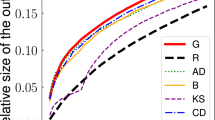
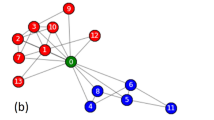
Abstract
The Internet and social media have fuelled enormous interest in social network analysis. New tools continue to be developed and used to analyse our personal connections, with particular emphasis on detecting communities or identifying key individuals in a social network. This raises privacy concerns that are likely to exacerbate in the future. With this in mind, we ask the question ‘Can individuals or groups actively manage their connections to evade social network analysis tools?’ By addressing this question, the general public may better protect their privacy, oppressed activist groups may better conceal their existence and security agencies may better understand how terrorists escape detection. We first study how an individual can evade ‘node centrality’ analysis while minimizing the negative impact that this may have on his or her influence. We prove that an optimal solution to this problem is difficult to compute. Despite this hardness, we demonstrate how even a simple heuristic, whereby attention is restricted to the individual’s immediate neighbourhood, can be surprisingly effective in practice; for example, it could easily disguise Mohamed Atta’s leading position within the World Trade Center terrorist network. We also study how a community can increase the likelihood of being overlooked by community-detection algorithms. We propose a measure of concealment—expressing how well a community is hidden—and use it to demonstrate the effectiveness of a simple heuristic, whereby members of the community either ‘unfriend’ certain other members or ‘befriend’ some non-members in a coordinated effort to camouflage their community.
This is a preview of subscription content, access via your institution
Access options
Access Nature and 54 other Nature Portfolio journals
Get Nature+, our best-value online-access subscription
$29.99 / 30 days
cancel any time
Subscribe to this journal
Receive 12 digital issues and online access to articles
$119.00 per year
only $9.92 per issue
Buy this article
- Purchase on Springer Link
- Instant access to full article PDF
Prices may be subject to local taxes which are calculated during checkout






Similar content being viewed by others
References
Mayer-Schnberger, V. & Cukier, K. Big Data: A Revolution That Will Transform How We Live, Work and Think (John Murray Publishers, London, 2013).
Moreno, J. L. Application of the Group Method to Classification (National Committee on Prisons and Prison Labor, New York, NY, 1932).
Granovetter, M. S. The strength of weak ties. Am. J. Sociol. 78, 1360–1380 (1973).
Freeman, L. C. The Development of Social Network Analysis. A Study in the Sociology of Science (Empirical Press, Vancouver, 2004).
Easley, D. & Kleinberg, J. Networks, Crowds, and Markets: Reasoning About a Highly Connected World (Cambridge Univ. Press, Cambridge, 2010).
Gross, R. & Acquisti, A. Information revelation and privacy in online social networks. In Proc. 2005 ACM Workshop on Privacy in the Electronic Society 71–80 (ACM, 2005).
Zhang, C., Sun, J., Zhu, X. & Fang, Y. Privacy and security for online social networks: challenges and opportunities. IEEE Netw. 24, 13–18 (2010).
Deliri, S. & Massimiliano, A. in Data Management in Pervasive Systems (eds Altshuler, Y., Elovici, Y., Cremers, A. B., Aharony, N. & Pentland, A.) 195–209 (Springer, New York, NY, 2013).
Wu, X., Ying, X., Liu, K. & Chen, L. in Managing and Mining Graph Data (eds Aggarwal, C. C. & Wang, H.) 421–453 (Springer, New York, NY, 2010).
Mislove, A., Viswanath, B., Gummadi, K. P. & Druschel, P. You are who you know: inferring user profiles in online social networks. In Proc. 3rd ACM Int. Conf. on Web Search and Data Mining 251–260 (ACM, New York, NY, 2010).
Zhou, B., Pei, J. & Luk, W. S. A brief survey on anonymization techniques for privacy preserving publishing of social network data. SIGKDD Explor. 10, 12–22 (2008).
Kearns, M., Roth, A., Wu, Z. W. & Yaroslavtsev, G. Private algorithms for the protected in social network search. Proc. Natl. Acad. Sci. USA 113, 913–918 (2016).
Lane, J. I., Stodden, V., Bender, S. & Nissenbaum, H. Privacy, Big Data, and the Public Good: Frameworks for Engagement (Cambridge Univ. Press, Cambridge, 2014).
King, G., Pan, J. & Roberts, M. E. How censorship in china allows government criticism but silences collective expression. Am. Polit. Sci. Rev. 107, 326–343 (2013).
King, G.., Pan, J.. & Roberts, M. E.. Reverse-engineering censorship in china: randomized experimentation and participant observation. Science 345, 1251722 (2014).
Nordrum, A. Pro-ISIS online groups use social media survival strategies to evade authorities. IEEE Spectrum https://spectrum.ieee.org/tech-talk/telecom/internet/proisis-online-groups-use-social-media-survival-strategies-to-evade-authorities (2016).
Johnson, N. F. et al. New online ecology of adversarial aggregates: ISIS and beyond. Science 352, 1459–1463 (2016).
Carley, K. M., Lee, J.-S. & Krackhardt, D. Destabilizing networks. Connections 24, 31–34 (2001).
Carley, K. M., Reminga, J. & Kamneva, N. Destabilizing terrorist networks. In NAACSOS Conference Proceedings (NAACSOS, Pittsburgh, PA, 2003).
McCulloh, I. & Carley, K. M. Detecting Change in Longitudinal Social Networks Technical Report (Defense Technical Information Center, 2011).
Cutillo, L. A., Molva, R. & Strufe, T. Safebook: a privacy-preserving online social network leveraging on real-life trust. IEEE Commun. Mag. 47, 94–101 (2009).
Baden, R., Bender, A., Spring, N., Bhattacharjee, B. & Starin, D. Persona: an online social network with user-defined privacy.Comput. Commun. Rev. 39, 135–146 (2009).
Li, J. Privacy policies for health social networking sites. J. Am. Med. Inform. Assoc. 20, 704–707 (2013).
Li, J. A privacy preservation model for health-related social networking sites. J. Med. Internet Res. 17, e168 (2015).
Narayanan, A. & Shmatikov, V. De-anonymizing social networks. In Proc. 2009 30th IEEE Symposiumo n Security and Privacy 173–187 (IEEE Computer Society, Washington DC, 2009).
Crossley, N., Edwards, G., Harries, E. & Stevenson, R. Covert social movement networks and the secrecy–efficiency trade off: the case of the UK suffragettes (1906–1914). Social. Netw. 34, 634–644 (2012).
Stevenson, R. & Crossley, N. Change in covert social movement networks: the “inner circle” of the provisional Irish republican army. Social. Mov. Stud. 13, 70–91 (2014).
Correa, C. D., Crnovrsanin, T. & Ma, K.-L. Visual reasoning about social networks using centrality sensitivity. IEEE Trans. Vis. Comput. Graph. 18, 106–120 (2012).
Orman, G. K. & Labatut, V. in Discovery Science (eds Gama, J., Costa, V. S., Jorge, A. M. & Brazdil, P. B.) 242–256 (Springer, New York, NY, 2009).
Freeman, L. C. Centrality in social networks conceptual clarification. Social. Netw. 1, 215–239 (1979).
Goldenberg, J., Libai, B. & Muller, E. Using complex systems analysis to advance marketing theory development: modeling heterogeneity effects on new product growth through stochastic cellular automata. Acad. Mark. Sci. Rev. 9, 1–18 (2001).
Kempe, D., Kleinberg, J. & Tardos, É. Maximizing the spread of influence through a social network. In Proc. 9th ACM SIGKDD Int. Conf. on Knowledge Discovery and Data Mining 137–146 (ACM, New York, NY, 2003).
Blondel, V. D., Guillaume, J.-L., Lambiotte, R. & Lefebvre, E. Fast unfolding of communities in large networks. J. Stat. Mech. 2008, P10008 (2008).
Newman, M. E. J. Finding community structure in networks using the eigenvectors of matrices. Phys. Rev. E 74, 036104 (2006).
Newman, M. E. J. & Girvan, M. Finding and evaluating community structure in networks. Phys. Rev. E 69, 026113 (2004).
Pons, P. & Latapy, M. in Computer and Information Sciences—ISCIS 2005 (eds Yolum, P., Güngör, T., Gürgen, F. & Özturan, C.) 284–293 (Springer, 2005).
Clauset, A., Newman, M. E. J. & Moore, C. Finding community structure in very large networks. Phys. Rev. E 70, 066111 (2004).
Rosvall, M., Axelsson, D. & Bergstrom, C. T. The map equation. Eur. Phys. J. Spec. Top. 178, 13–23 (2010).
Reichardt, J. & Bornholdt, S. Statistical mechanics of community detection. Phys. Rev. E 74, 016110 (2006).
Krebs, V. E. Mapping networks of terrorist cells. Connections 24, 43–52 (2002).
Borgatti, S. P., Everett, M. G. & Freeman, L. C. Ucinet for windows: software for social network analysis. Connections 15, 12–15 (2002).
Nagle, F. & Singh, L. Can friends be trusted? Exploring privacy in online social networks. In Proc. Int. Conf. on Advances in Social Network Analysis and Mining 312–315 (IEEE, 2009).
Chandola, V., Banerjee, A. & Kumar, V. Anomaly detection: a survey. ACM Comput. Surv. 41, 15 (2009).
Ahn, J., Plaisant, C. & Shneiderman, B. A task taxonomy for network evolution analysis. IEEE Trans. Vis. Comput. Graph. 20, 365–376 (2014).
Lerman, K., Ghosh, R. & Kang, J. H. Centrality metric for dynamic networks. In Proc. 8th Workshop on Mining and Learning with Graphs 70–77 (ACM, 2010).
Federico, P., Pfeffer, J., Aigner, W., Miksch, S. & Zenk, L. Visual analysis of dynamic networks using change centrality. In 2012 IEEE/ACM Int. Conf. on Advances in Social Networks Analysis and Mining 179–183 (IEEE, 2012).
Lü, L. & Zhou, T. Link prediction in complex networks: a survey.Phys. A Stat. Mech. Appl. 6, 1150–1170 (2011).
Michalak, T., Rahwan, T., Skibski, O. & Wooldridge, M. Defeating terrorist networks with game theory. IEEE Intell. Syst. 30, 53–61 2015).
Xie, J., Kelley, S. & Szymanski, B. K. Overlapping community detection in networks: the state-of-the-art and comparative study. ACM Comput. Surv. 45, 43 (2013).
Shaw, M. E. Group structure and the behavior of individuals in small groups. J. Psychol. 38, 139–149 (1954).
Murray, A. Beauchamp. An improved index of centrality. Behav. Sci. 10, 161–163 (1965).
Anthonisse, J. M. The Rush in a Directed Graph (Univ. Amsterdam Mathematical Centre, Amsterdam, 1971).
Freeman, L. C. A set of measures of centrality based on betweenness. Sociometry 40, 35–41 1977).
Bonacich, P. Power and centrality: a family of measures. Am. J. Sociol. 92, 1170–1182 (1987).
Hayes, B. Connecting the dots: can the tools of graph theory and social-network studies unravel the next big plot? Am. Sci. 94, 400–404 (2006).
Leskovec, J. & Mcauley, J. J. Learning to discover social circles in ego networks. In Proc. 25th Int. Conf. on Neural Information Processing Systems 539–547 (Curran Associates, 2012).
Barabási, A.-L. & Albert, R. Emergence of scaling in random networks. Science 286, 509–512 (1999).
Watts, D. J. & Strogatz, S. H. Collective dynamics of small-world networks. Nature 393, 440–442 (1998).
Erdös, P. & Rényi, A. On random graphs I. Publ. Math. Debr. 6, 290–297 (1959).
Acknowledgements
M.W. was supported by the Polish National Science Centre (grant 2015/17/N/ST6/03686). M.J.W. was supported by the European Research Council under Advanced Grant 291528 (‘RACE’). T.P.M. was supported by the Polish National Science Centre (grant 2014/13/B/ST6/01807) and, for the earlier versions of this article, also by the European Research Council under Advanced Grant 291528 (‘RACE’). No funders had any role in study design, data collection and analysis, decision to publish or preparation of the manuscript.
Author information
Authors and Affiliations
Contributions
T.P.M., M.J.W. and T.R. conceived the study and designed the experiments. M.W. and T.P.M. formalized the computational problems. M.W. and T.R. developed the heuristics. M.W. developed the proofs and performed the numerical simulations. All authors discussed the results and wrote the manuscript.
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note: Springer Nature remains neutral with regard to jurisdictional claims inpublished maps and institutional affiliations.
Supplementary information
Supplementary Information
Supplementary Notes, Supplementary Figures 1–92, Supplementary References 1–33
Rights and permissions
About this article
Cite this article
Waniek, M., Michalak, T.P., Wooldridge, M.J. et al. Hiding individuals and communities in a social network. Nat Hum Behav 2, 139–147 (2018). https://doi.org/10.1038/s41562-017-0290-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1038/s41562-017-0290-3
This article is cited by
-
Human intuition as a defense against attribute inference
Scientific Reports (2023)
-
Community deception in directed influence networks
Social Network Analysis and Mining (2023)
-
State of the art on adversarial attacks and defenses in graphs
Neural Computing and Applications (2023)
-
Recent Progress of Bio-inspired Camouflage Materials: From Visible to Infrared Range
Chemical Research in Chinese Universities (2023)
-
Community deception: from undirected to directed networks
Social Network Analysis and Mining (2022)