Abstract
In this paper, a novel image encryption algorithm based on the Once Forward Long Short Term Memory Structure (OF-LSTMS) and the Two-Dimensional Coupled Map Lattice (2DCML) fractional-order chaotic system is proposed. The original image is divided into several image blocks, each of which is input into the OF-LSTMS as a pixel sub-sequence. According to the chaotic sequences generated by the 2DCML fractional-order chaotic system, the parameters of the input gate, output gate and memory unit of the OF-LSTMS are initialized, and the pixel positions are changed at the same time of changing the pixel values, achieving the synchronization of permutation and diffusion operations, which greatly improves the efficiency of image encryption and reduces the time consumption. In addition the 2DCML fractional-order chaotic system has better chaotic ergodicity and the values of chaotic sequences are larger than the traditional chaotic system. Therefore, it is very suitable to image encryption. Many simulation results show that the proposed scheme has higher security and efficiency comparing with previous schemes.
Similar content being viewed by others
Introduction
With the rapid development in digital connectivity, the shared information like audio, video, image is widely spread on the network, and the security of data information is facing serious challenges. So, data security technologies like data encryption, digital signature have been extensively studied to protect data information from potential threats. Image as an important carrier of information plays a vital role in communication due to its vivid and intuitive characteristics. Therefore, the research of image encryption technology is particularly important1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43.
Permutation and diffusion are usually two separate stages in the image encryption12,16,17,18,19,20,21,22,23,24,28. In reference18 the multi-level chaotic map formed by three levels was applied to permutation and diffusion, so as to achieve good image encryption effect. Mondal et al.19 designed an image encryption algorithm based on pixel level scrambling in the confusion layer and bit XOR operation in the diffusion layer. At the same time, they also proposed a new two-dimensional cross chaotic map. Gopalakrishnan et al.22 applied the two-dimensional hyperchaotic map in the permutation stage, and the hybrid chaotic map is applied in the diffusion stage, thus the image encryption process is completed. However, due to the separation of image permutation and diffusion in traditional algorithms, the amount of data needed to be processed in the image increases significantly, which limits the efficiency of image encryption. In recent years, some researches on image encryption based on chaotic sequences and network structures have been proposed27, 2833,44. Maddodi et al.27 generated a pseudo-random sequence generator with neural network and chaotic sequence, and then combined DNA rules for image encryption. In order to enhance the security of the financial system, Pan et al.28 proposed an encryption scheme which combines the hybrid chaotic system and the deep network structure to realize the dynamic image encryption technology. The above algorithms make a new attempt on image encryption, but the encryption efficiency is not high, such as the histogram effect is not ideal, the information entropy is not high, and the encryption time is long etc.
The Long Short-Term Memory (LSTM) network structure has good application effect in many fields, especially in the field of artificial intelligence such as natural language processing, image segmentation, image classification, etc. At the same time, LSTM network structure is a kind of extended structure of Recurrent Neural Network (RNN), which can effectively deal with the problem of sequence transformation. In the process of image processing, the original image is often transformed into a series of pixel sequences. Therefore, image processing can be regarded as a sequence transformation process, which is effectively processed by LSTM29,30,31,32,45,46,47,48,49,50. Gregor et al.45 proposed an image generation network based on the LSTM structure in the image generation task, which can effectively generate the image corresponding to the input image in an iterative way. In the task of brain image segmentation, Marijn et al.46 introduced a multi-dimensional LSTM network based on pixel by pixel pyramid operation. Zhou et al.47 proposed a spectral space-based LSTM network in the hyperspectral image classification task, which has good performance by inputting the local pixel block composed of core pixels determined by PCA into LSTM. Aslan et al.48 applied three different LSTM in the ultrasonic image analysis task to construct the tracker system, which achieved high accuracy in the test. LSTM can process images in sequence mode, and most of the LSTM used are input and output of sequence (with equal length) and synchronous. Image encryption is an important research field of image processing. In the process of image encryption, the original image can be transformed from top to bottom, from left to right, and then the pixel sequence can be input into the structure for a series of encryption algorithm operations. Therefore, the image encryption/decryption process can be regarded as a series of encoding/decoding processes. However, the image encryption algorithm requires reversibility, and the matrix multiplication of traditional LSTM structure can not meet this requirement. Therefore, this paper takes the network structure of LSTM as the basic framework, and uses XOR operation to replace the traditional LSTM calculation method. At the same time, the parameters in this algorithm are derived from chaotic sequences, which do not need to be changed. That is to say, after entering the algorithm, the encrypted image can be obtained after only one forward propagation. Therefore, the structure of the algorithm is called as the Once Forward Long Short Term Memory Structure (OF-LSTMS). The OF-LSTMS can not only change the pixel value and the pixel position information at the same time, but also retain the memory ability of the structure to the previous information. It can effectively resist malicious attacks and is more suitable for image encryption. The simulation results show that the encryption algorithm has the advantages of high information entropy, ideal histogram and low time cost, especially for large-scale images.
Chaos system has a series of characteristics such as good ergodicity, sensitivity to initial state and control parameters. These characteristics are highly compatible with the characteristics of cryptosystem. In 1989, Matthews34 proposed a generalized logistic map, and encrypted the text data by pseudo-random sequence generated by the map. This is the first time that chaos system is applied in the field of encryption. In 1998, Fridrich35 used discrete chaotic mapping to scramble the image pixels, and proposed an image encryption system based on chaos. During the last three decades, there have been significant interests in the image encryption algorithm based on chaos system1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,18,19,20,21,22,23,25,28,34,35,36,37,38,39,40,41,42,43,51,52. Zhang et al.52 analyzed the dynamic characteristics of the fractional-order chaotic system in detail and designed an efficient image encryption algorithm. Experimental results show that the chaotic sequences generated by the system are very suitable for image encryption. Tsafack et al.11 generated the chaotic behavior through a circuit network, and proposed an image encryption protocol based on chaotic sequence which has a significant effect on network image encryption. El-Latif et al.1 applied chaotic systems to design a new cryptosystem, each of which generates periodic cycles. In addition, quantum random walks were applied in the design of cryptosystem, which solves the periodicity problem in traditional cryptosystem. Wang et al.25 obtained a new spatiotemporal chaos system by applying three different maps in CML mapping, and scrambling was carried out at the bit level of the image. But either the fractional-order chaotic system or the CML system have periodic windows in the bifurcation diagrams which implies parameters can only generate local chaotic behavior. The parameters should be selected carefully for image encryption. In our paper, we mainly apply the 2DCML fractional-order chaotic system to the encryption process. In comparisons with the traditional logistic map and the fractional-order chaotic system, the 2DCML fractional-order chaotic system contains good features as larger key space, better chaotic ergodicity, less periodic windows in bifurcation diagrams, the larger range of parameters for chaotic behaviors. In addition, the value of chaotic sequences that generated by the 2DCML fractional-order chaotic system are larger than the traditional 2DCML system with the logistic mapping. Therefore, the proposed system is very suitable to image encryption.
The security of encryption algorithm is an important indicator to test whether the algorithm is reliable and efficient. Some studies show that chaotic encryption system will have security problems21,36,37,38,39. Xie et al.37 analyzed the steps of Fridrich’s algorithm with mathematical language, found out some defects in the application of Solak’s attack method, and provided some optimization basis for the attack scheme of Fridrich’s algorithm and derivative algorithm. Akhavan et al.38 pointed out that Eslami’s algorithm has security problems such as low resistance to selection attacks and the key space is not ideal. At the same time, the strategy of optimizing the image encryption algorithm was given. When improving the chaotic encryption system of Baptista-type cryptosystem, Chen et al.36 proposed that in order to ensure the security of encryption, it is necessary to ensure that the system does not reveal the chaotic state information during iteration, and the key space needs to be large enough to resist the attack of direct exhaustive search of the key. Wheeler et al.39 pointed out that there may be problems such as short period and strong dependence on specific values when using computer to realize chaotic mapping. In our paper the secret keys of the proposed algorithm include five parameters which the total key space is more than 2425, and it can resist exhaustive search attacks. The chaotic sequences generated by the 2DCML fractional-order chaotic system depend on the input plain image and the chaotic sequence will change completely if the input image changes, which provides the algorithm has stronger anti chosen plain text attack ability. In addition, we select special images (“White” and “Black”), binary image and color image to encrypt and simulation results show that the encryption effect is better. We have also completed tests of resisting noise attack and data loss, and the results show that the main information of images are still retained, so it shows that the algorithm has good ability to resist attacks. As described in “The new features of the proposed chaotic system in dynamical behaviors” section the 2DCML fractional-order chaotic system has better chaotic ergodicity in dynamical behaviors and both the parameter range and the values of chaotic sequences are larger. Moreover, the application of OF-LSTMS increases the complexity of the algorithm, so the encryption scheme will not leak the information of chaotic sequences. Therefore, our encryption algorithm has better security. Implementation speed is another important indicator to test whether the encryption system is efficient. In the process of image encryption, through the combination of chaotic sequences and OF-LSTMS, the proposed algorithm can change the pixel position while changing the pixel value, that is, permutation and diffusion are carried out at the same time, so the time consumption is less and the proposed encryption algorithm is efficient.
The rest of this paper is organized as follows. In “The application of OF-LSTMS in the proposed algorithm” and “The 2DCML fractional-order chaotic system” sections the OF-LSTMS and the 2DCML fractional-order chaotic system are presented respectively. The proposed image encryption and decryption scheme are described in “The proposed image encryption and decryption algorithm” section. Simulation results and performance analyses are reported in “Performance analyses” section.
The application of OF-LSTMS in the proposed algorithm
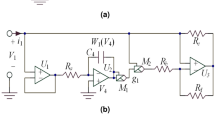
LSTM structure is a chain structure with recurrent neural network module. It adopts matrix multiplication calculation method and gradient update parameter training method. LSTM structure consists of four parts: memory unit, forgetting gate, input gate and output gate29,46,47,48,49,50. Image encryption algorithm requires reversibility and does not need to learn features of the sequence, so it is necessary to modify the structure of LSTM. Based on the structure of LSTM, we propose the Once Forward Long Short Term Memory Structure (OF-LSTMS), which uses XOR operation instead of traditional matrix operation. The OF-LSTMS can realize that the encrypted image be obtained after only one forward propagation after original image entering the algorithm. The OF-LSTMS is as shown in Fig. 1.
The operation used by the Neural Network (NN) structure of the traditional LSTM is matrix multiplication (MM), but it is not applicable in the image encryption task. MM cannot make the sum items (after being activated by MOD function) included in the output neurons be accurately restored to the input neurons during the decryption process, so the operation used by the NN structure of OF-LSTMS is XOR. The blue box NN in Fig. 1 (the part of The OF-LSTMS) shows the formal representation of NN structure and Fig. 2 shows the details of the XOR operation used by the NN structure of OF-LSTMS. As shown in Fig. 2, there are four original pixels, each of which contains 8-bit binary values. These pixels are divided into four groups of binary values, and XOR operation is performed with the same four sets of binary values (the values are from chaotic sequences). This operation process is called segmentation as shown in Fig. 2 (The part on the left which marked by green). In addition, the four groups of binary values in each rectangle in Fig. 2 come from the binary values of four different original pixels, which are finally calculated and then converted to decimal values. This operation process is called recombination as shown in Fig. 2 (The part on the right which marked by yellow).
The length of binary value used for recombination is 8 in order to ensure that no information is lost in the process of converting binary value to decimal value. Therefore, the number of neurons in the process of segmentation and recombination of the OF-LSTMS can only be multiple of 2, and the upper limit is 8. If the neurons and parameters are selected as 2 groups, 4 groups or 8 groups, it is necessary to select 2, 4 or 8 neurons as the neurons to enter the OF-LSTMS . We choose the number of neurons as 4 for balance the quality and efficiency of encryption.
In this paper, the mathematical formulas are shown in Eq. (1).
where \(bitDic(X_{t} )\) is a multivalued function that the binaries of the input \(X_{t}\) divide into 4 parts and each part has 2 bits. \(NN(X_{t} ,CS_{t}^{X} )\) is a mathematical formula for the NN structure of the OF-LSTMS that contains 4 neurons. \(CS_{t}^{X}\)(from the chaotic sequences) is the parameters of the corresponding inputs at the current moment. \(bitCon(x_{1}^{bit} ,x_{2}^{bit} ,x_{3}^{bit} ,x_{4}^{bit} )\) is a function that combines 4 binaries of 2 bits into 8 bits and converts them to decimals. \(X_{t}^{NN}\) is the outputs of the NN structure of the OF-LSTMS.
The function of the forgetting gate in the traditional LSTM is to determine which information inherited from the cell body at the previous moment to discard, which is determined by the input sequence at the current moment and the output at the previous moment. But it is not applicable in the image encryption task. The essence of the image encryption task is to scramble the image, and the less original image information contains in the encrypted image, the better the encryption effect. Therefore, the OF-LSTMS proposed in this paper designs the forgetting gate to the increasing gate, as shown in blue box A in Fig. 3. The cell body information at the current moment is obtained by accumulating with Eq. (2) the inputs’ parameters at the previous moment and the information inherited from the cell body at the previous moment chaotically.
where \(C_{t - 1}\) is the information inherited from the cell body at the previous moment. \(CS_{t - 1}^{X}\) is the inputs’ parameter at the previous moment. \(C_{t}^{temp}\) is the information at the current moment after the increasing gate.
The function of the input gate in the traditional LSTM is to determine which information is added to the information at the current moment after the increasing gate, and it uses the multiplication operation. But the input gate in the OF-LSTMS uses add operation, which is due to the limitations in the image encryption. The input gate in the OF-LSTMS is shown in blue box I in Fig. 3 and can be represented by
where \(\tilde{C}_{t}^{temp}\) is the information to be added to the information of the cell body at the current moment after the input gate.
The operation used in the OF-LSTMS is different from the operation used in traditional LSTM, and it uses XOR. As shown in blue box C in Fig. 3, it can be represented by
where \(C_{t}\) is the information of the memory unit in the cell body that will be used to encrypt the input sequence at the current moment.
The function of the output gate in the OF-LSTMS is to use the information in the cell body and additional chaotic sequences to encrypt the input sequence. It is shown in blue box O in Fig. 3, and can be represented by
where \(CS_{t}^{C}\) and \(CS_{t}^{O}\) (from the chaotic sequence) are the chaotically information added to the information in the cell body and input sequence at the current moment. \(C_{t}^{O}\) and \(X_{t}^{temp}\) are the information after \(C_{t}\) and \(X_{t}^{NN}\) are chaotic. \(O_{t}\) are the output, which are the sum of \(C_{t}^{O}\) and \(X_{t}^{temp}\).
In this algorithm, the original image sequence enters into the OF-LSTMS in order to operate with different chaotic sequences. The memory information Ct and the encrypted pixel value Ot can be obtained at the same time. According to the memory information Ct, the new position of the encrypted pixel can be obtained, that is, the encrypted pixel position and pixel value are determined at the same time. The synchronization of permutation and diffusion can improve the efficiency of encryption.
The 2DCML fractional-order chaotic system
The proposed chaotic system
Comparison with the traditional logistic map, the fractional-order logistic map contains larger key space and more parameters. Zhang et al.52 exhibited the features of the fractional-order chaotic system in dynamical behaviors. The following iteration equation is obtained52:
The parameters α, μ, r and the initial values x0 of the fractional-order logistic system can be designed the secret keys.
Based on the fractional-order logistic map, the proposed system coupled by the neighborhood links of the 2DCML system53 as follows:
where i , j are the lattices (\(1 \le i,j \le L\)) , ε is the coupling parameter (\(0 \le \varepsilon \le 1\)), n is the time index (n = 1,2,3, …) and \(f(x)\) is the fractional-order logistic map with the iteration equation is obtained as Eq. (6).
The new features of the proposed chaotic system in dynamical behaviors
To qualify the new features of the proposed system in dynamical behaviors mathematically, the bifurcation diagrams, the Lyapunov exponents, the space-amplitude diagrams and the patterns diagrams are widely analyzed theoretically in this section.
In the proposed system, the bifurcation diagrams are shown in Fig. 4c. In Fig. 4a the parameter μ in the traditional logistic map is (3.57, 4). In Fig. 4b the parameter μ in the fractional-order logistic differential map breaks the range of \(\mu \in (3.57,4)\) and the numerical range of chaotic sequence xn also breaks the range of (0,1). While an important phenomenon in Fig. 4c is that the proposed system not only retains the advantages of the fractional-order logistic map, but also its periodic windows are reduced substantially compared with the Fig. 4a,b and the gaps between bifurcation points vary closer. Due to the neighborhood coupling leading the instability of the possible periods of orbits, the times of period doubling bifurcations is misled and unobvious. Therefore, both the parameter range and the values of chaotic sequences of the proposed system are larger than the traditional logistic mapping and the fractional-order chaotic logistic system. In our encryption algorithm, the proposed chaotic system is selected to generate chaotic sequences, and the parameters are selected as secret keys.
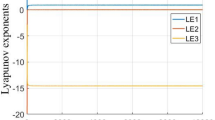
Any system holding chaotic behavior presented at least one positive Lyapunov exponent. In Fig. 5, comparing with the Lyapunov exponents of the fractional-order chaotic logistic system and the traditional logistic maps system, the positive interval of Lyapunov exponents of the proposed chaotic system is far greater than that of the former two systems. Therefore, the proposed chaotic system has strong chaotic characteristics and can generate better chaotic sequences. It is more suitable for encryption algorithm.
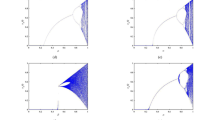
Because the fractional-order logistic map contains larger key space and more parameters comparing with the traditional logistic map, the proposed system contains more universality of chaos in space than the 2DCML system with the same parameter ε, which is shown in the space-amplitude plots as Fig. 6. In addition, the snapshot patterns shown in Fig. 7 indicate that the proposed system presents more complex chaotic resolutions than the 2DCML system. For example, Fig. 7f indicates that the same parameter ε which lead the proposed system in fully developed turbulence pattern, can only lead the 2DCML system in defect turbulence pattern which is shown in Fig. 7e.
The space-amplitude plots when times = 1000. (a) the 2DCML system (ε = 0.1), (b) the proposed system (ε = 0.1), (c) the 2DCML system (ε = 0.3), (d) the proposed system (ε = 0.3), (e) the 2DCML system (ε = 0.5), (f) the proposed system (ε = 0.5), (g) the 2DCML system (ε = 0.7), (h) the proposed system (ε = 0.7).
Snapshot patterns when times = 1000. (a) the 2DCML system (ε = 0.1), (b) the proposed system (ε = 0.1), (c) the 2DCML system (ε = 0.3), (d) the proposed system (ε = 0.3), (e) the 2DCML system (ε = 0.5), (f) the proposed system (ε = 0.5), (g) the 2DCML system (ε = 0.7), (h) the proposed system (ε = 0.7).
The proposed image encryption and decryption algorithm
Without loss of generality, the images are employed to present the encryption scheme for simplicity. The corresponding encryption algorithm and decryption algorithm can be presented as follows.
Encryption algorithm
- Step 1.:
-
Generate the key sequence K and the initial values \(\alpha ^{\prime}\), \(\mu ^{\prime}\), \(x^{\prime}\), \(r^{\prime}\) and \(\varepsilon ^{\prime}\) of the proposed system. The proposed algorithm utilizes a 160-bit secret key K, which is generated by the hash algorithm MD2. For source images, even if only one bit is changed, its hash value will change completely. By dividing the 160-bit secret key into 16-bit blocks (Ki), and the new initial values can be obtained by the following formulas:
$$\alpha ^{\prime} = \alpha + (bin2dec(k_{1} \oplus k_{2} )) \times 10^{ - 6} ,$$$$\mu ^{\prime} = \mu + (bin2dec(k_{3} \oplus k_{4} )) \times 10^{ - 6} ,$$$$x^{\prime} = x_{0} + (bin2dec(k_{5} \oplus k_{6} ) \times 10^{ - 6} ,$$$$r^{\prime} = r + (bin2dec(k_{7} \oplus k_{8} )) \times 10^{ - 6} ,$$$$\varepsilon ^{\prime} = \varepsilon + (bin2dec(k_{{9}} \oplus k_{{{10}}} )) \times 10^{ - 6}$$where \(\alpha\), \(\mu\), \(x_{{0}}\), \(r\) and \(\varepsilon\) are the initial given values.
- Step 2.:
-
The chaotic sequences are iterated according to Eq. (7), and the chaotic sequences used in the OF-LSTMS are determined.
- Step 3.:
-
The original image is transformed into a sequence, and each 4 pixels value is regarded as a subsequence.
- Step 4.:
-
The subsequences are encrypted in the OF-LSTMS according to “The application of OF-LSTMS in the proposed algorithm” section. Assume the size of the encrypted image is 512 × 512 and the image is divided into 65,536 pixel sequences with 4 pixels as a group. Then the shape of input data into the OF-LSTMS is [1, 65,536, 4].
Finally, the ciphered image is obtained. The encryption process is shown as Fig. 8.
Decryption algorithm
The decryption process is contrary to the encryption process. Using the secret keys provided by the sender, the receivers decrypt the cipher image according to the contrary operations of the encryption algorithm. The decryption process is shown as Fig. 9.
In the experiments, the test images are the “Boat.512 (512 × 512)” , “image 3.2.25 (1024 × 1024) ” and color image “image 4.2.03 (512 × 512)” from the USC-SIPI image database. We also chose two special images “White (512 × 512)”, “Black (512 × 512)” and binary image “Binary_boat.512 (512 × 512)” to be encrypted. Figures 10 and 11 show the encryption and decryption of images for one round.
Encryption and decryption of images. (a) Original image of Boat.512, (b) original image of image 3.2.25, (c) original image of White, (d) original image of Black, (e) encrypted image of Boat.512, (f) encrypted image of image 3.2.25, (g) encrypted image of White, (h) encrypted image of Black, (i) decrypted image of Boat.512. (j) decrypted image of image 3.2.25, (k) decrypted image of White, (l) decrypted image of Black.
Performance analyses
In order to evaluate the security of the proposed encryption algorithm, we undertake a series of statistical analysis on the encryption and decryption results, and show the analysis results in detail in this section.
Key space
Only if the key space is large enough, it can resist violent attacks. The secret keys include decimal parameters α, μ, r, ε and the initial value x0. The total key space is 1080 if the accuracy of the computer is 1016. In the proposed encryption algorithm, because the total key space is more than 2425 that the key space can satisfy the security requirements.
Key sensitivity
The characteristic of chaotic system is that the small change of initial value will lead to completely different chaotic sequences. We modify one of the parameter values, while the others remain unchanged. Simulation and analysis show that small changes in the key will lead to significant changes in the output, so the algorithm is very sensitive to the key. Figure 12 shows the results of the corresponding μ, α, r, x0 and ε tests, respectively.
Keys sensitivity. (a) Original image of Boat.512, (b) encrypted image of Boat.512 using original μ = 9, α = 0.85, r = 0.25, x0 = 0.30565487923280 and ε = 0.39, (c) encrypted image of Boat.512 using changed μ = 9.0000000001, (d) difference between (b) and (c). (e) encrypted image of Boat.512 using changed α = 0.8500000001, (f) difference between (b) and (e). (g) encrypted image of Boat.512 using changed r = 0.2500000001, (h) difference between (b) and (g). (i) encrypted image of Boat.512 using changed x0 = 0.30565487923281, (j) Difference between (b) and (i), (k) encrypted image of Boat.512 using changed ε = 0.3900000001, (l) difference between (b) and (k).
Histogram analysis
Histogram analysis is an important image analysis method, which can reflect the frequency distribution of pixel values in the image. Figures 13 and 14 show that encrypted images have completely different histograms against the original images. It shows that the encrypted image has no relationship with the original image. Therefore, the proposed image encryption algorithm can resist histogram analysis attacks.
The histograms of the encrypted binary image, color image and encrypted color image. (a) Histogram of encrypted Binary_boat.512, (b) histogram of R channel of color image 4.2.03, (c) histogram of R channel of encrypted color image 4.2.03, (d) histogram of G channel of color image 4.2.03, (e) histogram of G channel of encrypted color image 4.2.03, (f) histogram of B channel of color image 4.2.03, (g) histogram of B channel of encrypted color image 4.2.03.
Differential attack
To evaluate the encryption algorithm’s ability to resist differential attacks, we employ the unified average changing intensity (UACI) and the number of pixels change rate (NPCR) which are defined by
where c1and c2 are the two ciphered images. The test images also include some images from the USC-SIPI image database. The NPCR and UACI values about ciphered images are listed in Table 1, which shows that the proposed encryption algorithm is very sensitive to a pixel change in the original image.
Mean Squared Error (MSE) and Peak Signal to Noise Ratio (PSNR) can be used to test the efficiency of encryption and decryption40,41. We calculate the PSNR and the MSE of the original images and the encrypted images. It can be seen from Table 2 that the PSNR value is lower, while the MSE value is higher, which indicates that the image encryption process is more efficient. Similarly, we also calculate the PSNR and the MSE of the original images and the decrypted images. The results in Table 2 show that the PSNR value is higher and the MSE value is lower, indicating that the image decryption of algorithm is efficient too.
Correlation analysis
An efficient encryption scheme should reduce the correlation between adjacent pixels in the ciphered image significantly. In order to test the image correlation, we randomly select 3000 pairs of adjacent pixels from the image to calculate the correlation coefficients of adjacent pixels in the vertical, horizontal and diagonal directions using the following equation:
where x and y represent two adjacent pixels and S is the total number of adjacent pixels (x, y). E(x) is the expectation of x and D(x) is the variance of x, respectively. The pixels distribution of the plain images and the cipher images in three directions are shown in Figs. 15, 16, 17, 18, 19, 20. From figures it shows that the points in the encrypted images are randomly distributed, and the correlation of the images are greatly reduced. Meanwhile, Table 3 lists the correlation coefficients of the encrypted images which values are almost close to 0.
Distribution of adjacent pixels of the image Boat.512 and its encrypted images. (a) Horizontal direction of the image, (b) vertical direction of the image, (c) diagonal direction of the image, (d) horizontal direction of the encrypted image, (e) vertical direction of the encrypted image, (f) diagonal direction of the encrypted image.
Distribution of adjacent pixels of the image 3.2.25 and its encrypted images. (a) Horizontal direction of the image, (b) vertical direction of the image, (c) diagonal direction of the image, (d) horizontal direction of the encrypted image, (e) vertical direction of the encrypted image, (f) diagonal direction of the encrypted image.
Distribution of adjacent pixels of the color image 4.2.03 and its encrypted image. (a) Horizontal direction of R channel of the color image 4.2.03, (b) vertical direction of R channel of the color image 4.2.03, (c) diagonal direction of R channel of the color image 4.2.03, (d) horizontal direction of R channel of encrypted color image 4.2.03, (e) vertical direction of R channel of encrypted color image 4.2.03, (f) diagonal direction of R channel of encrypted color image 4.2.03, (g) horizontal direction of G channel of the color image 4.2.03, (h) vertical direction of G channel of the color image 4.2.03, (i) diagonal direction of G channel of the color image 4.2.03, (j) horizontal direction of G channel of encrypted color image 4.2.03, (k) vertical direction of G channel of encrypted color image 4.2.03, (l) diagonal direction of G channel of encrypted color image 4.2.03, (m) horizontal direction of B channel of the color image 4.2.03, (n) vertical direction of B channel of the color image 4.2.03, (o) diagonal direction of B channel of the color image 4.2.03, (p) horizontal direction of B channel of encrypted color image 4.2.03, (q) vertical direction of B channel of encrypted color image 4.2.03, (r) diagonal direction of B channel of encrypted color image 4.2.03.
Information entropy
Information entropy is the most important criterion to evaluate the efficiency of an image encryption algorithm. We calculate the information entropy of the cipher images and the results are listed in Table 4. The entropy of encrypted images are close to 8, which proves the proposed scheme is sufficient to withstand entropy-based attacks.
Comparison with existing algorithms
In recent years, some researchers have combined chaotic maps with optimization methods, DNA coding, S-box and mathematical transformation to propose secure and effective image encryption schemes1,4,25,40,41. Some encryption algorithms have improved the efficiency of encryption by optimizing the permutation and diffusion process16,18. In this paper, a new efficient image encryption algorithm is proposed by combining the OF-LSTMS with the 2DCML fractional-order chaotic system. By using the OF-LSTMS, the pixel position is changed while the pixel value is changed, which realizes the synchronization of permutation and diffusion. At the same time, the 2DCML fractional-order chaotic system has better chaotic ergodicity than traditional chaotic system. Compared with some recent literature, it is clear that the proposed encryption algorithm is better in performance, as shown in Table 5.
Robustness analysis
A feasible encryption algorithm needs the ability of anti-interference, and robustness is an important indicator2,7,26,44. We add Salt-and-Pepper noise with different intensities to the ciphertext images, and we also make different degrees of data loss to the ciphertext image at different locations. The decryption effects are shown in Fig. 21. The quantitative results of resisting noise and occlusion attacks are listed in Table 6. The experimental results show that the decrypted image can still display the main information of the original image, so the algorithm is anti attack.
Robustness analysis results. (a) The encrypted image Boat.512 with salt and pepper noise, intensity 0.01, (b) decryption of (a), (c) the encrypted image Boat.512 with salt and pepper noise, intensity 0.05, (d) decryption of (c), (e) The encrypted image Boat.512 with 6% data loss, (f) decryption of (e), (g) the encrypted image Boat.512 with 25% data loss, (h) decryption of (g), (i) the encrypted image 3.2.25 with salt and pepper noise, intensity 0.01, (j) decryption of (i), (k) the encrypted image 3.2.25 with salt and pepper noise, intensity 0.05, (l) decryption of (k), (m) the encrypted image 3.2.25 with 6% data loss, (n) decryption of (m), (o) The encrypted image 3.2.25 with 25% data loss, (p) decryption of (o).
Speed performance
The implementation environment of the proposed algorithm is Visual Studio 2019 (Visual C++) with Windows 10 Professional operating system. The specific configuration is Intel Core 2.8 GHz CPU, 8 GB RAM and 1000 GB hard disk. At the same time, MATLAB 2018 (a) is used to plot some graphs. The average running speed of encryption is 0.925 s and the encryption time of other encryption schemes7,14,25,33 is 2.44 s, 2.135 s, 1.067064 s and 0.9665 s, respectively. The comparison results show that our algorithm is more efficient and suitable for real-time applications.
Conclusions
We propose a novel image encryption algorithm based on the OF-LSTMS and the 2DCML fractional-order chaotic system. The original image is divided into several image blocks which are converted into sequence data and transfer to the OF-LSTMS for encryption. Image blocks are mapped to the new position by the OF-LSTMS and chaotic sequences, which achieving the effect of the synchronous change of image pixel values and position. In addition, the 2DCML fractional-order chaotic system contains good features as larger key space, better chaotic sequences which it is more suitable for encryption algorithm. The parameters used in the input gate, the output gate and memory unit of the OF-LSTMS are initialized according to the proposed chaotic system generated, which are different from the traditional LSTM initialization method. The proposed encryption algorithm greatly reduces the time consumption and improves the efficiency of image encryption. The extensive simulated experimental results such as key sensitivity, correlation, NPCR, UACI, information entropy and robustness analysis prove that proposed algorithm is high security and efficiency for image encryption applications.
References
El-Latif, A. A. A. et al. Quantum-inspired cascaded discrete-time quantum walks with induced chaotic dynamics and cryptographic applications. Sci. Rep. 10, 1930 (2020).
Mansouri, A. & Wang, X. Y. A novel one-dimensional sine powered chaotic map and its application in a new image encryption scheme. Inf. Sci. 520, 6–62 (2020).
Di Falco, A. et al. Perfect secrecy cryptography via mixing of chaotic waves in irreversible time-varying silicon chips. Nat. Commun. 10, 5827 (2019).
Ben Farah, M. A., Farah, A. & Farah, T. An image encryption scheme based on a new hybrid chaotic map and optimized substitution box. Nonlinear Dyn. 99, 3041–3064 (2020).
He, Y., Zhang, Y. Q. & Wang, X. Y. A new image encryption algorithm based on two-dimensional spatiotemporal chaotic system. Neural Comput. Appl. 79, 24–31 (2019).
Zhang, Y. et al. DNA origami cryptography for secure communication. Nat. Commun. 10, 5469 (2019).
Wang, X. Y. et al. A privacy encryption algorithm based on an improved chaotic system. Opt. Lasers Eng. 122, 335–346 (2019).
Vidhya, R. & Brindha, M. A novel conditional Butterfly Network Topology based chaotic image encryption. J. Inf. Secur. Appl. 52, 102484 (2020).
Ismail, S. M. et al. Generalized double-humped logistic map-based medical image encryption. J. Adv. Res. 10, 85–98 (2018).
Jithin, K. C. & Sankar, S. Colour image encryption algorithm combining Arnold map, DNA sequence operation, and a Mandelbrot set. J. Inf. Secur. Appl. 50, 102428 (2020).
Tsafack, N. et al. Design and implementation of a simple dynamical 4-D chaotic circuit with applications in image encryption. Inf. Sci. 515, 191–217 (2020).
Kumar, S. et al. Cryptographic construction using coupled map lattice as a diffusion model to enhanced security. J. Inf. Secur. Appl. 46, 70–83 (2019).
Zhang, Y. Q., He, Y., Li, P. & Wang, X. Y. A new color image encryption scheme based on 2DNLCML system and genetic operations. Opt. Lasers Eng. 128, 106040 (2020).
Nematzadeh, H. et al. Medical image encryption using a hybrid model of modified genetic algorithm and coupled map lattices. Opt. Lasers Eng. 110, 24–32 (2018).
Belazi, A. et al. Chaos-based partial image encryption scheme based on linear fractional and lifting wavelet transforms. Opt. Lasers Eng. 88, 37–50 (2017).
Wang, X. Y. & Zhao, H. Y. Fast image encryption algorithm based on parallel permutation-and-diffusion strategy. Multimed. Tools Appl. https://doi.org/10.1007/s11042-020-08810-z (2020).
Praveenkumar, P., Amirtharajan, R., Thenmozhi, K. & Thenmozhi, K. Fusion of confusion and diffusion: A novel image encryption approach. Telecommun. Syst. 65, 65–78 (2017).
Patro, K. A. K., Acharya, B. & Nath, V. Secure multilevel permutation-diffusion based image encryption using chaotic and hyper-chaotic maps. Microsyst. Technol. 25, 4593–4607 (2019).
Mondal, B., Behera, P. K. & Gangopadhyay, S. A secure image encryption scheme based on a novel 2D sine–cosine cross-chaotic (SC3) map. J. Real-Time Image Pr. https://doi.org/10.1007/s11554-019-00940-4 (2020).
Mondal, B., Kumar, P. & Singh, S. A chaotic permutation and diffusion based image encryption algorithm for secure communications. Multimed. Tools Appl. 77, 31177–31198 (2018).
Li, M. et al. Cryptanalysis and improvement in a chaotic image cipher using two-round permutation and diffusion. Nonlinear Dyn. 96, 31–47 (2019).
Gopalakrishnan, T. & Ramakrishnan, S. Image encryption using hyper-chaotic map for permutation and diffusion by multiple hyper-chaotic maps. Wireless Pers. Commun. 109, 437–454 (2019).
Gayathri, J. & Subashini, S. A spatiotemporal chaotic image encryption scheme based on self adaptive model and dynamic keystream fetching technique. Multimed. Tools Appl. 77, 24751–24787 (2018).
Devaraj, P. & Kavitha, C. An image encryption scheme using dynamic S-boxes. Nonlinear Dyn. 86, 927–940 (2016).
Wang, X. et al. A new image encryption scheme based on coupling map lattices with mixed multi-chaos. Sci. Rep. 10, 9784 (2020).
Wang, H. N., Xiang, S. Y. & Gong, J. K. Multi-user image encryption algorithm based on synchronized random bits generator in semiconductor lasers network. Multimed. Tools Appl. 78, 26181–26201 (2019).
Maddodi, G., Awad, A. & Awad, D. heterogeneous chaotic neural network generator and DNA encoding. Multimed. Tools Appl. 77, 24701–24725 (2018).
Pan, S., Wei, J. G. & Hu, S. B. A novel image encryption algorithm based on hybrid chaotic mapping and intelligent learning in financial security system. Multimed. Tools Appl. 79, 9163–9176 (2020).
Westhuizen, J. V. D. & Lasenby, J. The unreasonable effectiveness of the forget gate. arXiv: arXiv:1804.04849 (2018).
Theis, L. & Bethge, M. Generative image modeling using spatial LSTMs. In Advances in Neural Information Processing Systems 28: Annual Conference on Neural Information Processing Systems 2015, December 7–12, 2015, Montreal, Quebec, Canada, 1927–1935 (2015).
Han, M., Chen, W. Y. & Moges, A. D. Fast image captioning using LSTM. Cluster Comput. 22, 6143–6155 (2019).
Carlos, A., Theran, M. A. & Alvarez, E. A. A pixel level scaled fusion model to provide high spatial-spectral resolution for satellite images using LSTM networks. In Proceedings of the 10th Workshop on Hyperspectral Imaging and Signal Processing: Evolution in Remote Sensing, WHISPERS 2019, Amsterdam, Netherlands, September 24–26, 1–5 (2019).
Ahmad, M., Tarek, S. & Sheltami, R. Digital image encryption techniques for wireless sensor networks using image transformation methods: DCT and DWT. J. Amb. Intell. Hum. Comput. 10, 4733–4750 (2019).
Matthews, R. On the derivation of a “chaotic” encryption algorithm. Cryptologia 8, 29–41 (1989).
Fridrich, J. Symmetric ciphers based on two-dimensional chaotic maps. Int. J. Bifurcation Chaos 8, 1259–1284 (1998).
Chen, Y. & Liao, X. F. Cryptanalysis on a modified Baptista-type cryptosystem with chaotic masking algorithm. Phys. Lett. A 342, 389–396 (2005).
Xie, E. Y. et al. On the cryptanalysis of Fridrich’s chaotic image encryption scheme. Signal Process. 132, 150–154 (2017).
Akhavan, A., Samsudin, A. & Akhshani, A. Cryptanalysis of “an improvement over an image encryption method based on total shuffling”. Opt. Commun. 350, 77–82 (2015).
Wheeler, D. D. & Matthews, R. A. J. Supercomputer investigations of a chaotic encryption algorithm. Cryptologia. 15, 140–152 (1991).
Dua, M., Suthar, A., Garg, A. & Garg, V. An ILM-cosine transform-based improved approach to image encryption. Complex Intell. Syst. 1–17 (2020).
Dua, M., Wesanekar, A., Gupta, V., Bhola, M. & Dua, S. Differential evolution optimization of intertwining logistic map-DNA based image encryption technique. J. Amb. Intell. Hum. Comput. 11, 3771–3786 (2020).
Bisht, A., Dua, M. & Dua, S. A novel approach to encrypt multiple images using multiple chaotic maps and chaotic discrete fractional random transform. J. Amb. Intell. Hum. Comput. 10, 3519–3531 (2019).
Dua, M., Wesanekar, A., Gupta, V., Bhola, M. & Dua, S. Color image encryption using synchronous CML-DNA and weighted bi-objective genetic algorithm. In Proceedings of the 3rd International Conference on Big Data and Internet of Things, 121–125 (2019).
Lakshmi, C. et al. Hopfield attractor-trusted neural network: An attack-resistant image encryption. Neural Comput. Appl. https://doi.org/10.1007/s00521-019-04637-4 (2019).
Gregor, K. et al. DRAW: Recurrent neural network for image generation. In Proceedings of the 32nd International Conference on Machine Learning, ICML, Lille, France, 6–11 July 2015, Vol. 37, 1462–1471 (2015).
Marijn, F. et al. Parallel multi-dimensional lSTM, with application to fast biomedical volumetric image segmentation. In Advances in Neural Information Processing Systems 28: Annual Conference on Neural Information Processing Systems NIPS, December 7–12, 2015, Montreal, Quebec, Canada, 2998–3006 (2015).
Zhou, F. et al. Hyperspectral image classification using spectral-spatial LSTMs. Neurocomputing 328, 39–47 (2019).
Aslan, E. & Akgul, Y. S. Tongue contour tracking in ultrasound images with spatiotemporal LSTM networks, pattern recognition. In Proceedings of the 41st DAGM German Conference, DAGM GCPR 2019, Dortmund, Germany, September 10–13, 2019, Vol. 11824, 513–521 (2019).
Hochreiter, S. & Schmidhuber, J. Long short-term memory. Neural Comput. 9, 1735–1780 (1997).
Gers, F. A., Schmidhuber, J. & Cummins, F. Learning to forget: Continual prediction with LSTM. Neural Comput. 12, 2451–2471 (2000).
Yuan, L. G., Zheng, S. & Alam, Z. Dynamics analysis and cryptographic application of fractional logistic map. Nonlinear Dyn. 96, 615–636 (2019).
Zhang, Y. Q., Hao, J. L. & Wang, X. Y. An efficient image encryption scheme based on S-boxes and fractional-order differential logistic map. IEEE Access 8, 54175–54188 (2020).
Kaneko, K. Spatiotemporal chaos in one- and two-dimensional coupled map lattices. Phys. D 37, 60–82 (1989).
Acknowledgements
This research is supported by the Program for New Century Excellent Talents in Fujian Province University, the Natural Science Foundation of Fujian Province of China (No.2018J01100), Zhangzhou Science and Technology Project (No.ZZ2018J23), the National Natural Science Foundation of China (No.61672124), the Password Theory Project of the 13th Five-Year Plan National Cryptography Development Fund (No.MMJJ20170203), Liaoning Province Science and Technology Innovation Leading Talents Program Project (No.XLYC1802013), Key R&D Projects of Liaoning Province in 2019.
Author information
Authors and Affiliations
Contributions
Y.H. wrote the main manuscript text, code and also polished the language and modified the manuscript. Y.-Q.Z. provided ideas, design solutions, and the division of labor throughout the project. X.H. was responsible for preparing image materials, experimental testing and collating experimental data. X.-Y.W. supplemented the experiment and added manuscript text based on previous work.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
He, Y., Zhang, YQ., He, X. et al. A new image encryption algorithm based on the OF-LSTMS and chaotic sequences. Sci Rep 11, 6398 (2021). https://doi.org/10.1038/s41598-021-85377-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-021-85377-1
This article is cited by
-
A new approach based on artificial neural networks and chaos for designing deterministic random number generator and its application in image encryption
Multimedia Tools and Applications (2024)
-
A visually secure image encryption scheme using newly designed 1D sinusoidal chaotic map and P-tensor product compressive sensing
Nonlinear Dynamics (2024)
-
A survey of image encryption algorithms based on chaotic system
The Visual Computer (2023)
-
High-quality restoration image encryption using DCT frequency-domain compression coding and chaos
Scientific Reports (2022)
-
Image cryptosystem based on plain image correlation rate and selective chaotic maps
Multimedia Tools and Applications (2022)
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.