Abstract
We present a high-dimensional measurement device-independent (MDI) quantum key distribution (QKD) protocol employing biphotons to encode information. We exploit the biphotons as qutrits to improve the tolerance to error rate. Qutrits have a larger quantum system; hence they carry more bits of classical information and have improved robustness against eavesdropping compared to qubits. Notably, our proposed protocol is independent of measurement devices, thus eliminating the possibility of side-channel attacks. Also, we employ the finite key analysis approach to study the performance of our proposed protocol under realistic conditions where finite resources are used. Furthermore, we simulated the secret key rate for the proposed protocol in terms of the transmission distance for different fixed amounts of signals. The results prove that this protocol achieves a considerable secret key rate for a moderate transmission distance of 90 km by using \(10^{16}\) signals. Moreover, the expected secret key rate was simulated to examine our protocol’s performance at various intrinsic error rate values, \(Q=(0.3\%,0.6\%,1\%)\) caused by misalignment and instability due to the optical system. These results show that reasonable key rates are achieved with a minimum data size of about \(10^{14}\) signals which are realizable with the current technology. Thus, implementing MDI-QKD using finite resources while allowing intrinsic errors due to the optical system makes a giant step forward toward realizing practical QKD implementations.
Similar content being viewed by others
Introduction
Quantum key distribution (QKD) is a procedure for establishing symmetric cryptographic keys between legitimate participants by distributing quantum states1. In principle, QKD provides information-theoretic security, guaranteed by quantum mechanical laws2. Notably, QKD has developed from mere theoretical security proofs to commercial applications over the past two decades. However, practical QKD has yet to attain its full deployment owing to security lapses in the theoretical security proofs that arise from certain assumptions about the sources or devices belonging to Alice and Bob3. For example, QKD protocols depend on trusted device scenarios, i.e., it is assumed that no information is leaked from the transmitters or the senders, which is very challenging to guarantee in practice. This creates a gap between theory and experimental implementations, opens loopholes, and leads to various possible attacks on the QKD systems4. Moreover, during implementations, QKD protocols depend on trusted device scenarios, and this assumption allows the protocols to achieve effective rates. Unfortunately, this provides an opportunity for harmful attacks, such as the side-channel attacks5. As a result, besides the enormous theoretical and experimental quantum cryptography progress, some work remains before fully deploying QKD in commercial applications. Hence, the device-independent (DI) QKD provides an improved security degree compared to conventional QKD schemes by lessening the number of assumptions required concerning the physical devices used6.
The security of the DI-QKD depends on the violation of Bell inequalities7. However, the DI-QKD needs the loophole-free Bell experiments, making it impossible to realize using existing technologies. Recent demonstrations of various attacks highlight this on practical QKD systems5. As a result, the measurement device-independent (MDI) QKD provides an improved practical solution intrinsically insensitive to entire attacks caused by side channels. These attacks target a measurement device and remove the detection-associated security loopholes8,9. Furthermore, the participating parties are connected by an untrusted relay for an MDI-QKD, leading to a considerable gain in transmission distances compared to the traditional QKD schemes. Thus, this makes these set-ups ideally suitable for quantum networks. Moreover, some experimental demonstrations using MDI-QKD have been conducted in Refs.10,11. However, the practical MDI-QKD still experiences relatively low key rates compared to the conventional BB84 protocol due to the requirement of Bell-state measurements. Apart from these advances, adopting QKD widely has been a challenge, and it has been demonstrated that large-scale deployment will likely require chip-based devices for improved performance, miniaturization, and enhanced functionality12,13,14,15,16,17,18. Most significantly, these integrated photonic chips offer numerous benefits such as low cost, low power consumption, and well-established batch fabrication techniques19.
To encode information in a QKD protocol, the parties must choose a certain degree of freedom, for instance, polarization or phase properties of single-photon as quantum states1,20. This means one classical bit of information is encoded onto each quantum state, resulting in limited secret key rates21. As a result, high dimensional encoding presents a promising solution to address the limitation of low secret key rates in QKD22. High dimensional quantum systems allow the communicating parties in QKD to encode information beyond one bit per signal23. The secret key rate, which may be limited by inevitable factors such as losses in the channel, and source and detector flaws, can be significantly improved by high-dimensional encoding where each photon can encode up to \({\text {log}}_{2}d > 1\) bits. This allows a considerable amount of information to be sent in a given transmission of the signal in the channel. Notably, previous studies indicate that the resistance to noise of the protocols increases when one increases the dimension, both for one-way24,25,26 and two-way post-processing27. Furthermore, compared to qubit operations, high dimensional quantum states are robust against noise due to the background and hacking attacks24.
Qudits have been proven to be robust against quantum cloning compared to their qubit counterparts28. Thus, they are an excellent illustration of the effectiveness of high-dimensional quantum systems since they lead to higher error thresholds making it challenging for the eavesdropper to intercept a high-dimensional QKD scheme. Owing to this, the merits of several degrees of freedom have been examined for high dimensional QKD, which includes position-momentum29, orbital angular momentum23,30,31,32,33 and time energy34,35,36,37,38,39,40,41 and MDI-QKDs employing high-dimensional quantum states42,43,44. Another approach to realizing high dimensional encoding is using biphotons corresponding to a pair of indistinguishable photons with qutrit (i.e., a three-level quantum system) representation. Biphotons or pairs of entangled photons form a two-photon light and constitute one of the most critical states of light in recent quantum information and quantum optics45,46. The generation, manipulation, and detection procedures for single-mode biphoton beams with linear optics have been demonstrated in Refs.47,48,49.
We propose an MDI-QKD protocol that encodes information on qutrit states by exploiting the polarization state of single-mode biphoton field. Using biphotons as qutrits enhances the attainable secret key rate and security due to improved information capacity per photon and the high noise tolerance45. To examine the practicality of the proposed protocol, we investigate the finite-key bounds against the general attacks based on entropic uncertainty relations. Moreover, this security analysis pertains to the implementation using the decoy states. This enables the proposed protocol to be secure against Photon-Number-Splitting (PNS) attacks1. For the finite-key study, the statistical fluctuations are catered by leveraging the large deviation theory, particularly the multiplicative Chernoff bound50. This bound provides the tightest bounds on estimated parameters for the high-loss regime. More recently, a similar work on three-dimensional MDI-QKD was proposed by Jo et al.51. Their proposed protocol exploits the time bin entangled qutrit states to encode information and employs a tripartite qutrit discrimination setup. The setup relies on a tritter and non-destructive photon number measurements to filter the states for Bell state measurements. Conversely, our proposed MDI-QKD protocol utilizes the Mach Zehnder interferometer to generate biphoton states and the Brown Twiss schemes to achieve Bell state measurements. While the scheme in Ref.51 is more efficient in terms of fewer resources used in Charlie’s measurement site; it involves non-destructive measurements, which may open up a possibility of side-channel attacks. Another noticeable difference is that our work considers finite key analysis and studies the performance of the qutrit MDI-QKD under realistic conditions by determining the key rate as a function of transmission distance. The work in Ref.51 only provides tolerable error bounds that allow one to distill a secure key. Therefore, apart from this introduction, the following section describes the proposed protocol, while the next section provides the security proof based on the entropic uncertainty principle. After that, we simulate the performance of our protocol to demonstrate its feasibility and conclude this paper.
Protocol definition
Biphotons
The pure polarization state for a single-mode biphoton field is expressed according to the following45,47:
where \(c_{i}=|c_{i}|e^{i\phi _{i}}\) are complex amplitudes. The notation \(|n_{h},n_{v}\rangle\) represents a state that consists of n photons in the horizontal (h) mode as well as n photons in the vertical (v) polarization mode. Therefore, from Eq. (1), we can observe that a biphoton has a three-level quantum system (qutrit) representation, hence its use for ternary quantum information encoding. To realize the QKD protocol, one needs at least two mutually unbiased bases (MUB) from available \(d+1\) MUBs. The two orthonormal bases \({\mathscr {M}}_{1}=|\phi \rangle _{i}\), where \(i \in \{0,1,2\}\) and \({\mathscr {M}}_{2}=|\Phi \rangle _{j}\), where \(j \in \{0,1,2\}\) for a 3-dimensional Hilbert space \({\mathscr {H}}_{3}\) are considered mutually unbiased when all pairs of basis vectors \(|\phi \rangle _{i}\) and \(|\Phi \rangle _{j}\) satisfies
For biphotons, the standard basis is expressed in terms of the orthonormal states \(|\alpha \rangle =|2,0\rangle\), \(|\beta \rangle =|0,2\rangle\) and \(|\gamma \rangle =|1,1\rangle\). The states \(|2,0\rangle\) and \(|0,2\rangle\) represent type-I phase matching, while \(|1,1\rangle\) corresponds to type II phase matching, and one can obtain these biphoton fields through spontaneous parametric down-conversion (SPDC). The other three MUBs are realized from the superposition of the basis vectors as follows
and
where \(\omega =\exp (i2\pi /2)\). In our scenario, to realize high dimensional encoding with biphotons, we propose an MDI-QKD protocol exploiting two Fourier transformed bases, \({\mathscr {M}}_{1}=\{|\acute{\alpha }\rangle ,|\acute{\beta }\rangle ,|\acute{\gamma }\rangle \}\) and \({\mathscr {M}}_{2}=\{|\bar{\alpha }\rangle ,|\bar{\beta }\rangle ,|\bar{\gamma }\rangle \}\).
Preparation of states
Alice (Bob) starts by randomly preparing qutrit states from two mutually unbiased bases \({\mathscr {M}}_{1}=\{|\acute{\alpha }\rangle ,|\acute{\beta }\rangle ,|\acute{\gamma }\rangle \}\) and \({\mathscr {M}}_{2}=\{|\bar{\alpha }\rangle ,|\bar{\beta }\rangle ,|\bar{\gamma }\rangle \}\). The biphoton states \(\{|\acute{\alpha }\rangle ,|\bar{\alpha }\rangle \}\), \(\{|\acute{\beta }\rangle ,|\bar{\beta }\rangle \}\) and \(\{|\acute{\gamma }\rangle ,|\bar{\gamma }\rangle \}\) are assigned bit values 0, 1 and 2, (the value 2 is converted to binary digit during sifting to obtain two bits per signal) respectively. The states are prepared using a Mach–Zehnder interferometer consisting of 3 arms and appropriate non-linear crystals in each arm. This is illustrated in Fig. 1.
Mach–Zehnder interferometer set up used by Alice and Bob for biphoton state preparation. The laser beam is pumped towards a non-symmetric beam-splitter that transmits 2/3 and reflects 1/3 of the beam through the long and short arms. The \((\lambda /2)_{i}\) represents the halve wave plates for manipulating the amplitude, \(c_{i}\) of the states. The phase shifters (PS. 1 and PS. 2) introduce relative phases between the states. The DM denotes the dichroic mirror, which transmits two biphotons created using type I non-linear crystals from the long arm of the interferometer and reflect the pump from the short arm towards the type II non-linear crystal for the creation of state \(|1,1\rangle\).
The laser beam is pumped onto a non-symmetric beamsplitter that transmits two-thirds of the beam through the interferometer’s long arm and reflects the other beam via the short arm. The beam in the long arm is pumped towards the type I non-linear crystals for generating states \(|2,0\rangle\) and \(|0,2\rangle\) resulting in a superposition
with \(e^{i\phi _{31}}\) representing the relative phase between the states realized through phase shifters. The half-wave plate is used for manipulating the amplitudes of these states. A cut-off flitter is employed to remove the pump. After passing through the filter, the states arrive at the piezoelectric translator, where the phase shift, \(\phi _{2}\), is introduced between the superposition of states defined in Eq. (12) and the state \(|1,1\rangle\). The reflected beam traveling through the short arm is guided towards the half-wave plate to control the amplitude corresponding to the state \(|1,1\rangle\). The pump is reflected at the dichroic mirror towards the type II non-linear crystals to create the state \(|1,1\rangle\). The type I biphotons from the long arm of the interferometer is transmitted via the dichroic mirror. Thus, at the interferometer’s output, we have the superposition of three basic states in Eq. (1), which are then propagated through the insecure channel to the measurement site. Different states from two mutually unbiased bases are produced by adjusting the phase shifters and halve wave plates according to Table 1.
Measurement
Charlie allows the biphotons from Alice and Bob to interfere in a symmetric beam-splitter upon receiving the states. As a result, the Hong Ou Mandel effect occurs (see Fig. 2). The beam-splitter action can be described as follows. Let us assume Alice’s biphoton state at the input arm of the beam-splitter is denoted by \(|\psi \rangle _{1}\), then its transformation can be described as
Similarly if Bob’s state at the input arm is \(|\acute{\psi }\rangle _{2}\) then the action of the beam-splitter is described as
where \(a^{\dagger }_{i}\) denotes the creation operator and \(|\bar{x}\rangle\) is the reflected state. The overall beam-splitter transformations are described as
where
and
The subscripts 1, 2, and 3, 4 denote a beam-splitter’s input and output ports, respectively. According to the Hong Ou Mandel interference, identical photons will leave the beam-splitter from a similar output port, and distinguishable photons from both input ports of the beam-splitter will exit in both output ports. Let Alice and Bob choose a similar biphoton states \(|\acute{\alpha }_{A}\rangle\) and \(|\acute{\alpha }_{B}\rangle\), respectively. Therefore, based on the Hong Ou Mandel interference, the state \(|\Psi ^{-}\rangle\) in Eq. (17) will disappear, and the resultant state is
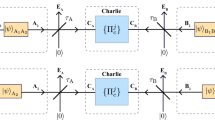
The generic measurement set up for our proposed MDI-QKD. Alice and Bob start by preparing the biphoton states from two mutually unbiased bases and send them through the unsecured channel to Charlie. Charlie allows the states to interfere in the symmetric beam-splitter (BS) upon receiving the states. The photons are directed towards the tritter and eventually detected in the Brown Twiss scheme (mode sorter).
Illustration of the measurement set up at Charlie’s site. The incoming biphotons interfere in the beam-splitter (BS) and exit through either of two output ports towards the two non-symmetric beam-splitter (NPBS), where they are further split into three channels and directed towards the tritter. The tritter setup shown in the upper left is a three-input-output port splitter. It comprises three conventional beam-splitters (BS), four-phase shifters (PS), and a mirror. The output ports of the tritter are linked with three Brown Twiss schemes for detecting the three basic states \(|\alpha \rangle\), \(|\beta \rangle\), and \(|\gamma \rangle\). Each Brown Twiss scheme consists of a non-symmetric beam-splitter (NPBS), wave plates (WP), polarization analyser (A), and detectors (D\({\textbf{P}}_{i}\)) where \({\textbf{P}} \in \{H,V\}\) represents polarization mode and subscript i denotes single photons forming biphotons. The abbreviation c.c corresponds to coincident counting or detection.
Therefore, identical biphotons will always appear in the same output arm of BS (3rd arm or 4th arm). Otherwise, if Alice and Bob prepare opposite biphotons, both \(|\Psi ^{-}\rangle\) and \(|\Psi ^{-}\rangle\) will exist, and there is a non-zero probability that the biphotons will exit at both output arms of the BS. The photons that exit the beam-splitter are transmitted toward the three input-output ports beam-splitter (tritter). The photons are directed toward the two non-polarizing beam-splitters to separate them into three channels from each output of the symmetric beam-splitter connected to each input of the two tritters (see Fig. 3). The probability of photons exiting through any of the output ports of the tritter is governed by the unitary matrix
In a case where each input of the tritter is injected with biphoton state, the resultant output state after the evolution induced by \({\mathscr {U}}\) is given by
where \(|1,1,1\rangle\) corresponds to one biphoton state in each input or output of the tritter, and \(|3,0,0\rangle\) represents three biphoton states exiting through one output port and no photons in the other two output ports. The output ports of each tritter are linked with three biphoton mode sorters. At the output of each tritter, the biphoton states from Alice and Bob, are directed towards the Brown Twiss schemes which are tuned to measure the standard basis biphoton modes \(|\alpha \rangle\), \(|\beta \rangle\) and \(|\gamma \rangle\). Each Brown Twiss scheme made up of polarization filters in the arms. The filters comprise a pair of phase-plates and a polarization analyzer used to realize the polarization states of single-photons creating the biphoton. Each Brown Twiss scheme is tuned to detect a certain polarization state of biphoton by setting wave plates (\(\lambda /4\) plate, \(\lambda /2\) plate) to angle positions that realize desired polarization and setting polarization analyser to allow the desired polarization to pass through. Different angle settings for wave plates are shown in Table 2. When a Brown Twiss scheme is tuned to the settings for detection of specific polarization states, the orthogonal biphoton states cannot result in coincidence detection. For instance, in the Brown Twiss scheme used to detect \(|\beta \rangle\) biphoton mode, there are two detectors for the horizontal polarization contributions from Alice and Bob’s biphoton states which are labelled as \(D_{HA}\) and \(D_{HB}\). Furthermore, there are two detectors for measuring the vertical polarization contributions of biphoton states from Alice and Bob labelled as \(D_{VA}\) and \(D_{VB}\) as shown in Fig. 3. Similarly, appropriate parameters are set in the filters of both arms of the Brown Twiss scheme for detecting other states to allow coincidence detection. Note that states prepared by Alice and Bob are a superposition of the three basic states \(|\alpha \rangle\), \(|\beta \rangle\) and \(|\gamma \rangle\). Therefore, a successful Bell state measurement in the Brown Twiss scheme corresponds to the observation of precisely 12 detectors being triggered; for instance, \(D_{H1A}\), \(D_{H1B}\), \(D_{H2A}\) and \(D_{H2B}\) (associated with \(|\alpha \rangle _{L}\) biphoton mode), \(D_{H3A}\), \(D_{H3B}\), \(D_{V4A}\) and \(D_{V4B}\) (associated with \(|\beta \rangle _{L}\) biphoton mode) and \(D_{V5A}\), \(D_{V5B}\), \(D_{V6A}\) and \(D_{V6B}\) (associated with \(|\gamma \rangle _{L}\) biphoton mode). These measurement results can be simplified in terms of Bell measurements as \(\frac{1}{\sqrt{2}}(D_{\alpha _{L}}D_{\beta _{L}}D_{\gamma _{L}}+D_{\alpha _{R}}D_{\beta _{R}}D_{\gamma _{R}})\) which represent a click in detectors on the left-hand side for \(|\alpha \rangle\), \(|\beta \rangle\) and \(|\gamma \rangle\) modes (i.e.,\(D_{\alpha _{L}}\) denotes coincidence detection in detectors of \(|\alpha \rangle\) mode) or a click on the right-hand side for \(|\alpha \rangle\), \(|\beta \rangle\) and \(|\gamma \rangle\) modes detectors. A conclusive result is given by click in detectors of the mode sorters on the left-hand side or the right-hand side only. The other Bell state measurements result in inconclusive measurement results, e.g., \(\frac{1}{\sqrt{2}}(D_{\alpha _{L}}D_{\beta _{L}}D_{\gamma _{R}}+D_{\alpha _{R}}D_{\beta _{R}}D_{\gamma _{L}})\). The results are provided in Table 3.
Sifting
Alice and Bob post select states prepared using the same basis when Charlie reports a conclusive event and discards the rest of the data. A conclusive event corresponds to a case where there is a coincidence detection in three Brown Twiss schemes (linked to the same tritter) for three different basis states \(|\alpha \rangle\), \(|\beta \rangle\) and \(|\gamma \rangle\). This occurs when Alice and Bob have prepared the same biphoton state. We define the set \({\mathscr {K}}\) comprising of biphoton signals if Alice and Bob selected the key basis \({\mathscr {M}}_{1}\) and Charlie gets a successful measurement. Similarly, \({\mathscr {C}}\) is a set of post-selected signals from measurement basis \({\mathscr {M}}_{2}\), which are used for monitoring the presence of an adversary. The protocol repeats the first steps until the sifting conditions \(|{\mathscr {K}}| \ge n\) and \(|{\mathscr {C}}| \ge m\) are met for all N signals prepared by Alice and Bob.
Parameter estimation
The participating parties, Alice and Bob, make use of the random bits obtained from \({\mathscr {K}}\) to create a raw key consisting of bit strings \({\textsf{K}}_{A}\) and \({\textsf{K}}_{B}\). Then, they compute the average error \(\frac{1}{|{\mathscr {C}}|} \sum a_{i}\oplus b_{i}\) where \(a_{i}\) and \(b_{i}\) are Alice and Bob’s bit values.
Error correction
The information reconciliation scheme is performed, which leaks at least \({\text {leak}}_{EC}\) bits of classical error-correction data. Alice evaluates a bit string (i.e., a hash) measuring length \(\log _{2}(1/\varepsilon _{\textrm{cor}})\) using a random \({\text {universal}}_{2}\) hash function to \({\textsf{K}}_{A}\). Then, Alice transmits the choice of the function, including the hash to the receiver, Bob. When the hash of \({\textsf{K}}_{B}\) does not match the hash of \({\textsf{K}}_{A}\), the protocol is aborted.
Privacy amplification
During this step, Alice uses a random \({\text {universal}}_{2}\) hash function for extracting the length \(\ell\) bits of secret key \({\textsf{S}}_{A}\) from \({\textsf{K}}_{A}\). Bob exploits a similar hash function for extracting the key \({\textsf{S}}_{B}\) of length \(\ell\) from \({\textsf{K}}_{B}\).
Security analysis
We consider the realistic scenarios where participating parties exchange finite signals N and determine the statistical fluctuations of finite-size key effects. The security analysis follows the proofs provided in Refs.52,53,54,55,56 based on a universally composable framework. The protocol creates a pair of key bit strings \({{\textsf{S}}_{{\textsf{A}}}}\) for Alice and \({{\textsf{S}}_{{\textsf{B}}}}\) for Bob. These key bit strings measure length \(\ell\) and must satisfy the correctness and secrecy requirements so that the protocol can be considered secure. Based on the composability requirement, the QKD protocol is considered to be correct when \({{\textsf{S}}_{{\textsf{A}}}}={{\textsf{S}}_\mathsf {{B}}}\) for any eavesdropping attack. Thus, the \(\varepsilon _{cor}\)-correct protocol differs from a correct one according to the error probability, \(\varepsilon _{\text {cor}}\), where \({\text {Pr}}[{{\textsf{S}}_{{\textsf{A}}}}\ne {{\textsf{S}}_{{\textsf{B}}}}] \le \varepsilon _{\text {cor}}\). Therefore, the CQ state, \(\rho _{{{\textsf{S}}_{\textsf{A}}}E}\) is \(\Delta\)-secret when
where \(\rho _{{{\textsf{S}}_{{\textsf{A}}}}E}\) is the classical-quantum (CQ) state, which represents the correlation between Alice’s key bit string \(S_A\) and Eve’s quantum state \(\rho _E\), and \(\rho _U\) corresponds to the completely mixed state on the key space.
Since we consider signals generated using spontaneous parametric down-conversion (SPDC) sources that sometimes emit at least one photon pair, our protocol is susceptible to photon number splitting (PNS) attacks. Therefore, we apply the decoy states technique analysis. With the decoy-state approach, Alice prepares photons at random by using the three different intensities \((\mu , \nu , \omega )\) with \(\mu\) denoting the signal state intensity, \(\nu\) for decoy states, and \(\omega\) represents the vacuum states57. These intensities are generally chosen according to the following probabilities \(P_{\mu }>P_{\nu }>P_{\omega }\) whereby \(P_{\mu }, P_{\nu }\), and \(P_{\omega }\) represent signal, decoy and vacuum states. Accordingly, signal states attained with the intensity \(\mu\) are utilized to generate the final secure key. Finally, the decoy-states acquired based on intensity \(\nu\) are used to bound the knowledge of Eve about the key. Therefore, the key rate of the \(\varepsilon _{\text {sec}}+\varepsilon _{cor}\)-MDI protocol with biphotons is expressed as
with \(q=\frac{N_{\mu }p_{\kappa }^{2}}{N_{\text {total}}}\), \(N_{\mu }\) represents the amount of detected signals prepared according to the intensity \(\mu\). In contrast, \(p_{\kappa }\) denotes the probability of measuring in the key basis \({\mathscr {M}}_{1}\) and \(N_{\text {total}}\) is the total amount of exchanged signals. The term \(Q_{\mu _{a}\mu _{b},{\mathscr {M}}_{1}}^{1,1}\) represents the gain of biphotons prepared by Alice and Bob in the key basis \({\mathscr {M}}_{1}\) with intensities \(\mu _{a}\) and \(\mu _{b}\), respectively. Accordingly, the term \(e_{{\mathscr {M}}_{2}}^{1,1U}\) denotes the upper bound on the error rate emanating from single-photon components in the non-key basis \({\mathscr {M}}_{2}\) and \({\text {leak}}_{\textrm{EC}}\) represents the quantity of information leaked to Eve in the error correction step which equals to \(N_{\mu }f_{\textrm{EC}}h_{3}(E_{\mu _{a}\mu _{b}{\mathscr {M}}_{1}})\). Here f denotes the efficiency due to error correction and \(h_{3}(x)\) is the entropy corresponding to three-dimensional quantum states given by \(h_{3}(x)=-x{\text {log}}_{2}(\frac{x}{2})-(1-x){\text {log}}_{2}(1-x)\). Finally, the correction terms \(\log _{2}(1/\varepsilon _{\textrm{cor}})\) and \(2\log _{2}(4/\varepsilon _{\textrm{sec}})\) correspond to the bits of information lost through computation of universal hash function during error correction step and the privacy amplification. The applicable parameters in Eq. (22) are derived in Appendix A.
Simulation results
We present the analysis of the behavior of the secret key rate in Eq. (22). The simulation results correspond to a fibre-based QKD scheme where the expected key rate is maximized by using the following experimental values where fiber loss coefficient 0.2 dB/km, detector efficiency \(\eta =14.5\%\), single-photon detector dark count rate \(P_d=1.7\times 10^{-6}\), error correction efficiency \(f_{EC}=1.22\), signal states mean photon number \(\mu =0.6\) and optimal probability \(p_{z}\) for the key basis is 0.95 Ref.58.
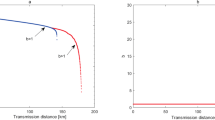
Figure 4 depicts the expected secret key rate corresponding to each pulse (i.e., \(\ell /N\)) in terms of the transmission distance between the participating parties, Alice and Bob, for various amounts of signals N. The simulation result demonstrates the feasibility of our proposed protocol in the finite-key regime. Notably, we obtain a fairly reasonable transmission distance of 90 km with realistic \(10^{16}\) photon signals. For comparison purposes, we provide the plot for key rate against transmission distance for our proposed biphoton MDI-QKD and the qubit-based MDI-QKD55 in Fig. 5. The results indicate that qubit-based MDI-QKD slightly outperforms our proposed biphoton QKD in terms of maximum transmission and achievable key rates. However, it is worth highlighting that the biphoton MDI-QKD provides a higher bit error rate tolerance compared to the qubit-based MDI-QKD. For example, it has previously been demonstrated in Ref.45,59 that biphoton-based QKD protocols can tolerate an error rate of about 17.7% to distill a secure key. In contrast, the best qubit-based one-way QKD can only tolerate up to 14.1% in the error rate45. Therefore, we highlight that owing to its ability to tolerate a higher quantum bit error rate, the biphoton MDI-QKD can still be considered a reliable candidate for key distribution purposes, particularly over short transmission distances with low losses in the channel. Notably, we remark that the means to create and detect biphoton optical fields have long been successfully investigated47,60,61,62. Furthermore, using comparable schemes the experimental results show that the biphoton states can be realized with high fidelity that ranged from 98.3 % to 99.8%, clearly demonstrating the feasibility of biphoton QKD. Most significantly, the advent of superconducting nanowire single-photon detectors has demonstrated detection efficiency of about 93%63. Thus, by harnessing these new technologies, the detection inefficiencies contributed by our detection system, which detectors in our scheme could contribute, can be drastically reduced, resulting in improved key rates. In Fig. 6, we present the performance expected secret key rate (per pulse) \(\ell /N\) given as a function of the number of signals N for various values of the intrinsic error rate: \(Q=(0.3\%,0.6\%, 1\%)\) owing to the misalignment and the optical system’s instability at a distance of 50 km. We show that a minimum data size of about \(10^{14}\) signals (attainable current hardware in practical QKD systems) is required to produce a provably secure secret key.
Illustration of the secret key rate (in logarithmic scale) in terms of the transmission distance (km) for our proposed biphoton MDI-QKD and the qubit-based MDI-QKD proposed in Ref.55 for a fixed amount of signals \(N=10^{16}\).
Conclusion
We presented a high-dimensional QKD protocol employing biphotons to encode information. The biphotons were exploited as qutrits to improve the secret key rate. This is because qutrits carry more bits of classical information and have improved robustness against eavesdropping compared to qubits. Moreover, the secret key rate for the MDI-QKD proposed protocol was simulated regarding the transmission distance for different fixed amounts of signals. These results prove that this protocol achieves a considerable secret key rate for a moderate transmission distance of 90 km by using \(10^{16}\) signals. Also, the expected secret key rate was simulated to examine our protocol’s performance at various intrinsic error rate values, \(Q=(0.3\%,0.6\%,1\%)\) caused by misalignment and instability due to the optical system. These results show that reasonable key rates are achieved with a minimum data size of about \(10^{14}\) signals which are realizable with the current technology. Therefore, the proposed protocol is crucial for realizing practical QKD implementations.
Data availability
The datasets generated during and/or analysed during the current study are available from the corresponding author on reasonable request.
References
Gisin, N., Ribordy, G., Tittel, W. & Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 74, 145 (2002).
Scarani, V. et al. The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301 (2009).
Mafu, M. & Senekane, M. Security of quantum key distribution protocols, in Advanced Technologies of Quantum Key Distribution (IntechOpen, 2018).
Pironio, S. et al. Device-independent quantum key distribution secure against collective attacks. New J. Phys. 11, 045021 (2009).
Pirandola, S. et al. Advances in quantum cryptography. Adv. Opt. Photonics 12, 1012–1236 (2020).
McKague, M. Device independent quantum key distribution secure against coherent attacks with memoryless measurement devices. New J. Phys. 11, 103037 (2009).
Hänggi, E. Device-independent quantum key distribution. arXiv preprint. arXiv:1012.3878 (2010).
Lo, H.-K., Curty, M. & Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108, 130503 (2012).
Wang, X.-B. Three-intensity decoy-state method for device-independent quantum key distribution with basis-dependent errors. Phys. Rev. A 87, 012320 (2013).
Liu, Y. et al. Experimental measurement-device-independent quantum key distribution. Phys. Rev. Lett. 111, 130502 (2013).
Rubenok, A., Slater, J. A., Chan, P., Lucio-Martinez, I. & Tittel, W. Real-world two-photon interference and proof-of-principle quantum key distribution immune to detector attacks. Phys. Rev. Lett. 111, 130501 (2013).
Sibson, P. et al. Chip-based quantum key distribution. Nat. Commun. 8, 1–6 (2017).
Wei, K. et al. High-speed measurement-device-independent quantum key distribution with integrated silicon photonics. Phys. Rev. X 10, 031030 (2020).
Semenenko, H. et al. Chip-based measurement-device-independent quantum key distribution. Optica 7, 238–242 (2020).
Zhao, P., Zhou, L., Zhong, W. & Sheng, Y.-B. Faithful entanglement distribution using quantum multiplexing in noisy channel. EPL (Europhys. Lett.) 135, 40001 (2021).
Cao, L. et al. Chip-based measurement-device-independent quantum key distribution using integrated silicon photonic systems. Phys. Rev. Appl. 14, 011001 (2020).
Kwek, L.-C. et al. Chip-based quantum key distribution. AAPPS Bull. 31, 1–8 (2021).
Liu, Q. et al. Advances in chip-based quantum key distribution. Entropy 24, 1334 (2022).
Orieux, A. & Diamanti, E. Recent advances on integrated quantum communications. J. Opt. 18, 083002 (2016).
Sekga, C. & Mafu, M. Tripartite quantum key distribution implemented with imperfect sources. Optics 3, 191–208 (2022).
Molina-Terriza, G., Torres, J. P. & Torner, L. Management of the angular momentum of light: preparation of photons in multidimensional vector states of angular momentum. Phys. Rev. Lett. 88, 013601 (2001).
He, C., Shen, Y. & Forbes, A. Towards higher-dimensional structured light. Light Sci. Appl. 11, 1–17 (2022).
Mafu, M. et al. Higher-dimensional orbital-angular-momentum-based quantum key distribution with mutually unbiased bases. Phys. Rev. A 88, 032305 (2013).
Bechmann-Pasquinucci, H. & Peres, A. Quantum cryptography with 3-state systems. Phys. Rev. Lett. 85, 3313 (2000).
Cerf, N. J., Bourennane, M., Karlsson, A. & Gisin, N. Security of quantum key distribution using d-level systems. Phys. Rev. Lett. 88, 127902 (2002).
Reimer, C. et al. High-dimensional one-way quantum processing implemented on d-level cluster states. Nat. Phys. 15, 148–153 (2019).
Nikolopoulos, G. M. & Alber, G. Security bound of two-basis quantum-key-distribution protocols using qudits. Phys. Rev. A 72, 032320 (2005).
Navez, P. & Cerf, N. J. Cloning a real d-dimensional quantum state on the edge of the no-signaling condition. Phys. Rev. A 68, 032313 (2003).
Howell, J. C., Bennink, R. S., Bentley, S. J. & Boyd, R. W. Realization of the Einstein–Podolsky–Rosen paradox using momentum-and position-entangled photons from spontaneous parametric down conversion. Phys. Rev. Lett. 92, 210403 (2004).
Sit, A. et al. High-dimensional intracity quantum cryptography with structured photons. Optica 4, 1006–1010 (2017).
Mirhosseini, M. et al. High-dimensional quantum cryptography with twisted light. New J. Phys. 17, 033033 (2015).
Wang, F. et al. Towards practical high-speed high dimensional quantum key distribution using partial mutual unbiased basis of photon’s orbital angular momentum. arXiv preprint. arXiv:1801.06582 (2018).
Bouchard, F. et al. Experimental investigation of high-dimensional quantum key distribution protocols with twisted photons. Quantum 2, 111 (2018).
Tittel, W., Brendel, J., Zbinden, H. & Gisin, N. Quantum cryptography using entangled photons in energy-time bell states. Phys. Rev. Lett. 84, 4737 (2000).
Thew, R. T., Acin, A., Zbinden, H. & Gisin, N. Bell-type test of energy-time entangled qutrits. Phys. Rev. Lett. 93, 010503 (2004).
Qi, B., Fung, C.-H. F., Lo, H.-K. & Ma, X. Time-shift attack in practical quantum cryptosystems. arXiv preprint. arXiv:0512080 (2005).
Ali-Khan, I., Broadbent, C. J. & Howell, J. C. Large-alphabet quantum key distribution using energy-time entangled bipartite states. Phys. Rev. Lett. 98, 060503 (2007).
Mower, J. et al. High-dimensional quantum key distribution using dispersive optics. Phys. Rev. A 87, 062322 (2013).
Nunn, J. et al. Large-alphabet time-frequency entangled quantum key distribution by means of time-to-frequency conversion. Opt. Express 21, 15959–15973 (2013).
Bunandar, D., Zhang, Z., Shapiro, J. H. & Englund, D. R. Practical high-dimensional quantum key distribution with decoy states. Phys. Rev. A 91, 022336 (2015).
Niu, M. Y., Xu, F., Shapiro, J. H. & Furrer, F. Finite-key analysis for time-energy high-dimensional quantum key distribution. Phys. Rev. A 94, 052323 (2016).
Jo, Y. & Son, W. Key-rate enhancement using qutrit states for quantum key distribution with askew aligned sources. Phys. Rev. A 94, 052316 (2016).
Hwang, W.-Y., Su, H.-Y. & Bae, J. N-dimensional measurement-device-independent quantum key distribution with n+ 1 un-characterized sources: zero quantum-bit-error-rate case. Sci. Rep. 6, 1–3 (2016).
Dellantonio, L., Sørensen, A. S. & Bacco, D. High-dimensional measurement-device-independent quantum key distribution on two-dimensional subspaces. Phys. Rev. A 98, 062301 (2018).
Bregman, I., Aharonov, D., Ben-Or, M. & Eisenberg, H. Simple and secure quantum key distribution with biphotons. Phys. Rev. A 77, 050301 (2008).
Chekhova, M. Polarization and spectral properties of biphotons, in Progress in Optics, vol. 56, 187–226 (Elsevier, 2011).
Bogdanov, Y. I. et al. Qutrit state engineering with biphotons. Phys. Rev. Lett. 93, 230503 (2004).
Burlakov, A. V. & Chekhova, M. V. Polarization optics of biphotons. J. Exp. Theor. Phys. Lett. 75, 432–438 (2002).
Maslennikov, G., Zhukov, A., Chekhova, M. & Kulik, S. Practical realization of the quantum cryptography protocol exploiting polarization encoding in the qutrits. arXiv preprint. arXiv:0305115 (2003).
Chernoff, H. A measure of asymptotic efficiency for tests of a hypothesis based on the sum of observations. Ann. Math. Stat. 23, 493–507 (1952).
Jo, Y., Bae, K. & Son, W. Enhanced bell state measurement for efficient measurement-device-independent quantum key distribution using 3-dimensional quantum states. Sci. Rep. 9, 1–11 (2019).
Yin, H.-L. & Chen, Z.-B. Finite-key analysis for twin-field quantum key distribution with composable security. Sci. Rep. 9, 1–9 (2019).
Mafu, M., Garapo, K. & Petruccione, F. Finite-size key in the Bennett 1992 quantum-key-distribution protocol for Rényi entropies. Phys. Rev. A 88, 062306 (2013).
Tomamichel, M., Lim, C. C. W., Gisin, N. & Renner, R. Tight finite-key analysis for quantum cryptography. Nat. Commun. 3, 1–6 (2012).
Curty, M. et al. Finite-key analysis for measurement-device-independent quantum key distribution. Nat. Commun. 5, 1–7 (2014).
Mafu, M., Garapo, K. & Petruccione, F. Finite-key-size security of the Phoenix-Barnett-Chefles 2000 quantum-key-distribution protocol. Phys. Rev. A 90, 032308 (2014).
Ma, X., Qi, B., Zhao, Y. & Lo, H.-K. Practical decoy state for quantum key distribution. Phys. Rev. A 72, 012326 (2005).
Wei, Z. et al. Decoy-state quantum key distribution with biased basis choice. Sci. Rep. 3, 1–4 (2013).
Sheridan, L. & Scarani, V. Security proof for quantum key distribution using qudit systems. Phys. Rev. A 82, 030301 (2010).
Moreva, E., Maslennikov, G., Straupe, S. & Kulik, S. Realization of four-level qudits using biphotons. Phys. Rev. Lett. 97, 023602 (2006).
Goldberg, A. Z. Quantum polarimetry. Prog. Opt. 67, 185–274 (2022).
Ma, P.-C., Chen, G.-B., Li, X.-W. & Zhan, Y.-B. Cyclic controlled remote state preparation in the three-dimensional system. Laser Phys. Lett. 19, 115204 (2022).
Marsili, F. et al. Detecting single infrared photons with 93% system efficiency. Nat. Photonics 7, 210–214 (2013).
Author information
Authors and Affiliations
Contributions
Conceptualization, C.S. and M.M.; methodology, C.S.; software, C.S.; validation, C.S. and M.M.; formal analysis, C.S., M.M. and M.S; writing—original draft preparation, C.S.; writing—review and editing, M.M.; supervision, M.M.; project administration, M.M.; funding acquisition, M.S. All authors have read and agreed to the published version of the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix
A: Estimation of key rate parameters
We evaluate gains and quantum bit error rates by considering the conditional probabilities for the coincidence detection of n-photon pairs in the Brown Twiss scheme. In terms of the basis state \(|\alpha \rangle\), the yield is given by
where \(Y_{0}\) is the background count rate, \(D_{H1A}\), \(D_{H1B}\), \(D_{H2A}\) and \(D_{H2B}\) correspond to detectors for measuring horizontally polarized states in the Brown Twiss scheme. The terms t and \(\eta\) represent channel transmittance and detection efficiencies. The yield for photon pairs that correspond to state \(|\beta \rangle\) is given by
where \(D_{H3A}\), \(D_{H3B}\), \(D_{V4A}\), and \(D_{V4B}\) correspond to detectors for measuring horizontal and vertical polarized states, respectively, in the Brown Twiss scheme. Similarly, the detection probability for the n-photon pair corresponding to \(|\gamma \rangle\) is
\(D_{V5A}\), \(D_{V5B}\), \(D_{V6A}\), and \(D_{V6B}\) correspond to detectors for measuring vertically polarized states in the Brown Twiss scheme. Therefore, the overall yield is given by
From these results, the gain for states prepared from key basis comprising of n-photon pairs is given by
where \(P(n_{a})\) and \(P(n_{b})\) denotes the probabilities for Alice and Bob’s SPDC sources to emit \(n_{a}\)-photon and \(n_{b}\)-photon pairs. This probability is expressed as
The gain corresponding to single-photon contributions is then given by
In addition, we have the overall gain expressed as
and the QBER, \(E_{\mu _{a}\mu _{b},{\mathscr {M}}_{1}}\) is expressed as
where the error rate of the n-photon pairs from Alice and Bob, \(e_{n,n}\) is expressed as
The error rate for the n-photon pair corresponding to the state \(|\alpha \rangle\) given by
The error rates \(e_{n}^{\beta }\) and \(e_{n}^{\gamma }\) associated with the detection of states \(|\beta \rangle\) and \(|\gamma \rangle\), respectively are analogously obtained as
Finally, the upper bound on the error rate measured in the complimentary basis used to approximate the phase error rate on the key basis is given by
where
In above equation \(P(\lambda |n)=\frac{(n+1)(\frac{\lambda }{2})^{n}}{(1+\frac{\lambda }{2})^{n+2}}\) with \(\lambda \in \{\mu , \nu \}\) and n denotes number of photons.
B: Secrecy
Let the system \(\tilde{{\textsf{E}}}\) represent information collected by Eve on Alice and Bob’s bit strings \({\textsf{K}}_{A}\) and \({\textsf{K}}_{B}\), respectively, up to the error correction step. By applying the privacy amplification based on the universal class-two hash function, we generate a \(\Delta\)-secret key of length \(\ell\), and
where \({\text {H}}_{\text {min}}^{\varepsilon }({\textsf{K}}_{A}|\tilde{{\textsf{E}}})\) represents the smooth min-entropy, which corresponds to the average probability which an adversary guesses \({\textsf{K}}_{A}\) correctly using an optimal strategy through having an access to \(\tilde{{\textsf{E}}}\). Let \(v=\frac{1}{2}\sqrt{2^{\ell -{\text {H}}_{\text {min}}^{\varepsilon }({\textsf{K}}_{A}|\tilde{{\textsf{E}}})}}\), then the secret key length, \(\ell\) is given by
During error correction, Alice and Bob reveal bits of information equals to \({\text {leak}}_{EC}+\log _{2}\Big (\frac{2}{\varepsilon _{\text {cor}}}\Big )\) to an eavesdropper. Therefore, we have that
where \({\textsf{E}}\) is Eve’s information prior to error correction step. Since our analysis is based on decoy states, \({\textsf{K}}_{A}\) can be written in terms of \({\textsf{K}}_{A}^{1}{\textsf{K}}_{A}^{m}\) and this represents the bit strings owing to single photons and multi-photons events. Through using the generalized chain rule for smooth entropies, we have that
and here the second inequality is based on the fact that \({\text {H}}_{\text {min}}^{\delta _{3}}({\textsf{K}}_{A}^{m}|{\textsf{E}}) \ge 0\). Next, we provide bound for \({\text {H}}_{\text {Twissmin}}^{\delta _{1}}({\textsf{K}}_{A}^{1}|{\textsf{K}}_{A}^{m}{\textsf{E}})\) by using the uncertainty relations for the smooth entropies. To achieve this, we use a gendankenexperiment where Alice and Bob prepare all their states in the basis \({\mathscr {M}}_{2}\) even when they choose the \({\mathscr {M}}_{1}\) basis. In this hypothetical protocol, the bit strings obtained from measurements in the complementary basis, \({\textsf{C}}_{A}\) and \({\textsf{C}}_{B}\) of length \(\ell\) replace the keys \({\textsf{K}}_{A}\) and \({\textsf{K}}_{B}\). The smooth min-entropy is expressed as
where \(n_{1,1\mu }=N_{\mu }p_{\kappa }^{2}Q_{\mu _{a}\mu _{b}{\mathscr {M}}_{1}}^{1,1}\) denotes the sifted raw key size obtained from the single photon occurances.
Finally, we combine all the terms which represent errors for min-entropies and error probabilities due to parameter estimation discussed in previous section. Thus, the secrecy is given by
Here, \(\varepsilon _{1}\) and \(\varepsilon _{2}\) represent error probabilities for estimating the single photon events as well as the phase error rate. The error term is set to a common value \(\varepsilon\) and \(\varepsilon _{\text {sec}}=8\varepsilon\). The final key length \(\ell\) is obtained using the results from Eqs. (40) to (42) and invoking the secrecy requirement from Eqs. (43) in (39). Then, the final derived formula is written as
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Sekga, C., Mafu, M. & Senekane, M. High-dimensional quantum key distribution implemented with biphotons. Sci Rep 13, 1229 (2023). https://doi.org/10.1038/s41598-023-28382-w
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-023-28382-w
This article is cited by
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.