Abstract
Hardware-based cryptography that exploits physical unclonable functions is required for the secure identification and authentication of devices in the Internet of Things. However, physical unclonable functions are typically based on anticounterfeit identifiers created from randomized microscale patterns or non-predictable fluctuations of electrical response in semiconductor devices, and the validation of an encrypted signature relies on a single-purpose method such as microscopy or electrical measurement. Here we report nanoscale physical unclonable function labels that exploit non-deterministic molecular self-assembly. The labels are created from the multilayer superpositions of metallic nanopatterns replicated from self-assembled block copolymer nanotemplates. Due to the nanoscale dimensions and diverse material options of the system, physical unclonable functions are intrinsically difficult to replicate, robust for authentication and resistant to external disturbance. Multiple, independently operating keys—which use electrical resistance, optical dichroism or Raman signals—can be generated from a single physical unclonable function, offering millisecond-level validation speeds. We also show that our physical unclonable function labels can be used on a range of different surfaces including dollar bills, human hair and microscopic bacteria.
Similar content being viewed by others
Main
As the Internet of Things (IoT) develops—and the number of devices that store personal data and interconnected over wireless networks increases1,2,3—there is a growing need for secure authentication and identification methods. Software-based validation systems are currently dominant but are potentially vulnerable to external disturbance such as hacking or electromagnetic interference4,5,6. Thus, hardware-based cryptography that exploits physical unclonable functions (PUFs) has been explored for IoT systems7,8,9,10,11,12,13,14. PUFs typically use anticounterfeit identifiers obtainable from randomized microscale patterns11,15,16,17,18,19 or non-predictable fluctuation of the electrical response in semiconductor devices20,21,22, and the validation of encrypted signature typically relies on a single-purpose method, including time-consuming microscopy or electrical measurement.
In this article, we report the development of a nanoscale PUF (nanoPUF) based on block copolymer (BCP) nanopatterning. Due to thermodynamically driven microphase separation behaviour that randomly occurs under thermal fluctuation23,24,25,26, BCP self-assembly can provide large-area parallel formation of fingerprint lamellar patterns with critical dimensions down to 3 nm. At this scale, replication of the PUF label is nearly impossible without high cost as well as time-consuming characterization/fabrication tools. The labels are created from multilayer superpositions of metallic nanopatterns replicated from the self-assembled BCP nanotemplates27,28. A single nanoPUF can generate multiple, independently operating keys, which use electrical resistance, optical dichroism or Raman signals. This means that a particular authentication key can be chosen for a specific system, and multiple keys can be combined for an ultrahigh security rate. To illustrate the capabilities of our approach, we show that the nanoPUF labels can be used on a range of different surfaces: dollar bills, flexible polymer substrates, human skin, human hair, an ant body and microscopic bacteria.
Multipurpose nanoPUF label generation
Biological vein networks are a complex biological medium with non-predictable connectivity and randomized length scales and are useful for high-security authentication (Fig. 1a)29,30. The distinctive geometric features of a vein network are hidden under human skin, yet they offer an important method of biometrics, eligible for secure authentication using a near-infrared laser. Protection and anticounterfeiting of assets that require high security, such as the banknote, can be achieved by introducing vein-like PUFs, allowing high-speed authentication by optical or electrical detection (Fig. 1b). Such a bioinspired PUF can be created via the multilayer superposition of metallic nanopatterns replicated from BCP nanotemplates27,28, which are formed by a non-deterministic self-assembly process relying on well-established microphase separation mechanisms23,24,31 (Fig. 1c and Methods).
a, Bioinspired motivation for nanoPUF. b, Real-world application of a PUF label to a banknote. c, Fabrication procedure for self-organized multilayer complex nanostructures. d, Multipurpose authentication mechanism for nanoPUF. e, SEM images of nanoPUFs for various layer stacking numbers. Scale bar, 200 nm. f, Physical properties of nanoPUFs for various layer stacking numbers. g, Total size of key space with the combination of authentication ways.
Nanoscale pattern dimensions are beyond typical optical resolution limits, and thus, the straightforward morphological validation of a nanoPUF label requires tedious microscopic scanning, such as scanning electron microscopy (SEM) or atomic force microscopy32,33. These time-consuming validation tools limit the potential practicality of an authentication system. Thus, our nanoPUFs, which are composed of nanostructured metals, respond to various physical stimuli—including electrical potential and polarized visible light—that can be used for effective validation within milliseconds and generating multiple unpredictable keys from an identical nanoPUF (Fig. 1d). These keys are encrypted through physically independent mechanisms—electrical resistance (electrical key, key 1), optical dichroism (dichroism key, key 2) and Raman scattering (Raman key, key 3)—enabling mutually independent authentication routes. Users are free to choose one of the authentication methods according to a demanded specific purpose. Furthermore, multilevel authentication with a high-security rate is possible through a combination of two or more independent authentication keys.
Multilayer stacking of BCP nanopatterns offers advantages for authentication labels. A monolayer BCP pattern provides a randomized fingerprint-like pattern with a unique length scale of lamellar period and localized orientation correlation among the neighbouring lamellae. More complex and less predictable interconnected nanopatterns can be generated via transfer printing of metallic nanopatterns, which can be overlaid several times (Fig. 1e). We theoretically calculated the two-dimensional (2D) information entropy and the orientational correlation length of the generated nanopatterns (Fig. 1f, Methods and Extended Data Fig. 1). A sample information entropy of a 2D matrix of continuous pixel values is employed, whereas the Hausdorff dimension of the 2D matrix is calculated for fractal dimension. As expected, the information entropy (pattern complexity) increases with the stacking number along with the reduction in orientational correlation length (local orientation). Multilayer stacking also allows the relatively narrow distribution of the order parameters over an arbitrarily large PUF label area. Small standard deviations for the spatial distribution of 2D information entropy (S) verify the uniform level of complexity yet fully non-predictable randomized pattern formation over the broad patterned area (Methods and Extended Data Fig. 1).
A further advantage of multilayer stacking is the reliable responsivity of the nanoPUF to physical validation methods, including electrical measurement and Raman scattering, where the formation of unpredictable conductive pathways or small nanogaps below the original lamellar period are crucial for the unpredictable signal generation. The resultant encoding capacity depends on the number of challenge–response pairs (CRPs) obtainable either from a single encryption method or a combination of several encryption methods (Methods and Fig. 1g). For example, a single key consists of a 15-bit CRP space in this work, subsequently yielding the key space of 215 (Methods). Thus, the integration of only two independent validation methods can provide multibillions of key space, comparable to the worldwide population (almost 8.0 × 109). Moreover, the integration of all three methods provides an extremely large key space approaching 3.3 × 1013 (Methods). The overall encoding capacity can also be further improved by increasing the size of the CRP space for each key (inversely proportional to the pixel area for patterned measurements).
Operation of multipurpose key generation
Figure 2a illustrates the challenge–response authentication process for a nanoPUF. In the initial challenge generation step (green dashed line), arbitrary challenges are introduced into the processing unit of each method. Electrical potential, polarization angle of incident light and light exposure time are set as the typical challenges for the electrical, dichroism and Raman keys, respectively, whereas 15 strings of challenges are sequentially applied to a nanoPUF (typically, 200 μm is the distance between the electrodes for the electrical key, and 50.00 × 50.00 μm2 and 0.75 × 0.75 μm2 are the pixel sizes for the dichroism and Raman keys, respectively). In the next identification generation step (blue dashed line), the nanoPUF acts as a random number generator through unique interaction with the challenges. Subsequent digitalization is performed based on the comparison with arbitrarily set threshold values to yield 15 response bits. Final authentication (red dashed line) is carried out by comparing and evaluating the keys with preset databases.
a, Challenge–response authentication process for a nanoPUF. b, Electrical measurement scheme for electrical key generation. Scale bars, 150 mm (top), 1 μm (bottom). c, Randomized electrical pathways in a multilayer interconnected nanoPUF. d, Random generation of electrical responses from a nanoPUF. e, Electrical key generation from various samples with different electrical thresholds. f, Different reflection intensities for polarized incident visible light at different spots in a nanoPUF. g, Polarized optical microscopy for different reflection states taken at the same sample location. Scale bars, 30.0 mm (left), 0.2 mm (right). h, Intensity difference in Raman scattering depending on the angle between the overlaid nanowires in stacked lamellar layers. i, Theoretical simulation of Raman enhancement for various input polarizations and angles between stacked nanowires.
One of the effective key generation methods from a nanoPUF relies on the generation of randomized patterns in electrical conductivity (Fig. 2b). A randomized electrical current response is expected depending on the output location even if an electrical potential is applied through an identical pair of electrodes in the nanoPUF. The electrical current is delivered through a randomized Kirchhoff resistance network composed of unpredictable combinations of conducting routes34 (Fig. 2c). For a reliable measurement of the randomized signals without concerning the influence from measurement errors or noise, a reference electrode was fabricated on a non-patterned metal film, over which the current distribution was carefully confirmed. As shown in Fig. 2d, the reference (bare thin metal film) exhibits nearly no fluctuation in the electrical resistance level (less than the milliohm scale), whereas four randomly selected nanoPUF samples reveal considerably large fluctuations over the scale of tens of ohms. These unique output values can be transformed into binary signals (namely, barcodes or QR codes) by introducing a predetermined threshold current value (Fig. 2e, Methods and Extended Data Fig. 2).
Another method for key generation exploits the inherent optical dichroism of the nanoPUF pattern. It is well known that a sub-wavelength-scale metallic nanowire pattern exhibits strong optical dichroism depending on the incident wavelength and polarization35. This dichroism is principally determined by the local anisotropy in the in-plane orientation of nanowires, as verified by a simulation study (Fig. 2f) (Methods and Extended Data Fig. 3). Indeed, a nanoPUF formed on a quartz substrate presents a distinctive linear dichroism with polarization-selective transmission of incident light (Fig. 2g), leading to a unique intensity distribution of reflectance for a polarized incidence beam (Extended Data Fig. 4). For practical key generation, we randomly selected a 15-point set and compared the intensity distribution of the reflectance (linearly polarized light with a wavelength of 633 nm) with respect to a predetermined threshold value (Methods and Extended Data Fig. 5).
Our third method of key generation utilizes the intensity distribution of Raman scattering from a nanoPUF. Plasmonic materials with nanoscale features, including gaps, crevices or sharp geometry, induce a strong amplification of incident light, caused by the localized surface plasmon resonance, to yield signature patterns of Raman scattering intensity36,37 (Fig. 2h). A unique plasmonic resonance is expected depending on the local angle between the stacked metal nanowires in our nanoPUF. Randomly occurring lateral gaps between the nanowires in different stacking layers are principally responsible for the enhancement in the Raman signal due to the smaller gap sizes compared with the original lamellar period (Fig. 2i, Methods and Extended Data Fig. 6). Raman keys can be readily generated by measuring the scattering intensities at the selected 15-point sets and the subsequent comparison with a threshold (Extended Data Figs. 3 and 7).
We have performed a quantitative statistical analysis of important PUF security parameters based on the experimental characterization, including uniqueness, bit aliasing and reliability38,39 (Table 1 and Methods). Here 12 PUF cores are fabricated with 15 digital strings for each key generation. All the different key generation schemes introduced in this work exhibit nearly ideal uniqueness (that is, mean values for the measured responses of μElectrical = 41.90%, μDichroism = 43.66%, μRaman = 50.61% and μIntegrated = 45.39%), confirming that each nanoPUF is well distinguishable from others for all the different validation mechanisms. The mean values for bit aliasing are sufficient to avoid similar responses from different PUF labels (that is, μElectric = 28.75%, μDichroism = 32.81%, μRaman = 46.11% and μIntegrated = 35.89%). For reliability, the mean values (μElectrical = 99.48%, μDichroism = 99.69%, μRaman = 98.33% and μIntegrated = 99.15%) are close to the ideal value (100%) to guarantee that a nanoPUF core can reproduce the same response bits under the same validation condition in a robust way. Furthermore, not only high-speed authentication is possible as a given nanoPUF generates multiple keys but high accessibility is also attainable by the unique response even with a macroscale identification resolution. Besides, it is possible to further enhance the encoding capacity by increasing the number of measurement set points for the bit generation.
Our experiment considers a simple case with six electrodes in electrical measurement or 15 points in optical and Raman measurement for the proof-of-concept realization of a nanoPUF. The size of the CRP space can be easily enlarged for our nanoPUF. For instance, in the electrical method, 25 electrodes with the typical width and space down to 20 μm (centre-to-centre distance between the electrodes, 40 μm) can be readily fabricated on a single side of 1 mm × 1 mm PUF pattern by conventional photolithography, thereby incorporating a total of 100 electrodes at all the sides of a PUF pattern. For an exemplary case employing 50 μm width and space (centre-to-centre distance between the electrodes, 100 μm), ten electrodes on one side and a total of 40 electrodes can be generated over a 1 mm × 1 mm PUF. From the combination of 40–100 electrodes, 780 (40C2)–4,950 (100C2)-bit CRP space can be generated. On average, an approximately 2,000-bit CRP space can be easily generated solely for the electrical validation method.
Both optical dichroism and Raman-based validation methods can also provide vastly expanded CRP spaces. It is technically easy to prepare hundreds—or even thousands—of measurement pixels, as the typical spatial resolution of beam focusing is smaller than 10 μm. For the PUF area of 200 μm × 200 μm along with a spatial pixel resolution of 10 μm, we can generate a total of 400 pixels. It is possible to transform these 400 pixels into mutually independent one-dimensional (1D)-bit strings using several 2D-to-1D matrix transformation schemes, such as zigzag (that is, left or right, up or down), spiral (in or out, left or right) and space-filling curves (that is, Hilbert curve, Gosper curve, Koch curve and so on). The total number of these schemes is approximately ten. Therefore, the CRP space for optical dichroism method can be extended up to at least 400 × 10 ≈ 4,000 bits. We suggest a similar manner for the Raman-based method to produce another 4,000-bit CRP space. As those three validation methods are mutually independent, it is possible to prepare an approximately 2,000 + 4,000 + 4,000 = 10,000-bit CRP space. This scale obviously satisfies the typical criterion for a strong PUF, as the total key space is ~210,000 (~103,010) to fulfil the requirements for a wide range of authentication purposes.
Extreme high-security nanopattern identifiers
Apart from the interesting key generation mechanisms from various physical responses, the nanoscale morphology of a nanoPUF itself can be potentially utilized as a reliable nanoidentifier for authentication. The possible number of distinguishable nanoidentifiers with a single kind of defect structure within a 1 μm × 1 μm area can be calculated as 4.8 × 1035 in our nanoPUF (Methods). Figure 3a presents that ten different nanoidentifiers exhibit sufficiently discernible responses to a single binary image challenge pattern based on a simple exclusive-OR (XOR) operation. Here 300 nanoidentifiers are identified (Supplementary Information) to yield a set of sufficiently different response patterns with the average Hamming distance (<μ>) close to 0.5 (that is, <μ> = 0.5007 ± 0.0545) (Fig. 3b and Extended Data Fig. 8). This assures that a nanoPUF can serve as a unique security medium. Conversely, one nanopattern identifier can discriminate different challenges with the average Hamming distance close to 0.5 again (that is, <μ> = 0.4993 ± 0.0082) (Extended Data Fig. 8).
a, XOR operation with a single challenge for multiple nanoPUF samples. b, Hamming distance distribution between responses from single challenge–different PUFs operation. c, Noise robustness test under various threshold conditions. d, Application of conventional fingerprint recognition principle to a nanoPUF.
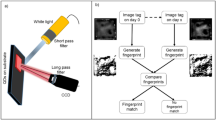
For an image-based nanoidentifier, noise robustness is a crucial requirement. As shown in Fig. 3c (Extended Data Fig. 8), although different threshold pixel values are set for the binarization of the greyscale image (that is, 50 different levels from 0.01 to 0.99), a nanoidentifier can provide distinguishable Hamming distance for a sufficiently wide range of thresholds, verifying safe and reliable authentication. Generally, random lamellar nanopatterns include topological defects, such as terminations and bifurcations (Fig. 3d). The unique distribution of such defects is compatible with the identification algorithm for fingerprint pattern recognition40,41. From a bilayer stack of BCP patterns, spatial coordinates of topological defects can be separately extracted from the top and bottom layers (Methods and Extended Data Fig. 9). Multilayer stacking also yields additional topological defects, such as crossing points. The digitalized images for terminations, bifurcations and crossing points are constructed with a designated pixel resolution. It is noteworthy that there are other types of structural defect that can also serve as independent identifiers, such as ridge island (or short ridge), dot, bridge, spur, eye (or enclosure), double bifurcation, delta, swirl, trifurcation and so on (Extended Data Fig. 10b). Therefore, at least 12 different groups with at least ten identifiers are present, which makes 120 bits for the nanoidentifier (that is, the CRP space for the nanoidentifier is ~120 bits). The estimated maximum code capacity of a single nanopattern layer is 5.32 × 1081. When two BCP layers are overlapped in this work, the maximum code capacity is 2.83 × 10163, which is a sufficiently large number for high-level security applications. Consequently, a nanoidentifier can serve as a unique encryption or authentication key solely based on topological defect distribution. Notably, recent progress in high-throughput nanoscale microscopy, including multitip parallel atomic force microscopy scanning, can be employed for rapid and highly secure authentication by exploiting the inherent high encoding capacity from miniaturized nanoscale features. Nonetheless, a thorough characterization of the entire nanoscale pattern must be avoided, as it significantly threatens the security of our PUF. In this regard, optically transparent adlayer formation above the surface of the nanoPUF can be suggested, which can prevent the direct contact of scanning probe or electron beam to the nanoscale pattern, whereas electrical or optical validation can still be functional.
Stability and application of nanoPUF labels
We have tested the stability and sustainability of the nanoPUF system under various environmental conditions. Practically, PUF labels are required to work on various types of material and geometry at the target surfaces. For long-term reliable operation, PUF labels are also required to be robust against external disturbances induced by undesired physical contacts. The mechanical robustness of a nanoPUF was evaluated by the repeated attaching and detaching of commercially available sticky tapes at the PUF label surfaces (Fig. 4a) for 30 cycles. Electrically generated keys from different samples show a high sustainability and fidelity of 85.93 ± 4.73% (Fig. 4b). The original nanoscale geometry is also well maintained, as verified from the minimal changes in information entropy and fractal dimension. It is noteworthy that mechanical stability can be further improved by employing protective encapsulation. A thermal stability test was conducted under the harsh condition of 150 °C for 1 h (Fig. 4c). Electrically generated keys from different samples reveal the high thermal stability with a coincidence rate of 93.75 ± 6.25%, as the nanoscale security performance is well sustained (Fig. 4d).
a, Mechanical stability test for a nanoPUF label. b, Variation in the physical properties and key performance after the mechanical stability test. c, Thermal stability test for a nanoPUF label. Scale bar, 0.5 cm. d, Variation in physical properties and key performance after thermal treatment. e, Application of nanoPUF labels to arbitrary objects, including a paper bill (left; scale bar, 0.5 cm), deformable transparent polymer substrate (middle; scale bar, 3 mm) and human wrist (right; scale bars, 4 mm and 20 mm (inset)). f, High-precision hidden labelling in human hair (left; scale bars, 50 µm and 1.5 mm (inset)), ant body (middle; scale bars, 50.0 mm and 3.0 mm (inset)) and microbacteria surface (right; scale bar, 300.0 nm).
Figure 4e presents the versatile implementation of a nanoPUF at arbitrary target surfaces. NanoPUF labels are well integrated at the surface of a dollar bill for an anticounterfeit tag and also stabilized at the flexible polymeric surfaces and human skin for wearable or skin-attachable IoT devices. Taking advantage of the intrinsic small size and flexible thin geometry, nanoPUF labels are easily integrated onto arbitrary non-planar deformable surfaces as hidden labels. Interestingly, our high-precision miniature labels can be implemented onto unusually small objectives (Fig. 4f). A PUF label can make conformal contact at the high-curvature surface of a single strand of human hair (radius of curvature, ~80 μm). Furthermore, it can be stabilized for small living organisms, such as ants or even microscopic bacteria (~1 μm), for the unique identification of those organisms from their colonies.
Conclusions
We have shown that non-deterministic molecular self-assembly, which occurs under thermal fluctuation, can be used to create nanoscale PUF labels with secure characteristic dimensions and large encoding capacities. The approach provides reliable multipurpose authentication, including electrical and optical responses as cryptographic key generators, with fast validation speeds. Our technique downscales the critical dimensions of PUFs and could provide a generalized platform for advanced authentication systems, with potential use in, for example, hidden miniature identifiers on arbitrary surfaces or distributed multikey integrated authentication systems. The large range of material choices available with PUF labels is also potentially beneficial for ubiquitous labelling, even under harsh electromagnetic-pulse shock or invasive high-energy radiation. The seamless integration of our nanoPUF with the necessary validation tools would be a valuable next step and could lead to versatile applications including hardware-based on-demand cryptographic key generation.
Methods
Materials and characterizations
All the polymers, including BCPs (PS-b-PMMA) and hydroxyl-terminated P(S-r-MMA) random copolymers, were purchased from Polymer Source. Toluene (99.8%, anhydrous) and tetrahydrofuran (99.9%, anhydrous) were purchased from Sigma Aldrich. Hydrofluoric acid (48.0%–51.0%, ACS Reagent) was purchased from J.T.Baker. SYLGARD 184 silicone elastomer base and curing agent were purchased from Sigma Aldrich. Furthermore, 5,000 Å wet-deposited 4-inch P<100> silicon dioxide wafers were purchased from iTASCO. Sticky tape (Scotch Magic Tape) for mechanical stability test was purchased from 3M.
Electrical current measurement
All the electrical characterizations were performed using a Keithley 4200A-SCS instrument. Every cell was applied to a voltage pulse under the same conditions repetitively: voltage amplitude, 1 V; rise and fall time, 1 µs; pulse width, 10 µs, time step, 20 ns; applied voltage, five times.
Polarized optical reflectivity measurement
A polarized optical microscope was developed to obtain the polarized reflectance map in a single shot. To capture the fine reflection features by local orientation, the microscope was equipped with an objective lens (MY10X-803, Thorlabs) and a tube lens for magnification. For polarized detection, the sample was illuminated with linearly polarized light with a wavelength of 633 nm (HeNe laser, Newport), and reflected light from the sample was detected by a complementary metal–oxide–semiconductor camera (DCC3240M, Thorlabs) with a linear polarizer (LPVISE100-A, Thorlabs); the polarization angles in both sides of the source and detector were matched. In the last step, the detected image was normalized by a silver mirror to constitute a polarized reflectance map.
Raman scattering measurement
Raman scattering of the fingerprint metal patterns was observed using a dispersive Raman spectrometer (ARAMIS, Horiba Jobin Yvon). Raman scattering measurements were operated with a 633 nm wavelength laser and 100 ms exposure time.
SEM measurement
Morphology of the self-assembled BCP films and fingerprint metal patterns were observed using SEM (S-4800, Hitachi). To enhance the image contrast and identify each layer of the multilayer stacked sample, SEM measurements were operated in 3 kV in the backscattered electron mode.
Non-deterministic nanopatterning by BCP self-assembly
BCPs and hydroxyl-terminated random copolymers were used as received without any purification. Surface energy of all the silicon oxide substrates was neutrally modified with the hydroxyl-terminated random copolymer brush treatment. Briefly, a neutral brush layer was spin casted from 1 wt% toluene solution onto a silicon substrate after ultraviolet ozone treatment. The substrates were thermally treated at 160 °C in a vacuum for 12 h and then rinsed with toluene to remove unreacted brush molecules. The PS-b-PMMA solution was prepared by blending two PS-b-PMMA BCPs (Mn (the number average molecular weight) values of one set of PS and PMMA blocks, 105 and 106 kg mol−1, respectively, and Mn values of the other set of PS and PMMA blocks, 5 and 5 kg mol−1, respectively) with a 7:3 weight ratio with toluene (total polymer concentration, 1.5 wt%). The BCP thin films were spin casted onto brush-treated silicon oxide and annealed under tetrahydrofuran vapour atmosphere for 1–2 h at room temperature.
Metal fingerprint nanopattern formation
For pattern transfer from BCP thin films onto metal nanopatterns, PMMA lamellar nanoscale domains in the BCP thin film were selectively etched by O2-plasma reactive ion etching, and the desired metal layer was electron-beam evaporated onto the entire substrate surface area with a deposition thickness of 10–20 nm, followed by a lift-off process under sonication.
Transfer printing of metal nanopatterns
A polydimethylsiloxane (PDMS) stamp film was prepared by blending SYLGARD 184 silicone elastomer and curing agent at a 10:1 weight ratio, followed by a crosslinking reaction under a vacuum at 60 °C for 6 h. To peel off the metal fingerprint pattern from the silicone oxide substrate onto the PDMS stamp, the underlying silicone oxide layer was etched by hydrogen fluoride vapour. The metal pattern stabilized at the PDMS surface was stamped at the desired substrates.
Calculation of entropy of BCP self-assembled nanopatterns
Sample entropy
For the given data with length of N, U = [u(1) u(2)…u(N)], we can calculate the sample entropy with a sampling algorithm accompanied by embedding the dimension. For sampling, sample data X(i) with length m can be extracted as follows:
X(i) = [u(i) u(i + 1) u(i + 2)…u(i + m – 1)], i = 1, 2,…N – m + 1.
Using X(i), we can calculate the certain information measure defined as
where d[\({X,X^ \ast }\)] denotes the scalar distance between the two data vectors X and \(X^{\ast}\) and r is the threshold distance. Typically, r is set as r = 0.2σ, where σ denotes the standard deviation of the overall data. Using the statistical sampling measure \(C_i^m(r)\), we can calculate the variation rate of normalized information, \(C_i^m\left( r \right)/(N - m)\), and translate it into the sample entropy SSP as follows:
The distribution of sample entropy of 50 bilayer PUF labels is shown in Extended Data Fig. 1.
LZ entropy
Lempel–Ziv (LZ) entropy relies on the calculation of LZ complexity42. For the calculation of LZ complexity, we converted the raw data into binary data with a threshold set as the overall average. With binary data, different combinations and its occurrence frequency can be translated into information complexity. When N is sufficiently large, it is known that CLZ approaches the Kolmogorov complexity. A detailed calculation algorithm for LZ complexity, CLZ, can be found elsewhere42. With this, we can calculate the LZ entropy SLZ as
The distribution of LZ entropy of 50 bilayer PUF labels is shown in Extended Data Fig. 1.
Permutation entropy
The entropy of information can also be calculated by considering the relative occurrence frequency of the ordinal pattern. To calculate the ordinal pattern frequency, we can apply a sampling method using order number d and delay τ such that
The sample data are coded with the inversion number, which denotes the possible permutation types. For example, \(X_i^{(2)}\) has 3! = 6 possible permutations, which provides six different inversion numbers for the code. The code can be systematically generated with the following relationship:
With a fixed window length W, a vector containing the permutation code P with W components can be generated. For the kth window vector, we can count the occurrence frequency of certain permutation code p, qp(k). Using qp(k), we can calculate the permutation entropy SPE as
The distribution of permutation entropy of 50 bilayer PUF labels is shown in Extended Data Fig. 1.
Conditional permutation entropy
To correct the noise effects on information measure, permutation entropy can be further revised into empirical conditional permutation entropy SCD. This measure considers the delay effects on permutation entropy such that
where pj,l(t) denotes the number of combinations with ordinal pattern code l of the sample data with delay τ, \(X_{t + \tau}^{\left( \tau \right)} = \left[ {x\left( {t + \tau } \right)x\left( {t + 2\tau } \right) \ldots x\left( {t + d\tau + \tau } \right)} \right]\), given the sample data \(X_t^{\left( \tau \right)} = \left[ {x\left( t \right)x\left( {t + \tau } \right) \ldots x\left( {t + d\tau } \right)} \right]\), which has the ordinal pattern code j. The distribution of conditional permutation entropy of 50 bilayer PUF labels is shown in Extended Data Fig. 1.
Calculation of fractal dimensions of BCP self-assembled nanopatterns
We employed generalized entropy at order q to measure the fractal dimension of self-assembled nanopatterns. First, the dimension spectrum Dq can be defined as
where M(r) denotes the number of hypercubes to cover the data or geometric patterns in the mth dimension with a unit hypercube with unit length r, N denotes the total number of signals or points in the data and Ni is the total number of data points in the ith hypercube.
Capacity fractal dimension
In the case of q = 0, the dimension spectrum corresponds to the Kolmogorov capacity or Kolmogorov dimension, which is mathematically identical to the Hausdorff dimension and is expressed as
The capacity fractal dimension is a typical fractal dimension (denoted as FDcap in the paper). The distribution of capacity fractal dimension of 50 bilayer PUF labels is shown in Extended Data Fig. 1.
Information fractal dimension
In the case of q = 1, the dimension spectrum can be expressed as
where the numerator in equation (8), namely, \(- \mathop {\sum }\limits_{{{{{i = 1}}}}}^{{{{{M(r)}}}}} p_i{{{\mathrm{log}}}}p_i\), is the Shannon entropy, and therefore, this fractal dimension corresponds to the information fractal dimension (denoted as FDinf in the paper).
Correlation fractal dimension
In the case of q = 2, the dimension spectrum can be expressed as
where H(x) is the Heaviside function and ρ(xi, xj) is the Chebyshev distance between the two points xi and xj, which is defined as
In equation (9), C(r) denotes the correlation function of the data points with distance r, and therefore, D2 corresponds to the correlation fractal dimension (denoted as FDcor in the paper).
Calculation of orientational order and correlation of self-assembled patterns
We employed a quantitative algorithm for evaluating the local orientation of self-assembled patterns in BCP thin films based on the principal components analysis algorithm. This algorithm analyses the local orientation of each pixel in the noise-processed greyscale electron microscopy images by calculating the local gradient vectors and their maximum likelihood to determine the governing orientation vector43. The local orientation can be represented by local orientation angle θ′, which can be rewritten as the degree of angular deviation from the average angle 〈θ′〉 such that θ = θ′ − 〈θ′〉. Using θ, we calculated the pair correlation function of position-dependent local orientation44,45 g(r) such that
where r and r′ are the 2D position vectors of the pixels in the image and N denotes the total number of pixels in the images. From the statistical point of view, g(r) provides quantitative information on the spatial variation in the orientational order over a certain distance. Therefore, it is possible to obtain a characteristic length scale for the persistence of orientational order such as an orientational-order correlation length Lcorr, which corresponds to the smallest value of r satisfying g(r) = 0, where r = |r|. A plot of the correlation function with the number of overlapped layers is depicted in Extended Data Fig. 1.
Key generation process consisting of digital bits and encoding capacity calculation
Electrical key generation
At least six electrodes are fabricated on the PUF label, and two electrode pairs are selected to measure the electrical current. The number of combinatorial electrode pairs is 6C2, a total of 15. By measuring the resistance value between the electrode pairs and comparing them with an arbitrarily set threshold value (for example, the average of the resistance value), digitalization that assigns 0 or 1 proceeds to generate 15 bits (Extended Data Fig. 2). Consequently, the size of the key space that can be generated with our 15-bit CPR is 215 from a single-PUF label.
Dichroism key generation
In dichroism key generation, the size of the CRP space can be assigned by dividing a reflectance map into multiple sections. As illustrated in Extended Data Fig. 4, the measured reflectance map of 200 μm × 200 μm is divided into 4 × 4 sections with each section size of 50 μm × 50 μm; 15 sections are selected among them. These patterned reflectance values can be multiplied by a normal distribution N(μ = μcentre, σ2 = (12 µm)2), where μcentre is the centre point of each section, to reduce the boundary effect, which helps consistent key generation under a minor shift variation in the image. After integrating the intensity of each section, the signal can be binarized compared with the preassigned threshold (Extended Data Fig. 5). Based on this process, one can generate unique dichroism keys, whose bits follow local polarization properties, depending on the complexity of metallic nanowires, which is extremely difficult to be replicated.
Raman key generation
Raman scattering measurements were carried out after aligning PUF labels using the preformed align keys. After laser exposure, the entire sample area is divided into 15 regions to compare the Raman scattering intensity from each region with an arbitrarily set threshold value (for example, the average of the Raman scattering intensity). Digitalization proceeds to generate 15 bits (Extended Data Fig. 7). The size of the key space that can be generated with our 15-bit CPR is 215 from a single-PUF label.
Overall, the maximum size of the key space can be calculated by multiplying the number of each key space based on an independent mechanism (215 × 215 × 215 = 245 = 3.3 × 1013).
Polarized optical reflectivity simulation study of nanoPUF
To analyse the reflectivity difference in nanoPUFs, electrodynamic simulation (finite-difference time-domain simulation, Lumerical) was conducted for bilayer stacked metallic nanowires depending on the angle between the nanowires and the polarization of incident light. In our simulation, the width and height of the wires are set at 50 and 10 nm, respectively, and the period in the width direction is 100 nm. The simulation results (Extended Data Fig. 3a,b) indicate that the reflectance can be randomized depending on the input polarization or orientation of the nanowires.
Plasmonic resonance simulation study of nanoPUF
To analyse the plasmonic resonance effect in nanoPUFs, electrodynamic simulation (finite-difference time-domain simulation, Lumerical) was conducted for bilayer stacked metallic nanowires depending on the angle between the nanowires and the polarization of incident light, with respect to the direction of the bottom wire layer. In our simulation, the width and height of the wires are set at 50 and 10 nm, respectively, and the period in the width direction is 100 nm. The simulation result (Extended Data Fig. 6) indicates that localized surface plasmon can be coupled among the complex interlocked metallic wires to induce a strong electric-field enhancement in the nanogap. Depending on the input polarization or orientation of nanowires, electric-field enhancement can be varied to affect the Raman enhancement (proportional to |E|4; Fig. 2i); the Raman enhancement was calculated by integrating |E|4 of a region smaller than 500 nm in depth of the substrate.
Calculation of PUF parameters
The test code for statistical analysis was built in the Python version 3.9 environment. The Hamming distance between two data strings is the number of different bits at which the corresponding symbols are different, and the Hamming weight is the number of zeroes in an n-bit response38,39.
Uniqueness
A PUF must be distinguishable from other PUFs obtained under the same fabrication process; however, the PUF should also be different by 50% from other PUFs. This metric is evaluated using the Hamming distance (HD) as below:
where Ri(n) and Rj(n) are the n-bit responses of the ith and jth PUF, respectively, and k is the total number of PUFs.
Bit aliasing
The responses from different PUFs must be different by 50% to have identical responses. This metric is evaluated using the Hamming weight (HW) as below.
where Ri(j) is the jth bit in an n-bit response from the ith PUF and k is the total number of PUFs.
Reliability
PUF must be able to generate a consistent response. This metric is evaluated using the Hamming distance as below:
where \(R_i^l\left( n \right)\) is the n-bit response from the ith PUF at the lth trial, T is the number of trials and k is the total number of PUFs.
Calculation of number of distinguishable nanoidentifiers
By assuming that the confined area is a 1 μm × 1 μm square and the period (λ, centre-to-centre distance) of the BCP lamellar pattern is 60 nm, we were able to create a grid with a spacing of 60 nm inside the 1 μm2 square16. Then, the effective possible positions, where minutia can exist, is the number of intersections inside the square, which is approximately 280 (17 horizontal lines and 17 vertical lines in the square). Additionally, we assume that the practical producible average minutiae density in 1 μm2 is 10 (85 termination points in 8.5 μm2) for termination (ridge ending) (Extended Data Fig. 10). The estimated maximum code capacity of one layer is 280C10 ≅ 6.937 × 1017 under the assumption that there is only one type of minutiae of termination. Finally, when two fingerprint patterns are stacked, the maximum number of distinguishable nanoidentifiers can be calculated by multiplying the number of each distinguishable layer owing to the morphological independence of each layer. Therefore, the maximum number of distinguishable nanoidentifiers of the bilayer PUF label is about 4.8 × 1035.
Designation of noise level
Here Inoise = I0(1 + Neff(rand – 0.5)), where I0 is the initial greyscale pixel value, Inoise is the pixel value under artificial noise, Neff is the factor controlling the noise effect and rand denotes a random number extracted from a uniform distribution between 0 and 1.
Layer-separation image processing for bilayer stacked BCP patterns
For the minutiae point extraction of each layer from bilayer stacked BCP nanopattern images, layer separation is required before other image processing. As shown in Extended Data Fig. 9, the pixel intensities in bilayer stacked BCP images follow a multimodal distribution, where the distinctive intensity peaks correspond to empty space (dark pixels), bottom layer (middle peak) or the cross-points of two layers (bright pixels). The pixel for only the second (top) layer is brighter in greyscale intensity than that of only the first (bottom) layer, but little darker than the cross-points. Taking the intensity of the middle peak as a threshold, the top layer image can be separated from the original image. The bottom layer is revealed after taking off the first top layer and then recovering the crossing points—the pixels have a higher intensity next to the brightest peak. After separating the two layers, the image of each layer is treated by a conventional fingerprint recognition process, consisting of image normalization, segmentation, enhancement using a Gabor filter and line thinning (skeletonization), to extract the minutiae points, such as termination, bifurcation and crossing points.
Data availability
The data that support the findings of this study are available from the corresponding authors upon reasonable request.
Change history
04 August 2022
A Correction to this paper has been published: https://doi.org/10.1038/s41928-022-00829-4
References
Chung, H. U. et al. Binodal, wireless epidermal electronic systems with in-sensor analytics for neonatal intensive care. Science 363, eaau0780 (2019).
Niu, S. et al. A wireless body area sensor network based on stretchable passive tags. Nat. Electron. 2, 361–368 (2019).
Yu, X. et al. Skin-integrated wireless haptic interfaces for virtual and augmented reality. Nature 575, 473–479 (2019).
Neuman, B. C. & Ts’o, T. Kerberos: an authentication service for computer networks. IEEE Commun. Mag. 32, 33–38 (1994).
Beckmann, N. & Potkonjak, M. Hardware-based public-key cryptography with public physically unclonable functions. in Information Hiding 206–220 (Springer, 2009).
Kune, D. F. et al. Ghost talk: mitigating EMI signal injection attacks against analog sensors. In 2013 IEEE Symposium on Security and Privacy 145–159 (IEEE, 2013).
Pappu, R. et al. Physical one-way functions. Science 297, 2026–2030 (2002).
Maes, R. & Verbauwhede, I. in Towards Hardware-Intrinsic Security: Foundations and Practice (eds Sadeghi, A.-R. & Naccache, D.) 3–37 (Springer, 2010).
Becker, G. T. The gap between promise and reality: on the insecurity of XOR arbiter PUFs. in Cryptographic Hardware and Embedded Systems—CHES 2015 (eds Güneysu, T. & Handschuh, H.) 535–555 (Springer, 2015).
Gao, Y. et al. Memristive crypto primitive for building highly secure physical unclonable functions. Sci. Rep. 5, 12785 (2015).
Arppe, R. & Sørensen, T. J. Physical unclonable functions generated through chemical methods for anti-counterfeiting. Nat. Rev. Chem. 1, 0031 (2017).
Carro-Temboury, M. R. et al. An optical authentication system based on imaging of excitation-selected lanthanide luminescence. Sci. Adv. 4, e1701384 (2018).
Gao, Y. et al. Physical unclonable functions. Nat. Electron. 3, 81–91 (2020).
Arppe-Tabbara, R. et al. Versatile and validated optical authentication system based on physical unclonable functions. ACS Appl. Mater. Interfaces 11, 6475–6482 (2019).
Nakayama, K. & Ohtsubo, J. Optical security device providing fingerprint and designed pattern indicator using fingerprint texture in liquid crystal. Opt. Eng. 51, 040506 (2012).
Bae, H. J. et al. Biomimetic microfingerprints for anti-counterfeiting strategies. Adv. Mater. 27, 2083–2089 (2015).
Wolterink, T. A. W. et al. Programmable two-photon quantum interference in 103 channels in opaque scattering media. Phys. Rev. A 93, 053817 (2016).
Gu, Y. et al. Gap-enhanced Raman tags for physically unclonable anticounterfeiting labels. Nat. Commun. 11, 516 (2020).
Martinez, P. et al. Laser generation of sub-micrometer wrinkles in a chalcogenide glass film as physical unclonable functions. Adv. Mater. 32, 2003032 (2020).
Devadas, S. et al. Design and implementation of PUF-based ‘unclonable’ RFID ICs for anti-counterfeiting and security applications. In 2008 IEEE International Conference on RFID 58–64 (IEEE, 2008).
Maiti, A. & Schaumont, P. Improving the quality of a physical unclonable function using configurable ring oscillators. In 2009 International Conference on Field Programmable Logic and Applications 703–707 (IEEE, 2009).
Scholz, A. et al. Hybrid low-voltage physical unclonable function based on inkjet-printed metal-oxide transistors. Nat. Commun. 11, 5543 (2020).
Bates, F. S. & Fredrickson, G. H. Block copolymer thermodynamics: theory and experiment. Annu. Rev. Phys. Chem. 41, 525–557 (1990).
Harrison, C. et al. Mechanisms of ordering in striped patterns. Science 290, 1558–1560 (2000).
Thurn-Albrecht, T. et al. Ultrahigh-density nanowire arrays grown in self-assembled diblock copolymer templates. Science 290, 2126–2129 (2000).
Jeong, S.-J. et al. Universal block copolymer lithography for metals, semiconductors, ceramics, and polymers. Adv. Mater. 20, 1898–1904 (2008).
Meitl, M. A. et al. Transfer printing by kinetic control of adhesion to an elastomeric stamp. Nat. Mater. 5, 33–38 (2006).
Kim, J. Y. et al. Highly tunable refractive index visible-light metasurface from block copolymer self-assembly. Nat. Commun. 7, 12911 (2016).
Yuhang, D. et al. A study of hand vein recognition method. In IEEE International Conference Mechatronics and Automation 4, 2106–2110 (IEEE, 2005).
Kumar, A. & Prathyusha, K. V. Personal authentication using hand vein triangulation and knuckle shape. IEEE Trans. Image Process. 18, 2127–2136 (2009).
Komiyama, H. et al. Binary nanoparticles coassembly in bioinspired block copolymer films: a stepwise synthesis approach using multifunctional catechol groups and magneto-optical properties. ACS Appl. Nano Mater. 1, 1666–1674 (2018).
Gates, B. D. et al. New approaches to nanofabrication: molding, printing, and other techniques. Chem. Rev. 105, 1171–1196 (2005).
Smith, B. W. & Suzuki, K. Microlithography: Science and Technology (CRC Press, 2020).
Mutiso, R. M. et al. Integrating simulations and experiments to predict sheet resistance and optical transmittance in nanowire films for transparent conductors. ACS Nano 7, 7654–7663 (2013).
Zhao, Y. et al. Twisted optical metamaterials for planarized ultrathin broadband circular polarizers. Nat. Commun. 3, 870 (2012).
Moskovits, M. Surface-enhanced spectroscopy. Rev. Mod. Phys. 57, 783–826 (1985).
Stiles, P. L. et al. Surface-enhanced Raman spectroscopy. Annu. Rev. Anal. Chem. 1, 601–626 (2008).
Maiti, A. et al. A systematic method to evaluate and compare the performance of physical unclonable functions. in Embedded Systems Design with FPGAs 245–267 (Springer, 2013).
Maiti, A. et al. A large scale characterization of RO-PUF. In 2010 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST) 94–99 (IEEE, 2010).
Xiao, Q. & Raafat, H. Fingerprint image postprocessing: a combined statistical and structural approach. Pattern Recognit. 24, 985–992 (1991).
Farina, A. et al. Fingerprint minutiae extraction from skeletonized binary images. Pattern Recognit. 32, 877–889 (1999).
Lempel, A. & Ziv, J. On the complexity of finite sequences. IEEE Trans. Inf. Theory 22, 75–81 (1976).
XiaoGuang, F. & Milanfar, P. Multiscale principal components analysis for image local orientation estimation. In Conference Record of the Thirty-Sixth Asilomar Conference on Signals, Systems and Computers 1, 478–482 (IEEE, 2002).
Ullner, M. & Woodward, C. E. Orientational correlation function and persistence lengths of flexible polyelectrolytes. Macromolecules 35, 1437–1445 (2002).
Murphy, J. N. et al. Automated defect and correlation length analysis of block copolymer thin film nanopatterns. PLoS ONE 10, e0133088 (2015).
Acknowledgements
Funding: This research was supported by the National Creative Research Initiative (CRI) Center for Multi-Dimensional Directed Nanoscale Assembly (2015R1A3A2033061) through the National Research Foundation of Korea (NRF) funded by the Ministry of Science, Nano·Material Technology Development Program through the NRF funded by the Ministry of Science and ICT (2022M3H4A1A02046445) and the Development of Long-Distance Plasmonic Waveguide Materials Working for Near-IR Band (KRF2021R1F1A106405111) funded by the NRF.
Author information
Authors and Affiliations
Contributions
B.H.K. proposed the initial idea for this work. J.H.K. principally performed the overall experiments and wrote the manuscript. S.J.K. analysed the physical properties of the PUF patterns and performed image processing to demonstrate the functionalities of patterns. S.N. and S.-W.S. performed the fingerprint recognition analysis of patterns. S.J. and J.S. performed the optical measurement of patterns and simulation study for plasmonic resonance. J.H.I. and K.M.K. performed the electrical measurement of patterns and calculated the PUF parameters. H.M.J., K.H.H., G.G.Y. and H.J.C. contributed to the BCP pattern formation and characterization. B.H.K. and S.O.K. supervised the entire research project and manuscript preparation.
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing interests.
Peer review
Peer review information
Nature Electronics thanks Thomas Just Sørensen and the other, anonymous, reviewer(s) for their contribution to the peer review of this work.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Extended data
Extended Data Fig. 1 Calculation of physical properties of BCP self-assembled nanopatterns.
a, Distribution of sample entropy, Lempel-Ziv entropy, permutation entropy, conditional entropy and capacity fractal dimension of fifty bi-layer PUF labels. b, Orientation color mapping images of monolayer pattern (left) and bi-layer stacked pattern (right). Scale bar: 500 nm. c, Plot of correlation function with the number of overlapped layers.
Extended Data Fig. 2
Electric-key generation process of PUF labels.
Extended Data Fig. 3
Random distribution of a, reflectance intensity and b, Raman scattering intensity.
Extended Data Fig. 4 Intensity distribution of reflectance for a polarized incidence beam.
a, Simulation result for reflectance in nanoPUF. The input polarization and angle between wires are 180° and 10°, respectively. Give 1 when larger than threshold reflectance and 0 when less. Threshold reflectance: 0.225 (a.u.). b, Reflectance measurements at different selected areas of PUF labels with different beam size (from 100 mm to 25 mm) and wavelength (from 400 nm to 800 nm).
Extended Data Fig. 5 Birefringence-key generation process of PUF labels.
a, Dividing reflectance map into multiple sections. b, Reflection-key generation process of PUF labels.
Extended Data Fig. 6 Simulation result for localized surface plasmonic resonance in nanoPUF.
The input polarization and angle between wires are 90° and 10°, respectively.
Extended Data Fig. 7
Raman scattering-key generation process of PUF labels.
Extended Data Fig. 8 Challenge-response operation of nanoPUF.
a, Uniqueness test. b, Challenge distinguishing capability test. c, Noise robustness test of 10 nano-identifiers.
Extended Data Fig. 9 Layer separation of overlapped patterns.
a, Layer separation of overlapped patterns with various threshold levels of greyscale. b, Minutiae point extraction with conventional fingerprint recognition process.
Extended Data Fig. 10 Morphological defects in BCP self-assembly patterns.
a, Ridge ending point density of termination minutia in a selected nanoPUF pattern area. Scale bar: 500 nm. b, Schematically illustrated images for the different defects in BCP self-assembly patterns.
Supplementary information
Supplementary Information
Supplementary Fig. 1.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Kim, J.H., Jeon, S., In, J.H. et al. Nanoscale physical unclonable function labels based on block copolymer self-assembly. Nat Electron 5, 433–442 (2022). https://doi.org/10.1038/s41928-022-00788-w
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1038/s41928-022-00788-w
This article is cited by
-
Intelligent block copolymer self-assembly towards IoT hardware components
Nature Reviews Electrical Engineering (2024)
-
A water-soluble label for food products prevents packaging waste and counterfeiting
Nature Food (2024)
-
All-silicon multidimensionally-encoded optical physical unclonable functions for integrated circuit anti-counterfeiting
Nature Communications (2024)
-
Dynamic multicolor emissions of multimodal phosphors by Mn2+ trace doping in self-activated CaGa4O7
Nature Communications (2024)
-
Printed smart devices for anti-counterfeiting allowing precise identification with household equipment
Nature Communications (2024)