Abstract
By manipulating the reference pulses amplitude, a security vulnerability is caused by self-reference continuous-variable quantum key distribution. In this paper, we formalize an attack strategy for reference pulses, showing that the proposed attack can compromise the practical security of CVQKD protocol. In this scheme, before the beam splitter attack, Eve intercepts the reference pulses emitted by Alice, using Bayesian algorithm to estimate phase shifts. Subsequently, other reference pulses are re-prepared and resubmitted to Bob. In simulations, Bayesian algorithm effectively estimates the phase drifts and has the high robustness to noise. Therefore, the eavesdropper can bias the excess noise due to the intercept-resend attack and the beam splitter attack. And Alice and Bob believe that their excess noise is below the null key threshold and can still share a secret key. Consequently, the proposed attack shows that its practical security can be compromised by transmitting the reference pulses in the continuous-variable quantum key distribution protocol.
Similar content being viewed by others
Introduction
Quantum key distribution (QKD) is one of the advanced technology to date, and the security of the shared keys is guaranteed by the quantum mechanics1,2,3,4,5. Allowing two authenticated parties to establish secret keys in an insecure channel, QKD provides a secure way. In the discrete-variable quantum key distribution (DVQKD), several significant achievements have been achieved6,7,8,9,10,11,12. For implementing DVQKD, Pan et al. has launched a low-Earth-orbit satellite, with key rate around 20 orders of magnitudes greater than optical fiber13. For decades, continuous-variable quantum key distribution (CVQKD) without the requirement of single-photon detection, has made significant progress of QKD research14,15,16. However, there is a fundamental limit on the maximum number of secret bits that can be generated by two remote parties. This limit is the secret key capacity of the lossy channel, which also known as the PLOB bound17. In this general context, Gaussian-modulated coherent state (GMCS) protocol has been experimentally achieved both in long distance and high speed18,19,20,21. Moreover, the protocol has already proved secure in the asymptotic regime22,23 and finite-size regime24,25. To be specific, the signal pulses and local oscillator (LO) pulses are simultaneously prepared by Alice in the GMCS protocol. In other words, the LO is deemed as a fixed phase reference for the signal detection, which can reduce the phase noise.
Nevertheless, the transmission of the LO brings about several limitations26,27,28,29. Firstly, the LO may be controlled and modified by eavesdropper. Eve may launch attacks by manipulating the LO, such as LO fluctuation attacks30, calibration attacks31, saturation attacks32 and wavelength attacks28,33. Secondly, the complicated techniques of multiplexing and de-multiplexing are necessary to transmit and separate the two pulses, respectively. Thirdly, sending the strong LO pulses can reduce the transmission efficiency. In order to solve these problems, self-reference CVQKD protocols are proposed, which can generate the LO locally at Bob’s side. Besides, several protocols have been proposed to solve the flaws of phase drift in the self-reference CVQKD protocol34,35,36.
Recently, Qin et al. formalize an attack strategy; Eve cuts down the quantum channel and inserts an external light into the self-reference CVQKD system37. However, the countermeasure for this attack is proposed in the reference38. Shengjun et al. propose a reference pulse attack, which can exploit the phase estimation error associated with the reference pulses to attack the self-reference CVQKD protocol39. Besides, Pereira et al. consider an attack on a coherent-state protocol; Eve not only taps the main communication channel but also hacks AliceâĂŹs device40. Nevertheless, there are some defects in theoretical analysis and it is hard to achieve. Inspired by side channel attack, we formalize the attack strategy for discrete-modulated and Gaussian-modulated self-reference CVQKD, respectively. The attack works as follows: Eve increases her amount of beam splitter attack on the quantum signal, which inevitably increasing the excess noise. Before the beam splitter attack, she utilizes the intercept-resend attack and the Bayesian algorithm to decrease the phase estimation error noise. Therefore, Eve can bias the excess noise due to the beam splitter attack and the intercept-resend attack, and Alice and Bob believe their excess noise estimation is below the null key threshold and they can still share a secret key. To intercept-resend attack, that is, Eve can monitor and intercept the reference pulses emitted by Alice. Subsequently, she measures each reference pulse and then estimates the phase drift using the Bayesian algorithm. After phase estimation and compensation operation, she re-prepares and resubmits another reference pulses, which is sent to Bob. What’s more, we propose to utilize Bayesian algorithm to estimate the reference pulses. The algorithm not only can obtain a confidence interval, but also has robustness to noise. Therefore, the algorithm can increase the accuracy of phase estimation for Eve. This series of operations can cause a security vulnerabilities through the manipulation of the reference pulses.
Practical Security Analysis
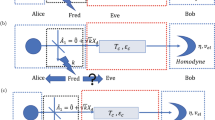
In this section, we start by describing the protocol of the self-reference CVQKD. Subsequently, we analyze how Eve can intercept the reference pulses and estimate the phase drift for the discrete-modulated and Gaussian-modulated self-reference CVQKD, respectively. The self-reference CVQKD protocol, as shown in Fig. 1, consists of two parts, one is the coherent states preparation and propagation, and the other part is the coherent states detection and processing. At the transmitter, Alice prepares the Gaussian-modulated coherent states (or the discrete-modulated states) and then transmits to Bob. The arbitrary phase drift of the states will be inevitably induced through the quantum channel. Therefore, the phase reference pulses are necessary to transmit along with the signal pulses. As depicted in Fig. 1, the reference pulses and signal pulses are sent by Alice alternatively and periodically. At the receiver, Bob can utilize the relatively strong reference pulses to estimate the phase35. In theory, quantum phase noise \(\Delta \varphi \) between the two users can be written as41
where \(L\) represents the length of the fiber, \(\Delta v\) is the difference frequency between the user’s lasers, and \(s\) denotes the speed of light in the fiber. Although several protocols are proposed to the phase compensation, the strong reference pulses are still indispensable in the self-reference CVQKD. However, propagating the relatively strong reference pulses may result in security vulnerabilities.
In what follows, we analyze the practical security of reference pulses for CVQKD with discrete modulation. In this scenario, Eve has the ability to monitor and intercept the reference pulses from Alice to Bob. Basically, Eve measures each reference pulse and estimates the phase drift emitted by Alice. After the phase compensation, she re-prepares and resubmits reference pulses, which are sent to Bob. Next, we introduce how Eve employs Bayesian algorithm to estimate the phase drift of the intercepted reference pulses. Without loss of generality, we analyze the four-state self-reference CVQKD protocol42,43,44. The four-state can be denoted as \(\left|\,{\alpha }_{k}\right\rangle =\left|\,\alpha {e}^{i(2k+1)\pi /4}\right\rangle \) with \(k\in \{0,1,2,3\}\), and the modulation variance is \(V=1+2{\alpha }^{2}\). When Eve intercepts reference pulses through the noisy channel, as shown in Fig. 2, the photon number resolving detector (PNRD) performs the measurement operation. Specifically, the measurement outcomes are denoted as \( {\mathcal E} \in \{\left|\,{\alpha }_{0}\right\rangle ,\left|\,{\alpha }_{1}\right\rangle ,\left|\,{\alpha }_{2}\right\rangle ,\left|\,{\alpha }_{3}\right\rangle \}\), and the total number of detected photons are described as \({\mathscr E}={\sum }_{i=0}^{3}{n}_{i}\), where \({n}_{i}\) symbolizes the detected photon of state \(\left|\,{\alpha }_{i}\right\rangle \). Then, we provide the critical process of Bayesian estimation. Above all, in order to estimate the correct eigenphase, an initial prior probability distribution \({\mathscr P}(\varphi )\) is provided to express the confidence interval that the current hypotheses is the correct eigenphase. Subsequently, the mean \(\mu \) and its standard derivation \(\sigma \) are updated on the basis of the measurement results of PNRD. What’s more, the posterior probability distribution can be calculated as45,46
Specifically, some particles drawn from the \({\mathscr P}(\varphi )\) mismatch the likelihood function, which will be discarded later. The likelihood function is defined as \({\mathscr P}(\left|\,{\alpha }_{0}\right\rangle | \varphi )=\frac{1}{4}(1+{e}^{-{\Delta }^{2}}\cos (\varphi ))\), \({\mathscr P}(\left|\,{\alpha }_{1}\right\rangle | \varphi )=\frac{1}{4}(1+{e}^{-{\Delta }^{2}}\sin (\varphi ))\), \({\mathscr P}(\left|\,{\alpha }_{2}\right\rangle | \varphi )=\frac{1}{4}(1-{e}^{-{\Delta }^{2}}\cos (\varphi ))\) and \({\mathscr P}(\left|\,{\alpha }_{3}\right\rangle | \varphi )=\frac{1}{4}(1-{e}^{-{\Delta }^{2}}\sin (\varphi ))\). Without loss of generality, the qubit undergoes a phase diffusion process whose amplitude is characterized by the parameter \(\Delta \). After obtaining the posterior distribution in Eq. 2, we set the posterior probability distribution to equal the prior probability distribution. This updating program can be deemed as the iterative processing for each of the emulation.
The practical security analysis of reference pulses for the CVQKD protocol with discrete modulation. CW laser, continuous wave laser; BS, beam splitter; PD, photodetector; VOA, variable optical attenuator; PBS, polarizing beam splitter; Att., attenuator; PNRD, photon number resolving detector; DL, delay line; PC, polarization controller; AM-PM, amplitude and phase modulation.
Subsequently, we provide the mathematical definition of probability density function (PDF) to illustrate the relation between the phase shift and the detected photons \({\mathscr E}\). The PDF is defined as \({{\mathscr P}}_{B}(\varphi ;{\mathscr E})=\frac{{\sum }_{i=0}^{3}{\mathscr P}{(\left|{\alpha }_{i}\right\rangle | \varphi )}^{{n}_{i}}}{ {\mathcal M} }\), where \( {\mathcal M} \) is the normalization factor satisfies with \({\int }_{0}^{2\pi }{{\mathscr P}}_{B}(\varphi ;{\mathscr E}){\rm{d}}\varphi =1\). The simulation results of phase drift are depicted in Fig. 3. The two subgraphs illustrate that, the phase drift tends to zero if we increase the number of \({n}_{0}\) (where \({n}_{1}\), \({n}_{2}\) and \({n}_{3}\) are constant). Here, \({n}_{i}\) is defined in the previous paragraph. Consequently, increasing the detected photons for intercepted reference pulses can improve the accuracy of phase estimation, thus reducing the possibility of phase shift. Next, we describe the main implementation steps of the Bayesian algorithm. In the initial interation of the algorithm, a prior distribution \({\mathscr E}({\mu }_{0},{\sigma }_{0})\) is to express the confidence interval. Then, the dataset is utilized to update the \(\mu \) and \(\sigma \) of the posterior probability distribution in accordance with Bayes’ theorem. The parameter estimation for the inferred \({\sigma }^{2}\) of the posterior probability density is simulated in Fig. 4a, and the shaded region stands for the proportion correct ratio of the predicted trials. In other words, increasing the signal intensity level can improve the proportion correct of concentration. As shown in Fig. 4b, we utilize the different initial \({\sigma }^{2}\) to simulate and test that the performance is insensitive to the initial \({\sigma }^{2}\). In other words, the Bayesian algorithm has the high robustness. Furthermore, the main steps of the algorithm45,47,48 are described in the Appendix.
By comparison to the discrete-modulated CVQKD protocol, the Gaussian-modulated CVQKD protocol is more complicated. We adopt the Mach-Zehnder (MZ) interferometer to estimate the phase drifts49,50,51,52,53. The Mach-Zehnder interferometer, as shown in Fig. 5, has two inputs labelled \(1\) and \(2\), one input is the intercepted reference pulses, and the other is the coherent light source. The two inputs are combined in two beamsplitters (\(B{S}_{1}\) and \(B{S}_{2}\)) and two internal arms. On the one of the branches for output, a beamsplitter (\(B{S}_{3}\)) has two outputs labelled as \(3\) and \(4\). On the other branch, a beamsplitter (\(B{S}_{3}\)) has two outputs labelled as \(5\) and \(6\). According to the mentioned above, photodetectors are applied to outputs and respond to intensities \({I}_{k}\). Therefore, we integrate over some observations \(T\), and define the parameter \({W}_{k}={\int }_{T}{I}_{k}\,{\rm{d}}t\) with \(k\in \left\{3,4,5,6\right\}\). Particularly, the parameter \({W}_{k}\) can be substituted by the integer \({n}_{k}\), where \({n}_{k}\) represents the photodetection result in the time interval \(T\). Based on the NFM theory (Noh, Fougères and Mandel)51, the unambiguous value of phase \(\varphi \) is estimated as
When the photon number \({\bar{n}}_{{\rm{in}}}\) at input \(1\) and \(2\) is determined, the outputs \(3\, \sim \,6\) have the mean values \({\bar{n}}_{3}={\bar{n}}_{{\rm{in}}}(1+V\cos \varphi )\), \({\bar{n}}_{4}={\bar{n}}_{{\rm{in}}}(1-V\cos \varphi )\), \({\bar{n}}_{5}={\bar{n}}_{{\rm{in}}}(1+V\sin \varphi )\) and \({\bar{n}}_{6}={\bar{n}}_{{\rm{in}}}(1-V\sin \varphi )\), where the maximum likelihood estimate can be given by
Consequently, based on the Poissonian distribution of photoncount and mean value \({\bar{n}}_{{\rm{in}}}\), the likelihood of \(\varphi \) and \({\bar{n}}_{{\rm{in}}}\) is
with the notation \({\bf{n}}=\left[{n}_{3},{n}_{4},{n}_{5},{n}_{6}\right]\). Assuming that \({\bar{n}}_{{\rm{in}}}\) is independent of \(\varphi \) and \(V\), we have
Consequently, the posterior probability distribution takes the following form
which is in accordance with the Eq. 2 of four-state self-reference CVQKD protocol.
The practical security analysis of reference pulses for the CVQKD protocol with Gaussian modulation. CW laser, continuous wave laser; BS, beam splitter; PD, photodetector; VOA, variable optical attenuator; PBS, polarizing beam splitter; Att., attenuator; PNRD, photon number resolving detector; DL, delay line; PC, polarization controller; AM, amplitude modulation; PM, phase modulation.
Performance Analysis
First of all, we define transmission probability and transition probability to analyze the performance of the reference pulses for the discrete modulation protocol. In the four-state self-reference CVQKD protocol, there are four kinds of the intercepted encoding phase, namely the \({\varphi }_{i}=\frac{(2k+1)\pi }{4}\), with \(k\in \left\{0,1,2,3\right\}\). According to the likelihood function, if the transmission states are in consistent with the measurement outcome \( {\mathcal E} \), the equation can be simplified as
Therefore, the transmission probability can be defined as \({{\mathscr P}}_{ii}={\mathscr P}(\left|\,{\alpha }_{i}\right\rangle | {\varphi }_{i})\) with \(i\in \left\{0,1,2,3\right\}\), which satisfies the constraint \({\sum }_{j=0}^{3}{\mathscr P}(\left|\,{\alpha }_{i}\right\rangle | {\varphi }_{j})=1\). Moreover, the transition probability can be expressed as \({{\mathscr P}}_{ij}=1-{{\mathscr P}}_{ii}\) with \(i\ne j\). Subsequently, the QBER for Eve can be calculated as \(QBER={\sum }_{n}{{\mathscr Q}}_{n}{ {\mathcal R} }_{n}\), with the notation
and \({ {\mathcal R} }_{n}=\frac{{e}^{-{N}_{c}}\cdot {N}_{c}^{n}}{n!},{C}_{n}^{k}=\frac{n!}{k!(n-k)!},n!=1\times 2\times 3\times \cdots (n-1)\times n\). Here, \(n\) and \({N}_{c}\) symbolize the transmitted photons (at the Alice’s side) and detected photons (at the Eve’s side) per pulse, respectively. Figure 6a depicts the QBER for Eve with the discrete modulation protocol. Considering the existence of noise in the channel, two parameters are restricted with \(n > {N}_{c}\). According to the result, we can see that, increasing the number of \(n\) and \({N}_{c}\) will improve the QBER of the intercept-resend attack for Eve.
In the following, we analyze the performance of the Bayesian estimator for the Gaussian-modulated self-reference CVQKD protocol. The Bayesian cost can be defined by the relation
Particularly, if a suitable initial phase value \({\varphi }^{^{\prime} }\) is given, the minimum mean squared error (MMSE) estimator of \({\varphi }^{^{\prime} }\) has the form
where \({\varphi }^{^{\prime} }\) can be initialized with the maximum likelihood (ML) estimate, and it can be defined as
Figure 6b simulates the performance of the different phase estimation schemes, in particular, the input intensity \({\bar{n}}_{{\rm{in}}}\) is simulated for the fixed phase shift \(\frac{\pi }{3}\). Specifically, the blue line denotes the NFM estimator51,53,54. Consequently, the Bayesian estimator outperforms NFM estimator.
Although the intercept-resend attack can compromise the practical security of QKD, the two remote participants can discover eavesdropping by the following method. At the receiver, Bob randomly chooses the same number of quantum pulses and reference pulses as training signals55. By utilizing the training signals, we can estimate the phase compensation error on reference signals and quantum signals, respectively. If the phase compensation error on signal pulses is different from that on reference pulses, we can conclude that Eve’s attack is attached in the quantum channel.
Conclusion
In this paper, we analyze a security vulnerability of strong reference pulses in the realistic self-reference CVQKD system. In this scenario, before the beam splitter attack, Eve intercepts the reference pulses emitted by Alice, and utilizing the Bayesian algorithm to estimate phase drifts of reference pulses. After phase estimation and compensation, she resubmits another reference pulses to Bob. The algorithm not only can obtain a well-motivated confidence interval, but also has robustness to noise. Thus, due to the intercept-resend attack and the beam splitter attack, Eve can bias the excess noise. Consequently, it shows that the practical security of the proposed attack can be compromised by transmitting the reference pulses in the continuous-variable quantum key distribution protocol.
Appendix
In the following, we take the four-state self-reference CVQKD protocol as an example, to derive the expression of the secret key rate under the intercept-resend attack. Assuming that the phase noise of quantum channel is zero-mean with variance \({V}_{{\rm{ch}}}\), while the phase noise reduced by Eve’s Bayesian algorithm is zero-mean with variance \({V}_{{\rm{Bayes}}}\), the deviation of the actual phase compensation error can be given by \({V}_{s}={V}_{{\rm{ch}}}-{V}_{{\rm{Bayes}}}\). According to the imperfect phase compensation, the actual transmittance can be defined as \({T}_{\kappa }=\kappa T\), where \(\kappa \) represents the phase estimation accuracy with \(\kappa ={\left(1-\frac{1}{2}{V}_{s}\right)}^{2}\), and \(T\) is the transmission efficiency. Besides, the actual excess noise can be expressed as \({\epsilon }_{\kappa }=\left[\epsilon +(1-\kappa )(V-1)\right]/\kappa \). Therefore, the total noise referred to the channel input can be expressed as \({\chi }_{{\rm{tot}}}^{\kappa }={\chi }_{{\rm{line}}}^{\kappa }+{\chi }_{\hom }/{T}_{\kappa }\), with the notation \({\chi }_{{\rm{line}}}=1/{T}_{\kappa }+{\epsilon }_{\kappa }-1\).
When Alice and Bob use reverse reconciliation, the secret key rate can be defined as
where \(\beta \) is the reconciliation efficiency, \(I(A:B)\) is the mutual information between Alice and Bob, and \(\chi (B:E)\) is the mutual information between Bob and Eve. Specifically, the mutual information \(I(A:B)\) is given by55
The Holevo bound of the information between Eve and Bob is given by
where \(G(x)=(x+1){{\rm{\log }}}_{2}(x+1)-x{{\rm{\log }}}_{2}x\). The symplectic eigenvalues \({\lambda }_{1,2}\) are given by
where
The symplectic eigenvalues \({\lambda }_{3,4}\) are given by
with the notation
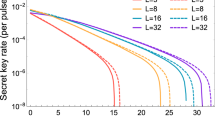
Subsequently, we conduct numerical simulation using the realistic parameters. The parameters are summarized below: \(\alpha =0.35\), \({v}_{{\rm{el}}}=0.001\), \(\epsilon =0.01\), \(\eta =0.6\), \(\beta =0.95\) and \({V}_{{\rm{ch}}}=0.01({{\rm{rad}}}^{2})\). Here, the phase noise reduced by Eve’s Bayesian algorithm submits to the normal distribution with variance \(0.001\), \(0.004\) and \(0.007\) (\({{\rm{rad}}}^{2}\)) respectively. In particular, \({V}_{{\rm{Bayes}}}=0\) represents the original CVQKD protocol without the intercept-resend. Fig. 7 is the simulation result in the asymptotic scenario. According to the simulation result, we can conclude that, the estimated key rate based on the intercept-resend and Bayesian algorithm is higher than the true security key rate. Therefore, the attack is effective in the self-reference CVQKD protocol. In our manuscript, the proposed algorithm is described as follows.
The theoretical and practical secret key rate of the four-state self-reference CVQKD under the intercept-resend attack. The phase noise reduced by Eve’s Bayesian algorithm submits to the normal distribution with variance \(0.001\), \(0.004\) and \(0.007\) (\({{\rm{rad}}}^{2}\)) respectively. In particular, \({V}_{{\rm{Bayes}}}=0\) represents the original CVQKD protocol without the intercept-resend. Other parameters are summarized below: \(\alpha =0.35\), \({v}_{{\rm{el}}}=0.001\), \(\epsilon =0.01\), \(\eta =0.6\), \(\beta =0.95\) and \({V}_{{\rm{ch}}}=0.01({{\rm{rad}}}^{2})\).
References
Bunandar, D. et al. Metropolitan quantum key distribution with silicon photonics. Phys. Rev. X 8, 021009 (2018).
Lo, H. K., Curty, M. & Tamaki, K. Secure quantum key distribution. Nat. Photonics 8, 595–604 (2015).
Weedbrook, C. et al. Gaussian quantum information. Rev. Mod. Phys. 84, 621 (2012).
Pirandola, S. et al. Advances in Quantum Cryptography, arXiv:1906.01645 (2019)
Samuel, L. B. & Peter, V. L. Quantum information with continuous variables. Rev. Mod. Phys. 77, 513 (2005).
Wang, S. et al. Beating the fundamental rate-distance limit in a proof-of-principle quantum key distribution system. Phys. Rev. X 9, 021046 (2019).
Cui, C. H. et al. Twin-Field Quantum Key Distribution without Phase Postselection. Phys. Rev. Applied 11, 034053 (2019).
Wang, S. et al. Practical gigahertz quantum key distribution robust against channel disturbance. Opt. Lett. 43, 2030–2033 (2018).
Wang, S. et al. Proof-of-principle experimental realization of a qubit-like qudit-based quantum key distribution scheme, Quantum Sci. Technol 3, 025006 (2018).
Yin, Z. Q. et al. Improved security bound for the round-robin-differential-phase-shift quantum key distribution. Nat. Commun. 9, 457 (2018).
Wang, S. et al. Experimental demonstration of a quantum key distribution without signal disturbance monitoring. Nat. Photonics 9, 832–836 (2015).
Wang, S., Chen, W., Yin, Z. Q., Li, H. W. & Han, Z. F. Field and long-term demonstration of a wide area quantum key distribution network. Opt. Express 22, 21739–21756 (2014).
Liao, S. et al. Satellite-to-ground quantum key distribution. Nature 549, 43–47 (2017).
García-Patrón, R. & Cerf, N. J. Unconditional optimality of Gaussian attacks against continuous-variable quantum key distribution. Phys. Rev. Lett. 97, 190503 (2006).
Lance, A. M., Symul, T. & Sharma, V. No-switching quantum key distribution using broadband modulated coherent light. Phys. Rev. Lett. 95, 180503 (2005).
Grosshans, F. & Grangier, P. Continuous variable quantum cryptography using coherent states. Phys. Rev. Lett. 88, 057902 (2002).
Pirandola, S., Laurenza, R., Ottaviani, C. & Banchi, L. Fundamental limits of repeaterless quantum communications. Nat. Commun. 8, 15043 (2017).
Huang, D., Huang, P., Lin, D. & Zeng, G. Long-distance continuous-variable quantum key distribution by controlling excess noise. Sci. Rep. 6, 19201 (2016).
Wang, C. et al. 25 MHz clock continuous-variable quantum key distribution system over 50 km fiber channel. Sci. Rep. 5, 14607 (2015).
Huang, D., Lin, D., Wang, C., Liu, W. & Zeng, G. Continuous-variable quantum key distribution with 1 Mbps secure key rate. Opt. Express 23, 17511 (2015).
Jouguet, P., Kunz-Jacques, S., Leverrier, A., Grangier, P. & Diamanti, E. Experimental demonstration of long-distance continuous-variable quantum key distribution. Nat. Photonics 7, 378–381 (2013).
Navascués, M., Grosshans, F. & Acín, A. Optimality of gaussian attacks in continuous-variable quantum cryptography. Phys. Rev. Lett. 97, 190502 (2006).
Renner, R. & Cirac, J. I. A definetti representation theorem for infinite dimensional quantum systems and applications to quantum cryptography. Phys. Rev. Lett. 102, 110504 (2009).
Leverrier, A., Grosshans, F. & Grangier, P. Finite-size analysis of a continuous-variable quantum key distribution. Phys. Rev. A 81, 062343 (2010).
Leverrier, A. Composable security proof for continuous-variable quantum key distribution with coherent states. Phys. Rev. Lett. 114, 070501 (2015).
Qian, Y. J. et al. Hacking the Quantum Key Distribution System by Exploiting the Avalanche-Transition Region of Single-Photon Detectors. Phys. Rev. Applied 10, 064062 (2018).
Huang, J. Z. et al. Quantum hacking on quantum key distribution using homodyne detection. Phys. Rev. A 89, 032304 (2014).
Huang, J. Z. et al. Quantum hacking of a continuous-variable quantum-key-distribution system using a wavelength attack. Phys. Rev. A 87, 062329 (2013).
Li, H. W. et al. Attacking a practical quantum-key-distribution system with wavelength-dependent beam-splitter and multiwavelength sources. Phys. Rev. A 84, 062308 (2011).
Ma, X., Sun, S., Jiang, M. & Liang, L. Local oscillator fluctuation opens a loophole for Eve in practical continuous-variable quantum-key-distribution systems. Phys. Rev. A 88, 022339 (2013).
Jouguet, P., Kunz-Jacques, S. & Diamanti, E. Preventing calibration attacks on the local oscillator in continuous-variable quantum key distribution. Phys. Rev. A 87, 062313 (2013).
Qin, H., Kumar, R. & Alléaume, R. Saturation Attack On Continuous-Variable Quantum Key Distribution System. Proc SPIE 8899, 88990N (2013).
Ma, X. C., Sun, S. H., Jiang, M. S. & Liang, L. M. Wavelength attack on practical continuous-variable quantum-key-distribution system with a heterodyne protocol. Phys. Rev. A 87, 052309 (2014).
Huang, D., Huang, P., Lin, D., Wang, C. & Zeng, G. High-speed continuous-variable quantum key distribution without sending a local oscillator. Opt. Lett. 40, 3695–3698 (2015).
Soh, D. B. S. et al. Self-referenced continuous-variable quantum key distribution protocol. Phys. Rev. X 5, 041010 (2015).
Marie, A. & Romain, A. Self-coherent phase reference sharing for continuous-variable quantum key distribution. Phys. Rev. A 95, 012316 (2017).
Qin, H., Kumar, R. & Alleaume, R. Quantum hacking on a practical continuous-variable quantum cryptosystem by inserting an external light, Proceedings Volume 9648, Electro-Optical and Infrared Systems: Technology and Applications XII and Quantum Information Science and Technology (2015).
Kunz-Jacques, S. & Jouguet, P. Robust shot-noise measurement for continuous-variable quantum key distribution. Phys. Rev. A 91, 022307 (2015).
Ren, S. et al. Reference pulse attack on continuous-variable quantum key distribution with local local oscillator. J. Opt. Soc. Am. B 36, 7–15 (2019).
Pereira, J. & Pirandola, S. Hacking Alice’s box in continuous-variable quantum key distribution. Phys. Rev. A 98, 062319 (2018).
Lucamarini, M., Yuan, Z. L., Dynes, J. F. & Shields, A. J. Overcoming the rate-distance limit of quantum key distribution without quantum repeaters. Nature 557, 400–403 (2018).
Zhang, H., Fang, J. & He, G. Improving the performance of the four-state continuous-variable quantum key distribution by using optical amplifiers. Phys. Rev. A 86, 022338 (2012).
Papanastasiou, P., Lupo, C., Weedbrook, C. & Pirandola, S. Quantum key distribution with phase-encoded coherent states: Asymptotic security analysis in thermal loss channels. Phys. Rev. A 98, 012340 (2018).
Ghorai, S., Grangier, P., Diamanti, E. & Leverrier, A. Asymptotic Security of Continuous-Variable Quantum Key Distribution with a Discrete Modulation. Phys. Rev. X 9, 021059 (2019).
Wiebe, N. & Granade, C. Efficient bayesian phase estimation. Phys. Rev. Lett. 117, 010503 (2015).
Daneshgaran, F., Delgado, M. T. & Mondin, M. Improved key rates for quantum key distribution employing soft metrics using Bayesian inference with photon counting detectors. Quantum Communications and Quantum Imaging IX 8163, 113–122 (2011).
Paesani, S. et al. Experimental bayesian quantum phase estimation on a silicon photonic chip. Phys. Rev. Lett. 118, 100503 (2017).
Wiebe, N., Granade, C., Ferrie, C. & Cory, D. G. Hamiltonian learning and certication using quantum resources. Phys. Rev. Lett. 112, 190501 (2014).
Řeháček, J., Hradil, Z., Dušek, M., Haderka, O. & Hendrych, M. Testing operational phase concepts in quantum optics. Quant. Semiclass. Opt 2, 237–244 (2000).
Walls, D., Milburn, G.Quantum Optics, 1st Edition, Springer, Berlin (1994).
Noh, J. W., Fougères, A. & Mandel, L. Measurement of the quantum phase by photon counting. Phys. Rev. Lett. 67, 1426–1429 (1991).
Rimmer, D. & Fitzgerald, W. J. Bayesian estimation of quantum optical phase by photon counting. Signal Process. 84, 1461–1471 (2004).
Noh, J. W., Fougères, A. & Mandel, L. Operational approach to the phase of a quantum field. Phys. Rev. A 45, 424–442 (1992).
Řeháček, J., Hradil, Z., Dusek, M., Haderka, O. & Hendrych, M. Testing operational phase concepts in quantum optics. J. Opt. B: Quantum Semiclass. Opt 2, 237–244 (1999).
Huang, B., Huang, Y. & Peng, Z. Practical security of the continuous-variable quantum key distribution with real local oscillators under phase attack. Opt. Express 27, 20621–20631 (2019).
Acknowledgements
This work is supported by the National Nature Science Foundation of China (Grant Nos. 61801522, 61872390), and National Nature Science Foundation of Hunan Province, China (Grant No. 2019JJ40352).
Author information
Authors and Affiliations
Contributions
D.H. defined the scientific goals and conceived the project. W.Z. carried out the whole protocol. R.-H.S. developed the phase estimation algorithm. W.Z., R.-H.S. and D.H. wrote the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare that they have no competing interests.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Zhao, W., Shi, R. & Huang, D. Practical Security Analysis of Reference Pulses for Continuous-Variable Quantum Key Distribution. Sci Rep 9, 18155 (2019). https://doi.org/10.1038/s41598-019-54249-0
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-019-54249-0
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.