Abstract
Verifying quantum states is central to certifying the correct operation of various quantum information processing tasks. In particular, in measurement-based quantum computing, checking whether correct graph states are generated is essential for reliable quantum computing. Several verification protocols for graph states have been proposed, but none of these are particularly resource efficient: multiple copies are required to extract a single state that is guaranteed to be close to the ideal one. The best protocol currently known requires O(n15) copies of the state, where n is the size of the graph state. In this paper, we construct a significantly more resource-efficient verification protocol for graph states that only requires O(n5 log n) copies. The key idea is to employ Serfling’s bound, which is a probability inequality in classical statistics. Utilizing Serfling’s bound also enables us to generalize our protocol for qudit and continuous-variable graph states. Constructing a resource-efficient verification protocol for them is non-trivial. For example, the previous verification protocols for qubit graph states that use the quantum de Finetti theorem cannot be generalized to qudit and continuous-variable graph states without tremendously increasing the resource overhead. This is because the overhead caused by the quantum de Finetti theorem depends on the local dimension. On the other hand, in our protocol, the resource overhead is independent of the local dimension, and therefore generalizing to qudit or continuous-variable graph states does not increase the overhead. The flexibility of Serfling’s bound also makes our protocol robust: our protocol accepts slightly noisy but still useful graph states.
Similar content being viewed by others
Introduction
The verification of quantum states plays an important role in ensuring the integrity of a number of quantum technologies including quantum computing, quantum cryptography, and quantum simulations. Graph states are a particularly important class of quantum states, since they can be resource states for measurement-based quantum computation (MBQC).1,2,3,4,5,6,7,8 In the case of MBQC, the problem of verifying quantum computation reduces to simply certify the measurements and the resource state. In this paper, we consider the task of verifying these important resource states that include qubit graph states, qudit graph states, and continuous-variable (CV) graph states.
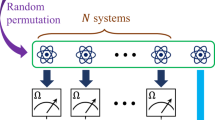
Let us consider the following general setup (as shown in Fig. 1): Bob has a universal quantum computer and he can prepare arbitrary quantum states. Alice, on the other hand, can only perform single-qubit measurements. She does not have any quantum memory and the ability to apply entangling gate operations. Therefore, Alice delegates the preparation of graph states to Bob. Bob generates an nNtotal-qubit state ρB and sends it to Alice. The state ρB consists of Ntotal registers, and each register contains n qubits. If Bob is honest, then the state of each register received by Alice is the correct n-qubit graph state |G〉. In other words,
If Bob is malicious, on the other hand, ρB can be any arbitrary nNtotal-qubit state. Alice randomly chooses Ntotal − 1 registers and measures all of them. In such a scenario, is it possible to construct a protocol such that if these measurement results satisfy certain conditions, then the state of the remaining (i.e., unmeasured) single register is guaranteed to be close to the ideal state |G〉? If such a verification protocol is possible, Alice can safely use the verified register for her desired MBQC. If we consider the qudit (qumode) case, the word “qubit” in the explanation should be replaced with “qudit” (“qumode”).
The schematic shows the setup considerd within this paper. Bob generates an nNtotal-qubit state ρB that consists of Ntotal registers. Each register is represented by a box and contains n qubits. Bob sends the state ρB to Alice. Alice randomly chooses Ntotal − 1 registers, and measures each qubit of them. If the measurement results satisfy certain conditions, the unmeasured single register is guaranteed to be close to the ideal graph state |G〉. If Bob sends Alice each qubit of ρB one by one, and if Alice measures each qubit sequentially, Alice does not need any quantum memory. If we consider the qudit (qumode) case, the word “qubit” in the above explanation should be replaced with “qudit” (“qumode”)
This setup models usual experiments. Bob is regarded to be an experimental equipment that is expected to generate many copies of the n-qubit graph state |G〉, and Alice is an experimentalist who has constructed the equipment. She would like to check the correctness of the experimental equipment. In this case, it is unreasonable to assume that ρB is any state, since the “attack” by the experimental equipment is not a malicious one, but is due to natural noise. In other words,
where \({\cal{E}}\) is a completely positive trace-preserving (CPTP) map that represents certain noise caused by the interaction between the experimental equipment and the environment.
Due to the inherent asymmetry between Alice and Bob, the verification setup shown in Fig. 1 can also be considered as a cloud quantum computing scenario.9,10 Imagine that Bob is the owner of a company, which provides a quantum computing service over the cloud, and Alice as a (computationally weak) client who wants to use the cloud service to perform her desired quantum operations. One way to achieve this task is that Bob generates graph states and send them to Alice one qubit at a time. Alice, who can only perform single-qubit measurements, measures each qubit, as it arrives, to perform her MBQC. Since Alice does not trust Bob, she has to verify the correctness of the graph states by herself. This situation is well modeled by taking \({\cal{E}}\) in Eq. (2) to be a general CPTP map, since Bob is restricted to non-adaptive attacks, which is equivalent to maliciously preparing the initial state.
Several verification protocols, including ones based on self-testing, have been proposed for graph states.11,12,13,14,15,16,17,18 However, all the previous protocols encounter at least one of the three problems described below. First, they are not resource efficient, i.e., Ntotal is large. For example, protocols of refs. 11,12 use the idea of the quantum de Finetti theorem19 to make ρB close to independent and identically distributed (i.i.d.) copies of a single fixed state, but this comes at the cost of large overhead. Such protocols require Ntotal = O(n21) to complete the verification. There are some protocols that do not use the quantum de Finetti theorem,13,14,15,16 but nonetheless Ntotal = O(n15) (for details, see the “Resource efficiency” subsection in the RESULTS section).
Second, although extensions to qudit or CV states are in principle possible for existing protocols13,15,16 (and in fact, extensions to qudit systems are explicitly mentioned in refs. 13,15,16), extending the previous verification protocols11,12,17,18 to higher dimension without increasing Ntotal is highly non-trivial. In fact, in the case when the quantum de Finetti theorem is used for a qudit system with the qudit dimension d ≥ 3, for example, Ntotal depends on \(\sqrt {\log d}\), and therefore if we take d → ∞ to construct a CV verification protocol, we come across the unpleasant consequence that Ntotal → ∞. Note that recently, in ref. 16, the generalization to qudit systems has been made without increasing Ntotal = O(n15). However, this resource overhead is large. Resource-efficient verification protocols for qudit and CV states are indispensable. In fact, there are many important qudit or CV quantum states such as the photon orbital angular momentum states20 and the Gottesman-Kitaev-Preskill (GKP) states.21 Recently, large-scale CV entangled states composed of more than 104 qumodes have been generated.22
Finally, although many previous protocols13,15,16,17 have an error tolerance, it is low or its evaluation is insufficient (for details, see the “Robustness” subsection in the RESULTS section). The error tolerance is an important feature of verification protocols due to the following reason: Even if Bob is honest, the state ρB that Alice receives might be slightly different from the ideal state \(\left| G \right\rangle ^{ \otimes N_{{\mathrm{total}}}}\) because of the imperfections of Bob’s operations and the channel noise between Bob and Alice. These slightly perturbed states can still be useful for fault-tolerant computation. The acceptance of such states by Alice would lead to better verification protocols. A fault-tolerant verification protocol14 that accepts noisy but still error-correctable states has been proposed, but it can be only used for the bipartite graph states.
In this paper, we introduce a new verification protocol that overcomes all the three aforementioned problems. First, we show that our protocol is significantly more resource efficient than previous approaches, i.e., Ntotal = O(n5 log n). (Recall that the best known previous protocols need Ntotal = O(n15)13,14,15,16). The key idea to achieve this efficiency is by employing Serfling’s bound.23,24 Serfling’s bound is a probability inequality for the sum in sampling without replacement, and is often used in classical statistics (for details, see Lemma 1). Serfling’s bound has also been used in the security proofs of quantum key distribution,24,25,26,27 but to the best of our knowledge, so far, Serfling’s bound has never been applied to the verification of quantum computation.
Second, our protocol can be generalized to qudit and CV graph states, while maintaining resource efficiency. As we have explained, constructing a resource-efficient qudit or CV verification protocol is non-trivial. The reason why we succeed in the construction is again because of Serfling’s bound; When we use Serfling’s bound for a qudit system with d ≥ 3, Ntotal is independent of d. Therefore, we can increase d without increasing Ntotal. Note that our verification protocol for CV graph states can also be generalized to CV weighted hypergraph states. Hypergraph states are generalizations of graph states, and “weighted” implies that a real number is associated with each hyperedge. The precise definition will be given in the “CV weighted hypergraph states” subsection in the RESULTS section. Several important CV states are weighted hypergraph states, such as the CV cluster state5 and the CV weighted toroidal lattice state,28 and our protocol is useful for verifying these states. We also point out that our verification protocol for CV graph states can be used to construct a verifiable blind quantum computing protocol with CV states. To the best of our knowledge, no verifiable blind CV quantum computing protocol was known previously except for the protocol of ref. 29. The protocol of ref. 29 assumes that the malicious server is restricted to preparing i.i.d. copies of single-qumode states while the malicious server in our protocol can perform any CPTP map as an attack.
Finally, our protocol is robust to some extent against slight perturbations of quantum states. For example, in previous protocols,13,15,16,17 all Ntotal − 1 registers have to pass a test in order for Alice to accept the remaining state as correct, which means that slightly perturbed but still useful states are rejected by Alice. In our protocol, on the other hand, Alice accepts even if some of the Ntotal − 1 registers fail a test. This relaxed acceptance criteria allows Alice to accept noisy but still useful resource states. As non-fault-tolerant small-scale quantum processors are becoming available,30,31,32 our protocols may be useful to verify these near-term quantum computers.
In addition to the verification protocols for graph states mentioned above, there are other approaches to verifiable quantum computing. The protocols in refs. 33,34 use trap based techniques to perform verifiable blind quantum computing. In their protocols, a client is required to prepare single-qubit states whereas single-qubit measurements are required in our setup. In order to make the client classical, several multi-server protocols have been proposed.35,36,37,38,39 Particularly, Coladangelo et al. have recently constructed two resource-efficient protocols for a classical client to verifiably delegate quantum computing to two non-communicating but entangled quantum servers.38 Other multi-server protocols have also been proposed to make verification protocols device independent.40,41 However, the assumption that servers do not communicate with each other is hard to impose in practice due to latency in real-world networks and the finite speed of quantum operations. Recently, Mahadev has shown that quantum computation can be verified by an entirely classical client even when only one quantum processor is available, under computational assumptions.42 Such protocols, however, necessitate extremely large quantum processors due to the relatively large key sizes necessary for cryptographic security.
Results
This section is organized as follows: first, as preliminaries, we review the definitions of qudit graph states and their stabilizer operators. Second, we construct a stabilizer test as a sub-protocol of our verification protocol. With respect to CV weighted hypergraph states, we also review their definitions and construct a stabilizer test. After that, based on the stabilizer tests, we propose our verification protocol, which is the main result of this paper. We also discuss the resource efficiency and the error tolerance of our verification protocol. Finally, we generalize our verification protocol so that it can be used to verify multiple quantum states simultaneously.
Qudit graph states
A graph G ≡ (V, E) is a pair of a set \(V \equiv \left\{ {v_i} \right\}_{i = 1}^n\) of vertices and a set \(E \equiv \left\{ {e_i} \right\}_{i = 1}^{|E|}\) of edges with n ≡ |V|. Here, |V| and |E| denote the number of elements of V and E, respectively. Let \(\left\{ {|k\rangle } \right\}_{k = 0}^{d - 1}\) be an orthonormal basis in a d-dimensional Hilbert space, where d( ≥ 2) is finite. A qudit graph state |Gd〉 that corresponds to G is defined by
where
is the +1 eigenvector of the generalized Pauli-X operator
and
is a qudit analogue of the controlled-Z (CZ) gate acting on the ith and the jth qudits. It is easy to confirm that when d = 2, a qudit graph state becomes a conventional qubit graph state. The ith stabilizer \(g_i^{(d)}\) (with 1 ≤ i ≤ n) of |Gd〉 is given by
where N(i) is the set of neighbors of the ith vertex, and
is the generalized Pauli-Z operator acting on the jth qudit. It is easy to check that \(g_i^{(d)}\left| {G_d} \right\rangle = \left| {G_d} \right\rangle\).
Stabilizer test for qudit graph states
Consider a stabilizer test which is an essential sub-protocol of our verification protocol for qudit graph states. Let ρ be an n-qudit quantum state. We define the stabilizer test for \(g_i^{(d)}\) on ρ as follows: Alice measures Xi and Zj for all j ∈ N(i). Let xi ∈ {0, …, d − 1} and zj ∈ {0, …, d − 1} be the measurement outcomes of Xi and Zj, respectively. We say that Alice passes the stabilizer test for \(g_i^{(d)}\) on ρ if
Since the correct qudit graph state |Gd〉 always satisfies Eq. (11), it passes the stabilizer test for \(g_i^{(d)}\) with unit probability for all i.
CV weighted hypergraph states
A weighted hypergraph G ≡ (V, E, Ω) is a triple of a set \(V \equiv \{ v_i\} _{i = 1}^n\) of vertices, a set \(E \equiv \left\{ {e_i} \right\}_{i = 1}^{|E|}\) of hyperedges, and a set \(\Omega \equiv \left\{ {\Omega _i} \right\}_{i = 1}^{|E|}\) of weights, where n ≡ |V|. Here, a hyperedge is a set of vertices, and \(\Omega _i \in {\Bbb R}\) represents the weight of the ith hyperedge. An edge is a special case of the hyperedge when |e| = 2, where |e| denotes the number of vertices linked to the hyperedge e. Let
be a CV weighted hypergraph state corresponding to G, where \(\left| {0_p} \right\rangle _{v_i}\) is a phase-squeezed state corresponding to the ith vertex, i.e., the eigenvector of the phase quadrature operator \(\hat p \equiv - i(\hat a - \hat a^\dagger )/\sqrt 2\) corresponding to the eigenvalue 0, \(\hat a\) \((\hat a^\dagger )\) is the boson annihilation (creation) operator,
is a CV analogue of the CZ gate acting on qumodes corresponding to vertices in the hyperedge ej, and \(\hat x_i \equiv (\hat a_i + \hat a_i^\dagger )/\sqrt 2\) is the amplitude quadrature operator acting on the ith qumode. From Eqs. (12) and (13), it can be seen that when |ej| = 2 for all j, a CV weighted hypergraph state becomes a CV weighted graph state. Since a hypergraph has at most 2n − 1 hyperedges, the time required to generate a hypergraph state is at most O(2n). Hereafter, we assume that |E| = poly(n), because states with superpolynomial scaling in n in general require greater than polynomial time to generate, which is considered inefficient. The ith stabilizer \(g_i^{({\mathrm{C}}V)}\) (with 1 ≤ i ≤ n) of |GCV〉 is defined by
where \(\hat p_i\) is the phase quadrature operator acting on the ith qumode. Let E(i) be the set of hyperedges that contain the ith vertex vi. From Eq. (14),
where we have used the Baker-Hausdorff lemma and the commutation relation \([\hat x,\,\hat p] = i\). It is easy to check that \(g_i^{({\mathrm{CV}})}\left| {G_{{\mathrm{CV}}}} \right\rangle = 0\left| {G_{{\mathrm{CV}}}} \right\rangle\). Since the quadrature operators can be measured using homodyne measurements, and Ω are known, the measurement of \(g_i^{({\mathrm{CV}})}\) can be accomplished using only homodyne measurements, which are single-qumode measurements.
Stabilizer test for CV weighted hypergraph states
The stabilizer test for CV weighted hypergraph states forms an essential sub-protocol of our CV verification protocol. Let ρ be an n-qumode quantum state. We define the stabilizer test for \(g_i^{({\mathrm{CV}})}\) on ρ as follows: Alice measures \(\hat p_i\) on the ith qumode and \(\hat x_k\) on all qumodes in \(\cup _{e_j \in E^{(i)}}e_j - \{ v_i\}\). Let \(p_i \in {\Bbb R}\) and \(x_k \in {\Bbb R}\) be the measurement outcomes of \(\hat p_i\) and \(\hat x_k\), respectively. We say that Alice passes the stabilizer test for \(g_i^{({\mathrm{CV}})}\) on ρ if
Here, we assume that measurements are infinitely accurate. However, as shown in the “Robustness” subsection in the RESULTS section, we can relax this assumption to some extent. Since we assume that |E| = poly(n), Alice can calculate the left-hand side of Eq. (16) in classical polynomial time. The correct CV weighted hypergraph state |GCV〉 passes the stabilizer test for \(g_i^{({\mathrm{CV}})}\) with unit probability for all i because the correct CV weighted hypergraph state |GCV〉 always satisfies Eq. (16).
Main protocol
Our verification protocol for qudit graph states (CV weighted hypergraph states) runs as follows (see Fig. 2):
-
1.
Bob sends an nNtotal-qudit (qumode) state ρB to Alice as shown in Fig. 1. The state ρB consists of Ntotal registers, and each register stores n qudits (qumodes). If Bob is honest, the state of each register is |Gd〉 (|GCV〉), i.e., \(\rho _B = \left| {G_d} \right\rangle \left\langle {G_d} \right|^{ \otimes N_{{\mathrm{total}}}}\) (\(\rho _B = \left| {G_{{\mathrm{CV}}}} \right\rangle \left\langle {G_{{\mathrm{CV}}}} \right|^{ \otimes N_{{\mathrm{total}}}}\)). On the other hand, if he is malicious, ρB can be any arbitrary state.
-
2.
Alice repeats the following for i = 1, …, n: she chooses Ntest registers from the remaining Ntotal − (i − 1)Ntest registers independently and uniformly at random, and then she performs the stabilizer tests for \(g_i^{(d)}\) \((g_i^{({\mathrm{CV}})})\) on each of them. Let Npass,i be the number of registers that pass the stabilizer test for \(g_i^{(d)}\) \((g_i^{({\mathrm{CV}})})\).
-
3.
Alice uniformly and randomly chooses a single register from the remaining Ntotal − nNtest registers that were not used for the stabilizer tests in step 2. We call the chosen single register the target register. Therefore, the averaged state of the target register is \(\rho _{{\mathrm{tgt}}} \equiv \mathop {\sum}\limits_i {\rho _i} /(N_{{\mathrm{total}}} - nN_{{\mathrm{test}}})\), where ρi is the ith remaining register. All the other Ntotal − nNtest − 1 registers are discarded.
-
4.
If
she uses the target register for her MBQC, otherwise she discards the target register.
The schematic shows our verification protocol. a The ideal case, i.e., \(\rho _B = \left| G \right\rangle \left\langle G \right|^{ \otimes N_{{\mathrm{total}}}}\), where |G〉 ∈ {|Gd〉, |GCV〉}. In this figure, |G〉 is represented by the five-vertex graph (n = 5). In the first repetition of step 2 of our protocol, Alice chooses Ntest registers uniformly and independently at random from Ntotal registers. The chosen Ntest registers are highlighted in green color. Alice performs the stabilizer test for \(g_1 \in \{ g_1^{(d)},g_1^{({\mathrm{CV}})}\}\) on each of these chosen green registers. In the second repetition of step 2 of our protocol, Alice chooses Ntest registers uniformly and independently at random from the remaining Ntotal − Ntest registers. These chosen Ntest registers are highlighted in blue color. Alice performs the stabilizer test for \(g_2 \in \{ g_2^{(d)},g_2^{({\mathrm{CV}})}\}\) on each of these chosen blue registers. Alice repeats the same procedure n times. In the n-th repetition, i.e., in the last repetition, Alice chooses Ntest registers uniformly and independently at random from the remaining Ntotal − (n − 1)Ntest registers. These chosen Ntest registers are highlighted in yellow color. Alice performs the stabilizer test for \(g_n \in \{ g_n^{(d)},g_n^{({\mathrm{CV}})}\}\) on each of these chosen yellow registers. Finally, Alice chooses one register, which we call the target register, from the remaining Ntotal − nNtest registers. The target register is highlighted in red color. If the results of the stabilizer tests satisfy a certain condition (see step 4 of our protocol), the state ρtgt of the target register is guaranteed to be close to |G〉 with high probability. b In general, ρB can be any nNtotal-qudit (qumode) state. The state ρB consists of Ntotal registers, and each register contains n qudits (qumodes). Each register is represented by a box. Any entanglement can be generated amongst registers, which is indicated by the purple “cloud” behind boxes
We will later show that our verification protocol gives the lower bound on the fidelity between the state ρtgt of the target register and the ideal graph state |Gd〉 (|GCV〉) (see Theorem 1).
Note that in the above protocol, no quantum memory is needed for Alice. This is because Bob sends each qubit of ρB one by one to Alice, and she randomly chooses her action from the stabilizer tests, MBQC on the target register, and discarding. Most importantly, our protocol does not assume any i.i.d. property on the quantum state ρB. In other words, ρB can be any state, and we do not assume that \(\rho _B = \sigma ^{ \otimes N_{{\mathrm{total}}}}\), where σ is an n-qudit (qumode) state.
To show that our protocol is valid, we now show its completeness and soundness. Intuitively, if Alice accepts the correct quantum state with high probability, we say that the verification protocol has the completeness. In other words, the completeness means that Alice does not mistakenly reject the correct quantum state. On the other hand, if the verification protocol guarantees that the accepted quantum state is close to the correct state with high probability, we say that the verification protocol has the soundness. That is, the soundness means that Alice does not mistakenly accept any quantum state that is far from the ideal state. It is not difficult to show the completeness of our protocol. In fact, when Bob is honest, i.e., when he sends \(\left| {G_d} \right\rangle ^{ \otimes N_{{\mathrm{total}}}}\) \((\left| {G_{{\mathrm{CV}}}} \right\rangle ^{ \otimes N_{{\mathrm{total}}}})\) to Alice, she uses the target register for her MBQC in step 4 with unit probability, because \(\mathop {\sum}\nolimits_{i = 1}^n {N_{{\mathrm{pass}},i}} = nN_{{\mathrm{test}}}\). With respect to the soundness, the following theorem holds:
Theorem 1
(Soundness) Let \(N_{\mathrm{pass}} \equiv \mathop {\sum}\nolimits_{i = 1}^n {N_{\mathrm{pass},i}}\). If we set Ntotal = 2nNtest and \(N_{\mathrm{test}} = \left\lceil {5n^4\log n/32} \right\rceil\), the n-qudit (qumode) averaged state ρtgt of the target register (over all random selections) satisfies, with probability at least 1 − n1−5c/64,
where \(\left\lceil \cdot \right\rceil\) is the ceiling function, c is any constant satisfying 64/5 < c < (n − 1)2/4, n ≥ 9, and |G〉 ∈ {|Gd〉, |GCV〉}.
We defer the detailed proof of Theorem 1 to the Supplementary Information Section A. A brief explanation of the proof is given in the METHODS section.
If Eq. (17) holds, Theorem 1 gives the non-trivial lower bound:
Hence Theorem 1 shows the soundness of our verification protocol.
Resource efficiency
To show the resource efficiency of our protocol, we compare it with the verification protocol of ref. 15, which can verify any graph state and is one of the most efficient protocols currently known. For simplicity, let us consider the situation where the quantum state ρB generated by Bob consists of Ntotal − 1 ideal states \(\left| G \right\rangle ^{ \otimes (N_{{\mathrm{total}}} - 1)}\) and a single incorrect n-qudit (qumode) state η. In other words, \(\rho _B = P[(\left| G \right\rangle \left\langle G \right|)^{ \otimes (N_{{\mathrm{total}}} - 1)} \otimes \eta ]\), where P is a permutation operator for registers. Bob knows that how P permutes \((\left| G \right\rangle \left\langle G \right|)^{ \otimes (N_{{\mathrm{total}}} - 1)} \otimes \eta\) while Alice does not. In this case, since Npass ≥ nNtest − 1 holds with unit probability, Eq. (19) holds with probability at least 1 − n1−5c/64. In order to satisfy this statement, our verification protocol requires \(N_{{\mathrm{total}}} = 2n\left\lceil {5n^4\log n/32} \right\rceil\) registers. The verification protocol of ref. 15 guarantees the fidelity 1 − 1/(αM) with probability at least 1 − α using (Ntotal = )M registers. Here, α is an upper bound on the probability of a quantum state whose fidelity is less than 1 − 1/(αM) being selected as the target register. Therefore, if we require the protocol of ref. 15 to achieve the same fidelity and the probability as ours,
have to be satisfied. From these equations, we obtain
For example, if c = 192, M = O(n15), which should be compared with our resource overhead Ntotal = O(n5 log n). In general, if c > 64, the order of M is larger than that of Ntotal, because if c > 64, M = O(nt) and
while Ntotal = O(n5 log n). (Note that n ≥ 18 is required to satisfy c > 64 because c < (n − 1)2/4). A similar argument holds for other previous protocols.13,14,16
The reason why our protocol is more efficient than that of ref. 15 can be explained as follows: the fidelity F′ = 1 − 1/(αM) of their protocol depends on M and α, and therefore, M has to be increased in order to decrease the order of α while keeping the order of 1 − F′ same. Our fidelity, \(F = 1 - (2\sqrt c + 1)/n\), also depends on Ntotal and the probability, because n does, but our fidelity also contains the constant c, which is independent of Ntotal. Therefore, by increasing c instead of increasing Ntotal, we can improve the order of the probability without increasing the order of 1−F. The existence of such an extra parameter c is the advantage of using Serfling’s bound. (The constant c comes from ν of Serfling’s bound via \(\nu = \sqrt c /n^2\)). Note that in general, it is difficult to compare our protocol with previous protocols without performing experiments. This is because the parameter Npass in Theorem 1 is determined by experiment. In addition, it is also difficult to compare our protocol with other approaches mentioned in the last paragraph in the INTRODUCTION section. This is because their definitions of the soundness (verifiability) is different from ours. Our definition of the soundness relies on the fidelity between the ideal resource state and the actual one. On the other hand, their definitions do not (directly) rely on the fidelity.
Robustness
To investigate the error tolerance of our protocol, consider a simple example where all registers of ρB are in the same state σ, and the state σ is a slightly deviated state from the ideal state |G〉:
where \(0 \,<\, \epsilon\, <\, 1\), and η is any n-qudit (qumode) state. In other words,
When \(\epsilon = 1/{\mathrm{poly}}(n)\), such σ is still useful for quantum computing, because
where ||·|| is the trace norm, for any positive operator-valued measure (POVM) element A. Therefore, the output probability distribution of MBQC on σ is close to that on |G〉 within the 1/poly(n) error, which is sufficient enough to solve, for example, bounded error quantum polynomial time (BQP) decision problems.
When \(\epsilon\, <\, O(1/(n^5\log n))\), our protocol can accept ρB of Eq. (24) with almost unit probability. In fact, by a direct calculation, our protocol accepts ρB with the probability
where \(\left\lfloor \cdot \right\rfloor\) is the floor function. From \(p_{{\mathrm{acc}}}\, >\, (1 - \epsilon )^{nN_{{\mathrm{test}}}}\) and nNtest = O(n5 log n), if \(\epsilon\, <\, O(1/(n^5\log n))\), pacc approaches 1 in the limit of large n.
The acceptance probability pacc of our protocol is higher than that of ref. 15, suggesting that our protocol is more robust than that of ref. 15. In fact, the protocol of ref. 15 accepts ρB of Eq. (24) with the probability
Therefore, if c > 64,
where we have used Eq. (26) and the fact that nNtest ≤ M − 1, which is asymptotically true for large n when c > 64, because nNtest = Ntotal/2 = O(n5 log n) and M = O(nt) where t > 5 from Eq. (22).
For simplicity, we have considered the tensor product of the same state σ as shown in Eq. (24). However, it is easy to confirm that a similar argument holds even when small entanglement is created among registers of ρB. Furthermore, since the errors considered above can also be treated as errors in measurements, we can relax the assumption where measurements are ideal to some extent.
Verification of multiple quantum states
In step 3 of our protocol, Alice chooses a single register, which we call the target register. What happens if she chooses \(\tilde n\) registers, instead of a single register? We can show the following theorem:
Theorem 2
Let \(N_{{\mathrm{pass}}} \equiv \mathop {\sum}\nolimits_{i = 1}^n {N_{{\mathrm{pass}},i}}\). If we set Ntotal = 2nNtest and \(N_{{\mathrm{test}}} = \left\lceil {5n^4\log n/32} \right\rceil\), the averaged state \(\tilde \rho _{{\mathrm{tgt}}}\) of \(\tilde n\) target registers (over all random selections) satisfies, with probability at least 1 − n1−5c/64,
where \(\left\lceil \cdot \right\rceil\) is the ceiling function, c is any constant satisfying \(64/5 \,< \,c \,< \,[n/\tilde n - 32(\tilde n - 1)/(5\tilde nn^4\log n) - 1]^2/4\), \(n \ge 9\tilde n\), \(\tilde n = O(n^t)\), t < 1, and |G〉 ∈ {|Gd〉, |GCV〉}.
If Eq. (17) holds, Theorem 2 gives the non-trivial lower bound:
Note that setting \(\tilde n = 1\) in Theorem 2 results in Theorem 1. This implies that Theorem 1 is a special case of Theorem 2. In several tasks, such as sampling problems, Alice would like to have several copies of graph states. Theorem 2 is useful in such situations. In simple terms, Eq. (30) implies that Alice can obtain \(\tilde n = O(n^t)\) quantum states with the fidelity 1 − O(1/n1–t) using Ntotal = O(n5 log n) registers. For verifying a single quantum state, the resource overhead O(n5−t log n) of our protocol is almost the same as that O(n4 log n) of some previous device-independent multi-server verification protocols.40,41 Particularly, in the protocol of ref. 40, the Azuma-Hoeffding bound43,44 is used to achieve such overhead while we use Serfling’s bound. A proof of Theorem 2 is provided in the Supplementary Information Section B.
Discussion
We have proposed an efficient and robust verification protocol for any qudit graph state and any polynomial-time-generated CV weighted hypergraph state using Serfling’s bound. Our protocol is much more efficient than the existing verification protocols when the size of the quantum state, the guaranteed fidelity, and the probability are sufficiently large.
Our analysis which is based on Serfling’s bound is not directly applicable to the verification protocols for qubit hypergraph states.11,12,16 This is mainly due to two reasons: (a) in our analysis, the required number Ntotal of registers is proportional to the number of measurement settings, which is n in our case. However, in some existing protocols,11,12 the number of settings is more than poly(n). (b) The ratio of the number of randomly chosen registers in step 3 to that of the remaining registers must be less than O(1/(n4 log n)). This is crucial in order for Theorems 1 and 2 to work. In an existing protocol,16 the number of the remaining (unmeasured) register is only one. It would be interesting to apply our analysis to these existing verification protocols11,12,16 by appropriately modifying them. However, we leave this as an open problem for further research.
If the open problem will be solved, our analysis would become more attractive. This is because hypergraph states are also resource states of MBQC.8,45 Particularly, in ref. 45, a hypergraph state \(\left| {G_n^d} \right\rangle\) has been constructed such that it enables to perform universal MBQC with only Pauli-X and Z basis measurements. Note that the CV analogue of \(\left| {G_n^d} \right\rangle\) can be efficiently verified using our protocol presented in this paper. This is because a CV hypergraph state is a special case of CV weighted hypergraph states.
Besides an application to the verification of universal quantum computing, our protocol can be applied to the verifiable blind quantum computing (VBQC) scenario. In VBQC, a client with weak quantum resources delegates an arbitrary quantum computing to a remote (universal) quantum server in such a way that the client’s privacy is preserved and at the same time the integrity of the server is verified. Almost all of the VBQC protocols can be divided into two types, i.e., remote state preparation (RSP) type33 and measurement-only (MO) type.13 In the former type, the client is required to prepare single- or multi-qubit quantum states. On the other hand, in the latter one, the client is required to perform single-qubit projective measurements on the quantum states (usually graph states). A non-verifiable blind quantum computing (BQC) protocol using CV graph states has already been proposed for both types,46 but a VBQC protocol using CV graph states has not yet been proposed. In this paper, we focus on the MO type because the homodyne measurement is generally considered to be significantly easier than the generation of highly squeezed states. By combining the original MO-type BQC protocol10 with our verification protocol of CV weighted hypergraph states, we construct a MO-type CV VBQC protocol as follows:
-
1.
The quantum server generates Ntotal CV cluster states,5 and sends them to the client.
-
2.
The client performs our CV verification protocol. If the verification protocol succeeds (If Eq. (17) holds), they proceed to the next step. Otherwise, the client aborts the protocol.
-
3.
The client performs MBQC on the verified quantum states.
Note that this VBQC protocol requires no quantum memory for the client. Although the protocol above is phrased sequentially, when no quantum memory is used, the computation is actually interspersed with the test runs which themselves take place out of order. The decision to accept or reject is taken once all qumodes have been measured or discarded.
From the universality of the CV cluster state, it follows that our CV VBQC protocol has perfect correctness, i.e., the client can obtain the correct result if the server is honest. Next, our protocol is blind, i.e., the server cannot learn client’s inputs, algorithms, and outputs, because there does not exist any communication channel from the client to the server. Finally, the verifiability of our VBQC protocol follows from our CV verification protocol given in the RESULTS section.
In our CV VBQC protocol, we assume that the honest server sends the client an ideal CV graph state whose squeezing level is infinite. One possible approach to relax this assumption is to construct a test where even finitely squeezed states can pass with sufficiently high probability. Recently, Liu et al. have constructed a fidelity witness with respect to the tensor products of finitely squeezed cubic phase states.29 Based on this fidelity witness, they have also proposed another CV VBQC protocol. Therefore, their VBQC protocol does not need infinitely squeezed states unlike our VBQC protocol. On the other hand, their protocol assumes that the malicious server is restricted to preparing i.i.d. copies of single-qumode states while the malicious server in our protocol can perform any CPTP map as the attack. It would be interesting to combine these two approaches to design better and more practical CV VBQC protocols.
Methods
In this section, we provide the primary mathematical tool used in the proof of Theorem 1 and an intuitive explanation of the proof. Our main tool is Serfling’s bound:
Lemma 1
(Serfling's bound 23,24) Consider a set of binary random variables Y = (Y1, Y2, …, YT) with Yj taking values in {0, 1} and T = N + K. Then, for any 0 < ' ν< 1,
where Π is a set of K samples chosen independently and uniformly at random from Y without replacement. \(\bar {\Pi}\) is the complementary set of Π.
Note that the sampling without replacement means that once a sample is selected, it is removed from the population in all subsequent selections.
In step 2 of our protocol, when i = 1, Alice measures the stabilizer operator \(g_1 \in \{ g_1^{(d)},g_1^{({\mathrm{CV}})}\}\) for Ntest samples of the set Π(1) that is uniformly and randomly chosen out of the total Ntotal registers. In this case when Alice passes the stabilizer test for g1 on the jth register (1 ≤ j ≤ Ntest), Yj = 0; else Yj = 1. Therefore, by setting K = Ntest and T = Ntotal in Lemma 1, it reveals the upper bound
on the number of registers that are not stabilized by g1 in the remaining complementary set \(\bar {\Pi}^{(1)}\), which includes Ntotal − Ntest registers (for details, see the second paragraph of the proof in the Supplementary Information Section A).
Next, Alice performs the stabilizer tests for g2 (when i = 2) by uniformly and randomly choosing Ntest registers, which are in the set Π(2), from Ntotal − Ntest remaining registers. Similarly, in Lemma 1, by setting K = Ntotal and T = Ntotal − Ntest, Alice can estimate that at most
registers are not stabilized by g2 in the remaining Ntotal − 2Ntest registers that are not measured by g1 and g2.
From Eqs. (32) and (33), we find a lower bound
on the number of remaining Ntotal − 2Ntest registers that are stabilized by both g1 and g2. In estimating this lower bound, we use the pigeonhole principle. In other words, we consider a worst case scenario where the remaining registers that are not stabilized by g1 and g2 do not completely overlap with each other.
Using the same argument recursively, Alice estimates a lower bound on the number of the remaining registers stabilized by all of \(\left\{ {g_i} \right\}_{i = 1}^n\) in the remaining Ntotal − nNtest registers. Since only the ideal state |G〉 is stabilized by all the gi with 1 ≤ i ≤ n, this bound gives a lower bound \(N_{{\mathrm{cor}}}^{\mathrm{L}}\) on the number of the ideal states in the remaining registers. If \(N_{{\mathrm{cor}}}^{\mathrm{L}}/(N_{{\mathrm{total}}} - nN_{{\mathrm{test}}})\) is large, the averaged fidelity of the target register is also large because Alice finally selects one registers uniformly at random from the remaining registers.
Data availability
No data sets were generated or analyzed during the current study.
References
Raussendorf, R. & Briegel, H. J. A one-way quantum computer. Phys. Rev. Lett. 86, 5188 (2001).
Raussendorf, R., Browne, D. & Briegel, H. J. Measurement-based quantum computation on cluster states. Phys. Rev. A 68, 022312 (2003).
Zhou, D. L., Zeng, B., Xu, Z. & Sun, C. P. Quantum computation based on d-level cluster state. Phys. Rev. A 68, 062303 (2003).
Hein, M., Eisert, J. & Briegel, H. J. Multiparty entanglement in graph states. Phys. Rev. A 69, 062311 (2004).
Menicucci, N. C. et al. Universal quantum computation with continuous-variable cluster states. Phys. Rev. Lett. 97, 110501 (2006).
Gross, D. & Eisert, J. Novel schemes for measurement-based quantum computation. Phys. Rev. Lett. 98, 220503 (2007).
Raussendorf, R., Harrington, J. & Goyal, K. Topological fault-tolerance in cluster state quantum computation. New J. Phys. 9, 199 (2007).
Miller, J. & Miyake, A. Hierarchy of universal entanglement in 2D measurement-based quantum computation. npj Quant. Info. 2, 16036 (2016).
Broadbent, A., Fitzsimons, J. & Kashefi, E. Universal Blind Quantum Computation. In Proc. of the 50th Annual Symposium on Foundations of Computer Science 517–526 (FOCS, Los Alamitos, USA, 2009).
Morimae, T. & Fujii, K. Blind quantum computation protocol in which Alice only makes measurements. Phys. Rev. A 87, 050301(R) (2013).
Morimae, T., Takeuchi, Y. & Hayashi, M. Verification of hypergraph states. Phys. Rev. A 96, 062321 (2017).
Takeuchi, Y. & Morimae, T. Verification of many-qubit states. Phys. Rev. X 8, 021060 (2018).
Hayashi, M. & Morimae, T. Verifiable measurement-only blind quantum computing with stabilizer testing. Phys. Rev. Lett. 115, 220502 (2015).
Fujii, K. & Hayashi, M. Verifiable fault tolerance in measurement-based quantum computation. Phys. Rev. A 96, 030301(R) (2017).
Markham, D. & Krause, A. A simple protocol for certifying graph states and applications in quantum networks. arXiv:1801.05057 (2018).
Zhu, H. & Hayashi, M. Efficient verification of hypergraph states. arXiv:1806.05565 (2018).
Sato, G., Koshiba T. & Morimae T. Arbitrable blind quantum computation. arXiv:1709.10420 (2017).
McKague, M. Self-testing graph states. In Conference on Quantum Computation, Communication, and Cryptography 104–120 (Springer, Berlin, 2011).
Li, K. & Smith, G. Quantum de Finetti theorem under fully-one-way adaptive measurements. Phys. Rev. Lett. 114, 160503 (2015).
Dada, A. C., Leach, J., Buller, G. S., Padgett, M. J. & Andersson, E. Experimental high-dimensional two-photon entanglement and violations of generalized Bell inequalities. Nat. Phys. 7, 677 (2011).
Gottesman, D., Kitaev, A. & Preskill, J. Encoding a qubit in an oscillator. Phys. Rev. A 64, 012310 (2001).
Yokoyama, S. et al. Ultra-large-scale continuous-variable cluster states multiplexed in the time domain. Nat. Photon. 7, 982 (2013).
Serfling, R. J. Probability inequalities for the sum in sampling without replacement. Ann. Stat. 2, 39 (1974).
Tomamichel, M. & Leverrier, A. A largely self-contained and complete security proof for quantum key distribution. Quantum 1, 14 (2017).
Furrer, F. et al. Continuous variable quantum key distribution: finite-key analysis of composable security against coherent attacks. Phys. Rev. Lett. 109, 100502 (2012).
Lim, C. C. W., Portmann, C., Tomamichel, M., Renner, R. & Gisin, N. Device-independent quantum key distribution with local bell. Test. Phys. Rev. X 3, 031006 (2013).
Pfister, C., Rol, M. A., Mantri, A., Tomamichel, M. & Wehner, S. Capacity estimation and verification of quantum channels with arbitrary correlated errors. Nat. Commun. 9, 27 (2018).
Menicucci, N. C., Flammia, S. T. & Pfister, O. One-way quantum computing in the optical frequency comb. Phys. Rev. Lett. 101, 130501 (2008).
Liu, N., Demarie, T. F., Tan, S.-H., Aolita, L. & Fitzsimons, J. F. Client-friendly continuous-variable blind and verifiable quantum computing. In Proc. SPIE 10803 108030J (SPIE, Berlin, Germany, 2018).
Ozaeta, A. & McMahon, P. L. Decoherence of up to 8-qubit entangled states in a 16-qubit superconducting quantum processor. arXiv:1712.07080 (2017).
Ferrari, D. & Amoretti, M. Efficient and effective quantum compiling for entanglement-based machine learning on IBM Q devices. Int. J. Quantum Inform. 16, 1840006 (2018).
Wang, Y., Li, Y., Yin, Z.-q & Zeng, B. 16-qubit IBM universal quantum computer can be fully entangled. npj Quant. Info. 4, 46 (2018).
Fitzsimons, J. F. & Kashefi, E. Unconditionally verifiable blind quantum computation. Phys. Rev. A 96, 012303 (2017).
Aharonov, D., Ben-Or, M., Eban, E. & Mahadev, U. Interactive proofs for quantum computations. arXiv:1704.04487 (2017).
Reichardt, B. W., Unger, F. & Vazirani, U. Classical command of quantum systems. Nature 496, 456–460 (2013).
McKague, M. Interactive proofs for BQP via self-tested graph states. Theory of Comput. 12, 1–42 (2016).
Natarajan, A. & Vidick, T. Robust self-testing of many-qubit states. In Proc. of the 49th Annual ACM SIGACT Symposium on Theory of Computing 1003–1015 (ACM, Montreal, Canada, 2017).
Coladangelo, A., Grilo, A., Jeffery, S. & Vidick, T. Verifier-on-a-Leash: new schemes for verifiable delegated computation, with quasilinear resources. arXiv:1708.07359 (2017).
Fitzsimons, J. F., Hajdušek, M. & Morimae, T. Post hoc Verification of Quantum Computation. Phys. Rev. Lett. 120, 040501 (2018).
Hajdušek, M., Pérez-Delgado, C. A. & Fitzsimons. J. F. Device-independent verifiable blind quantum computation. arXiv:1502.02563 (2015).
Hayashi, M. & Hajdušek, M. Self-guaranteed measurement-based quantum computation. Phys. Rev. A 97, 052308 (2018).
Mahadev, U. Classical verification of quantum computations. In Proc. of the 59th Annual Symposium on Foundations of Computer Science 259–267 (FOCS, Paris, France, 2018).
Hoeffding, W. Probability inequalities for sums of bounded random variables. J. Am. Stat. Assoc. 58, 13–30 (1963).
Azuma, K. Weighted sums of certain dependent random variables. Tohoku Math. J. Sec. Ser. 19, 357–367 (1967).
Takeuchi, Y., Morimae, T. & Hayashi, M. Quantum computational universality of hypergraph states with Pauli-X and Z basis measurements. arXiv:1809.07552 (2018).
Morimae, T. Continuous-Variable Blind Quantum Computation. Phys. Rev. Lett. 109, 230502 (2012).
Acknowledgements
We thank Seiseki Akibue for helpful discussions. Y.T. is supported by the Program for Leading Graduate Schools: Interactive Materials Science Cadet Program. T.M. is supported by JST ACT-I No.JPMJPR16UP, the JSPS Grant-in-Aid for Young Scientists (B) No.JP17K12637, and JST PRESTO No.JPMJPR176A. A.Mantri is supported by SUTD President’s Graduate Fellowship. A. Mantri and J.F.F. acknowledges support from Singapore’s Ministry of Education and National Research Foundation, the ANR-NRF grant NRF2017-NRF-ANR004, and the US Air Force Office of Scientific Research under AOARD grant FA2386-15-1-4082. This material is based on research funded in part by the Singapore National Research Foundation under NRF Award NRF-NRFF2013-01.
Author information
Authors and Affiliations
Contributions
Y.T. conceived the key idea through discussions with A.Mantri and A.Mizutani. Y.T. refined the key idea through discussions with A.Mantri, T.M. and J.F.F. Y.T. performed the calculations, and all the authors contributed to checking the validity of the calculations and writing of the paper.
Corresponding author
Ethics declarations
Competing interests
J.F.F. has financial holdings in Horizon Quantum Computing Pte. Ltd. Remaining authors declare no competing interests.
Additional information
Publisher’s note: Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Takeuchi, Y., Mantri, A., Morimae, T. et al. Resource-efficient verification of quantum computing using Serfling’s bound. npj Quantum Inf 5, 27 (2019). https://doi.org/10.1038/s41534-019-0142-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41534-019-0142-2
This article is cited by
-
Robust and efficient verification of graph states in blind measurement-based quantum computation
npj Quantum Information (2023)
-
Public verifiable measurement-only blind quantum computation based on entanglement witnesses
Quantum Information Processing (2023)
-
Quantum certification and benchmarking
Nature Reviews Physics (2020)
-
Towards the standardization of quantum state verification using optimal strategies
npj Quantum Information (2020)
-
Secure Two-Party Computation Based on Blind Quantum Computation
International Journal of Theoretical Physics (2020)