, this is because the number of nodes in upper shells decreases monotonously with the increase of kS.  remains stable with the increase of kS.
remains stable with the increase of kS.  increases with kS and in the innermost core, this value goes up to 0.6 and above. For large kS,
increases with kS and in the innermost core, this value goes up to 0.6 and above. For large kS,  is much greater than
is much greater than  , which means a large proportion of links of high shells point to the their lower shells, obviously higher than the proportion of links within the shell. In Fig. 3 (d)–(f) for the second group,
, which means a large proportion of links of high shells point to the their lower shells, obviously higher than the proportion of links within the shell. In Fig. 3 (d)–(f) for the second group,  decreases with kS in Email and CA-Hep, although there is some fluctuation in Hamster.
decreases with kS in Email and CA-Hep, although there is some fluctuation in Hamster.  increases with kS. In the innermost core,
increases with kS. In the innermost core,  is close to 0.7 in Email, close to 1.0 in CA-Hep and close to 0.8 in Hamster, which is at least 50% larger than that of the first group.
is close to 0.7 in Email, close to 1.0 in CA-Hep and close to 0.8 in Hamster, which is at least 50% larger than that of the first group.  increases with kS at first and falls suddenly at some high shells. For these three networks,
increases with kS at first and falls suddenly at some high shells. For these three networks,  are under 0.4 in the innermost core and is much lower than
are under 0.4 in the innermost core and is much lower than  . This indicates that in the second group, the proportion of links from high shells pointing to lower shells is obviously lower than the proportion of links pointing within the shell. This is a sign of densely connected small group within the shell. The average clustering coefficient of nodes in high shells also reflects the overly dense connection in high shells in the second group (See Fig. S4 in SI). We plot the link strength of each shell to its lower shells, equal shell and upper shells in the degree-degree correlation preserving randomized networks in Fig. S5.
. This indicates that in the second group, the proportion of links from high shells pointing to lower shells is obviously lower than the proportion of links pointing within the shell. This is a sign of densely connected small group within the shell. The average clustering coefficient of nodes in high shells also reflects the overly dense connection in high shells in the second group (See Fig. S4 in SI). We plot the link strength of each shell to its lower shells, equal shell and upper shells in the degree-degree correlation preserving randomized networks in Fig. S5.  is promoted above 0.35 and is greater than
is promoted above 0.35 and is greater than  in most high shells in CA-Hep and Hamster, although in Email there is only a little promotion. The rewiring has changed the dense local link patterns of core-like groups, which is reflect by the increase of
in most high shells in CA-Hep and Hamster, although in Email there is only a little promotion. The rewiring has changed the dense local link patterns of core-like groups, which is reflect by the increase of  and decrease of
and decrease of  in high shells. The promoted kS performance in Fig. S3 is the result of enhanced link diversity.
in high shells. The promoted kS performance in Fig. S3 is the result of enhanced link diversity.
Next, we focus on the link pattern of the innermost core. The link strength  defines the ratio of links from a innermost core node i to the shell with index kS to the degree of node i.
defines the ratio of links from a innermost core node i to the shell with index kS to the degree of node i.  is the average link strength of nodes in the innermost core to the shell with index kS. Fig. 4 (a) shows the link strength of innermost core to all shells in the first three networks, which is a U-shape curve. In these networks, apart from the link ratio within the core, the largest link ratio points to the shell with most nodes, usually the 1-shell. A U-shape distribution of links from the core is a good feature of core-periphery structure, in which core nodes are well connected to other core nodes and to periphery nodes and periphery nodes are not well connected to each other46. In the second group, shown in Fig. 4 (b), the link of innermost core to all shells is different from the first group. Core nodes are very inclined to connecting to core nodes, with a link strength above 0.6. The second largest link ratio points to the adjacent shell of the innermost core, other than the shell with most nodes. When an epidemic spreading origins from core nodes, it is easy to spread throughout the core, but is relatively difficult to spread system wide. This locally connected phenomenon also implies the origin of core-like group (i. e., false core): nodes are densely connected within a small group which contributes much to the kS index of the nodes, but in the whole network these nodes are not best connected and not located in the most important position for spreading. The link pattern of the second innermost shell is shown in Fig. S6 in SI.
is the average link strength of nodes in the innermost core to the shell with index kS. Fig. 4 (a) shows the link strength of innermost core to all shells in the first three networks, which is a U-shape curve. In these networks, apart from the link ratio within the core, the largest link ratio points to the shell with most nodes, usually the 1-shell. A U-shape distribution of links from the core is a good feature of core-periphery structure, in which core nodes are well connected to other core nodes and to periphery nodes and periphery nodes are not well connected to each other46. In the second group, shown in Fig. 4 (b), the link of innermost core to all shells is different from the first group. Core nodes are very inclined to connecting to core nodes, with a link strength above 0.6. The second largest link ratio points to the adjacent shell of the innermost core, other than the shell with most nodes. When an epidemic spreading origins from core nodes, it is easy to spread throughout the core, but is relatively difficult to spread system wide. This locally connected phenomenon also implies the origin of core-like group (i. e., false core): nodes are densely connected within a small group which contributes much to the kS index of the nodes, but in the whole network these nodes are not best connected and not located in the most important position for spreading. The link pattern of the second innermost shell is shown in Fig. S6 in SI.
Link strength of the innermost core to each shell of the network.
(a) The link strength of the innermost core to each shell exhibits a U-shape curve in Router (black squares), Emailcontact (red circles) and AS (blue triangles) networks. (b) The link strength of the innermost core to each shell exhibit a slope in Email (black squares), CA-Hep (red circles) and Hamster (blue triangles) networks. kS ranges from the smallest kS value to the largest kS value in the network.
Identifying core-like groups from a structural perspective
The above analysis suggests an obvious structural difference between the two groups of networks: in the first one, the link pattern of innermost core to other shells exhibits a strong diversity, while in the second group, the link of innermost core is very localized within the shell. To quantify the link diversity of a shell with index kS, we define a link entropy as

where  is the average link strength of kS-shell to the
is the average link strength of kS-shell to the  -shell and L is the number of shells. The normalized factor lnL measures the entropy when links are uniformly distributed in all shells. This normalization makes the networks with different number of shells comparable. For the innermost core of each network, kS is set to the maximum kS value of the network. Entropy of cores of the real network and its degree-preserving randomized version are shown in Fig. 5. In Fig. 5 (a), true cores have a link entropy
-shell and L is the number of shells. The normalized factor lnL measures the entropy when links are uniformly distributed in all shells. This normalization makes the networks with different number of shells comparable. For the innermost core of each network, kS is set to the maximum kS value of the network. Entropy of cores of the real network and its degree-preserving randomized version are shown in Fig. 5. In Fig. 5 (a), true cores have a link entropy  higher than 0.6 while false cores have a link entropy lower than 0.5. But in the randomized network, Fig. 5 (b), all the cores have a link entropy
higher than 0.6 while false cores have a link entropy lower than 0.5. But in the randomized network, Fig. 5 (b), all the cores have a link entropy  higher than 0.6. Fig. S7 in SI shows the core entropy of degree-degree preserving randomized networks, which is above 0.5 for all studied networks. High entropy corresponds to a more uniform link pattern, where the core is well-connected to the other parts of the network. Low entropy corresponds to a localized link pattern, where the core is densely connected within the shell. In fact, these false cores are not located in the central position of the networks, reflecting by the relatively low spreading efficiency, e.g. the 11-shell in Email, 31-shell in CA-Hep and 24-shell in Hamster, as shown in Figs. S9 and S10 in SI.
higher than 0.6. Fig. S7 in SI shows the core entropy of degree-degree preserving randomized networks, which is above 0.5 for all studied networks. High entropy corresponds to a more uniform link pattern, where the core is well-connected to the other parts of the network. Low entropy corresponds to a localized link pattern, where the core is densely connected within the shell. In fact, these false cores are not located in the central position of the networks, reflecting by the relatively low spreading efficiency, e.g. the 11-shell in Email, 31-shell in CA-Hep and 24-shell in Hamster, as shown in Figs. S9 and S10 in SI.
Link entropy of the innermost core for the real networks and their randomized version.
(a) Link entropy of the innermost core for the real networks. (b) Link entropy of the innermost core for the degree-preserving randomized networks.  is the largest kS value in the network.
is the largest kS value in the network.  is the link entropy of the innermost core.
is the link entropy of the innermost core.
Locating the position of core-like groups throughout the networks
Uncovering locally connected core-like groups leads us to understand the imprecision of coreness centrality in the spreading process. We present the imprecision function of PGP, Netsci and Astro networks in Fig. 6 (a)–(c). The coreness performs very well at large kS values, but then rises suddenly at certain shells. Specifically speaking, in PGP at the 22-shell and above, the imprecision of kS is lower than that of k. However, there are sudden rises at the 21-shell, 16-shell and 15-shell. From the 10-shell, the kS imprecision is lower than k again. In Netsci, the kS imprecision is very low at the 8-shell. Then it rises up at the 7-shell and 6-shell. The kS imprecision is worse than that of k until the 4-shell. In Astro, the kS imprecision is low at the 51-shell and higher shells. Then it rises up at the 48-shell and then falls. The same phenomenon occurs at the 30-shell. The rise of kS imprecision implies that the corresponding shells are core-like groups. Locating them by a dynamic spreading method requires time-consuming simulations.
Locating core-like groups in real networks by link entropy.
(a)–(c) The imprecision of kS and k as a function of kS for three real networks. The kS imprecision(black squares) and k imprecision(red circles) are compared. Link entropy of shells in three networks.  is the link entropy of kS shell. Hollow red circles outline the shells which are densely connected core-like groups. These are 21-shell, 16-shell and 15-shell in PGP, 7-shell and 6-shell in Netsci and 48-shell and 30-shell in Astro. kS ranges from the smallest kS value to the largest kS value in the network.
is the link entropy of kS shell. Hollow red circles outline the shells which are densely connected core-like groups. These are 21-shell, 16-shell and 15-shell in PGP, 7-shell and 6-shell in Netsci and 48-shell and 30-shell in Astro. kS ranges from the smallest kS value to the largest kS value in the network.
According to Eq. (6), we calculate the link entropy of each shell in these networks. The shells outlined by hollow red circles in Fig. 6 (d)–(f) have relatively low entropy, which corresponds to locally connected core-like groups. This is reflected by the rise in kS imprecision shown in Fig. 6 (a)–(c). The link patterns of the core-like groups, shown in Fig. S8, are similar to that of false cores in the second group of Email, CA-Hep and Hamster: a dense connection within the shell. The only difference is that these core-like groups locate in the outer shells of the network other than the innermost shell. These core-like groups have an obvious low spreading efficiency than their adjacent shells, which is also confirmed in Fig. S9 and S10. From the above, we see the link entropy provides a fast way to locate the position of core-like groups in the network without running a large amount of spreading simulations, which is very important in identifying key spreaders and controlling the spreading dynamics on networks.
Discussion
Analyzing and profiling the structures of real networks is an important step in understanding and controlling dynamic behaviors on networks. The k-shell decomposition is a powerful tool to profile the hierarchical structures of networks. The inner core corresponds to the shells of large kS and the network periphery corresponds to the shells of small kS. This makes kS index an effective centrality measure to distinguish the spreading capability of nodes, which is validated in many real networks. However, there are circumstances where the k-shell decomposition is not able to identify influential spreaders, which leaves much space to explore. Here from the perspective of core's spreading efficiency, we discover that in some real networks, there exist core-like groups, which have high coreness but are in fact not located in the core of the network. By analyzing the k-core structure of real networks, we discover the distinct link patterns of true cores and core-like groups. For the true core of a network, it displays strong link diversity to other shells of the network, represented by a U-shape link curve. As for the core-like group, it has a very dense and local internal connection, represented as a slope-shape link curve. Based on the link pattern, we define a measure of link entropy to evaluate the link diversity of a shell to the remaining shells of the network. This provides a fast way to locate the core-like groups throughout the network from a structural perspective, which have a relatively low link entropy. We note that in Ref. 29 the authors calculated the entropy of each node to assess the heterogeneity of links. They use k-shell decomposition to assign each node a global feature and compute for each node an entropy as its global diversity, which is then combined with local feature to rank node influence. However, this entropy relates much to the degree of a node. A node with small degree has a limited number of layers it can connect to, even the connection is uniformly distributed. The node entropy is limited in the sense of statistics. Contrary to their work, we target to a group. We consider the link diversity of a shell, which consists of several nodes and these nodes have different degrees. By using the entropy for a shell, we can effectively locate the core-like groups, whose k-shell index is unable to reflect their global importance. This makes implication to the works that use the k-shell index in ranking node importance.
Uncovering these core-like groups is important in identifying key players and making control strategy for spreading dynamics. It is worth noticing that in the core-like groups, there may also exist some good spreaders. It implies that there should be new network analysis method which will effectively locate the nodes of different importance in core-like groups in the right hierarchical position. The new method should apply well in real networks with specific structures such as strong community structures.
Methods
The k-shell decomposition
The algorithm starts by removing all nodes with degree k = 1. After removing all nodes with k = 1, there may appear some nodes with only one link left. We should iteratively remove these nodes until there is no node left with k = 1. The removed nodes are assigned with an index kS = 1 and are considered in the 1-shell. In a similar way, nodes with degree k = 2 are iteratively removed and assigned an index kS = 2. This pruning process continues removing higher shells until all nodes are removed. As a result, each node is assigned a kS index and the network can be viewed as a hierarchical structure from the innermost shell to the periphery shell.
SIR Model
The Susceptible-Infected-Recovered (SIR) model is widely used for simulating the spreading process on networks. In the model, a node has three possible states: S (susceptible), I (infected) and R (recovered). An individual in the susceptible state does not have the disease yet but could catch it if they come into contact with someone who does. An individual in the infected state has the disease and can pass it to susceptible individuals. An individual in recovered state neither spread disease nor be infected by others. In the start of a spreading process, a single node is infected, considered as seed and all other nodes are in susceptible states. At each time step, there are two stages. In the first stage, susceptible individuals become infected with probability λ when they have contacted with an infected neighbor. In the second stage, infected nodes recover or die (change to R state) with probability μ. Here we set μ = 1 for generality. The spreading process stops when there is no infected node in the network. The proportion of recovered nodes defines the final infection population in a spreading process. We record the average infected population Mi originating at node i over 100 times of the spreading process to quantify the influence of node i in a SIR spreading.
As we take the final infected population to quantify the spreading efficiency of each node, the infection probability should be carefully considered. If it is too large, the effect of node position is not obvious and all nodes show almost identical spreading capabilities. If it is too small, the infection is very localized in the neighborhood, which cannot reflect the overall spreading influence of the nodes. So we first calculate the epidemic threshold of a network using the heterogeneous mean-filed method in Ref. 47. That is λc = ⟨k⟩/(⟨k2⟩ − ⟨k⟩). Then we chose an infection probability λ > λc14,37, which makes the final infected population above the critical point, M > 0 and reaches a finite but small fraction of the network size for most nodes as spreading origins, in the range of 1%–20%12. In fact, we plot the infected population of a shell as an average over nodes belong to the shell when infection probability is 1–5 times of the threshold λc, as well as the infected population when infection probability is around the chosen infected probability λ. We find that, the relative spreading efficiency of shells is almost the same under different infection probabilities (See >Fig. S9 and S10 in SI).
Rewiring Schemes
In the first rewiring scheme, we randomly choose two edges of the network and label the ends of the first edge as A and B and the ends of the second edge as C and D. Then we rewire the two edges, connecting end A and D as an edge and connecting end B and C as another edge. We avoid multiple edge and self-edge in the rewiring process. This rewiring preserves the degree sequence of the original real network but destroys the degree correlations. In the second rewiring scheme, we randomly choose an edge and test the degree of one end, record as k. A second edge with an end having degree k is then chosen. We rewire the two edges as before and ensure that the end connecting to a node of degree k still connects to a node of degree k after rewiring. This scheme preserves both the degree sequence and the degree-degree correlations as the original real network.
Data Sets
The real networks studied in the paper are: (1) Router (the router level topology of the Internet, collected by the Rocketfuel Project)48;(2) Email-contact (Email contacts at Computer Science Department of University college London)12; (3) AS (Internet at the autonomous system level)49; (4) Email (e-mail network of University at Rovira i Virgili, URV)50;(5) CA-Hep (Giant connected component of collaboration network of arxiv in high-energy physics theory)51; (6) Hamster (friendships and family links between users of the website hamsterster.com)52; (7) PGP (an encrypted communication network)53; (8) Netsci (collaboration network of network scientists)54; (9) Astro physics (collaboration network of astrophysics scientists)55.
References
Kempe, D., Kleinberg, J. & Tordos, . Maximizing the spread of influence through a social network. in Proc of the 9th ACM SIGKDD Int. Conf. on knowledge discovery and data mining (ACM, Washington, DC, USA, 2003), KDD 03 137–146 (2003).
Gallos, L. K., Liljeros, F., Argyrakis, P., Bunde, A. & Havlin, S. Improving immunization strategies. Phys. Rev. E 75 045101(R) (2007).
Lloyd-Smith, J. O., Schreiber, S. J., Kopp, P. E. & Getz, W. M. Superspreading and the effect of individual variation on disease emergence. Nature 438, 355–359 (2005).
Freeman, L. C. Centrality in social networks conceptual clarification. Social Networks 1, 215–239 (1978).
Freeman, L. C. A set of measures of centrality based upon betweenness. Sociometry 40, 35–41 (1977).
Sabidussi, G. The centrality index of a graph. Psychometrika 31, 581–603 (1966).
Bonacich, P. & Floyd, P. Eigenvector-like measures of centrality for asymmetric relations. Social Networks 23, 191–201 (2001).
Brin, S. & Page, L. The anatomy of a large-scale hypertextual Web search engine. Computer Networks 30, 107–117 (1998).
Kleinberg, J. M. Authoritative sources in a hyperlinked environment. J. ACM 46, 604–632 (1999).
Canright, G. S., & Engø-Monsen, K. Spreading on networks: a topographic view. Complexus 3, 131–146 (2006).
Lü, L. Y., Zhang, Y. C., Yeung, C. H. & Zhou, T. Leaders in social networks, the delicious Case. PLoS ONE 6, e21202 (2011).
Kitsak, M. et al. Identification of influential spreaders in complex networks. Nat. Phys. 6, 888–893 (2010).
Chen, D. B., Lü, L. Y., Shang, M. S., Zhang, Y. C. & Zhou, T. Identifying influential nodes in complex networks. Physica A 391, 1777–1787 (2012).
Macdonald, B., Shakarian, P., Howard, N. & Moores, G. Spreaders in the Network SIR mode: an empirical study. arXiv e-print 1208.4269v1 (2012).
Borge-Holthoefer, J., Rivero, A. & Moreno, Y. Locating privileged spreaders on an online social networks. Phys. Rev. E 85, 066123 (2012).
Tanaka, G., Morino, K. & Aihara, K. Dynamical robustness in complex networks: the crucial role of low-degree nodes. Sci. Rep. 2, 232 (2012).
Bolobás, B. Graph Theory and Combinatorics: Proc. Cambridge Combinatorial Conf. in honor of P. Erdös (Academic Press, NY, 1984).
Batagelj, V. & Zaversnik, M. An O(m) algorithm for cores decomposition of networks. arXiv e-print cs/0310049 (2003).
Alvarez-Hamelin, J. I., Asta, L. D., Barrat, A. & Vespignani, A. k-core decomposition: a tool for the visualization of large scale networks. arXiv e-print cs/0504107v2 (2005).
Carmi, S., Havlin, S., Kirkpatrick, S., Shavitt, Y. & Shir, E. A model of Internet topology using k-shell decomposition. Proc. Natl. Acad. Sci. USA 104, 11150–11154 (2007).
Dorogovtsev, S. N., Goltsev, A. V. & Mendes, J. F. F. k-core organization of complex networks. Phys. Rev. Lett. 96, 040601 (2006).
Alvarez-Hamelin, J. I., Dall'Asta, L., Barrat, A. & Vespignani, A. K-core decomposition of Internet graphs: hierarchies, self-similarity and measurement biases. Networks and Hetero Media 3, 371–393 (2008).
Colomer-de-Simón, P., Serrano, M. ., Beiró, M. G., Alvarez-Hamelin, J. I. & Boguñá, M. Deciphering the global organization of clustering in real complex networks. Sci. Rep. 3, 2517 (2013).
Holme, P. Core-periphery organization of complex networks. Phys. Rev. E 72, 046111 (2005).
Zhang, G. Q., Zhang, G. Q., Yang, Q. F., Cheng, S. Q. & Zhou, T. Evolution of the Internet and its cores. New J. Phys. 10, 123027 (2008).
Hébert-Dufresne, L., Allard, A., Young, J. & Dubé, L. J. Random networks with arbitrary k-core structure. arXiv e-print 1308.6537v1 (2013).
Castellano, C. & Pastor-Satorras, R. Competing activation mechanisms in epidemics on networks. Sci. Rep. 2, 371 (2012).
Pei, S. & Makse, H. A. Spreading dynamics in complex networks. J. Stat. Mech. 12, 12002 (2013).
Fu, Y.-H., Huang, C.-Y. & Sun, C.-T. Identifying super-spreader nodes in complex networks. Mathematical Problems in Engineering 2014, 675713 (2014).
Garas, A., Argyrakis, P., Rozenblat, C., Tomassini, M. & Havlin, S. Worldwide spreading of economic crisis. New J. Phys. 12, 113043 (2010).
Borge-Holthoefer, J. & Moreno, Y. Absence of influential spreaders in rumor dynamics. Phys. Rev. E 85, 026116 (2012).
Reppas, A. I. & Lawyer, G. Low k-shells identify bridge elements critical to disease flow in small-world networks. AIP Conf. Proc. 1479, 1426–1429 (2012).
Zeng, A. & Zhang, C. J. Ranking spreaders by decomposing complex networks. Phys. Lett. A 377, 1031–1035 (2013).
Ren, Z. M., Zeng, A., Chen, D. B., Liao, H. & Liu, J. G. Iterative resource allocation for ranking spreaders in complex networks. Europhys. Lett. 106, 48005 (2014).
Corominas-Murtra, B., Fuchs, B. & Thurner, S. Detection of the elite structure in a virtual multiplex social systems by means of a generalized k-core. arXiv e-print 1309.6740 (2013).
Liu, J. G., Ren, Z. M. & Guo, Q. Ranking the spreading influence in complex networks. Physica A 392, 4154–4159 (2013).
Bae, J. & Kim, S. Identifying and ranking influential spreaders in complex networks by neighborhood coreness. Physica A 395, 549–559 (2014).
Garas, A., Schweitzer, F. & Havlin, S. A k-shell decomposition method for weighted networks. New J. of Phys. 14, 083030 (2012).
Eidsaa, M. & Almaas, E. S-core network decomposition: A generalization of k-core analysis to weighted networks. Phys. Rev. E 88, 062819 (2013).
Miorandi, D. & Pellegrini, F. D. K-shell decomposition for dynamic complex networks. Ad Hoc and Wireless Networks(WiOpt), 2010 Proc. of the 8th Int. Symp., IEEE 499–507 (2010).
Azimi-Tafreshi, N., Gómex-Gardeñes, J. & Dorogovtsev, S. N. k-core percolation on multiplex networks. arXiv e-print 1405.1336v1 (2014).
Pei, S., Muchnik, L., Andrade, J. S., Zheng, Z. M. & Makse, H. A. Searching for superspreaders of information in real-world social media. Sci. Rep. 4, 5547 (2014).
Anderson, R. M. & May, R. M. Infectious diseases in humans (Oxford University Press, Oxford, 1991).
Moreno, Y., Pastor-Satorras, R. & Vespignani, A. Epidemic outbreaks in complex heterogeneous networks. Eur. Phys. J. B 26, 521–529 (2002).
Maslov, S. & Sneppen, K. Specificity and stability in topology of protein networks. Science 296, 910–913 (2002).
Rombach, M. P., Porter, M. A., Fowler, J. H. & Mucha, P. J. Core-Periphery structure in networks. SIAM J. Appl. Math. 74, 167–190 (2014).
Castellano, C. & Pastor-Satorras, R. Thresholds for epidemic spreading in networks. Phys. Rev. Lett. 105, 218701 (2010).
Spring, N., Mahajan, R., Wetherall, D. & Anderson, T. Measuring ISP topologies with Rocketfuel. IEEE/ACM Trans. Networking 12, 2–16 (2004).
Newman, M. E. J. Network data. (2006) Available at: http://www-personal.umich.edu/%7Emejn/netdata. (Accessed: 12/12/2012)
Guimera, R., Danon, L., Diaz-Guilera, A., Giralt, F. & Arenas, A. Self-similar community structure in a network of human interactions. Phys. Rev. E 68, 065103(R) (2003).
Leskovec, J., Kleinberg, J. & Faloutsos, C. Graph Evolution: Densification and Shrinking Diameters. ACM Trans. on Knowledge Discovery from Data (ACM TKDD) 1, 1 (2007).
Kunegis, J. Hamsterster full network dataset - KONECT. (2014) Available at: http://konect.uni-koblenz.de/networks/petster-hamster. (Accessed: 01/03/2014)
Boguñá, M., Pastor-Satorras, R., Diaz-Guilera, A. & Arenas, A. Models of social networks based on social distance attachment. Phys. Rev. E 70, 056122 (2004).
Newman, M. E. J. Finding community structure in networks using the eigenvectors of matrices. Phys. Rev. E 74, 036104 (2006).
Newman, M. E. J. The structure of scientific collaboration networks. Proc. Natl. Acad. Sci. USA 98, 404–409 (2001).
Acknowledgements
This work was partially supported by the National Natural Science Foundation of China (Grant Nos. 11105025, 91324002, 61433014), Scientific Research Starting Project of Southwest Petroleum University (No. 2014QHZ024) and Youth Foundation of Southwest Petroleum University (Grant No. 285). Y. Do was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education, Science and Technology (NRF-2013R1A1A2010067).
Author information
Authors and Affiliations
Contributions
Y.L., M.T. and T.Z. devised the research project. Y.L. performed numerical simulations. Y.L., M.T. and Y.H.D. analyzed the results. Y.L., M.T., T.Z. and Y.H.D. wrote the paper.
Ethics declarations
Competing interests
The authors declare no competing financial interests.
Electronic supplementary material
Supplementary Information
Supporting Information
Rights and permissions
This work is licensed under a Creative Commons Attribution 4.0 International License. The images or other third party material in this article are included in the article's Creative Commons license, unless indicated otherwise in the credit line; if the material is not included under the Creative Commons license, users will need to obtain permission from the license holder in order to reproduce the material. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/
About this article
Cite this article
Liu, Y., Tang, M., Zhou, T. et al. Core-like groups result in invalidation of identifying super-spreader by k-shell decomposition. Sci Rep 5, 9602 (2015). https://doi.org/10.1038/srep09602
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/srep09602
This article is cited by
-
Identifying influential nodes in complex networks using a gravity model based on the H-index method
Scientific Reports (2023)
-
Identifying spreading influence nodes for social networks
Frontiers of Engineering Management (2022)
-
Best influential spreaders identification using network global structural properties
Scientific Reports (2021)
-
The relative importance of structure and dynamics on node influence in reversible spreading processes
Frontiers of Physics (2021)
-
Top influencers can be identified universally by combining classical centralities
Scientific Reports (2020)
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.

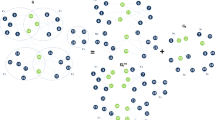



 (black squares), equal shell
(black squares), equal shell  (red circles) and upper shells
(red circles) and upper shells  (blue triangles) are represented. kS ranges from the smallest kS value to the largest kS value in the network.
(blue triangles) are represented. kS ranges from the smallest kS value to the largest kS value in the network.

