Abstract
Universality is an important feature, but less researched in quantum communication protocols. In this paper, a kind of universal quantum secret sharing protocol is investigated. Firstly, we design a quantum secret sharing protocol based on the Borras-Plastino-Batle (BPB) state. Departing from previous research, our protocol has a salient feature in that participants in our protocol only need projective measurement instead of any unitary operations. It makes our protocol more flexible. Secondly, universality of quantum communication protocols is studied for the first time. More specifically, module division of quantum communication protocols and coupling between different modules are discussed. Our aforementioned protocol is analyzed as an example. On one hand, plenty of quantum states (the BPB-class states and the BPB-like-class states, which are proposed in this paper) could be used as carrier to perform our protocol. On the other hand, our protocol also could be regarded as a quantum private comparison protocol with a little revision. These features are rare for quantum communication protocols, and make our protocol more robust. Thirdly, entanglements of the BPB-class states are calculated in the Appendix.
Similar content being viewed by others
Introduction
In secret sharing problem, a boss wants to split his secret into several parts, and distribute them to various agents. The secret could be reconstructed by sufficient number of agents. These agents need to cooperate with each other. Classical secret sharing problem is independently introduced by Shamir1 and Blakley2 in 1979. Quantum secret sharing (QSS) is the quantum version solution of secret sharing problem. Players utilize some necessary quantum technique to achieve the goal. Importantly, quantum mechanics provides the possibility of designing unconditionally secure protocols3,4.
There are two branches in QSS protocols. The first one is sharing classical information. In 1999, Hillery et al.5 proposed a QSS scheme with the Greenberger-Horne-Zeilinger (GHZ) state. Later, Guo et al. considered a QSS protocol without entanglement6. In this protocol, only product states are employed. After that, Xiao et al.7 generalized Hillery’s scheme5 into arbitrary multi-parties, and also increased the efficiency of their scheme. In 2005, a QSS between multiparty (m members in group 1) and multiparty (n members in group 2) without entanglement was investigated by Yan et al.8. Only single photons are used in the protocol. The secret message shared by all members of group 1 is shared by all members of group 2. Only the entire set of each group (not only group 1 but also group 2) is efficient to read the secret message. Afterwards, a dynamic QSS protocol was considered9. The secret is shared between a sender and a dynamic agent group. Dynamic schemes are more flexible and suitable for practical applications. In the same year, Long et al.10 designed a QSS protocol via the BPB state. In the protocol, the boss owns three particles in one state, while each of three agents only owns one. Unfortunately, Qin et al.11 found that the information leakage exists in above protocol. Then, Dehkordi et al.12 designed a (t, m) − (s, n) threshold QSS scheme between multiparty (m members in group 1) and multiparty (n members in group 2) using GHZ state. Threshold scheme is useful and efficient when parties are not all present. Recently, a QSS protocol based on local distinguishability is proposed13. The protocol also is a (k, n) threshold scheme (k = 2 or  ).
).
The other branch is sharing quantum information, i.e., quantum state. This kind of protocol is also be called as quantum state sharing (QSTS). Cleve et al.14 firstly introduced the concept of QSTS in 1999. Later, a multi-party m-particles separable state sharing protocol was studied by Yang et al.15. A short time ago, a sequential multi-qubit secret sharing protocol was given by Ray et al.16. The sequential secret sharing means that the dealer can add some secret states in the middle of processes, without performing the protocol again.
Lately, Zhang et al. designed a quantum summation protocol17 and quantum private comparison (QPC) protocol18 based on the BPB state, respectively. If each of three participants measures two particles respectively in one BPB state, three results are relevant. This correlation is the key of these two protocols. It also ensures the correctness and security of the protocols.
The universality is one of the crucial characters in practical situation. In computer science, universality is researched and shown in the form of module division19,20. Concretely, a system is divided into different modules, coupling is the degree of interdependence between different modules. In a well-designed system, one module should not be strongly connected with the others. When the other modules are determined, this module is better to be alterable. Lowering coupling will reduce the connection of different modules, and the impact of revising one module to the whole system. It makes the system more robust.
For a quantum communication protocol, state is regarded as a part of modules. If a protocol can be performed by different states, it’s universal. In 2014, we21 considered the universality of a QPC protocol originally. Concretely, we discussed how to perform one protocol in different quantum states. We researched the symmetry of some quantum states, and proposed a class of QPC protocols based on it21. This is the first universal QPC protocol class, and it is easy to be performed in the existing technical condition. The protocol which belongs to this class can be performed by lots of symmetrical states with a little revision.
Entanglement is one of the most important property of quantum mechanics and quantum information processing. Entanglement channel is an important tool for quantum information processing5,7,13,21. Highly entangled states are vital for the establishment of entanglement channel. For bipartite quantum state, entanglement can be easily calculated by reduced density matrix and von Neumann entropy. However, there is no recognized method to calculate the entanglement of a multipartite state. In 2005, Eisert et al.22 summarized some candidate methods of multi-particle entanglement. One of the candidates is proposed by Wei et al.23. They utilized the geometric measure to describe the multi-particle entanglement.
In this paper, we firstly follow the works in refs 17, 18, and design a QSS protocol based on the BPB state. In our protocol, the correlation of the measurement result is also exploited. What’s more, the boss only need to prepare the quantum state, transport the state to Alice and Bob, and perform measurement. While, agents only need to perform measurement. The procedures are simple, and easy to be achieved under current conditions.
Secondly, we research the universality of quantum communication protocols in detail. First of all, module division of quantum communication protocol is proposed. There are seven modules in total. Coupling of different modules are discussed. Some existing protocols are analyzed as example. We say that if coupling of different modules in a protocol is low, the protocol is universal. Subsequently, peculiarity of the BPB state is studied, and the BPB-class/BPB-like-class states are proposed correspondingly. In these two classes, all of states have the similar form, which are detailed in equation (7) and (10). We extend aforementioned protocol into a class of QSS protocols based on the BPB-class/BPB-like-class states. This is the first universal QSS protocol class. The protocol can be performed by lots of states. All the states of the above two classes, can be utilized to perform the protocol perfectly. Next, we discuss the relation of the QPC protocol18 to our QSS protocol. We find that the private comparison is the inverse process of secret sharing in a way. If we have designed a QPC protocol, it may be easy to infer a QSS protocol. It shows that our protocol can be utilized to accomplish the task of QPC or QSS with a little alteration. Through these analysis, we find that our protocol has low coupling, and is robust.
Thirdly, entanglements of the six-particle BPB-class states are investigated by pseudo entanglement and Wei’s tool23 respectively. Pseudo entanglement is introduced by ourselves and inspired by the way to calculate the entanglement of bipartite quantum state. Detailed calculation is given in Supplementary Information.
Results
A new quantum secret sharing protocol based on |Ψ6qb〉
Preliminaries
In 2007, Borras et al.24 discovered a new six-particle state, which is maximum entangled (it’s called BPB state for short). The state is known as

This state can be rewritten in X basis as:

For further research, the state could also be rewritten as

Here,

are Bell states. These four states can be used to construct an orthonormal basis, i.e., Bell basis.
We can encode four Bell states into two classical bits:

Furthermore, according to Eq. (3), if we measure the (1-st, 2-nd), (3-rd, 4-th), (5-th, 6-th) particle of one BPB state by Bell basis, and encode the result into two classical bits accordingly, we can find that  . For instance, if the results are |Φ−〉, |Ψ+〉 and |Ψ−〉, then R12 = 01, R34 = 10 and R56 = 11. This equation is inspired by and similar with Zhang’s protocol17,18. The differences are orders of the 5-th and 6-th particle.
. For instance, if the results are |Φ−〉, |Ψ+〉 and |Ψ−〉, then R12 = 01, R34 = 10 and R56 = 11. This equation is inspired by and similar with Zhang’s protocol17,18. The differences are orders of the 5-th and 6-th particle.
In other words, exact measurement results of the BPB state cannot be predetermined, but the relation of three results is satisfied anyway. It shows an excellent property, which can be utilized to design some quantum communication protocols.
Suppose that the Boss Charlie owns the secret messages S. The binary representation of S is S = (s0, s1, …, s2N−1), i.e, S could be rewritten as  . For further consideration, we split S into pairs, namely, S = (S0, S1, …, SN−1) = ((s0, s1), (s2, s3), …, (s2N−2, s2N−1)).
. For further consideration, we split S into pairs, namely, S = (S0, S1, …, SN−1) = ((s0, s1), (s2, s3), …, (s2N−2, s2N−1)).
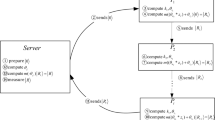
The processes of our quantum secret sharing protocol
[S − 1] The boss Charlie prepares the N groups of |Ψ6qb〉 state. He divides the groups into three sequences. The first and second particles of each state form the sequence  . Similarly, the third and fourth (fifth and sixth) particles form the sequence
. Similarly, the third and fourth (fifth and sixth) particles form the sequence  (
( ).
).
[S − 2] Then, Charlie produces two decoy state sequences. The state in the sequences belongs to the set {|0〉, |1〉, |+〉, |−〉}, and the length of each sequence is K. As soon as the sequences are produced, Charlie inserts the first (second) decoy state sequence into SA (SB) at the random position. New sequence is symbolized by SA2 (SB2). After that, he sends these two new sequences to agent Alice and agent Bob respectively.
[S − 3] Once Alice and Bob received the sequences, three participants check whether there exists an eavesdropper in the channel. Charlie tells them the exact position of decoy state in sequences SA2 and SB2, and what basis they need to utilize in the measurement operation. Actually, they measure the state in Z basis if the state is |0〉 or |1〉, and measure the state in X basis if it is |+〉 or |−〉. After the measurement, two agents tell Charlie the results, which are necessary for him to analyze the error rate. If the rate is higher than the preset threshold, three participants discard all the sequences and restart the step [S − 1]. Otherwise, they go next.
[S − 4] Three participants throw these decoy states away, and construct the rest of the particles into sequences SA3, SB3 and SC3 respectively. Afterwards, they measure the (1-st, 2-nd), (3-rd, 4-th), (5-th, 6-th) particles of these sequences in Bell basis, and record the results in two classical bits as the way in Eq. (5). The i-th classical bit pairs of Alice, Bob, and Charlie are denoted as RAi, RBi, RCi. That is to say, RAi, RBi, RCi ∈ {00, 01, 10, 11} for ∀i.
[S − 5] Then, Charlie calculates CSi = RCi ⊕ Si, and announces the sequence CS. After the reception of CS, Alice and Bob consult and determine one party to rebuild sequence S. Suppose that Alice rebuilds the secret, Bob will send RB to her. Then, Alice computes  = CSi ⊕ RAi ⊕ RBi = Si. Finally, she can get the secret S.
= CSi ⊕ RAi ⊕ RBi = Si. Finally, she can get the secret S.
The processes of our protocol are also graphically described in Fig. 1.
Now, we analyze the correctness of this protocol briefly. As we all know, RAi ⊕ RBi ⊕ RCi = 00. So it’s easy to verify that  = CSi ⊕ RAi ⊕ RBi = RCi ⊕ Si ⊕ RAi ⊕ RBi = Si. Namely,
= CSi ⊕ RAi ⊕ RBi = RCi ⊕ Si ⊕ RAi ⊕ RBi = Si. Namely,  = Si, then we know that Alice has gained the secret successfully. In the Table 1, a part of possible values of classical bits used in our protocol are listed. We also can get
= Si, then we know that Alice has gained the secret successfully. In the Table 1, a part of possible values of classical bits used in our protocol are listed. We also can get  = Si from this table.
= Si from this table.
Security Analysis
On one hand, outside attack is analyzed. In our protocol, quantum states are only transmitted in [S − 2]. In this step, as far as the general outside attack is concerned, the sender use the decoy states to prevent from eavesdropping. Several attacks, such as intercept-resend attack, measurement-resend attack, and entanglement-measure attack, will be detected with a nonzero probability. This conclusion has been proved25. Consider Eve’s correlation-elicitation attack, the utilization of decoy states also can ensure the security. This fact has been showed26.
Some other common attacks could be resisted with the help of corresponding equipment. Consider about the faked states attack27,28,29,30 and time-shift attack29,31, an extra detector could be utilized to monitor the time when the state arrives at the sides of receiver Alice and Bob. As far as the detector blinding attack28,32, light intensity monitor will play a vital role.
What’s more, the states are only transported for one time. It shows that the Trojan-horse attacks (such as the delay-photon Trojan horse attack and the invisible photon eavesdropping (IPE) Trojan horse attack) are invalid for our protocol.
To wit: our protocol is safe for the kinds of outside attack.
On the other hand, Participants’ attack is discussed. Consider that all the participants are rational. They will not choose the attack type which cannot help them to gain useful information. For example, they will not disrupt the procession of the protocol deliberately if they could obtain no useful information about the sharing secret.
Since Alice and Bob play the same role in the protocol, we only discuss the situation that Alice wants to get the secret without the help of Bob.
The analysis of reduced density matrix is a common attack approach. Players can use the particles in hand to deduce the residual particles in other participants’ hand, and the classical information of them. In fact, players don’t need to perform any operation but projection measurement. In detail, they only perform measurement on the step [S − 4] in Bell basis beside the eavesdropping check. The states before three participants’ final measurement can be only in |Ψ6qb〉.
The reduced density matrix of Alice’s particles is

Here, I4 is the identity matrix of 4 dimension Hilbert space. We can know that ρA is independent with players’ classical information RAi, RBi and RCi.
Similarly, we can find that ρB = ρC = I4/4. And then, we know that Alice cannot distinguish Bob’s classical bit 0 from 1, or infer any useful information. So do Bob.
Universality of quantum communication protocols and our QSS protocol
The universality of quantum communication protocols and our QSS protocol is researched in this section. Firstly, the module division of quantum communication protocols, coupling of different modules, and relative explanations are studied originally. Then, we propose the BPB-class/BPB-like-class states, and extend our QSS protocol into a class of QSS protocols. It shows that our protocol is universal for the module Quantum States. Next, we study the relation of our QSS protocol to the QPC protocol18. It means that our protocol is universal for the module Aim. Finally, discussion about the universality, and a quantitative way to describe the universality are also given. These discussions make our analysis more systematic and comprehensive.
The module division of quantum communication protocols
Just like a machine, or software, a quantum communication protocol also can be treated as a system, and be divided into several modules. These modules can uniquely determine a protocol. If all the modules are determined, the protocol is only. A quantum communication protocol consists of:
-
1
Aim: What the communication protocol is designed for.
-
2
Participants: The parties /roles who perform the protocol.
-
3
Quantum States: The carrier of information, which will be transported in the protocol.
-
4
Quantum Operations: The ordered set of quantum operations used in the protocol, by which information is mainly transmitted.
-
5
Quantum Equipment: The equipment for quantum information processing.
-
6
Classical Operations (if necessary): The ordered set of classical operations used in the protocol, by which classical information is transmitted.
-
7
Classical Equipment (if necessary): The equipment for classical information processing.
The division of our protocol is also given in Fig. 2. Note that quantum equipment is only related to quantum operations, so the arrow associate with Quantum Equipment only exists in Quantum Operations. So do the arrow between Classical Equipment and Classical Operations.
Coupling is the degree to evaluate the relationship between different modules. If the relation is close, we say these modules are highly coupling. In this subsubsection, we consider the coupling of different modules in quantum communication protocols. Before that, we divide the degree of coupling into the following 9 levels, which are shown in Table 2.
If the level of Participants → Aim is −4, from Table 2, we can know that Participants is controlled by Aim. Further, we say Aim is controlling Participants, and the level of Aim → Participants is +4. A table is given to describe the coupling between different modules in general protocols, i.e., Table 3.
(1) The relationship between Aim and the others.
Aim → Participants, +4. Aim is the core of a protocol. The other modules are designed to achieve the aim. Once the aim is made certain, participants are generally determined. We say that Aim and Participants are highly coupled. In order to show this point, a brief example is given: The millionaire Alice and Bob are necessary in a QPC protocol. Besides, TP is designed to help the players in most of these protocols. There are three kinds of TP: honest, semi-honest21,26,33,34 and dishonest35. Different protocols may contain different kinds of TP (Researchers usually don’t employ the honest TP in a protocol because this assumption is too strong).
Aim → Quantum States, +2. On one hand, lots of quantum states could be utilized to accomplish the same aim. For instance, the GHZ state26,33, the |χ〉 state21, and lots of other quantum state34,35, could be used to perform a QPC protocol. On the other hand, the GHZ state could be exploited to execute not only a QPC protocol, but also a QSS protocol7, and so on ref. 36.
Aim → Quantum Operations, +3. For a certain aim, quantum operations are closely determined. Take remote state preparing (RSP) protocols as example, sharing of some entangled states, measurement of quantum states are necessary37,38.
Aim → Quantum Equipment, 0. Quantum equipment is only relative with corresponding quantum operations, so the relation level is 0.
Aim → Classical Operations, +3. Just like quantum operations, classical operations are also closely determined by the aim. For a RSP protocol37,38, coding and transmission of measurement results are necessary (Receiver need to use these classical bits to prepare the state).
Aim → Classical Equipment, 0. Since we say classical equipment is only relative with corresponding classical operations, the relation level is 0.
(2) The relationship between Participants and the others.
Participants → Quantum States. Since Participants and Aim are highly coupled, the level of Participants → Quantum States equals to Aim → Quantum States. Similarly, Participants → QO/QE/CO/CE equals to Aim → QO/QE/CO/CE.
(3) The relationship between Quantum States and the others.
Quantum States → Quantum Operations, +1. For the same quantum state, plenty of quantum operations could be performed. In |χ〉 state’s case21, measurement in X basis, Z basis, Bell basis, and the others are all allowed. At the same time, Pauli operations are universal for all the bipartite quantum states.
Quantum States → Quantum Equipment, 0. Similar to the reason we have explained in Aim → Quantum Equipment, the level of Quantum States → Quantum Equipment is 0.
Quantum States → Classical Operations, +1. These two modules have weak coupling, because we cannot derive effective information about classical operations from quantum states, and vice versa.
Quantum States → Classical Equipment, 0. Likewise, the level of Quantum States → Classical Equipment is 0.
(4) The relationship between Quantum Operations and the others.
Quantum Operations → Quantum Equipment, +2. Once the quantum operations are made certain, the sort of quantum equipment is determined, but details about the equipment are not. Under many circumstances39, security proofs assume that participants have well control of the state preparation and of the measurement devices. But its not necessary for all the protocols. In 2012, Lo et al.40 proposed a measurement-device-independent (MDI) quantum key distribution (QKD) protocol. In this protocol, measurement device is independent, participants don’t need to know detailed knowledge of measurement devices, or trust them. It’s more safe than the previous protocols because the security is not based on measurement device. MDI protocol can be treated as the protocol in which Quantum Equipment does not have strong connection with Quantum Operations.
Quantum Operations → Classical Operations, +2. Sometimes the accomplishment of quantum operations needs the assist of classical information. For instance, in QSTS protocols, agent who recover the state needs the classical information of other agents. So others will convey classical information to him/her. The degree of coupling between Quantum Operations and Classical Operations is not low.
Quantum Operations → Classical Equipment, 0. These two modules have no connection, the level is 0.
(5) The relationship between Quantum Equipment and the others. As we have described, all the levels are equal to 0 except Quantum Operations → Quantum Equipment.
(6) The relationship between Classical Operations and the others.
Classical Operations → Classical Equipment, +2. There are two kinds of classical operations in a quantum communication protocol: transmission and storing. On one hand, when we discuss the transmission of classical information, in most cases, we suppose this process is public. The security of this process is not required. On the other hand, storing of classical information is enough safe under the present conditions if we don’t send the information. Based on the analysis above, Classical Equipment has a weak connection with Classical Operations.
A class of QSS protocols via the BPB-class/BPB-like-class states
Inspired by the BPB state, we build a set to describe some states which share common traits. The state in this set is described as follows:

Here, ai ∈ {1, −1} for 0 ≤ i ≤ 15. Consider the global phrase, we suppose that a0 = 1. There are 215 possible states in the set, all of them could be utilized to perform this protocol, i.e., 1 ≤ j ≤ 215. In the Table 4, some states of  and corresponding coefficients are shown. Here,
and corresponding coefficients are shown. Here,  is the quantum carrier in our original QSS protocol.
is the quantum carrier in our original QSS protocol.
 .
.If we utilize Bell basis to measure  , and encode the results of (1-st, 2-nd), (3-rd, 4-th), (5-th, 6-th) particle as mc112, mc134, mc156, respectively, it’s easy to get
, and encode the results of (1-st, 2-nd), (3-rd, 4-th), (5-th, 6-th) particle as mc112, mc134, mc156, respectively, it’s easy to get

Then, we concatenate them as mc1 (mc1 = mc112||mc134||mc156). All the different mc1 constitute a set MC, and

Similarly, there are 215 other states which can also perform this protocol. These states are written in Z basis as follow:

For 0 ≤ i ≤ 15, fi ∈ {1, −1}. Consider the global phrase, we can set f0 = 1; i.e., 1 ≤ j ≤ 215.
Besides, we also can re-encode four states {|00〉, |01〉, |10〉, |11〉} into two classical bits:

If we utilize Z basis to measure  , and encode the results as the previous way, these classical bits are denoted as mc212, mc234, mc256, separately. Similarly, we can get
, and encode the results as the previous way, these classical bits are denoted as mc212, mc234, mc256, separately. Similarly, we can get

We concatenate these bits as mc2. Obviously, mc2 ∈ MC, too.
Actually, we call  states as the BPB-class states,
states as the BPB-class states,  states as the BPB-like-class states.
states as the BPB-like-class states.
All the BPB-class states and BPB-like-class states can be utilized to perform our QSS protocol. Our protocol is universal for quantum states. We call these protocols (with different states) as a class of QSS protocols. The processes of these protocols are the same with the steps [S − 1] to [S − 5]. The only difference is, if the BPB-like-class states are utilized, participants need to measure SA3/SB3/SC3 in Z basis instead of Bell basis. By the way, the measurement in Z basis is much easier to be performed than in Bell basis.
The relation of Zhang’s QPC protocol to our QSS protocol
With the development of computer science and corresponding applications41,42,43,44,45,46, security of data has been attracting a lot of attention. Secure multi-party computation (SMC) is an important kind of multi-user remote coordinative computation problems. A good solution of SMC problems need to ensure the correctness of computation and the security of players’ data. In other words, the schemes not only need to help players to get the correct result, but also ensure that the private input values will not be revealed to others.
Private comparison is an important SMC problem. In this problem, two or more players want to compare the equality of the private information. QPC protocol is the quantum version solution of private comparison problem. Zhang et al. proposed a QPC protocol based on the BPB state18, which could be used to compare three values M1, M2 and M3 for one time. In this subsubsection, we discuss the relation between this QPC protocol and our QSS protocol.
From Table 5, we know that the QPC protocol and QSS protocol we discussed are similar. For ease of analysis, we show the correspondence of these symbols firstly in Table 6.
Analysis of Table 5 is shown as follow. There is almost a one-to-one correlation between the quantum steps (1)–(4), (7) in the QPC protocol and the steps (1)–(5) in our QSS protocol. So do the classical steps (1)–(3) in the QPC protocol and the steps (1)–(3) in our QSS protocol.
On one hand, since the QPC protocol18 is designed for three parties without any fourth party, P1 is not a common player, but a special one who has mission to prepare the states. He could be regarded as the combination of a common player who want to compare his private input, and an assistant player who need to help common player to compare their inputs. Because of that, he also has the motivation to steal more information for his own benefit. That is what the quantum steps (5)–(6), and classical steps (4)–(6) aim for. Concretely, these steps are performed to check whether P1 shares genuine |Ψ6qb〉 to P2 and P3. Since the Boss Charlie does not have motivation to cheat in QSS protocol, these steps are unnecessary. In this sense, quantum operations of these two protocols are equivalent.
On the other hand, secret sharing could be regarded as the process of diving the information (Boss divides the secret into two/many parts), while private comparison could be considered as the process of integrating information (Assistant player integrates two secret inputs into one bit, i.e., these inputs are equal or not). We can say that the private comparison is the inverse process of secret sharing in a way.
A brief discussion about the quantum carrier
All the Bell (Z) basis measurement results of the BPB-class (BPB-like-class) states have the same statistical distribution. Firstly, the Bell (Z) measurement results of each BPB-class (BPB-like-class) state are related, and shown in Eqs (8) and (12). Secondly, the relations of results are the same for different states, and could be utilized for different functions, such as QSS and QPC. These properties are the key to design a protocol, which is universal for the quantum carrier and aim. Besides that, our protocol is the first of its kind. Thirdly, BPB state has be researched on designing QSS10, quantum summation17 and QPC18 protocol respectively. This six-particle state is a small hot topic on the research. Since all the BPB-class/BPB-like-class states hold the similar properties, these states could also play important roles in quantum communication protocols. In this view, these states are worthy and advantageous for the concern of universality.
Discussion about the universality
The situation what we are mostly focus on in this paper is, in general quantum communication protocols, if module Participants, QO, QE, CO and CE are certain, the module Aim and QS are determined generally. Namely, it’s hard for researchers to seek a new aim or quantum state to replace the old one in a certain protocol.
In our protocol, quantum states are optional in the foregoing state classes. Participants will have many options to consider. Connection between the third module and the others is weak. This property is discussed in Section A class of QSS protocols via the BPB-class/BPB-like-class states. Besides, the aim could be QSS or QPC. The difference between the QSS protocol (in this paper) and QPC protocol18 is a little. A QSS protocol could be used to execute the QPC protocol with a little modification. Connection between the first module and the others is not particularly strong as other quantum communication protocols. This property is discussed in Section The relation of the QPC protocol18 to our QSS protocol. This is a feature what most of protocols don’t have. This property makes our system more useful. Exactly, our protocol is multi-functional.
In one word, our protocol is subtly designed, and has low coupling.
Besides that, in Table 3 we described the coupling of quantum communication protocols in general. Actually, we can tabulate for any specific protocol. Our QSS protocol is also analyzed as example in Table 7.
A way to quantitatively describe the coupling of a protocol, is summing the absolute value of all the numbers, and then dividing the sum of absolute value in Table 3.

Here, Sums means the summation of all the absolute value in a specific protocol, Sumt means the summation of all the absolute value in Table 3.
Since Sumt = 56, Eq. (13) could be rewritten as:

Now, let’s sum the absolute value of all the numbers in Table 7, the answer is 50. So, DC = 50/56 = 0.89. It shows that our protocol is well-designed indeed.
In addition, Sums and Sumt also could be the weighted sum of absolute values, not only direct sum. The item which is more valued for the researchers, will have a heavier weight.
Further, for any specific protocol, if DC is lower, the coupling of the protocol will be lower, and the protocol will be better-designed. By the way, for all the protocols, DC is in direct proportion to Sumt. If we want to compare the coupling of two protocols, the concrete value of Sumt is not important.
Discussion
In this paper, we propose a kind of universal QSS protocol. Firstly, we perfectly design a new QSS protocol via the BPB state. Correctness and security analysis of the protocol are given. Only preparation and measurement of the states are needed in the protocol. It shows that the protocol is not only safe, but also flexible. Then, through research on the characteristics of BPB state, the BPB-class states are proposed. Measure of entanglement of these states is also detailedly calculated. Furthermore, the above-mentioned protocol is extended into a class of QSS protocols based on the BPB-class states. In this class, utilized states are alterable. Besides that, we discuss the relation of the QPC protocol18 to our protocol, and pioneer the module division and coupling of quantum communication protocols. Some existing protocols are analyzed as example. A way to quantitatively describe the coupling is given. It concludes that our protocol is universal. Our research will help us to find and design universal protocols, which will be more practical under the present technical conditions.
Methods
Geometric measure
For a pure state |ψ〉, we need to find a separable state |ϕ〉 which makes the inner product 〈ϕ|ψ〉 maximum. The measure of entanglement  is defined as follows23:
is defined as follows23:

If  is smaller,
is smaller,  will be larger. Then, |ψ〉 is more like the pure state |ϕ〉, entanglement of |ψ〉 is lower. On the contrary, if
will be larger. Then, |ψ〉 is more like the pure state |ϕ〉, entanglement of |ψ〉 is lower. On the contrary, if  is more close to 1, entanglement of |ψ〉 will be higher.
is more close to 1, entanglement of |ψ〉 will be higher.
Additional Information
How to cite this article: Chen, X.-B. et al. A kind of universal quantum secret sharing protocol. Sci. Rep. 7, 39845; doi: 10.1038/srep39845 (2017).
Publisher's note: Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
Shamir, A. How to share a secret. Commun. ACM 22, 612–613 (1979).
Blakley, G. R. Safeguarding cryptographic keys. Managing Requirements Knowledge, International Workshop on. IEEE Computer Society 48, 313–317 (1979).
Lo, H. K. & Chau, H. F. Unconditional security of quantum key distribution over arbitrarily long distances. Science 283, 2050–2056 (1999).
Mayers, D. Unconditional security in quantum cryptography. J ACM 48, 351–406 (2001).
Hillery, M., Buzek, V. & Berthiaume, A. Quantum secret sharing. Phys Rev A 59, 1829 (1999).
Guo, G. P. & Guo, G. C. Quantum secret sharing without entanglement. Phys Rev A 310, 247–251 (2003).
Xiao, L., Long, G. L., Deng, F. G. & Pan, J. W. Efficient multiparty quantum-secret-sharing schemes. Phys Rev A 69, 052307 (2004).
Yan, F. L. & Gao, T. Quantum secret sharing between multiparty and multiparty without entanglement. Phys Rev A 72, 012304 (2005).
Jia, H. Y., Wen, Q. Y., Gao, F., Qin, S. J. & Guo, F. Z. Dynamic quantum secret sharing. Phys Lett A 376, 1035–1041 (2012).
Long, Y., Qiu, D. & Long, D. Quantum secret sharing of multi-bits by an entangled six-qubit state. J Phys A-Math Theor 45, 195303 (2012).
Qin, S. J. & Liu, F. Information leakage in quantum secret sharing of multi-bits by an entangled six-qubit state. Int J Theor Phys 53, 3116–3123 (2014).
Dehkordi, M. H. & Fattahi, E. Threshold quantum secret sharing between multiparty and multiparty using Greenberger - Horne - Zeilinger state. Quantum Inf Process 12, 1299–1306 (2013).
Rahaman, R. & Parker, M. G. Quantum scheme for secret sharing based on local distinguishability. Physical Review A 91, 022330 (2015).
Cleve, R., Gottesman, D. & Lo, H. K. How to share a quantum secret. Phys Rev Lett, 83, 648 (1999).
Yang, C. P., Chu, S. I. & Han, S. Efficient many-party controlled teleportation of multiqubit quantum information via entanglement. Phys Rev A 70, 022329 (2004).
Ray, M., Chatterjee, S. & Chakrabarty, I. Sequential quantum secret sharing in a noisy environment aided with weak measurements. Eur Phys J D 70, 1–11 (2016).
Zhang, C., Sun, Z. W., Huang, X. & Long, D. Y. Three-party quantum summation without a trusted third party. Int J Quantum Inf, 13, 1550011 (2015).
Zhang, C., Sun, Z. W., Huang, X. & Long, D. Y. Three-party quantum private comparison of equality based on genuinely maximally entangled six-qubit states. arXiv preprint 1503.04282 (2015).
Allen, E. B., Khoshgoftaar, T. M. & Chen, Y. Measuring coupling and cohesion of software modules: an information-theory approach. Metrics 124–134 (2001).
Offutt, A. J., Harrold, M. J. & Kolte, P. A software metric system for module coupling. J Syst Software, 20, 295–308 (1993).
Chen, X. B., Dou, Z., Xu, G., Wang, C. & Yang, Y. X. A class of protocols for quantum private comparison based on the symmetry of states. Quantum Inf Process 13, 85–100 (2014).
Eisert, J. & Gross, D. Multi-particle entanglement. arXiv preprint quant-ph/0505149 (2005).
Wei, T. C. & Goldbart, P. M. Geometric measure of entanglement and applications to bipartite and multipartite quantum states. Physical Review A 68, 042307 (2003).
Borras, A., Plastino, A. R., Batle, J., Zander, C., Casas, M. et al. Multiqubit systems: highly entangled states and entanglement distribution. J Phys A-Math Theor 40, 13407 (2007).
Shor, P. W. & Preskill, J. Simple proof of security of the BB84 quantum key distribution protocol. Phys Rev Lett, 85, 441 (2000).
Chen, X. B., Xu, G., Niu, X. X., Wen, Q. Y. & Yang, Y. X. An efficient protocol for the private comparison of equal information based on the triplet entangled state and single-particle measurement. Opt Commun 283, 1561–1565 (2010).
Makarov, V., Anisimov, A. & Skaar, J. Effects of detector efficiency mismatch on security of quantum cryptosystems. Phys Rev A 74, 022313 (2006).
Jain, N., Stiller, B., Khan, I., Elser, D., Marquardt, C. et al. Attacks on practical quantum key distribution systems (and how to prevent them). Contemp Phys 1–22 (2016).
Zhao, Y., Fung, C. H. F., Qi, B., Chen, C. & Lo, H. K. Quantum hacking: Experimental demonstration of time-shift attack against practical quantum-key-distribution systems. Phys Rev A 78, 042333 (2008).
Scarani, V., Bechmann-Pasquinucci, H., Cerf, N. J., Dušek, M., Lütkenhaus, N. et al. The security of practical quantum key distribution. Rev Mod Phys 81, 1301 (2009).
Qi, B., Fung, C. H. F., Lo, H. K. & Ma, X. Time-shift attack in practical quantum cryptosystems. Quantum Inf Comput 7, 73–82 (2007).
Lydersen, L., Wiechers, C., Wittmann, C., Elser, D., Skaar, J. et al. Thermal blinding of gated detectors in quantum cryptography. Opt Express 18, 27938–27954 (2010).
Chang, Y. J., Tsai, C. W. & Hwang, T. Multi-user private comparison protocol using GHZ class states. Quantum Inf Process 12, 1077–1088 (2013).
Li, Y. B., Qin, S. J., Yuan, Z., Huang, W. & Sun, Y. Quantum private comparison against decoherence noise. Quantum Inf Process 12, 2191–2205 (2013).
Yang, Y. G. & Wen, Q. Y. An efficient two-party quantum private comparison protocol with decoy states and two-photon entanglement. J Phys A-Math Theor 42, 055305 (2009).
Wang, C., Deng, F. G. & Long, G. L. Multi-step quantum secure direct communication using multi-particle Green-Horne-Zeilinger state. Opt Commun 253, 15–20 (2005).
Bennett, C. H., DiVincenzo, D. P., Shor, P. W., Smolin, J. A., Terhal, B. M. et al. Remote state preparation. Phys Rev Lett 87, 077902 (2001).
Ye, M. Y., Zhang, Y. S. & Guo, G. C. Faithful remote state preparation using finite classical bits and a nonmaximally entangled state. Phys Rev A 69, 022310 (2004).
Acín, A., Brunner, N., Gisin, N., Massar, S., Pironio, S. et al. Device-independent security of quantum cryptography against collective attacks. Phys Rev Lett 98, 230501 (2007).
Lo, H. K., Curty, M. & Qi, B. Measurement-device-independent quantum key distribution. Phys Rev Lett, 108, 130503 (2012).
Fu, Z. J., Sun, X. M., Liu, Q., Zhou, L. & Shu, J. G. Achieving Efficient Cloud Search Services: Multi-keyword Ranked Search over Encrypted Cloud Data Supporting Parallel Computing. IEICE T Commun 98, 190–200 (2015).
Ren, Y. J., Shen, J., Wang, J., Han, J. & Lee, S. Y. Mutual Verifiable Provable Data Auditing in Public Cloud Storage. J INTERNET Technol 16, 317–323 (2015).
Xia, Z. H., Wang, X. H., Sun, X. M. & Wang, Q. A Secure and Dynamic Multi-keyword Ranked Search Scheme over Encrypted Cloud Data. IEEE T Parall Distr, doi: 10.1109/TPDS.2015.2401003 (2015).
Fu, Z. J., Ren, K., Shu, J. G., Sun, X. M. & Huang, F. X. Enabling Personalized Search over Encrypted Outsourced Data with Efficiency Improvement. IEEE T Parall Distr, doi: 10.1109/TPDS.2015.2506573 (2015).
Fu, Z., Wu, X., Guan, C., Sun, X. M. & Ren, K. Towards Efficient Multi-keyword Fuzzy Search over Encrypted Outsourced Data with Accuracy Improvement. IEEE T Inf Foren Sec, 11, 2706–2716 (2016).
Gu, B., Sheng, V. S., Tay, K. Y., Romano, W. & Li, S. Incremental support vector learning for ordinal regression. IEEE T Neur Net Lear 26, 1403–1416 (2015).
Acknowledgements
This work is supported by the National Natural Science Foundation of China (Grant Nos. 61671087, 61272514, 61170272, 61411146001), the National Development Foundation for Cryptological Research (Grant No. MMJJ201401012), the Fok Ying Tung Education Foundation (Grant No. 131067), Program for New Century Excellent Talents in University (Grant No. NCET-13-0681), and the China Scholarship Council (CSC).
Author information
Authors and Affiliations
Contributions
X.-B.C., and Z.D. initiated the idea. X.-B.C., Z.D., and G.X. wrote the main manuscript text. X.-Y.H. and Y.-X.Y. reviewed the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing financial interests.
Supplementary information
Rights and permissions
This work is licensed under a Creative Commons Attribution 4.0 International License. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in the credit line; if the material is not included under the Creative Commons license, users will need to obtain permission from the license holder to reproduce the material. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/
About this article
Cite this article
Chen, XB., Dou, Z., Xu, G. et al. A kind of universal quantum secret sharing protocol. Sci Rep 7, 39845 (2017). https://doi.org/10.1038/srep39845
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/srep39845
This article is cited by
-
Multi-Party Quantum Secret Sharing Protocol Based on GHZ States Entanglement Swapping
International Journal of Theoretical Physics (2022)
-
Standard (3, 5)-threshold quantum secret sharing by maximally entangled 6-qubit states
Scientific Reports (2021)
-
Efficient Verifiable Quantum Secret Sharing Schemes via Eight-Quantum-Entangled States
International Journal of Theoretical Physics (2021)
-
A new n-party quantum secret sharing model based on multiparty entangled states
Quantum Information Processing (2019)
-
Cryptanalysis and Improvement of a Multiparty Quantum Direct Secret Sharing of Classical Messages with Bell States and Bell Measurements
International Journal of Theoretical Physics (2019)
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.