Abstract
Through introducing controlled alternate quantum walks, we present controlled alternate quantum walks (CAQW) based quantum hash function. CAQW based quantum hash function have excellent security, outstanding statistical performance and splendid expansibility. Furthermore, due to the structure of alternate quantum walks, implementing CAQW based quantum hash function significantly reduces the resources necessary for its feasible experimental realization than implementing other quantum hash functions.
Similar content being viewed by others
Introduction
Hash function, as an important part of modern cryptography, has wide applications in message authentication, signature protocol and Public Key Infrastructure. There are many theoretical studies about classical hash functions and mature hash functions such as MD5, SHA1 and SHA512. These hash functions are generally constructed based on mathematics complexity and thus they are computationally secure. In the field of quantum communication, Quantum key distribution(QKD) is the most mature branch of quantum communication. QKD generally contains three steps: (1) raw key sifting, (2) error reconciliation, and (3)privacy amplification. As an important step of QKD, privacy amplification is implemented by adopting universal hash functions1. Besides, classical hash functions are used extensively in other quantum protocols to ensure the safety of quantum communication, yet it is contradictory with the fact that the quantum computer could solve difficult mathematical problems. For the reason above, Li et al. presented a kind of quantum hash function based on two-particle controlled interacting quantum walks (CIQW)2,3. This quantum hash function guarantees the security of hash function by infinite possibilities of the initial state and the irreversibility of measurement rather than hard mathematic problems. In ref.4 Yang et al. improved the CIQW based quantum hash function and found its applications in the privacy amplification process of quantum key distribution, pseudorandom number generation and image encryption. But this quantum hash function still have two unsatisfactory defects. One of that is for the quantum hash function2,3, predictable collisions happens for some special states as initial coin state. The second one is that realization of controlled two-particle interacting quantum walks needs more resource than one-particle quantum walks. Therefore, we present the quantum hash function based on controlled alternate quantum walks (CAQW) here to avoid these defects.
Quantum walk, one famous quantum computation model, has widely applications in quantum computation and quantum information5,6,7,8,9,10,11,12. Alternate quantum walk is a kind of quantum walk which attracts a lot of attentions13,14,15,16,17,18,19,20. Di Franco et al.13,14 proposed a two-dimensional quantum walk where the requirement of a higher dimensionality of the coin space is substituted with the alternance of the directions in which the walker can move. They also proposed the N-dimensional alternate quantum walk and discussed some of its properties through the analysis of the dispersion relation15. Then, the authors found16 that by properly choosing the measurement basis, the x–y spatial entanglement can be increased with respect to the value obtained with the measurement on the computational basis. They also studied the localizationlike effect in two-dimensional alternate quantum walk with periodic coin operations17. In ref.18 Machida and Chandrashekar presented a three-state alternate quantum walk on a two-dimensional lattice and discussed its localization and limit laws. Recently, Bru et al. considered the two-dimensional alternate quantum walk on a cylinder19. Chen and Zhang revealed the quantum and classical behaviors of the two-dimensional alternate quantum walk in the presence of decoherence20.
Results
CAQW based quantum hash function
At first, we propose CAQW for constructing quantum hash function.
CAQW take place in the product space \({ {\mathcal H} }_{p}\,\otimes \,{ {\mathcal H} }_{c}\). Let |x, y, γ〉 be a basis state, where x, y and γ represent the walker’s position and the coin state respectively.
In every step of the CAQW, the evolution of the whole system can be described by the global unitary operator, denoted by U,
The shift operator S x is defined as
And S y is similar to S x . The coin operator C is a 2 × 2 unitary operator. The general coin operator is defined as
For CAQW, we randomly select two parameters θ 1, θ 2 to construct two coin operators C 0 and C 1. The choice of the coin operator is controlled by a binary string, i.e. message. When the ith bit of the message is 0 (1), the ith step of the quantum walk executes with the coin operator C0(C 1). For example, if the message is 0100, the final state is expressed by
where |ψ 0〉 is the initial state of the total quantum system, \({U}_{0}={S}_{y}( {\mathcal I} \otimes {C}_{0}){S}_{x}( {\mathcal I} \otimes {C}_{0})\), \({U}_{1}={S}_{y}( {\mathcal I} \otimes {C}_{1}){S}_{x}( {\mathcal I} \otimes {C}_{1})\).
Hence the probability of finding the walker at position (x, y) after t steps is
where U(message) is the global unitary operator controlled by the message.
Then, the CAQW based quantum hash function is constructed as follows.
-
1)
Select the parameters (n, k, (θ 1, θ 2), (α, β)). θ 1, θ 2 ∈ (0, π/2) and |α|2 + |β|2 = 1.
-
2)
Run the two-dimensional CAQW under the control of the message. Each direction of the two-dimensional space is a n-length circle. θ 1, θ 2 are the parameters of the two coin operators respectively. The initial state is \(|\mathrm{0,}\,0\rangle (\alpha |0\rangle +\beta |1\rangle )\).
-
3)
Multiply all values in the resulting probability distribution by 108 modulo 2k to form a binary string as the hash value. The bit length of the hash value is n 2 k.
Security of CAQW based quantum hash function
Security of CAQW based quantum hash function is based on the infinite possibilities of the initial state and the irreversibility of measurement and modulo operator.
By using modulo operator, probability distribution is transformed to hash value. This process is irreversible because it is a many-to-one relationship. The probability to transform the hash value back to right probability distribution is approximately 0. It is the first shield to prevent message and initial coin state from unauthorized person.
The second shield of this quantum hash function is the irreversibility of measurement. This is the main reason why the CAQW based quantum Hash function is safe. The final state of CAQW is
This state is a pure state and is linear with the initial state. The probability distribution is
As a result, one can get the probability distribution easily by a quantum computer or a classical computer. However, the probability distribution is the sum of squares of amplitudes which will break the linearity between the final state and the initial state.
If an unauthorized person Eve has plaintext-cipher pairs, he still can not turn the probability distribution into the right linear composition of squares of amplitudes, let alone he doesn’t have the accurate probability distribution. This is because of the infinity of decomposing a number as the sum of squares,
Then, Eve can only suppose the final state is
Therefore, he can not get the right initial state even he knows the right message.
This process protects the initial coin state from any unauthorized person. Together with the infinite possibilities of the initial state, even with a powerful quantum computer, nobody can seek out the initial state by trying all possibilities in theory.
Properties of CAQW based quantum hash function
In this section, we performed several hash tests and theoretical analysis to evaluate the performance of the proposed quantum hash function. We choose n = 5, k = 8, so the hash value we consider here is 200 bits. The result shows that CAQW based quantum hash function have outstanding statistical performance.
Sensitivity of hash value to message
C1, C2, C3 and C4 represent the message, and the messages with tiny modifications respectively. The results listed below show the high sensitivity to the message and the tiny changes.
Condition 1: The original message;
Condition 2: Change the 8th bit from 0 to 1;
Condition 3: Delete the last bit of the message;
Condition 4: Insert a bit in front of the 100th bit.
The corresponding 200-bit hash values in the hexadecimal format are given by:
Condition 1: F4D7DFFE8A6F9269CFF39B665D9D33FFE0912551E598438C35;
Condition 2: 9714B30709B92AC7DBC6909D95F8C5DE85F7907BD5430953E1;
Condition 3: B9CF2BA89451E17A5BC2AFEF7072A7A1AC469A644FB754B773;
Condition 4: D709199C062129047E6C68F4D5DEE1EE4E0307490A92A7CE90.
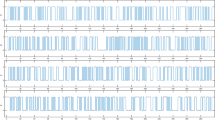
The plots of the hash values are shown respectively in Fig. 1 and it is clearly indicated that any tiny modification to the message will cause a substantial change in the final hash value.
Statistical analysis of diffusion and confusion
The diffusion and confusion tests are performed as follows:
-
(1)
Select a message and generate the corresponding hash value;
-
(2)
Change one bit of the message randomly and generate a new hash value;
-
(3)
Compare the two hash values and count the changed bits called B i ;
-
(4)
Repeat steps (1)–(3) N times.
Given the definitions:
Minimum changed bit number \({B}_{{\min }}=\,{\min }({\{{B}_{i}\}}_{1}^{N})\);
Maximum changed bit number \({B}_{max}=max(\{{B}_{i}{\}}_{1}^{N})\);
Mean changed bit number \(\bar{B}={\sum }_{i\mathrm{=1}}^{N}{B}_{i}/N\);
Mean changed probability \(P=(\bar{B}\mathrm{/200)}\times \mathrm{100 \% }\);
Standard variance of the changed bit number \({\rm{\Delta }}B=\sqrt{\frac{1}{N-1}{\sum }_{i=1}^{N}{({B}_{i}-\bar{B})}^{2}}\);
Standard variance of the changed probability \({\rm{\Delta }}P=\sqrt{\frac{1}{N-1}{\sum }_{i=1}^{N}{({B}_{i}/200-P)}^{2}}\times 100 \% \).
The diffusion and confusion tests are perforemed with N = 1024, 2048, 10000, respectively, as shown in Table 1. We concluded from the tests that the mean changed bit number \(\bar{B}\) and the mean changed probability P are close to the ideal value 100 and 50% respectively. ΔB and ΔP are very little, B min and B max are around 100, so that it demonstrates the stability of diffusion and confusion. The excellent statistical effect ensures that it is impossible to forge plaintext-cipher pairs given known plaintext-cipher pairs.
Collision analysis
It is hard to provide a mathematical proof on the capability of collision resistance of chaotic hash functions. Thus, we performed the following tests for collision resistance:
-
(1)
Select an original message randomly and generate the corresponding hash value in ASCII format.
-
(2)
Change a bit in the message randomly and generate the corresponding hash value in ASCII format.
-
(3)
Compare these two hash values and count the number of ASCII characters with the same value at the same location.
Moreover, the number of ASCII characters with the same value at the same location, i.e. ω, and the theoretical number of ω same values through N independent tests, i.e. W N (ω) can be computed according to the following formulas:
where (x) is the Dirac delta function.
where e i and \({e^{\prime} }_{i}\) are the i th entries of the original and new hash values in ASCII format, respectively. In equation 11, ω = 0, 1, …, n 2. We run this test N = 10,000 times. The experimental values and the of experimental values W N (ω) in the proposed function are shown in Table 2. The experimental values of W N (ω) are similar to the theoretical values.
Uniform distribution on hash space
In order to check the distribution capacity in hash space, we generated two hash values according to the method described in previous subsection and then counted the number of the changed bits at each location. The statistical results for N = 10,000 are shown in Fig. 2. The mean of the changed bit number 4998.2 is very close to the ideal value 5000, which accounts for half of the test times. It can be concluded that the hash value is distributed uniformly in the hash space as all the changed bit numbers are around the ideal value. Obviously, this demonstrates the resistance against statistical attack.
Resistance to birthday attack
Birthday attack implies a lower bound of the length of hash value. The length of the hash value we considered here is 200 = 52 × 8 bits. Therefore, it needs 2n/2 = 2100 ≈ 1.2677 × 1030 trials (n is the size of hash value) to find two messages with identical hash values with a probability of 1/2. Furthermore, CAQW based quantum hash function can be easily extended to be 392 = 72 × 8 bits or more. Therefore, the results of the tests, the size of the hash value, and the collision resistance of the proposed algorithm suggest that the birthday attack is almost impossible and that the proposed algorithm is resistant against this type of attack.
Advantages
Through the analysis above, we find that CAQW based quantum hash function has excellent security and outstanding statistically performance, which is basically same with CIQW based quantum hash function. However, at the same time, CAQW based quantum hash function has some advantages than CIQW based quantum hash function due to the structure of CAQW.
In ref.2 Li et al. considered two interactions: \( {\mathcal I} \)-interaction and π-phase interaction. \( {\mathcal I} \)-interaction and π-phase interaction are in fact a coin operator spanned by two 2 × 2 unitary operators. But CIQW with these two interactions have predictable collisions that quantum walks with same special initial coin state but different messages may have the same probability distribution. In refs3,4 to avoid this kind of collisions, the Grover operator, a swap operator21 and the coin operator E22 are chosen. But it is more hard to implement these 4 × 4 coin operators than a coin operator spanned by two 2 × 2 unitary operators.
CAQW use the 2 × 2 coin operator in Euq. 3 to control the movement of the quantum walker on two directions. By selecting two values as the parameter θ, two coin operators for CAQW can be constructed. Our tests prove that predictable collisions do not happen in CAQW. Furthermore, implementing two 2 × 2 unitary operators significantly reduces the resources necessary for its feasible experimental realization than implementing a coin operator spanned by two 2 × 2 unitary operators, let alone a 4 × 4 coin operator.
Another important advantage of CAQW is that two-dimensional CAQW can be easily extended to higher dimensional CAQW. That means it is easier to construct a hash function with longer hash value. For example, when n = 5, k = 8, the bit length of the Hash value is 1000 = 53 * 8 for three-dimensional CAQW based quantum Hash scheme, while the bit length of the Hash value is 200 = 52 * 8 for two-dimensional CAQW based quantum Hash scheme. Furthermore, for a d-dimensional CAQW based quantum hash function, the size of the state space is n d × 2 while the size of the state space is n d × 2d for a d-dimensional CIQW based quantum hash function2,3,4. It is obviously that implementing a 2d × 2d coin operator is easier and save more resources than implementing d 2 × 2 coin operators.
A comparison about three kinds of quantum walks is shown at Table 3. C 2 and C 4 denote coin operators of size 2 × 2 and 4 × 4 respectively. It is obviously that CAQW is the best of them for building a quantum hash function from the aspect of safety and implementability.
Discussion
In this paper, based on the presentation of controlled alternate quantum walks, we introduce CAQW based quantum hash function. Security of CAQW based quantum hash function is based on the infinite possibilities of the initial state and the irreversibility of measurement and modulo operator. Furthermore, CAQW based quantum hash function has outstanding statistical performance from the aspects of sensitivity, diffusion and confusion, collision, uniform distribution, resistance to birthday attack. More importantly, due to the structure of alternate quantum walks, CAQW based quantum hash function has some advantages than CIQW based quantum hash functions. CAQW based quantum hash function doesn’t have predictable collisions in ref.2. Furthermore, implementing CAQW based quantum hash function significantly reduces the resources necessary for its feasible experimental realization than implementing CIQW based quantum hash functions in refs2,3,4. Also, two-dimensional CAQW based quantum hash function can be easily extended to be higher dimensional CAQW based quantum hash function, which will speed up implementing 200 bits quantum hash function. And controlled quantum walks based quantum hash function can not only be used in quantum computers, but also be used in classical computers. Therefore, CAQW based quantum hash function is eligible for privacy amplification in quantum key distribution, pseudo-random number generation and image encryption4.
References
Bennett, C. H., Brassard, G., Crépeau, C. & Maurer, U. M. Generalized privacy amplification. IEEE Trans. Inf. Theory 41, 1915–1923 (1995).
Li, D., et al. Discrete-time interacting quantum walks and quantum hash schemes. Quant. Inf. Proc. 3, 1501–1513 (2013).
Li, D., Zhang, J., Ma, X. W., Zhang, W. W. & Wen, Q. Y. Analysis of the two-particle controlled interacting quantum walks. Quant. Inf. Proc. 6, 2167–2176 (2013).
Yang, Y. G., Xu, P., Yang, R., Zhou, Y. H. & Shi, W. M. Quantum hash function and its application to privacy amplification in quantum key distribution, pseudo-random number generation and image encryption. Sci. Rep. 6, 19788 (2016).
Elas, S. & Andraca, V. Quantum walks: a comprehensive review. Quant. Inf. Proc. 11, 1015–1106 (2012).
Ambainis, A. Quantum walk algorithm for element distinctness. SIAM J. Comput. 37, 210 (2007).
Shenvi, N., Kempe, J. & Whaley, B. K. Quantum random-walk search algorithm. Phys. Rev. A 67, 052307 (2003).
Berry, S. D. & Wang, J. B. Two-particle quantum walks: Entanglement and graph isomorphism testing. Phys. Rev. A 83, 042317 (2011).
Zhan, X., Qin, H., Bian, Z.-H., Li, H. & Xue, P. Perfect state transfer and efficient quantum routing: A discrete-time quantum-walk approach. Phys. Rev. A 90, 012331 (2014).
Babatunde, A. M., Cresser, J. & Twamley, J. Using a biased quantum random walk as a quantum lumped element router. Phys. Rev. A 90, 012339 (2014).
Kurzynski, P. & Wojcik, A. Quantum walk as a generalized measuring device. Phys. Rev. L 110, 200404 (2013).
Liu, Y., Yuan, J. B., Duan, B. J. & Li, D. Quantum walks on regular uniform hypergraphs. arXiv 1709, 05015 (2017).
Di Franco, C., Mc Gettrick, M. & Busch, Th. Mimicking the Probability Distribution of a Two-Dimensional GroverWalk with a Single-Qubit Coin. Phys. Rev. Lett 106, 080502 (2011).
Di Franco, C., Mc Gettrick, M., Machida, T. & Busch, Th. Alternate two-dimensional quantum walk with a single-qubit coin. Phys. Rev. A 84, 042337 (2011).
Roldan, E., Di Franco, C., Silva, F. & de Valcarcel, G. J. N-dimensional alternate coined quantum walks from a dispersion-relation perspective. Phys. Rev. A 87, 022336 (2013).
Di Franco, C., Mc Gettrick, M., Machida, T. & Busch, Th. Measurement-induced generation of spatial entanglement in a two-dimensional quantum walk with single-qubit coin. Journal of Computational & The oretical Nanoscience 7, 1613 (2013).
Di Franco, C. & Paternostro, M. Localizationlike effect in two-dimensional alternate quantum walks with periodic coin operations. Phys. Rev. A 91, 012328 (2015).
Machida, T. & Chandrashekar, C. M. Localization and limit laws of a three-state alternate quantum walk on a two-dimensional lattice. Phys. Rev. A 92, 062307 (2015).
Bru, L. A. et al. Quantum walks on a cylinder. Phys. Rev. A 94, 032328 (2016).
Chen, T. & Zhang, X. D. Extraordinary behaviors in a two-dimensional decoherent alternative quantum walk. Phys. Rev. A 94, 012316 (2016).
Xue, P. & Sanders, B. C. Two quantum walkers sharing coins. Phys. Rev. A 85, 022307 (2012).
Štefaňák, M., Barnett, S. M., Kollár, B., Kiss, T. & Jex, I. Directional correlations in quantum walks with two particles. New J. Phys. 13, 033029 (2011).
Acknowledgements
This work is supported by NSFC (Grant Nos 61571226, 61572053, 61701229, 61702367), Natural Science Foundation of Jiangsu Province, China (Grant No. BK20140823, BK20170802), the Beijing Natural Science Foundation (Grant No. 4162005), the Fundamental Research Funds for the Central Universities (Grant No. NS2014096), Jiangsu postdoctoral science foundation.
Author information
Authors and Affiliations
Contributions
D. Li initiated the idea. D. Li and J.L. Bi made the numerical simulations. All authors reviewed the manuscript.
Corresponding author
Ethics declarations
Competing Interests
The authors declare that they have no competing interests.
Additional information
Publisher's note: Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Li, D., Yang, YG., Bi, JL. et al. Controlled Alternate Quantum Walks based Quantum Hash Function. Sci Rep 8, 225 (2018). https://doi.org/10.1038/s41598-017-18566-6
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-017-18566-6
This article is cited by
-
Quantum hash function based on controlled alternate lively quantum walks
Scientific Reports (2023)
-
Electronic medical records protection framework based on quantum blockchain for multiple hospitals
Multimedia Tools and Applications (2023)
-
Quantum color image encryption based on controlled two-particle quantum walks
Multimedia Tools and Applications (2023)
-
Controlled alternate quantum walk-based block hash function
Quantum Information Processing (2023)
-
Efficient cancellable multi-biometric recognition system based on deep learning and bio-hashing
Applied Intelligence (2023)
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.