Abstract
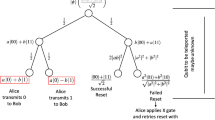
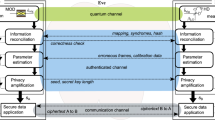
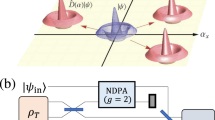
Quantum cryptography has recently been extended to continuous-variable systems, such as the bosonic modes of the electromagnetic field possessing continuous degrees of freedom. In particular, several cryptographic protocols have been proposed and experimentally implemented using bosonic modes with Gaussian statistics. These protocols have shown the possibility of reaching very high secret key rates, even in the presence of strong losses in the quantum communication channel. Despite this robustness to loss, their security can be affected by more general attacks where extra Gaussian noise is introduced by the eavesdropper. Here, we show a ‘hardware solution’ for enhancing the security thresholds of these protocols. This is possible by extending them to two-way quantum communication where subsequent uses of the quantum channel are suitably combined. In the resulting two-way schemes, one of the honest parties assists the secret encoding of the other, with the chance of a non-trivial superadditive enhancement of the security thresholds. These results should enable the extension of quantum cryptography to more complex quantum communications.
This is a preview of subscription content, access via your institution
Access options
Subscribe to this journal
Receive 12 print issues and online access
$209.00 per year
only $17.42 per issue
Buy this article
- Purchase on Springer Link
- Instant access to full article PDF
Prices may be subject to local taxes which are calculated during checkout





Similar content being viewed by others
References
Braunstein, S. L. & Pati, A. K. Quantum Information Theory with Continuous Variables (Kluwer–Academic, Dordrecht, 2003).
Braunstein, S. L. & van Loock, P. Quantum information with continuous variables. Rev. Mod. Phys. 77, 513–577 (2005).
Eisert, J. & Plenio, M. B. Introduction to the basics of entanglement theory in continuous-variable systems. Int. J. Quantum Inf. 1, 479–506 (2003).
Ferraro, A., Olivares, S. & Paris, M. G. A. Gaussian States in Quantum Information (Bibliopolis, Napoli, 2005).
Hillery, M. Quantum cryptography with squeezed states. Phys. Rev. A 61, 022309 (2000).
Ralph, T. C. Continuous variable quantum cryptography. Phys. Rev. A 61, 010303(R) (2000).
Ralph, T. C. Security of continuous-variable quantum cryptography. Phys. Rev. A 62, 062306 (2000).
Reid, M. D. Quantum cryptography with a predetermined key, using continuous-variable Einstein–Podolsky–Rosen correlations. Phys. Rev. A 62, 062308 (2000).
Gottesman, D. & Preskill, J. Secure quantum key distribution using squeezed states. Phys. Rev. A 63, 022309 (2001).
Cerf, N. J., Lévy, M. & Van Assche, G. Quantum distribution of Gaussian keys using squeezed states. Phys. Rev. A 63, 052311 (2001).
Grosshans, F. & Grangier, Ph. Continuous variable quantum cryptography using coherent states. Phys. Rev. Lett. 88, 057902 (2002).
Grosshans, F. et al. Quantum key distribution using Gaussian-modulated coherent states. Nature 421, 238–241 (2003).
Iblisdir, S., Van Assche, G. & Cerf, N. J. Security of quantum key distribution with coherent states and homodyne detection. Phys. Rev. Lett. 93, 170502 (2004).
Grosshans, F. & Cerf, N. J. Continuous-variable quantum cryptography is secure against non-Gaussian attacks. Phys. Rev. Lett. 92, 047905 (2004).
Weedbrook, C. et al. Quantum cryptography without switching. Phys. Rev. Lett. 93, 170504 (2004).
Lance, A. M. et al. No-switching quantum key distribution using broadband modulated coherent light. Phys. Rev. Lett. 95, 180503 (2005).
Silberhorn, Ch. et al. Continuous variable quantum cryptography: Beating the 3 dB loss limit. Phys. Rev. Lett. 89, 167901 (2002).
Namiki, R. & Hirano, T. Practical limitation for continuous-variable quantum cryptography using coherent states. Phys. Rev. Lett. 92, 117901 (2004).
Namiki, R. & Hirano, T. Security of continuous-variable quantum cryptography using coherent states: Decline of postselection advantage. Phys. Rev. A 72, 024301 (2005).
Namiki, R. & Hirano, T. Efficient-phase-encoding protocols for continuous-variable quantum key distribution using coherent states and postselection. Phys. Rev. A 74, 032302 (2006).
Heid, M. & Lütkenhaus, N. Efficiency of coherent-state quantum cryptography in the presence of loss: Influence of realistic error correction. Phys. Rev. A 73, 052316 (2006).
Grosshans, F., Cerf, N. J., Wenger, J., Tualle-Brouri, R. & Grangier, Ph. Virtual entanglement and reconciliation protocols for quantum cryptography with continuous variables. Quantum. Inf. Comput. 3, 535–552 (2003).
Van Assche, G., Cardinal, J. & Cerf, N. J. Reconciliation of a quantum-distributed Gaussian key. IEEE Trans. Inf. Theory 50, 394–400 (2004).
Navascués, M., Grosshans, F. & Acín, A. Optimality of Gaussian attacks in continuous-variable quantum cryptography. Phys. Rev. Lett. 97, 190502 (2006).
García-Patrón, R. & Cerf, N. J. Unconditional optimality of Gaussian attacks against continuous-variable quantum key distribution. Phys. Rev. Lett. 97, 190503 (2006).
Renner, R., Gisin, N. & Kraus, B. Information-theoretic security proof for quantum-key-distribution protocols. Phys. Rev. A 72, 012332 (2005).
Renner, R. Security of Quantum Key Distribution. PhD thesis, Swiss Federal Institute of Technology (ETH) Zurich (2005).
Lodewyck, J. & Grangier, Ph. Tight bound on coherent states quantum key distribution with heterodyne detection. Phys. Rev. A 76, 022332 (2007).
Sudjana, J., Magnin, L., García-Patrón, R. & Cerf, N. J. Tight bounds on the eavesdropping of a continuous-variable quantum cryptographic protocol with no basis switching. Phys. Rev. A 76, 052301 (2007).
Grosshans, F. Collective attacks and unconditional security in continuous variable quantum key distribution. Phys. Rev. Lett. 94, 020504 (2005).
Navascués, M. & Acín, A. Security bounds for continuous variables quantum key distribution. Phys. Rev.Lett. 94, 020505 (2005).
Dušek, M., Haderka, O., Hendrych, M. & Myška, R. Quantum identification system. Phys. Rev. A 60, 149–156 (1999).
Acknowledgements
The research of S.P. was supported by a Marie Curie Outgoing International Fellowship within the 6th European Community Framework Programme (Contract No. MOIF-CT-2006-039703). S.P. thanks CNISM for hospitality at Università di Camerino and Gaetana Spedalieri for her moral and logistic support. S.L. was supported by the W.M. Keck centre for extreme quantum information processing (xQIT).
Author information
Authors and Affiliations
Corresponding author
Supplementary information
Supplementary Information
Supplementary Information and Supplementary Figures 1 and 2 (PDF 201 kb)
Rights and permissions
About this article
Cite this article
Pirandola, S., Mancini, S., Lloyd, S. et al. Continuous-variable quantum cryptography using two-way quantum communication. Nature Phys 4, 726–730 (2008). https://doi.org/10.1038/nphys1018
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1038/nphys1018
This article is cited by
-
How to verify identity in the continuous variable quantum system?
Quantum Information Processing (2023)
-
The Emerging Trends of Quantum Computing Towards Data Security and Key Management
Archives of Computational Methods in Engineering (2021)
-
Continuous-variable source-device-independent quantum key distribution against general attacks
Scientific Reports (2020)
-
Continuous-variable measurement-device-independent quantum key distribution via quantum catalysis
Quantum Information Processing (2020)
-
Statistical quadrature evolution by inference for multicarrier continuous-variable quantum key distribution
Quantum Studies: Mathematics and Foundations (2020)