Abstract
Although quantum communication systems are being deployed on a global scale, their realistic security certification is not yet available. Here we present a security evaluation and improvement protocol for complete quantum communication systems. The protocol subdivides a system by defining seven system implementation sub-layers based on a hierarchical order of information flow; then it categorises the known system implementation imperfections by hardness of protection and practical risk. Next, an initial analysis report lists all potential loopholes in its quantum-optical part. It is followed by interactions with the system manufacturer, testing and patching most loopholes, and re-assessing their status. Our protocol has been applied on multiple commercial quantum key distribution systems to improve their security. A detailed description of our methodology is presented with the example of a subcarrier-wave system. Our protocol is a step towards future security evaluation and security certification standards.
Similar content being viewed by others
Introduction
Instead of relying on assumptions of computational hardness like most other classical cryptography protocols, quantum cryptography relies on the laws of physics for providing information-theoretic security. From the first theoretical proposal in 19831 to the recent key exchange via satellite over \(1200\,\mathrm{km}\)2, quantum key distribution (QKD) has come forward a long way. Over the course of time, the journey has been (and is still being) impeded by a number of attacks that exploit the deviations between theory and practice3,4,5,6,7,8,9,10,11,12. Ironically, as a consequence of the attacks, QKD has been equipped with improved protocols and tools like decoy states13,14, measurement device independence15, device-independence16, twin-field QKD17 and so on. As a result, QKD today is much more secure and efficient in practice than it was 20 years ago.
It is now time for QKD to be expanded and deployed on a larger scale. As the push from the lab to practical deployment is initiated in various parts of the globe, a number of security, compatibility and connectivity issues are needed to be solved. These demand developing universally accepted standards and certification methodologies, and also the formation of a common platform for collaboration and addressing these issues. To fulfil this need, ETSI has had an industry specification group for QKD (ISG-QKD) since 2008 that provides a platform for the creation of universally accepted standards and promotes coordination, cooperation and standardization of research for QKD18,19,20. Development of security certification standards is at present being discussed in this group and in other standards organisations such as International Organisation for Standardisation (ISO)21 and International Telecommunication Union (ITU)22,23. At the same time, several recent studies attempt to introduce certification of countermeasures against specific vulnerabilities in a quantum-optical part. For example, Ref.24 studies the security of a photon source in a fiber-based QKD system against a general Trojan-horse attack (THA)25,26. By treating the attack as an information leakage problem, the secure key rate becomes a function of the specifications of the installed optical components. The latter can be characterised when necessary. A similar approach has been suggested for other individual imperfections12,27,28,29,30. A methodology to characterise and secure the source against several imperfections is under development31. Attention to several imperfections and attacks is being paid when designing QKD equipment32.
Although these studies have addressed several individual vulnerabilities, no complete system analysis has yet been reported. This is what we do in this work. We lay out a methodology for security evaluation and certification of a complete quantum communication system against all known implementation imperfections in its quantum optical part. To exemplify how our security evaluation methodology works, we present the results of our initial security evaluation performed at ITMO University and Quantum Communication Ltd. (St. Petersburg, Russia) in 2017. They are therefore the first commercial QKD manufacturer to openly publish the security assessment of their system. We also present the results of follow-up (performed by the manufacturer) to exemplify the follow-up step of our methodology. It consists of theoretical and experimental studies that have allowed the manufacturer to quickly improve implementation security of their product by patching its most prominent loopholes. We hope that our methodology will pave the way for developing security evaluation and certification standards for complete quantum communication systems.
The security evaluation team has performed a very similar initial security evaluation in 2016 on the QKD system Clavis3 from ID Quantique (Switzerland) and on \(40\,\mathrm{MHz}\) QKD system from QuantumCTek (China). The follow-up step with the latter is currently in progress. We stress that these two industry projects are highly similar in their methodology, character of results and outcomes to the one reported in this Article. I.e., the methodology we report here is applicable to different commercial systems. However details of vulnerabilities found in the two above-mentioned systems remain confidential at the request of the manufacturers. At the same time, in the case of ITMO’s system, the complete security analysis results along with all the vulnerabilities and follow-up tasks have been presented here and no information has been kept hidden.
The Article is organised as follows. Our proposed layered architecture of the complete quantum communication system is presented in “System implementation layers” and our severity rating scheme for the implementation imperfections in “Quantifying hardness against implementation imperfections”. We describe the system under test in “Security evaluation of ITMO’s subcarrier-wave quantum key distribution system”. Our initial security evaluation results are presented in “Potential vulnerabilities” and the follow-up from the manufacturer is presented in “Follow-up stage”. We conclude in “Conclusion”.
Security evaluation and certification methodology
Our methodology requires an iterative interaction between the manufacturer and the certifiers. The certifying agency needs to have an in-depth knowledge of and physical access to the system in order to perform its security evaluation and certification. Thus, the issue of trust has to be implicit in all the security certification tasks. The first stage in our methodology is the security evaluation stage by the testing team; then the follow-up stage by the manufacturer; then again the security evaluation stage, and so on. Through this iterative process, the system security is gradually expected to reach a level that can be trusted and widely accepted.
The security evaluation stage consists of: (a) subdivision of the complete system into seven layers based on the definitions provided in Table 1; (b) scrutinising the system for implementation vulnerabilities that may make it vulnerable against known attacks, as well as trying to find any new unknown attacks that may apply; and (c) categorising each discovered vulnerability according to the hardness level defined in Table 2. When the evaluation stage ends, the follow-up stage starts. In this stage, the security evaluation results are provided to the manufacturer and the patching commences. We have used this same methodology to evaluate the ITMO’s system and the two other systems mentioned above.
System implementation layers
Security analysis of a complete quantum communication system is a complex procedure that requires different areas of expertise. To simplify the job and ensure that people with specific expertise can tackle the right problems, it is necessary to subdivide the implementation complexity into layers. As a first step of our security evaluation methodology, we have subdivided the system implementation into seven layers based on a hierarchical order of information flow and control as presented in Table 1. Our layer structure is conceptually similar to the open systems interconnection (OSI) model for telecommunication systems33. Just like OSI layers, a layer in our system serves the layer above it and is served by the layer below; however, unlike OSI, all our layers are inside one system, and most of them are not abstraction layers. When a generic system is installed, it starts with the top layer: Q7 installation and maintenance; then operation and processing is subsequently initiated in each underlying layer until it gets down to handling quantum states in Q1 optics layer. Once the optics layer generates photon detections, they are again processed in each layer above in sequence until the top layers: either Q6 interfacing the output of the quantum protocol with the application that has requested it, or all the way up to Q7. Below we explain the functioning of each layer with examples.
The lowest layer Q1 handles the photonic signals that carry the quantum states and service functions. The next layer Q2 interfaces the optical components with digital processing and possibly performs some analog signal processing. It contains analog electronics and digital-analog converters. Q3 comprises digital and software algorithms that immediately control the electronics and optics, including its calibration aspects. It might contain, for example, a set of algorithms to maintain avalanche photodiode (APD) temperature, bias voltage, and gating. The next layer Q4 is software that decides which Q3 layer subroutine to run. For example, it decides when APDs need to be cooled, or when gating control should be initiated. The next layer Q5 processes the raw data generated by the hardware to distill the final data in the protocol, for example generate secret keys in QKD. The layer above Q6 handles the communication between the quantum protocol and the classical application that asks for the service of the protocol. Finally, the topmost layer Q7 handles issues in any underlying layer that require human intervention, even if the human follows a checklist. We have found that the system evaluated in this Article, as well as several other QKD systems, allow a clear division into this layer structure. An example is given in “Methods”.
We admit that the definition of the layers may not be complete and there could be cases when the functionality of a particular hardware component may span across several layers. In that case, the component accommodates more than one layer. For example, signal processing and algorithms belonging to the layers Q2 through Q5 can be implemented in a single physical field-programmable gate array (FPGA) chip. Also, the ordering of the layers may not be absolute. For example, in some systems, the layer Q5 post-processing may run in parallel with the layers below it while in other systems it may start after the end of Q4 operation cycle. In any case, improvisations have to be made when cutting each system into the layers.
If the system contains a separate physical random number generator (RNG), it is considered to be a separate quantum device and therefore not included into our layer classification. Its output would of course interface somewhere with the system, e.g., at layer Q5. Being a separate device it may have an implementation structure of its own, which we do not consider here.
We remark that an initial theoretical proposal of a quantum communication protocol (such as Refs.1,37) covers a part of the single layer Q5, while being mostly ignorant of the other layers except their few selected aspects. However practical security loopholes can be present anywhere in the complete implementation and be in any of its layers. The implementation of each layer has high technical complexity and contain tens of optical components, operator’s checklists, thousands of electronic components and lines of software code. The task of security analysis is to find all the loopholes.
Quantifying hardness against implementation imperfections
When an implementation imperfection is suspected to be security-critical, it is necessary to evaluate the security risks. The first step is testing. If it is found to be compromising the security then the next step is to design a countermeasure solution, and the last step is checking the robustness of that solution. This procedure is often a loop, because most countermeasures in turn need to be tested. In order to quantify implementation imperfections—existing inside the system—in terms of solutions implemented, we have categorised them as shown in Table 2. The lowest state CX indicates that the imperfection is suspected to be a potential security issue, and needs to be further analysed or tested before a conclusion can be made. After an imperfection is found to be security-critical, its state becomes C0, i.e., insecure. Next, a solution needs to be developed that provides security against the original attack model. At this state the solution is expected to be robust and the imperfection is considered to be state C2. After it has been integrated into a security proof, the state can be shifted to C3: solution secure. However, often it may be the case that newer attack models are found that bypass the countermeasure; then the state moves to C1, which means the solution is robust only against a specific attack model but not against others or a combination of the original and some other attacks.
For example, in ID Quantique Clavis2 QKD system, the imperfection that the detectors were vulnerable to bright-light detector control attack became C0 upon its discovery in 20093, was reclassified C2 after being patched in 2015, then downgraded to C1 next year after the patch was demonstrated to be inadequate against a modified attack10. A similar development can be traced for another imperfection: variation of detector efficiency with angle of the incoming light7. It was suspected to be a security vulnerability (CX) up to 2015, then proven to be so (C0) in 20157,38, then moved to C2 by the use of a pinhole and later brought down to C1 after the results presented in Refs.9,39.
We emphasize that the categorisation of a specific vulnerability reflects only the existing knowledge about them which can change with time as seen from the above discussion. Also the categorisation of each existing imperfection depends on the specific system and the specific solution implemented. For example, an imperfection in the single-photon detectors may be classified as insecure (C0) but the same imperfection might be irrelevant (C3) for a system running a measurement-device-independent (MDI) QKD protocol.
Eventually, the objective of the security evaluation process should be to upgrade the system such that all imperfections are on the level C3. Level C3 should be considered good for a commercial product, while levels C1, C0 and CX should be deemed inadequate and need to be remedied by a security update or new product development. Level C2 lies in the gray zone and while it may be considered secure for practical purposes, i.e., adequate for a commercial product, one should remember that it has no theoretical security proof based on quantum mechanics. However, the development of security proofs taking into account imperfections can—in some cases—be a slow process, and we expect many of them to attain C2 earlier than C3.
Security evaluation of ITMO’s subcarrier-wave quantum key distribution system
In the rest of this Article we demonstrate how our proposed security evaluation and certification methodology can be applied to a specific system. As an example, we select the subcarrier-wave quantum key distribution (SCW QKD) system manufactured by ITMO University and its spin-off company Quantum Communications Ltd. During the initial security evaluation, the manufacturer has provided us with an overall design specification of the system along with further oral information and written notes on various aspects of design and manufacturing process. We had physical access to the hardware but did not perform any experiments on the setup during that stage. Following the methodology from “System implementation layers” and Table 1, we have performed a complete security analysis of the bottom four layers (Q1–Q4) that correspond to optics, analog electronics, driver and calibration algorithms, and operation cycle of the system. For these layers, we have examined all suspected implementation security issues according to the current knowledge. For higher layers Q5 and up (from QKD protocol post-processing and up), we cannot perform a complete security evaluation as they lay outside our expertise area; they should be analysed by a team with expertise in classical information technology security. Nevertheless, we have pointed out a few issues in the layer Q5.
The results of this initial security evaluation have initially been delivered to ITMO in a confidential report in February 2018 (prepared by those authors not affiliated with ITMO). A summary of that report is presented in “Potential vulnerabilities”, after we briefly introduce the system to the reader.
The subcarrier-wave QKD principle was proposed in 199940 and experimentally demonstrated later the same year41. It was initially conceived as a practical fiber-optic system offering an alternative to then-dominant polarization and time-bin encoding schemes that would require a precise alignment during operation40, as well as to “plug-and-play” systems developed a year earlier42 that limited QKD source repetition rate due to an intrinsic two-pass architecture. More recently, SCW QKD has been demonstrated as being robust against external conditions affecting the telecom fiber43, allowing increased spectral density44,45, and being invariant to telescope rotation in open-air links46. Its viability has been experimentally demonstrated for metropolitan area telecommunication lines47, multi-user48,49 and software-defined50 networks.
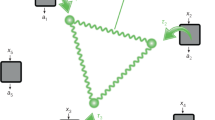
A basic design of the SCW QKD system is shown in Fig. 1. In Alice module, a continuous narrow linewidth laser acts as a light source. This radiation with frequency \(\omega \) is usually referred as carrier wave, or simply a carrier. It passes through an electro-optical phase modulator, to which an electrical driving signal with frequency \(\Omega \) is applied. As a result, two subcarriers (or sidebands) with frequencies \(\omega -\Omega \) and \(\omega +\Omega \) appear in the optical frequency spectrum, as shown on the plot in Fig. 1. Quantum information is encoded in the phase shift \(\varphi _A\) between the carrier and the subcarriers, which is induced by phase modulation of the electrical driving signal43. Four phase states (0, \(\pi /2\), \(\pi \), \(3\pi /2\)) are used in both Alice and Bob modules. After modulation the signal passes to the quantum channel through an attenuator. Carrier power, modulation index and attenuation value are chosen so that the mean photon number \(\mu _{\mathrm{sb}}\) (on two sidebands combined) meets the protocol requirements. On Bob side a similar modulator introduces phase shift \(\varphi _B\) resulting in single-photon interference on the sidebands. An optical filter separates the carrier from the sidebands, and the latter are detected on a single-photon detector. The registered optical power depends on the difference \(|{\varphi _A-\varphi _B}|\). If Alice and Bob introduce equal phase shifts, constructive interference is observed, and the optical signal power at the sidebands differs from zero. In the opposite case, when the difference equals \(\pi \), destructive interference occurs and the registered counts correspond to dark noise of the detector. Instances when the difference is \(\pi /2\) are discarded during sifting. Key bits are obtained from the registered counts using algorithms similar to a phase-encoded BB84 protocol43,51. A full quantum description of the system and the implemented protocols can be found in Refs.51,52.
Potential vulnerabilities
Based on the received information about the system, we have identified a number of potential security issues that might be exploitable by an adversary Eve. A summary of these results is given in Table 3. For each imperfection, we specify the corresponding Q-layers (see “System implementation layers”), hardness level \(C_{\mathrm{init}}\) (see “Quantifying hardness against implementation imperfections”) and an estimate of the risk. Almost all the identified issues require further detailed analysis, and in many cases, in-depth experimental testing in a laboratory. For many issues, the hardness level is CX, meaning the issue’s applicability to the system implementation needs to be studied and tested. We specify in which system implementation Q-layers each issue is located, according to the classification introduced in “System implementation layers”.
The risk evaluation listed in Table 3 is based on a guessed likelihood of the vulnerability, expected fraction of the secret key leakage, and estimated feasibility of exploit technology. It is essential for manufacturers with limited resources to prioritize the problems. Vulnerabilities that can be exploited using today’s technology and compromise full secret key are a more immediate threat. They should be addressed before those that require future technology or provide only partial key information (thus requiring of Eve an additional classical cryptanalytic task). We have followed this strategy and tested the two highest risk issues during the follow-up stage (see “Follow-up stage”). The security proof and implementation of post-processing have also been completed after the report.
We remark that more security issues may be discovered in the future once the system design and operation are examined in greater detail. We now explain the identified issues.
Controllable detectors
Two types of detectors are used in the present implementation: ID Quantique (IDQ) ID210 gated APD and Scontel TCORPS-CCR-001 superconducting nanowire single-photon detector (SNSPD). Among them, Scontel SNSPD is at least partially controllable by bright light57,58,59. Whether the same was true for ID210, required experimental testing. From our previous measurements on ID Quantique Clavis2 QKD system, we know that it is possible to blind its detectors by sending a continuous-wave (c.w.) light of power \(P_{\mathrm{blind}} = 0.3\,\mathrm{mW}\)10. Then by choosing a trigger pulse power \(P_{\mathrm{tr}}\) greater than the threshold power \(P_{\mathrm{th}} = 0.15\,\mathrm{mW}\), it is possible to force a click when Bob-Eve phases match. If we assume ID210 behaves similarly to the detectors in Clavis2 system, then Eve could send c.w. power to blind it and perform the faked-state attack3 detailed in “Methods”.
However, sending a trigger power \(P_{\mathrm{tr}}\) at the subcarrier frequency will not work as the photons will be shifted to another frequency due to Bob’s modulation. Instead, Eve needs to inject extra photons in the reference signal frequency so that they are shifted to the subcarrier after the modulation and trigger a click in the blinded detector. Due to the small m in the present system, the reference power required by Eve is \(P_{\mathrm{ref}} \approx P_{\mathrm{tr}} / m\). For example, for \(m = 0.05\), a \(1\,\mathrm{ns}\) trigger pulse at the subcarriers with peak power \(P_{\mathrm{tr}} >0.15\,\mathrm{mW}\)10 just before the detectors would require a \(1\,\mathrm{ns}\) wide reference pulse with peak power of \(P_{\mathrm{ref}} > 3\,\mathrm{mW}\) at Bob’s input. This is an easily generated and transmitted optical power.
Laser damage
Whether the current system is vulnerable to laser damage attack (LDA)9,60, can be ascertained only after experimental testing. Since one of attenuating components, a variable optical attenuator (VOA; FOD 5418) in Alice is the closest to the channel (see Fig. 2), it will be the first target for Eve’s LDA. Eve can send high power laser to damage the optical attenuator to reduce its attenuation. If successful, lights coming out of Alice will have higher mean photon numbers than permitted by the security proofs, thus compromising the security.
It will also be interesting to experimentally check the effect of laser damage on the optical PSMs to see whether LDA can affect m. If it can, then further studies need to be conducted to check whether it leads to a denial of service or a security compromise. Finally, if LDA can reduce the insertion loss of either the PSM1, linear polarizer (LP) or fixed optical attenuator (FOA) in Alice, it may facilitate other attacks, e.g., Trojan-horse attack. Hence, these components must be characterized meticulously against LDA.
Trojan-horse attack
In SCW QKD protocol, after sifting, Alice and Bob keep only the outcomes for which they both used the same phase, i.e., \(\varphi _A =\varphi _B\). Thus if Eve can extract information on either \(\varphi _A\) or \(\varphi _B\) by performing a Trojan-horse attack (THA)25,26,61, the security will be compromised. With current technology, Eve needs a mean photon number \(\mu _{B\rightarrow E} \sim 4\) to perform homodyne detection61.
The secure key rate in the presence of THA—under reasonable assumptions—is available for both single-photon and decoy-state Bennett-Brassard 1984 (BB84) protocol24. It is based on Alice’s ability to upper-bound the outgoing mean photon number \(\mu _{\mathrm{out}}\). A similar theoretical analysis under assumptions appropriate for the present scheme is not available, and needs to be performed. Moreover, wavelength can also be an attack variable11,62. It is thus important to measure experimentally the actual values of the insertion loss and reflection coefficients of several components such as LP, FOA, OI, connectors, etc. in a large range of wavelengths that can propagate through the optical fiber (from \(< 400\) to \(> 2500\,\mathrm{nm}\)). Since a laboratory with wideband characterisation equipment is not readily available to us, we have limited our analysis to Eve using a single \(1550\,\mathrm{nm}\) wavelength. With these two shortcomings, our security evaluation of the system against the THA is detailed below.
Alice: In the present scheme (Fig. 2), possible sources of reflection are the LP (Thorlabs ILP1550PM-APC), FOA (Fibertool FC-FC 15 dB), optical isolator (OI; AC Photonics PMIU15P22B11), all the standard optical connectors placed after PSM1 (i.e., at its side facing away from the quantum channel), and that facet of PSM1. We identify that one of the strongest sources of reflection is the LP with \(45\,\mathrm{dB}\) return loss (according to its data sheet). Assuming the VOA is set to \(70\,\mathrm{dB}\) (which is a typical attenuation value required by the SCW QKD protocol), the insertion loss of the PSM1 is \(3\,\mathrm{dB}\) and that of each connector is \(0.3\,\mathrm{dB}\), the total round-trip attenuation experienced by a Trojan photon is \(193.4\,\mathrm{dB}\). For the other protocols, an appreciable decline of performance begins at \(\mu _{\mathrm{out}} \sim 10^{-6}\)24. For that, an eavesdropper would need to send \(2.2 \times 10^{13}\) photons per pulse into the system, which—considering a phase change frequency of \(f = 100\,\mathrm{MHz}\)—corresponds to injecting c.w. power of \(280\,\mathrm{W}\). This is somewhat above present-day technology capability, may be around the physical limit of how much power the standard fibers can carry, and will certainly trigger laser damage of Alice’s components. Most fiber-optic components get damaged at less than \(10\,\mathrm{W}\)9,34,63,64. While this suggests the risk of THA at Alice’s side is relatively low, it is important to check the reflection from the OI and FOA, which requires experimental testing. Finally, this analysis should be repeated for lower attenuation settings of the VOA that may be used by the system and the risk should be evaluated accordingly.
Bob: The risk of THA on Bob seems to be comparatively higher than that at Alice since there is no attenuator or isolator in Bob’s module (Fig. 3). The reflection coefficient of the polarization beam combiner (PBC; AC Photonics PBS15P12S11-2m) just after PSM2 is \(50\,\mathrm{dB}\) (according to its data sheet) while the insertion loss of the polarization beam splitter (PBS; same as PBC), PSM2, and each of the four connectors is 0.48, 1.7, and \(0.3\,\mathrm{dB}\), respectively. Assuming the point of reflection is the PBC just after the phase modulator, the total loss experienced by a Trojan photon will be \(l=56.8\,\mathrm{dB}\). This means that in order to get a single photon out, Eve needs to inject a c.w. power of only \(6\,\upmu \mathrm{W}\), which is easy.
Bob’s optical scheme in detail. Bob’s phase shift modulator PSM2 is polarization-insensitive and is implemented as two identical modulators acting on orthogonal components of input polarization. PBS fiber-optic polarization beam splitter, PBC fiber-optic polarization beam combiner, C circulator, FBG fiber Bragg grating.
Note that ID210 runs in gated mode with afterpulsing. So, Eve can send the Trojan photons just after the gate but still inside the phase modulation window. However, this may cause a high level of afterpulsing in Bob’s single-photon detectors61. Scontel TCORPS-CCR-001 has no afterpulsing but it runs in continuous mode, thus making it difficult for Eve to send Trojan photons. Eve can resort to a longer wavelength (such as \(1924\,\mathrm{nm}\)) to reduce both the afterpulsing side-effect11 and also the probability of the Trojan photons to be detected. As a result, wavelength filters are necessary in Bob. Nevertheless, afterpulsing characterization of detectors along with characterization of the wavelength filter at longer wavelengths are necessary in order to prevent the THA.
Lack of general security proof
An apparent requirement of the SCW QKD protocol (to prevent photon number splitting (PNS)37,65 and unambiguous state discrimination (USD) attack6,66) is to monitor the carrier signal as highlighted in41,67. However, based on our discussions with ITMO’s engineers, we learned that the monitoring of the reference signal might not be implemented partly due to implementation complexity and partly because they do not deem it necessary for security, because Ref.51 shows that the system is secure against a collective beam splitting (CBS) attack over a large distance. Here, we emphasize that being secure against the CBS attack mentioned in Ref.51 does not guarantee security against more general attacks. As an example, we outline a more powerful attack in “Methods”.
Manipulation of reference pulse
Here we assume that the reference pulse monitoring is implemented in the system and analyse the consequences. If care is not taken during the implementation, there might still be ways for Eve to perform the USD attack as the following.
First, Eve intercepts Alice’s signal just outside Alice’s lab and performs a USD measurement68. For any conclusive measurement, she prepares the same state with a higher mean photon number and sends it to Bob via a lossless channel, in order to maximize his detection probability. For any inconclusive measurement, she still needs to send the reference signal to Bob and wants it to be detected. However, sending only the reference signal while suppressing the sidebands does not work as it will introduce errors. Instead, Eve wishes the subcarrier signal detection probability to be as low as possible while still keeping the reference signal detection probability as high as possible. The number of photons in the subcarrier and reference signal—after Bob’s modulation—is given in Ref.51 as
Here, \(\mu _0\) is the mean photon number of the reference pulse, \(\eta (L)\) is channel transmission, \(\eta _B\) is transmission in Bob module, and \(\alpha \) is additional loss induced by Eve. \( |d_{00}^s (\beta ')|\) is the Wigner d-function that decides the number of photons to be shifted from reference to side-bands based on its argument \(\beta '\), which itself is a function of the modulation index and the phase difference between Alice and Bob.
We assume APDs are used for the detection of both the reference and subcarrier signals. Then the detection probability in mode \(i \in \{\text {ref, sb}\}\) is \(P_{\mathrm{det}}^i = 1 - e^{-n_{\mathrm{ph}}^i}\) (for simplicity, we consider unity detection efficiency). For normal operation, \(n_{\mathrm{ph}}^{\mathrm{sb}} \ll n_{\mathrm{ph}}^{\mathrm{ref}}\), which leads to \(P_{\mathrm{det}}^{\mathrm{sb}} \ll P_{\mathrm{det}}^{\mathrm{ref}}\). Depending on the chosen value of m and \( \mu _0\), \(P_{\mathrm{det}}^{\mathrm{sb}}\) can be significantly more sensitive to \(\alpha \) compared to \(P_{\mathrm{det}}^{\mathrm{ref}}\). In that case, increasing \(\alpha \) would reduce \(P_{\mathrm{det}}^{\mathrm{sb}}\) much faster than \(P_{\mathrm{det}}^{\mathrm{ref}}\). As a result, it might be possible for Eve to reduce subcarrier signal detection rate without affecting the reference detection rate considerably. The small reduction in \(P_{\mathrm{det}}^{\mathrm{ref}}\) can be compensated by adjusting the power of the pulses sent during the conclusive measurement cases. The only limitation on \(\alpha \) is that \(P_{\mathrm{det}}^{\mathrm{ref}}\) should not be lowered significantly for Alice and Bob to notice. A countermeasure to this attack can be to monitor the reference and subcarrier detection rates. However, a further study is required to find the optimal strategy to monitor the reference and subcarriers and also to design the monitoring detector, determine \(\mu _0\), monitoring threshold, and m.
Time-shift attack
In order to achieve time synchronization, Alice sends to Bob a continuous 10 MHz sinusoidal optical signal, which is further modulated by a signal of a special shape with \(60\,\mathrm{ms}\) period. The position of bit slots of \(10\,\mathrm{ns}\) period43 and other time intervals are defined with respect to this signal. We suspect that it might be possible for Eve to control the time delay of the reference and side-band signals relative to this synchronization signal to shift their arrival times into a specific moment inside or outside the phase modulation window. This might make the system vulnerable against time-shift attacks (TSA)69. A time-shift attack can be performed on the SCW QKD system as follows. For ease of understanding, let us first assume that there is a time gap between successive phase modulation windows (i.e., they are narrower than the bit slot), and in between the modulation windows the phase is 0. We assume a faked-state attack in which Eve stays outside of Alice’s module and performs USD of Alice’s states. Whenever she obtains a conclusive outcome, she sends the same state \(\varphi _E\) to Bob in the correct time window (i.e., she does not alter the arrival time). When Bob measures in the same basis, and \(\varphi _E = \varphi _B\) (\(\varphi _E \ne \varphi _B\)), he gets a click (no click). However, when Eve obtains an inconclusive outcome, she generates a \(\varphi _E = \pi \) state and sends it in-between the phase modulation windows. Since in between the modulation window the phase applied is 0, this ensures no detection by Bob’s detector.
In our discussion with the developers, we learned that in the current SCW QKD implementation, there is no gap between successive phase modulation windows. However, at the transition region from one window to the next, there is a fast fluctuation. Thus, it will be interesting to know what effective phase shift is experienced by a pulse if it is sent at the time interval corresponding to the fluctuations. For example, if the effective phase shift is \(\varphi _0\), then it might still be possible for Eve to remain inconspicuous during the inconclusive measurement slots by sending a state \(\varphi _E = \pi + \varphi _0\). However, the feasibility of this attack can only be ascertained by experimental testing. For that, one needs to characterize Bob’s phase modulation windows—including the transition regions—in the time domain for all phase values. Click processing by Bob will also need to be checked for detection times in the transition regions.
Privacy amplification method
In the composability framework of QKD70, to achieve \(\epsilon \)-security, it is required that Alice and Bob estimate the upper bound of Eve’s information on their key up to the end of error correction step, and apply a proper universal-2 hash function. This is done to generate a shorter secret key such that the probability that the key is not perfect and the protocol did not abort is bounded by \(\epsilon \). However, the present system does privacy amplification by first calculating secret key size and then randomly discarding bits in the error-corrected key to match that calculated secret key size. The disadvantage of this random key removal procedure compared to hashing is that Eve can listen to the classical communication between Alice and Bob and follow the exact procedure to discard bits from her own set. At the end, \(\epsilon \)-security cannot be guaranteed. To make the secret key \(\epsilon \)-secure according to the composability framework, the proper implementation of privacy amplification using the hash function is advised.
Finite-key-size analysis
In the present system, the size of the raw key is limited by the size of Alice’s memory (1 Mbit). According to the developers, this leads to a sifted key size of \(\approx 20\,\mathrm{kbit}\) for a distance of 12 km. For a larger distance of \(200\,\mathrm{km}\), the size becomes as low as \(\approx 10\,\mathrm{kbit}\)43. \(10\%\) of this sifted key is used for parameter estimation. This small sample size has a high probability to lead to discrepancies between the estimated and actual parameter values due to finite-size-effects71. Since the present security proof used by the developers does not consider the finite-key-size effects, the system might be vulnerable to them.
Based on our previous analysis on a different system72, we know that the finite-size effects become significant when the sifted key size is lower than \(200\,\mathrm{kbit}\). At that size of the sifted key, the system—without finite-size-analysis—generated a larger secret key than the upper-bound set by the finite-key-size analysis. Thus, security of the generated key was not guaranteed. Since the sifted-key size of \(20\,\mathrm{kbit}\) in the present system is much lower than \(200\,\mathrm{kbit}\), we strongly suspect that finite-size effects are significant. Thus, we advise to develop a thorough finite-key analysis. To do this, any deviation of parameters due to finite-size-effect needs to be analysed. An example of this effect is the collision probability, i.e., the probability of a hash function mapping two different input keys to the same output key. Other examples could be found in Refs.55,70,73,74,75.
Non-quantum random number generator
In the present system, three types of RNGs can be used in an interchangeable manner. One is a pseudorandom number generation software \(drand48\_r\) from Linux operating system. The second is a commercial product manufactured by the developers of this QKD system. The third one is the internal RNG of Altera Cyclone IV FPGA chip. Using a pseudorandom generator (or randomness expansion) does not satisfy the randomness assumption of the security proof. For the other two generators, care should be taken to verify the quantum origin of the random numbers and the quality of implementation.
Intersymbol interference
Owing to the limited bandwidth of the driving electronics, high speed systems might exhibit intensity correlation among the neighboring pulses—an effect known as the intersymbol interference or the pattern effect76,77. The electronic signal applied to the modulator might be dependent on the preceding pulse, which violates the assumption of security proof. This may lead to vulnerability. Testing should be done in order to assess the risk of the intersymbol interference in the present system.
Follow-up stage
After the initial security evaluation report had been delivered in 2017, the follow-up process ensued. Till now, laboratory testing of the two issues controllable detectors and laser damage has been carried out. In both cases, the testing has confirmed the vulnerability’s presence and the manufacturer has designed countermeasures and implemented them in the current version of the SCW QKD system. Most other issues (Trojan-horse attack, lack of general security proof, manipulation of reference pulse, privacy amplification, finite key size effects, non-quantum RNG) have also been addressed as outlined below. Two lower-risk issues, time-shift attack and intersymbol interference, remain to be studied in the future.
Controllable detectors: Both detector units mentioned in “Lack of general security proof” have been tested. It has been found that ID210 is fully controllable by bright light54, while Scontel SNSPD with a built-in electronic countermeasure (recently developed by Scontel) is partially controllable and the countermeasure in it needs to be improved59. The optical power required to control ID210 can easily be generated and transmitted through Bob’s optical scheme54, confirming our original risk assessment. Technical countermeasures against this attack are currently under consideration. We remark that this vulnerability remains unsolved in most existing QKD systems78.
Laser damage attack: as suggested in “Laser damage”, we have performed laboratory testing of the VOA unit (FOD 5418). We have found it to be severely vulnerable to the LDA34. A brief application of \(\sim 2.8\,\mathrm{W}\) c.w. laser power damages a metal film layer inside this component and reliably reduces its attenuation by \(\sim 10\,\mathrm{dB}\), which renders the key insecure. A countermeasure currently under consideration is to insert another component between the line and the VOA, in order to prevent the latter from being exposed to high power. Candidates for this other component are being tested63,64.
Protocol-related issues: A proof of security for a general attack—the lack of which has been highlighted in “Lack of general security proof”—has been developed in Ref.52. It is summarised in “Methods”. The issues discussed in “Lack of general security proof” and “Manipulation of reference pulse* have been closed by an analysis of advanced attack and appropriate countermeasures79,80. We recap these results in “Methods”. Finally, a correct privacy amplification method (“Privacy amplification method”) and finite-key (“Finite-key-size analysis”) have been included in Ref.52. The finite-key analysis is recapped in “Methods”. Since all these issues appear to have been addressed by this recently published theoretical work, we have updated their current hardness level in Table 3 to C3.
Two more issues have also been analysed and patched by the manufacturer. For the Trojan-horse attack (“Trojan-horse attack”), additional components have been added to the optical scheme in order to detect the attack (patent pending). Also, possible Eve’s information acquired by Trojan-horse attack has been quantified and considered in the security model. The non-quantum RNG (“Non-quantum random number generator”) will be replaced in the next version of the system by a quantum one developed by the ITMO team.
Overall, our joint work has allowed ITMO University and Quantum Communications Ltd. to quickly patch most of the loopholes by introducing countermeasures. The implementation hardness levels have been raised from \(C_{\mathrm{init}}\) of CX and C0 at the time of the initial report to the current state \(C_{\mathrm{curr}}\) of mostly C2 or even C3. Countermeasures marked C2 may eventually become C3, after additional experimental testing and improvement. The two groups also continue to jointly verify the protocol security proof.
Conclusion
The lack of security certification methodology for quantum cryptography is ironic, since security is the main concern behind the shift from classical to quantum cryptography. In this work we have presented a methodology for security evaluation of a complete quantum communication system. Our methodology works in an iterative interaction between the certifiers’ evaluation stage and the manufacturer’s follow-up stage. At the evaluation stage, the complete system implementation is subdivided into seven layers, a set of layers (in our case the bottom four) are exhaustively searched for vulnerabilities, and finally each discovered imperfection is categorised based on the hardness of the realised solution and practical risk. At the follow-up stage, work is performed to eliminate these vulnerabilities.
We have applied this methodology to three different QKD systems and presented here the results for the SCW QKD system from ITMO University and Quantum Communications Ltd. In this system, we have found a number of potential security issues—which we expose here without omissions—that need a careful investigation by the manufacturer. Experimental tests, countermeasure and theory development have followed. As the result, most of the issues have been addressed, increasing the hardness rating of this implementation. Projects of a very similar character are going on with the two other systems (by ID Quantique and QuantumCTek) that we earlier analysed. I.e., our protocol is applicable beyond the system detailed in this Article. We hope it will pave the way towards development of a security certification methodology for existing and future quantum communication systems.
Our security certification methodology is developed with only point-to-point QKD protocols in mind and we are not sure how applicable it will be for a network scenario. We hope that making the point-to-point systems secure would eventually make the resultant network secure.
One important but sometimes overlooked aspect should be emphasised. When someone is engaged in designing a system, his mindset tends to become biased, and he may not be able to think from a different point of view and see security problems with his own design. This is the very reason the task of security certification should be done in collaboration with third-party experts whose main goal is to find problems. This helps a responsible QKD manufacturer to quickly assess and resolve the security issues, as has clearly happened in the case of ITMO. Furthermore, the third-party analysis should ideally begin during initial design considerations, rather than after the commercial implementation has been completed (as has been the case here).
Methods
Another example of layer subdivision
To give another example, let’s consider commercial QKD system Clavis381. Its operation can be divided into our proposed layer structure as follows. When a customer receives the system, the first steps involve a manual installation procedure that is done according to the instruction from the manufacturer. For example, the user needs to connect Alice and Bob QKD stations with a fiber, setup two control PCs (running Linux OS) to install the ‘Clavis3 Cockpit’ software, configure an Ethernet network with specific IP addresses to establish communication between control PC and Alice-Bob QKD stations, and connect fibers in Bob QKD station in a specific way depending on whether internal or external single-photon detectors are used. During the course of operation, manual interventions may be needed from time to time for maintenance: for instance, if the control software hangs, a manual restart is required. All these fall under layer Q7. Next, the system should interact with some external key management system or encryption engine. These tasks are handled in layer Q6. Next, layer Q5 specifies the post-processing rules: for example, coherent-one-way (COW) QKD protocol with LDPC error correction (with a code rate 2/3) and security parameter of \(\epsilon = 4 \times 10^{-9}\). Next layer Q4 decides which subroutine to initiate: for instance, whether to adjust synchronization between the Alice and Bob QKD stations, optimise modulator voltages in order to maximize the interference visibility, or send qubits from Alice to Bob. The control is then transferred to layer Q3, which executes the chosen subroutines with help from Q2 and Q1. For example, when Q3 initiates the raw key exchange subroutine, the field-programmable gate array (FPGA) chip in Alice—at layer Q2—outputs a stream of 1.25 Gbps digital pulses with adjustable amplitude and width to drive an intensity modulator that prepares the quantum signals. The latter are then sent over the fiber to Bob. Another FPGA at Bob—a layer Q2 device—outputs another stream of 1.25 Gbps pulses to provide the gating signals to the single-photon detectors and receives detection signals from these detectors. Here, the intensity modulators, fiber, and detectors all belong to layer Q1 that—together with components from layer Q2—executes a subroutine initiated by layer Q3.
Faked-state attack strategy
Let’s assume first that there is no reference monitoring implemented in the system. Let’s assume Alice encodes phase \(\varphi _A\). We further assume that Eve—sitting outside Alice’s module—measures the signal (using similar measurement setup as Bob) by randomly applying \(\varphi _E \in \{0, \pi /2, \pi , 3\pi /2 \}\). Another part of her—sitting near Bob—sends bright c.w. light of power \(P_{\mathrm{blind}}\) to blind Bob’s side-band detector. When \(\varphi _E =\varphi _A\), she gets a detection. In this case, she recreates the reference-subcarrier pulse pairs scaling their powers up to make \(P_{\mathrm{ref}} = 3\,\mathrm{mW}\). When Bob also measures in the same basis as Alice-Eve and \(\varphi _E = \varphi _B\) (\(\varphi _E =\varphi _B \pm \pi \)), this results in constructive (destructive) interference and will (will not) trigger a click in the blinded sideband detector. If Bob and Eve select different bases, Bob should not register any detection. For the slots when Eve gets no detection due to \(\varphi _E \ne \varphi _A\) or low detection efficiency, she simply does nothing owing to the absence of reference pulse monitoring, and these events will appear as loss to Bob.
In order to successfully perform this attack in practice, the blinded detector should be characterized to know \(P_{\mathrm{never}}\) and \(P_{\mathrm{always}}\), which are the thresholds of the trigger pulse power making the detector never click and always click. The trigger pulse power \(P_{\mathrm{tr}}\) in the successful attack needs to satisfy the conditions
However, if the reference monitoring is implemented, both the reference and sideband monitoring detectors would be blinded and Eve will need to modify her strategy. When she has a conclusive outcome, she proceeds as before. However, when her measurement outcome is inconclusive, i.e., \(\varphi _E \ne \varphi _A\), Eve needs to tailor the power of the reference signal in such a way that it is enough to force a click on the blinded reference detector but not on the subcarrier detector.
Note that, sometimes Eve gets a detection when measuring in the opposite basis to that of Alice and has no way to know if her measurement result coincides with Alice’s bit. However, these states are either not detected at Bob due to Eve-Bob basis mismatch or detected and then discarded during sifting due to Alice-Bob basis mismatch.
A more general attack than CBS attack mentioned in Ref.51
-
For each quantum signal going from Alice to Bob, Eve splits off a tiny fraction x of each signal in the channel.
-
Eve performs a quantum non-demolition measurement on the split signal66.
-
If no photons are found, she splits off another fraction x. She does this until her induced loss equals the line loss.
-
When photons are found, she keeps them in her quantum memory and sends the rest of the radiation to Bob via a lossless channel. The state of each photon in her possession is
$$\begin{aligned} |{\psi }\rangle _e = (a^{\dagger } + m e^{i\varphi _A} b^{\dagger }) |{0}\rangle _A |{0}\rangle _B, \end{aligned}$$(3)where \(a^{\dagger }\) and \(b^{\dagger }\) are the creation operators on the carrier and subcarrier modes respectively, m is the modulation index and \(\varphi _A\) is Alice’s phase encoding.
-
For different values of \(\varphi _A \in \{0, \pi /2, \pi , 3\pi /2\}\), Eve’s states are not orthogonal. To make them orthogonal to each other, Eve needs to apply a filtering operation
$$\begin{aligned}&A_{\mathrm{success}} = m |{0}\rangle _B \langle {0}|_B + |{1}\rangle _B \langle {1}|_B,\nonumber \\&A_{\mathrm{fail}} = I - A_{\mathrm{success}}. \end{aligned}$$(4)This turns \(|{\psi }\rangle _e\) into
$$\begin{aligned} |{\psi '}\rangle _e = (a^{\dagger } + e^{i\varphi _A} b^{\dagger }) |{0}\rangle _A |{0}\rangle _B \end{aligned}$$(5)with a success probability
$$\begin{aligned} P_{\mathrm{success}} = \frac{2m^2}{1 + m^2}. \end{aligned}$$(6) -
When the bases are revealed during sifting, Eve simply measures \(|{\psi '}\rangle _e\) in the correct basis to extract \(\varphi _A\).
This attack is more powerful because, in Ref.51, for a line loss \(\eta \) Eve uses a \((1-\eta ) : \eta \) beam splitter and the attack only succeeds when both Eve and Bob receive a photon. This becomes less likely as the line loss increases. However, in the present case Eve is not restricted to split in the \((1-\eta ) : \eta \) ratio for the line loss \(\eta \), which gives her more power. Thus, the security proof should be updated to include more (and ideally the most) general attacks than the collective beam splitting attacks.
Asymptotic security
We assume here, that the family of protocols considering in this paper belongs to the class of one-way QKD protocols with independent and identically-distributed (i.i.d.) information carriers and direct reconciliation. It is commonly accepted that secure key generation rate K for the protocols of this class in the presence of collective attacks in asymptotic regime is lower bounded according to82,83 by the Devetak-Winter bound84
where \(\nu _S\) is the repetition rate; \(P_B\) is the probability of successful decoding and accepting a bit in a single transmission window; Q is the quantum bit error rate (QBER), the probability that a bit accepted by Bob is erroneous; \(\mathrm{code}_{\mathrm{EC}}(Q)\) is the amount of information revealed by Alice through the public channel for the sake of error correction, which depends on QBER and is limited by the Shannon bound: \(\mathrm{code}_{\mathrm{EC}}(Q)\ge h(Q)\) where \(h(Q)=-Q\log _2Q-(1-Q)\log _2(1-Q)\) is the binary Shannon entropy. Quantity \(\chi (A:E)\) in Eq. (7)) is the Holevo capacity, giving an upper bound for amount of information accessible to eavesdropper Eve in a given collective attack (quantum channel). It is well-known that coherent attacks in i.i.d. case can be bounded with collective attacks. So one usually considers coherent attacks as general collective attacks85 in terms of arbitrary unitary operations on purified states in enlarged Hilbert space (described in terms of isometry) provided by Eve.
In Reference52, the result of arbitrary isometry is considered in order to estimate Holevo capacity in complementary channel. Eve performs unitary operation (described by isometry) between states in the channel and Eve’s ancillas to make them (in general case) entangled in some way86. It has been shown that Holevo capacity of complementary channel is maximized when states become untangled (but interacted). Further considering the property of isometry, i.e., preserving the overlap between the states, it has been shown that highest mutual information between Alice and Eve is bounded by the Holevo bound. This statement eliminates the necessity to consider particular kinds of isometries.
In case of subcarrier-wave quantum key distribution Holevo bound can be found considering reduced unconditioned channel density operator, i.e., considering only two states since Eve can wait to measure her states after reconciliation. Therefore the obtained Holevo bound using binary Shannon entropy function \(h(x)=-x\log _2 x-(1-x)\log _2(1-x)\) of the unconditioned channel density operator eigenvalues is as follows:
where \(\mu _0\) is the amplitude of the coherent state on the of carrier wave determined by the average number of photons in a transmission window provided with coherent monochromatic light beam with optical frequency \(\omega \), \(d^S_{00}(\beta )\) is the Wigner d-function from the quantum theory of angular momentum87, and \(\beta \) is determined by the modulation index m51.
Advanced unambiguous-state-discrimination attack
The collective attack that considers a mutual information between Alice and Eve might not be the most general attack. There might be attacks that decrease conditional mutual information I(A; B|E) to zero. An example of such attack has been introduced in Ref.80 where Eve performs an errorless USD measurement88,89 then blocks inconclusive results and alters (amplifies and adds errors) the distinguished states. The latter is necessary to maintain both detection and error rates. In Reference80 the condition of revealing Eve’s actions90 is generalised as
where \(P_{\mathrm{det}}\) is an expected detection probability and \(P_{\mathrm{USD}}\) is the probability of unambiguous state discrimination. Obviously there are two main strategies to increase the performance of the system. The first is to increase \(P_{\mathrm{det}}\) and the second is to decrease \(P_{\mathrm{USD}}\). We refer to Refs.79,80 for a further discussion of proposed approaches against the USD attack.
Finite-key security
Since the resources such as time and memory are finite, it is not sufficient to consider asymptotic security. Therefore, in Ref.52 a finite-key analysis has been performed. To estimate appropriate bound on secure key rate we consider the notation of Renyi entropies \(H_{\alpha }(X)=\frac{1}{1-\alpha } \log \left( \sum _{i=1}^n p_i^\alpha \right) \), because they describe the worst case and not the average one. In the paper we consider that \(\alpha \rightarrow \infty \) since we use min-entropy \(H_\infty (X)=H_{\mathrm{min}} =-\log \max _i p_i\). Thereby a quantum asymptotic equipartition property (QAEP)91 is considered in order to bound \(\varepsilon \)-smooth min-entropy by von Neumann entropy. It means that for a large number of rounds, the operationally relevant total uncertainty can be well approximated by the sum over all i.i.d. rounds. In SCW QKD, conditional von Neumann entropy, or more precisely an entropy of Alice’s bit conditioned on Eve’s side-information in a single round, is bound as \(H(\mathbf {A}|\mathbf {E})\ge 1-\chi (\rho )\).
To provide the key extraction one should carry out the following steps.
-
(i)
Parameter estimation. One should estimate the error rate (Bob publicly sends a random subset of k bits to Alice, and she estimates the QBER \(Q_{\mathrm{est}}\) in that subset) and detection rate at Bob’s side.
-
(ii)
Error correction. At this step both legitimate parties should check and correct the errors in their bit strings. It can be done using any error correction code.
-
(iii)
Privacy amplification. In Reference52, the privacy amplification has been studied using the bound from Ref.92, which tells us that the trace distance d between the protocol’s output and an ideal output (where the key is uniform and independent from Eve, even after Eve knows the matrix used for the hashing) is bound above by
$$\begin{aligned} d&= \frac{1}{2}\Vert \rho _{\mathrm{KFE}}-\omega _{K}\otimes \sigma _{\mathrm{FE}}\Vert _{1} \nonumber \\&\le \varepsilon _s + \frac{1}{2}\sqrt{2^{l - H_{\mathrm{min}}^{\varepsilon _s}(\mathbf {A}'|\mathbf {E})}} \nonumber \\&\le \varepsilon _s + \frac{1}{2}\sqrt{2^{-\mathrm{loss}_{\mathrm{PA}}}} \nonumber \\&\le \varepsilon _s + \varepsilon _{\mathrm{PA}} =\varepsilon _{\mathrm{sec}}, \end{aligned}$$(10)where in the last step the quantity \(\varepsilon _{sec}\) is introduced as an upper bound on d.
Reference52 gives the final result that the protocol is \(\varepsilon _{\mathrm{corr}}\)-correct with \(\varepsilon _{\mathrm{corr}} = \varepsilon _{\mathrm{EC}}\) and \(\varepsilon _{\mathrm{sec}}\)-secure with \(\varepsilon _{\mathrm{sec}} =\varepsilon _s + \varepsilon _{\mathrm{PA}}\), hence \(\varepsilon _{\mathrm{QKD}}\)-secure-and-correct, with \(\varepsilon _{\mathrm{QKD}} =\varepsilon _{\mathrm{EC}} + \varepsilon _s + \varepsilon _{\mathrm{PA}}\) providing secure bit string with length
References
Bennett, C. H. & Brassard, G. Quantum cryptography: Public key distribution and coin tossing. In Proceedings of International Conference on Computers, Systems, and Signal Processing, 175–179 (IEEE Press, New York, Bangalore, India, 1984).
Yin, J. et al. Satellite-based entanglement distribution over 1200 kilometers. Science 356, 1140. https://doi.org/10.1126/science.aan3211 (2017).
Lydersen, L. et al. Hacking commercial quantum cryptography systems by tailored bright illumination. Nat. Photon. 4, 686–689. https://doi.org/10.1038/nphoton.2010.214 (2010).
Xu, F., Qi, B. & Lo, H.-K. Experimental demonstration of phase-remapping attack in a practical quantum key distribution system. New J. Phys. 12, 113026. https://doi.org/10.1088/1367-2630/12/11/113026 (2010).
Sun, S.-H., Jiang, M.-S. & Liang, L.-M. Passive Faraday-mirror attack in a practical two-way quantum-key-distribution system. Phys. Rev. A 83, 062331. https://doi.org/10.1103/PhysRevA.83.062331 (2011).
Sajeed, S. et al. Attacks exploiting deviation of mean photon number in quantum key distribution and coin tossing. Phys. Rev. A 91, 032326. https://doi.org/10.1103/PhysRevA.91.032326 (2015).
Sajeed, S. et al. Security loophole in free-space quantum key distribution due to spatial-mode detector-efficiency mismatch. Phys. Rev. A 91, 062301. https://doi.org/10.1103/PhysRevA.91.062301 (2015).
Sajeed, S. et al. Insecurity of detector-device-independent quantum key distribution. Phys. Rev. Lett. 117, 250505. https://doi.org/10.1103/PhysRevLett.117.250505 (2016).
Makarov, V. et al. Creation of backdoors in quantum communications via laser damage. Phys. Rev. A 94, 030302. https://doi.org/10.1103/PhysRevA.94.030302 (2016).
Huang, A. et al. Testing random-detector-efficiency countermeasure in a commercial system reveals a breakable unrealistic assumption. IEEE J. Quantum Electron. 52, 8000211. https://doi.org/10.1109/JQE.2016.2611443 (2016).
Sajeed, S., Minshull, C., Jain, N. & Makarov, V. Invisible Trojan-horse attack. Sci. Rep. 7, 8403. https://doi.org/10.1038/s41598-017-08279-1 (2017).
Pinheiro, P. V. P. et al. Eavesdropping and countermeasures for backflash side channel in quantum cryptography. Opt. Express 26, 21020. https://doi.org/10.1364/OE.26.021020 (2018).
Hwang, W.-Y. Quantum key distribution with high loss: Toward global secure communication. Phys. Rev. Lett. 91, 057901. https://doi.org/10.1103/PhysRevLett.91.057901 (2003).
Lo, H.-K., Ma, X. & Chen, K. Decoy state quantum key distribution. Phys. Rev. Lett. 94, 230504. https://doi.org/10.1103/PhysRevLett.94.230504 (2005).
Lo, H.-K., Curty, M. & Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108, 130503. https://doi.org/10.1103/PhysRevLett.108.130503 (2012).
Acín, A. et al. Device-independent security of quantum cryptography against collective attacks. Phys. Rev. Lett. 98, 230501. https://doi.org/10.1103/PhysRevLett.98.230501 (2007).
Lucamarini, M., Yuan, Z. L., Dynes, J. F. & Shields, A. J. Overcoming the rate-distance limit of quantum key distribution without quantum repeaters. Nature 557, 400–403. https://doi.org/10.1038/s41586-018-0066-6 (2018).
Länger, T. & Lenhart, G. Standardization of quantum key distribution and the ETSI standardization initiative ISG-QKD. New J. Phys. 11, 055051. https://doi.org/10.1088/1367-2630/11/5/055051 (2009).
ETSI white paper no. 8, “Quantum safe cryptography and security” (2015). http://www.etsi.org/images/files/ETSIWhitePapers/QuantumSafeWhitepaper.pdf. Accessed 10 Mar 2020.
ETSI white paper no. 27, “Implementation security of quantum cryptography” (2018). https://www.etsi.org/images/files/ETSIWhitePapers/etsi_wp27_qkd_imp_sec_FINAL.pdf. Accessed 10 Mar 2020.
ISO/IEC 23837, first working draft, “Security requirements, test and evaluation methods for quantum key distribution” (2019). https://www.iso.org/standard/77097.html. Accessed 24 Sept 2019.
International Telecommunications Union, Recommendation under study X.sec-QKDN-ov, “Security Requirements for QKD Networks–Overview” (2019). https://www.itu.int/itu-t/workprog/wp_item.aspx?isn=15001. . Accessed 24 Sept 2019.
International Telecommunications Union, Recommendation under study X.sec-QKDN-tn, “Security Requirements for QKD Networks – Trusted node” (2019). https://www.itu.int/itu-t/workprog/wp_item.aspx?isn=15244. Accessed 24 Sept 2019.
Lucamarini, M. et al. Practical security bounds against the Trojan-horse attack in quantum key distribution. Phys. Rev. X 5, 031030. https://doi.org/10.1103/PhysRevX.5.031030 (2015).
Vakhitov, A., Makarov, V. & Hjelme, D. R. Large pulse attack as a method of conventional optical eavesdropping in quantum cryptography. J. Mod. Opt. 48, 2023–2038. https://doi.org/10.1080/09500340108240904 (2001).
Gisin, N., Fasel, S., Kraus, B., Zbinden, H. & Ribordy, G. Trojan-horse attacks on quantum-key-distribution systems. Phys. Rev. A 73, 022320. https://doi.org/10.1103/PhysRevA.73.022320 (2006).
Xu, F. et al. Experimental quantum key distribution with source flaws. Phys. Rev. A 92, 032305. https://doi.org/10.1103/PhysRevA.92.032305 (2015).
Huang, A., Sun, S.-H., Liu, Z. & Makarov, V. Quantum key distribution with distinguishable decoy states. Phys. Rev. A 98, 012330. https://doi.org/10.1103/PhysRevA.98.012330 (2018).
Huang, A. et al. Laser-seeding attack in quantum key distribution. Phys. Rev. Appl. 12, 064043. https://doi.org/10.1103/PhysRevApplied.12.064043 (2019).
Wu, Z. et al. Hacking single-photon avalanche detectors in quantum key distribution via pulse illumination. Opt. Express 28, 25574–25590. https://doi.org/10.1364/OE.397962 (2020).
Tomita, A. Implementation security certification of decoy-BB84 quantum key distribution systems. Adv. Quantum Technol. 2, 1900005. https://doi.org/10.1002/qute.201900005 (2019).
Dixon, A. R. et al. Quantum key distribution with hacking countermeasures and long term field trial. Sci. Rep. 7, 1978. https://doi.org/10.1038/s41598-017-01884-0 (2017).
OSI model, Wikipedia. http://en.wikipedia.org/wiki/OSI_model. Accessed 10 Mar 2020.
Huang, A. et al. Laser-damage attack against optical attenuators in quantum key distribution. Phys. Rev. Appl. 13, 034017. https://doi.org/10.1103/PhysRevApplied.13.034017 (2020).
Meda, A. et al. Quantifying backflash radiation to prevent zero-error attacks in quantum key distribution. Light Sci. Appl. 6, e16261. https://doi.org/10.1038/lsa.2016.261 (2017).
Jain, N. et al. Device calibration impacts security of quantum key distribution. Phys. Rev. Lett. 107, 110501. https://doi.org/10.1103/PhysRevLett.107.110501 (2011).
Bennett, C. H., Bessette, F., Salvail, L., Brassard, G. & Smolin, J. Experimental quantum cryptography. J. Cryptol. 5, 3–28. https://doi.org/10.1007/bf00191318 (1992).
Rau, M. et al. Spatial mode side channels in free-space QKD implementations. IEEE J. Quantum. Electron. 21, 6600905. https://doi.org/10.1109/JSTQE.2014.2372008 (2015).
Chaiwongkhot, P. et al. Generalized spatial-mode detection efficiency mismatch in a free-space QKD system with Zernike polynomials. QCrypt 2018 conference abstract (2018). http://www.vad1.com/publications/chaiwongkhot2018.QCrypt2018-subm196.pdf.
Mérolla, J.-M., Mazurenko, Y., Goedgebuer, J.-P., Porte, H. & Rhodes, W. T. Phase-modulation transmission system for quantum cryptography. Opt. Lett. 24, 104–106. https://doi.org/10.1364/OL.24.000104 (1999).
Mérolla, J.-M., Mazurenko, Y., Goedgebuer, J.-P. & Rhodes, W. T. Single-photon interference in sidebands of phase-modulated light for quantum cryptography. Phys. Rev. Lett. 82, 1656–1659. https://doi.org/10.1103/PhysRevLett.82.1656 (1999).
Muller, A. et al. ‘Plug and play’ systems for quantum cryptography. Appl. Phys. Lett. 70, 793–795. https://doi.org/10.1063/1.118224 (1997).
Gleim, A. V. et al. Secure polarization-independent subcarrier quantum key distribution in optical fiber channel using BB84 protocol with a strong reference. Opt. Express 24, 2619–2633. https://doi.org/10.1364/OE.24.002619 (2016).
Mora, J. et al. Experimental demonstration of subcarrier multiplexed quantum key distribution system. Opt. Lett. 37, 2031–2033. https://doi.org/10.1364/OL.37.002031 (2012).
Ortigosa-Blanch, A. & Capmany, J. Subcarrier multiplexing optical quantum key distribution. Phys. Rev. A 73, 024305. https://doi.org/10.1103/PhysRevA.73.024305 (2006).
Kynev, S. M. et al. Free-space subcarrier wave quantum communication. J. Phys. Conf. Ser. 917, 052003. https://doi.org/10.1088/1742-6596/917/5/052003 (2017).
Gleĭm, A. V. et al. Sideband quantum communication at 1 Mbit/s on a metropolitan area network. J. Opt. Technol. 86, 362–367. https://doi.org/10.1364/JOT.84.000362 (2017).
Chistyakov, V. V., Gleim, A. V., Egorov, V. I. & Nazarov, Y. V. Implementation of multiplexing in a subcarrier-wave quantum cryptography system. J. Phys. Conf. Ser. 541, 012078. https://doi.org/10.1088/1742-6596/541/1/012078 (2014).
Bannik, O. I. et al. Multinode subcarrier wave quantum communication network. QCrypt 2017 conference abstract Th413 (2017). http://2017.qcrypt.net/wp-content/uploads/2017/09/Th413.pdf.
Chistyakov, V. V. et al. Software-defined subcarrier wave quantum networking operated by OpenFlow protocol. arXiv:1709.09081.
Miroshnichenko, G. P., Kozubov, A. V., Gaidash, A. A., Gleim, A. V. & Horoshko, D. B. Security of subcarrier wave quantum key distribution against the collective beam-splitting attack. Opt. Express 26, 11292–11308. https://doi.org/10.1364/OE.26.011292 (2018).
Kozubov, A., Gaidash, A. & Miroshnichenko, G. Finite-key security for quantum key distribution systems utilizing weak coherent states. arXiv:1903.04371.
Lydersen, L. et al. Thermal blinding of gated detectors in quantum cryptography. Opt. Express 18, 27938–27954. https://doi.org/10.1364/oe.18.027938 (2010).
Chistiakov, V., Huang, A., Egorov, V. & Makarov, V. Controlling single-photon detector ID210 with bright light. Opt. Express 27, 32253–32262. https://doi.org/10.1364/OE.27.032253 (2019).
Tomamichel, M., Lim, C. C. W., Gisin, N. & Renner, R. Tight finite-key analysis for quantum cryptography. Nat. Commun. 3, 634. https://doi.org/10.1038/ncomms1631 (2012).
Ivanova, A., Chivilikhin, S., Miroshnichenko, G. & Gleim, A. Fiber quantum random number generator, based on vacuum fluctuations. Nanosyst. Phys. Chem. Math. 8, 441. https://doi.org/10.17586/2220-8054-2017-8-4-441-446 (2017).
Lydersen, L., Akhlaghi, M. K., Majedi, A. H., Skaar, J. & Makarov, V. Controlling a superconducting nanowire single-photon detector using tailored bright illumination. New J. Phys. 13, 113042. https://doi.org/10.1088/1367-2630/13/11/113042 (2011).
Tanner, M. G., Makarov, V. & Hadfield, R. H. Optimised quantum hacking of superconducting nanowire single-photon detectors. Opt. Express 22, 6734–6748. https://doi.org/10.1364/OE.22.006734 (2014).
Elezov, M., Ozhegov, R., Goltsman, G. & Makarov, V. Countermeasure against bright-light attack on superconducting nanowire single-photon detector in quantum key distribution. Opt. Express 27, 30979. https://doi.org/10.1364/OE.27.030979 (2019).
Bugge, A. N. et al. Laser damage helps the eavesdropper in quantum cryptography. Phys. Rev. Lett. 112, 070503. https://doi.org/10.1103/PhysRevLett.112.070503 (2014).
Jain, N. et al. Trojan-horse attacks threaten the security of practical quantum cryptography. New J. Phys. 16, 123030. https://doi.org/10.1088/1367-2630/16/12/123030 (2014).
Jain, N. et al. Risk analysis of Trojan-horse attacks on practical quantum key distribution systems. IEEE J. Sel. Top. Quantum Electron. 21, 6600710. https://doi.org/10.1109/JSTQE.2014.2365585 (2015).
Ponosova, A. et al. Isolation reduction of quantum cryptography systems induced by continuous-wave high-power laser. conference abstract at School on Quantum Technologies, Roza Khutor, Russia, 1–6 March 2020. http://www.vad1.com/publications/ponosova2020.QTS-poster39.pdf.
Ruzhitskaya, D. et al. Laser damage attack on an integrated optics chip for quantum key distribution. conference abstract at School on Quantum Technologies, Roza Khutor, Russia, 1–6 March 2020. http://www.vad1.com/publications/ruzhitskaya2020.QTS-poster40.pdf.
Lütkenhaus, N. Quantum key distribution with realistic states: Photon-number statistics in the photon-number splitting attack. New J. Phys. 4, 44. https://doi.org/10.1088/1367-2630/4/1/344 (2002).
Dušek, M., Jahma, M. & Lütkenhaus, N. Unambiguous state discrimination in quantum cryptography with weak coherent states. Phys. Rev. A 62, 022306. https://doi.org/10.1103/PhysRevA.62.022306 (2000).
Bennett, C. H. Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68, 3121–3124. https://doi.org/10.1103/PhysRevLett.68.3121 (1992).
Huttner, B., Muller, A., Gautier, J. D., Zbinden, H. & Gisin, N. Unambiguous quantum measurement of nonorthogonal states. Phys. Rev. A 54, 3783–3789. https://doi.org/10.1103/PhysRevA.54.3783 (1996).
Zhao, Y., Fung, C.-H.F., Qi, B., Chen, C. & Lo, H.-K. Quantum hacking: Experimental demonstration of time-shift attack against practical quantum-key-distribution systems. Phys. Rev. A 78, 042333. https://doi.org/10.1103/PhysRevA.78.042333 (2008).
Renner, R. Security of quantum key distribution. Ph.D. thesis, ETH Zurich (2005). https://doi.org/10.3929/ethz-a-005115027.
Ben-Or, M., Horodecki, M., Leung, D. W., Mayers, D. & Oppenheim, J. The universal composable security of quantum key distribution. Lect. Notes Comp. Sci. 3378, 386–406. https://doi.org/10.1007/978-3-540-30576-7_21 (2005).
Chaiwongkhot, P., Sajeed, S., Lydersen, L. & Makarov, V. Finite-key-size effect in a commercial plug-and-play QKD system. Quantum Sci. Technol. 2, 044003. https://doi.org/10.1088/2058-9565/aa804b (2017).
Cai, R. Y. Q. & Scarani, V. Finite-key analysis for practical implementations of quantum key distribution. New J. Phys. 11, 045024. https://doi.org/10.1088/1367-2630/11/4/045024 (2009).
Renner, R. & König, R. Universally composable privacy amplification against quantum adversaries. Lect. Notes Comp. Sci. 3378, 407–425. https://doi.org/10.1007/978-3-540-30576-7_22 (2005).
Scarani, V. & Renner, R. Quantum cryptography with finite resources: Unconditional security bound for discrete-variable protocols with one-way postprocessing. Phys. Rev. Lett. 100, 200501. https://doi.org/10.1103/PhysRevLett.100.200501 (2008).
Yoshino, Ken-ichiro et al. Quantum key distribution with an efficient countermeasure against correlated intensity fluctuations in optical pulses. NPJ Quantum Inf. 4, 8. https://doi.org/10.1038/s41534-017-0057-8 (2018).
Roberts, G. L. et al. Patterning-effect mitigating intensity modulator for secure decoy-state quantum key distribution. Opt. Lett. 43, 5110. https://doi.org/10.1364/OL.43.005110 (2018).
Fedorov, A. et al. Comment on Inherent security of phase coding quantum key distribution systems against detector blinding attacks (2018 Laser Phys. Lett. 15 095203). Laser Phys. Lett. 16, 019401. https://doi.org/10.1088/1612-202X/aaf22d (2019).
Gaidash, A., Kozubov, A. & Miroshnichenko, G. Methods of decreasing the unambiguous state discrimination probability for subcarrier wave quantum key distribution systems. J. Opt. Soc. Am. B 36, B16–B19. https://doi.org/10.1364/JOSAB.36.000B16 (2019).
Gaidash, A., Kozubov, A. & Miroshnichenko, G. Countermeasures for advanced unambiguous state discrimination attack on quantum key distribution protocol based on weak coherent states. Phys. Scr. 94, 125102. https://doi.org/10.1088/1402-4896/ab3277 (2019).
Clavis3 QKD platform. https://www.idquantique.com/quantum-sensing/products/clavis3-qkd-platform/. Accessed 10 Mar 2020.
Scarani, V. et al. The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301–1350. https://doi.org/10.1103/RevModPhys.81.1301 (2009).
Pirandola, S. et al. Advances in quantum cryptography. Adv. Opt. Photon. 12, 1012. https://doi.org/10.1364/AOP.361502 (2020).
Devetak, I. & Winter, A. Distillation of secret key and entanglement from quantum states. Proc. R. Soc. A 461, 207–235. https://doi.org/10.1098/rspa.2004.1372 (2005).
Christandl, M., König, R. & Renner, R. Postselection technique for quantum channels with applications to quantum cryptography. Phys. Rev. Lett. 102, 020504. https://doi.org/10.1103/PhysRevLett.102.020504 (2009).
Ekert, A. K., Huttner, B., Palma, G. M. & Peres, A. Eavesdropping on quantum-cryptographical systems. Phys. Rev. A 50, 1047. https://doi.org/10.1103/PhysRevA.50.1047 (1994).
Varshalovich, D. A., Moskalev, A. N. & Khersonskii, V. K. Quantum Theory of Angular Momentum (World Scientific, Singapore, 1988).
Peres, A. & Terno, D. R. Optimal distinction between non-orthogonal quantum states. J. Phys. A 31, 7105. https://doi.org/10.1088/0305-4470/31/34/013 (1998).
Chefles, A. Unambiguous discrimination between linearly independent quantum states. Phys. Lett. A 239, 339–347. https://doi.org/10.1016/S0375-9601(98)00064-4 (1998).
Tamaki, K. & Tsurumaru, T. Security proof of quantum key distribution. IEICE Trans. Fundam. Electron. Comm. Comput. Sci. E93.A, 880–888. https://doi.org/10.1587/transfun.E93.A.880 (2010).
Tomamichel, M., Colbeck, R. & Renner, R. A fully quantum asymptotic equipartition property. IEEE Trans. Inf. Theory 55, 5840–5847. https://doi.org/10.1109/TIT.2009.2032797 (2009).
Tomamichel, M., Schaffner, C., Smith, A. & Renner, R. Leftover hashing against quantum side information. IEEE Trans. Inf. Theory 57, 5524–5535. https://doi.org/10.1109/TIT.2011.2158473 (2011).
Acknowledgements
We thank M. Legré, N. Lütkenhaus, E. Tan and R. Renner for discussions. This work was funded by NSERC of Canada (programs Discovery and CryptoWorks21), MRIS of Ontario, and the Ministry of Education and Science of Russia (programs 5-in-100 and NTI center for quantum communications). P.C. was supported by Thai DPST scholarship. A.H. was supported by China Scholarship Council, the National Natural Science Foundation of China (Grant 61901483), and the National Key Research and Development Program of China (Grant 2019QY0702). H.Q. is sponsored by Shanghai Pujiang Program. This work was funded by Government of Russian Federation (grant 08-08).
Author information
Authors and Affiliations
Contributions
S.S., P.C., A.H., H.Q., and V.M. performed the security analysis. V.E., A.K., A.Ga., V.C., A.V., and A.Gl. developed the SCW QKD system, its security proof and countermeasures to the attacks listed in the security analysis. All authors wrote the article.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Sajeed, S., Chaiwongkhot, P., Huang, A. et al. An approach for security evaluation and certification of a complete quantum communication system. Sci Rep 11, 5110 (2021). https://doi.org/10.1038/s41598-021-84139-3
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-021-84139-3
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.