Abstract
The decoy-state method substantially improves the performance of quantum key distribution (QKD) and perfectly solves crucial issues caused by multiphoton pulses. In recent years, the decoy-state method has occupied a key position in practicality, and almost all the QKD systems have employed the decoy-state method. However, the imperfections of traditional intensity modulators limit the performance of the decoy-state method and bring side channels. In this work, a special intensity modulator and its accompanying modulation method are designed and experimentally verified for the secure, stable, and high-performance decoy-state QKDs. The experimental result indicates that its stable and adjustable intensities, convenient two-level modulation, inherently high speed, and compact structure is extremely fit for future trends and will help the decoy-state method to be perfectly applied to QKD systems.
Similar content being viewed by others
Introduction
Quantum key distribution (QKD)1 provides a way for two legitimate remote users, namely, Alice and Bob, to share secret keys with information-theoretic security2,3,4,5,6. However, this security relies on the single-photon state while the ideal single-photon sources are not yet practically useful. As an alternative, a revolutionary method named the decoy-state method7,8,9 is employed in almost all practical QKD systems. This method allows a practical system based on weak coherent pulse sources to achieve the security performance of a single-photon QKD, which is a perfect combination of theory and practice.
The decoy-state method significantly improves the secret key rate and achievable distance of practical systems, but the legitimate users have to modulate several different intensities10,11,12,13,14,15,16,17,18,19,20,21,22,23,24 precisely and independently. Usually, a decoy-state QKD requires weak coherent pulses with three or more different intensities. Some systems also require a special decoy state named vacuum state. Compared with classic optical communications, the intensity modulation in QKD systems is more difficult since the conflict between completely random modulation and finite modulation bandwidth.
A good intensity modulation for decoy-state QKD should be secure, stable, and flexible. The ‘secure’ is a basic requirement that the modulation should not violate the security assumptions of the QKD. The ‘stable’ means the output intensities should be insensitive to disturbances in an electric signal. The ‘flexible’ is that the manipulation should be as simple as possible. Meanwhile, it is important for a good intensity modulation that it should not be a short slab of the system performance. However, existing modulators cannot meet all the above requirements at the same time. The most widely used commercial LiNbO3-based Mach–Zehnder interferometer (MZI) is extremely sensitive to the electric signal disturbance, which violates the condition of ‘stable’, brings intensity fluctuation, and reduces the secret key rate22,25,26,27,28. To make the matter worse, a special intensity fluctuation named patterning effect29 introduces correlation of adjacent signals, which provides additional information and allows Eve to perform sophisticated attacks since current security analysis usually assumes independent and identically distributed (i. i. d) pulses. The imperfection of the MZI modulator has shaken the basis of the QKD.
To fill the loophole in the intensity modulation, two countermeasures are proposed. The first one is a post-processing method29. It works by discarding some pulses depending on the state of predecessor and successor. Another countermeasure is an intensity modulator based on Sagnac interferometer30. It is used as a secure two-level intensity modulator for QKD, not only can mitigate the patterning effect but also is immune to the DC drift. The two countermeasures are secure and convenient but not so friendly to high-performance QKDs. The post-processing method ineluctably reduces the secret key rate since it discards too many key bits while the higher key rate is what people pursue in the QKD field. The Sagnac modulator is also not so suitable for the decoy-state method since its two-level intensity modulation and fixed stable intensities cannot meet the requirement of more than two adjustable intensities. Besides, the worst of it is that its common-path mechanism brings an inherent speed limit. Considering that the high-speed system is a trend of the QKD field, the Sagnac modulator may become a short slab in QKD systems in the future.
An interesting question is whether we can design an intensity modulator that can generate three, four, or even more stable intensities, and these stable intensities should be tunable to optimize intensities for improving the secret key rate21,31,32,33. Beyond that, it is lacing on the cake if its driving-voltages only switch between two different voltages, which would significantly reduce the modulation difficulty. Fortunately, the answer is yes. In this work, an intensity modulator named multipath Mach-Zehnder interferometer (MMZI) and its accompanying modulation method that meets all the above requirements are proposed. By working only at the ‘half-wave points’, the MMZI can generate a variety of different stable intensities to mitigate the intensity fluctuation and the patterning effect for secure and robust QKD systems. The MMZI is also inherently high-speed and facility for integration due to the traveling-wave modulation and its compact structure.
Results
Most QKD systems generate the decoy states by commercial LiNbO3-based MZIs, in which an input pulse is first split into two parts by a 1 × 2 splitter and then recombined by a 2 × 1 coupler. The splitting ratios of the splitter and the coupler of commercial MZIs are both \(\frac{1}{2}\). Thus, the output intensity I(α) is
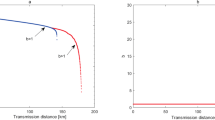
where the α is the phase difference of the two paths and the μin is the input intensity. In many decoy-state QKD systems, commercial MZIs are applied to produce a signal state μs, a decoy state μd and a vacuum state μv = 020,23,34. As illustrated in Fig. 1, the signal state corresponds to the flat peak point S and the decoy state corresponds to the slope point D. We define the points with 0 derivative as stable points. Here the point S is a stable point. It is obvious that comparing with the stable points, the slope points are more sensitive to disturbances such as timing jitter and electric waveform distortion, which would cause unforeseeable fluctuation on μd. Especially, in high-speed systems35,36,37, a finite modulation bandwidth leads to a correlation between adjacent signals, namely, the intensity of a pulse would be correlated with its previous one, which violates the important i.i.d. assumption.
To make QKD systems more secure and robust, we present a MMZI and an accompanying modulation method, which can be perfectly applied to decoy-state QKD systems. By working at the half-wave voltage, the interferometer can generate several stable intensities to mitigate the intensity fluctuation and the patterning effect for the security. As illustrated in Fig. 2, the interferometer consists of an 1 × N splitter, a N × 1 coupler and N parallel paths. One of the path (path-0) includes a variable optical attenuator (VOA) to tune its attenuation ratio η and others paths (path-1 to N − 1) each has a built-in phase modulator to shift the relative phases αk for k ∈ {1, 2....N − 1}. An input coherent pulse with intensity μin is first split by the 1 × N splitter whose splitting ratio to the path-k is denoted by \({t}_{k}^{\prime}\) and then modulated in each path. After that, the pulses in each path couple and interfere in the N × 1 coupler whose splitting ratio to the path-k is denoted by \({t}_{k}^{^{\prime\prime} }\). To make the following formulas clearer, we define \({t}_{k}=\sqrt{{t}_{k}^{\prime}{t}_{k}^{^{\prime\prime} }}\).
In this modulator, input pulses are split by an 1 × N splitter and enter into N different paths. The path-0 has a VOA to attenuate the pulse and the path-1 to N − 1 each has a phase modulator to modulate the relative phases. Finally, the split pulses interfere in a N × 1 coupler. P path; BS beam splitter; PM phase modulator; VOA variable optical attenuator.
Note that since QKD systems have an attenuator to attenuate the intensity to single-photon level34,35,36,38,39,40,41,42,43,44,45,46,47, we ignore the insertion loss in the follows. The output pulse of the path-0 and path-k for k ∈ {1, 2, ...., N − 1} are, respectively, \(\left|\sqrt{\eta }{t}_{0}\sqrt{{\mu }_{\rm{in}}}\right\rangle\) and \(\left|{t}_{k}{e}^{i{\alpha }_{k}}\sqrt{{\mu }_{\rm{in}}}\right\rangle\). After the interference, the MMZI outputs:
The output intensity can be regarded as a function of relative phases:
Since the condition of a stationary point is that all its partial derivatives should be 0, namely, the
the ∀αk ∈ {0, π} are general solutions of Eq. (4). For simplicity, we define these general solutions as the ‘half-wave points’ in the follows. In another word, when the voltages on each path is V0 or Vπ, the output intensity would be stable. Since each αk can be tuned to be 0 or π, there are 2N−1 stable intensities, which can be denoted by \({I}_{1},{I}_{2},....,{I}_{{2}^{N-1}}\).
For a specific decoy-state QKD system that requires optimized intensities μ1, μ2, ...., μn, without loss of generality, we assume that the {I1, I2, ...., In} and {μ1, μ2, ...., μn} are sorted in descending order. A user should firstly find a set of tk and a η according to Eqs. (2) and (3) to make
After that, the user adjusts the attenuator in the QKD system to make the maximum intensity I1, which always corresponds to the point ∀αk = 0, equals to the μ1. Naturally the other stable intensities equal to the other optimized decoy states. We take the optimized intensity sets [\({\mu }_{s}=0.015,\,{\mu }_{{d}_{1}}=0.006,\,{\mu }_{{d}_{2}}=0.002,\,{\mu }_{v}=0\)] and [\({\mu }_{s}=0.43,\,{\mu }_{{d}_{1}}=0.19,\,{\mu }_{{d}_{2}}=0.05,\,{\mu }_{v}=0\)] in the recent twin-field QKD experiments45,46 as examples. We employ a three-path MMZI and denote its four stable intensities as I(0, 0), I(0, π), I(π, 0) and I(π, π), respectively. To generate the first optimized intensity set, an user should firstly set the splitting ratios and fine-tune the VOA to [\(\sqrt{\eta }{t}_{0}=0.5\), t1 = 0.3170, t2 = 0.1830] to make the I(0, π)/I(0, 0) = 0.4019, I(π, 0)/I(0, 0) = 0.1122 and I(π, π) = 0. After that, he (she) adjust the attenuator in the QKD system to make I(0, 0) = μs = 0.015, then naturally, the \(I(0,\pi )={\mu }_{{d}_{1}}=0.006\), \(I(\pi ,0)={\mu }_{{d}_{2}}=0.002\), and I(π, π) = μv = 0. Similarly, to generate the second optimized intensity set, an user can set the tk and η to [\(\sqrt{\eta }{t}_{0}=0.5\), t1 = 0.3305, t2 = 0.1695] and adjust the attenuator in the QKD system to make \(I(0,\pi )={\mu }_{{d}_{1}}=0.43\). Then the \(I(0,\pi )={\mu }_{{d}_{1}}=0.19\), \(I(\pi ,0)={\mu }_{{d}_{2}}=0.05\)and I(π, π) = μv = 0.
It is worth noting that, the stable intensities are adjusted by setting the splitting ratios and tuning the VOA. The MMZI would only has a limited tuning range when the splitting ratios are fixed. A more flexible structure with a larger tuning range can be achieved by adding VOA in each path. The details are introduced in the Discussion.
Discussion
The stable intensities of the MMZI can be fine-tuned by the built-in VOA so that users can optimize the secret key rate. However, the tuning range is limited. In this section, another structure for improving the tuning range is proposed., As illustrated in Fig. 3, each path owns a VOA. The attenuation ratio of the path-k is denoted by ηk for k ∈ {0, 1, 2, ...., N − 1}. By adjusting these ηk, the ratio of the stable intensities can be modified flexibly to meet the need for intensity optimization.
In order to simplify the problem, we assume that the splitter has a balanced splitting ratio, namely, tk = 1/N for k ∈ {0, 1, 2, ...., N − 1}. The output state of the path-0 and the path-k (k ∈ {1, 2, ...., N − 1}) are denoted by \(\left|\frac{1}{N}\sqrt{{\eta }_{0}{\mu }_{\rm{in}}}\right\rangle\) and \(|\frac{{e}^{i{\alpha }_{k}}}{N}\sqrt{{\eta }_{k}{\mu }_{\rm{in}}}\rangle\) respectively. the output state of the interferometer is:
The output intensity is:
The outputs of the stable points mainly depend on ηk for k ∈ {0, 1, 2, ...., N − 1}, namely, they can be modified flexibly by adjusting the built-in VOAs.
The partial derivative equations of Eq. (7) is expressed as:
Significantly, the general solution is also ∀αk ∈ {0, π} for k ∈ {1, 2, ...., N − 1}.
With the development of high-speed QKD systems, the widely used commercial LiNbO3 MZIs are increasingly difficult to meet the need for security, robustness, and flexibility. To improve the performance of the decoy-state QKD and make it more practical, a MMZI and its accompanying modulation method are proposed in this work. Our method can generate 2N−1 different stable intensities to mitigate the intensity fluctuation and the patterning effect from imperfect modulation signals. The flexibility of its ‘half-wave modulation’ and tunable outputs makes it suitable for different protocols and systems. Its compact structure makes it easy to integrate. Besides, it is inherently high-speed due to the traveling-wave modulation. A user may generate stable decoy states by cascading several MZIs. However, in this scheme, the splitting ratio of each MZI must be specially designed. Considering that almost all commercial MZIs have a symmetric splitting ratio, each MZI in the series must be customized, which would increase difficulty and cost. Even if the customized MZIs are employed, the stable intensities of the cascade MZI design are fixed when connecting N MZIs in series, the user can generate at most 2N stable intensities. By contrast, the user can build 2N-path MMZI by connecting N MZIs in parallel, in another word, he (she) can generate at most 22N−1 stable intensities, which is much more than connecting in series. Compared with cascading several customized MZIs, a 3-path MMZI (DPMZI or connecting two commercial MZI in parallel) can generate 4 stable intensities and the intensities are tunable, which is much more flexible and convenient in practical applications.
We have also experimentally demonstrated the modulation method by an commercial dual-parallel MZI (DPMZI) which could be regarded as a special case of the MMZI. We measured a random sequence consisting of signal, decoy, and vacuum state. The result suggests that our method can effectively mitigate the influence of the patterning effect. We have also demonstrated adjusting the ratio \({\mathcal{R}}\) to verify its convenience for intensity optimization. The details could be found in METHODS. The result indicates that our interferometer and modulation method are feasible in practice and will be secure, robust, and flexible for decoy-state QKD systems. Since its compact structure is easy to integrate, we believe that an integrated MMZI can be perfectly applied in high-speed decoy-state QKD systems and help the practical QKDs to achieve the optimized performance.
Methods
Experimental demonstration
In this section, we demonstrate the MMZI and its accompanying modulation method by a commonly used three-intensity decoy-state method17,22,48,49 which consists of a signal state, a decoy state, and a vacuum state. An integrated commercial modulator named DPMZI50,51,52, which can be regarded as a special case of our MMZI is employed in the demonstration. As illustrated in Fig. 4, a DPMZI consists of two parallel sub-MZIs, one of which can be regarded as a VOA and the other one can be regarded as two independent paths. For simplicity, we use VOA to refer to the first sub-MZI. In other words, the DPMZI can be regarded as an equivalent of our modulator with three paths. Since all beam splitters in DPMZI have a 50:50 ratio, the splitting ratio t0, t1, and t2 are fixed to, respectively, 0.5, 0.25 and 0.25. The output of DPMZI is written as:
The output intensity is a function of α1 and α2, which is written as:
As discussed above, the half-wave points are stable. The I(0, 0) is the maximum intensity, which is regarded as the signal state μs. The other half-wave points can be employed as decoy states, here we select the I(0, π) as the decoy state μd. Since the splitting ratios of the integrated commercial DPMZI have been fixed (namely, we cannot adjust splitting ratios to make the vacuum state on a half-wave point), we employ a particular solution, which is the solution of the equation set
as the vacuum state. Experimentally, we can obtain the vacuum point by scanning the driving-voltage of path-1 and 2 alternately and taking the voltage which minimizes the output intensity in each turn.
As illustrated in Fig. 5. The point S (α1 = 0, α2 = 0) is a peak point which corresponds to the signal state μs; The point D (α1 = 0, α2 = π) is a saddle point that is selected to generate the decoy state μd. The point V is a trough point which corresponds to the vacuum state. Now that the tk are fixed, the stable intensities are \(I(0,0)=\frac{{\mu }_{\rm{in}}}{4}{(1+\sqrt{\eta })}^{2}\) and \(I(0,\pi )=\frac{{\mu }_{\rm{in}}}{4}\eta\), which are functions of the η. Defining that \({\mathcal{R}}={\mu }_{d}/{\mu }_{s}\), the user can adjust the VOA to \(\eta ={(\frac{\sqrt{{\mathcal{R}}}}{1-\sqrt{{\mathcal{R}}}})}^{2}\) to make \(I(0,\pi )/I(0,0)={\mathcal{R}}\).
In our experimental demonstration, a series of 50 ps light pulses generated from a 1 GHz high-speed picosecond laser were fed to a DPMZI (produced by FUJITSU OPTICAL COMPONENTS LIMITED and the model is FTM7960EX). A 5 GS/s-sampling-rate arbitrary waveform generator with two RF-amplifiers was applied to drive the interferometer. A pseudo-random number sequence was employed to the arbitrary waveform generator to generate random encoding signals. Complementary encoding signals similar to ref. 29 were employed to meet the need of the RF-amplifiers. On the detection side, the modulated pulses were detected by a 20-GHz-bandwidth high-speed photodiode and recorded by a 12.5-GHz-bandwidth oscilloscope. Since it is assumed that the average intensity reflects the mean photon number in the quantum pulses through heavy attenuation linearly29, we measured the intensities before they are attenuated to single-photon magnitude and calculated the intensity by the area of the pulse traced by the oscilloscope.
To demonstrate the ability to mitigate the patterning effect, a random sequence consisting of signal, decoy, and vacuum state was measured and 20,000 pulses were collected for statistical analysis. A short subset of the tracing result was shown in Fig. 6. To show the flexibility of tuning the ratio of signal and decoy state, we measured the average intensities of different patterns with different η. We adjusted the η to make the \({\mathcal{R}}={\mu }_{d}/{\mu }_{s}=0.24\), 0.21, 0.18, and 0.12 as the interval of 0.1–0.25 is widely used in decoy-state QKDs18,43,53 and recorded the average intensities of different patterns in Table 1. After that, we did a control experiment in which all the devices were the same as the previous one except for the modulator was replaced by a commercial LiNbO3 MZI. In the control experiment, we also prepared random sequences consisting of the three states, and we adjusted the voltage to tune the \({\mathcal{R}}\) to do a comparison with the DPMZI. The comparison is listed in Table 2. The results indicate that under the same condition, the patterning effect in our method is two or three orders of magnitude smaller than the traditional intensity modulator. Employing our modulator is the inevitable demand for higher performance since in practical systems.
The upper surface plot illustrates and the two contour plots denote the two partial derivatives. The upper color bar belongs to the surface plot and the lower color bar belongs to the two contour plots. The ‘S’, ‘D’, and ‘V’ points are employed as the signal state, decoy state, and vacuum state respectively and the partial derivatives of the three points are all 0.
Simulation
Except for the patterning effect, the random intensity fluctuation due to thermal noise or timing jitter of modulation signal also brings side-channels to practical systems. As discussed in previous works22,26,27,54, considering the worst case in the parameter estimation is a countermeasure for the loophole, but the system performance would be unavoidably reduced and the performance depends on the magnitude of the fluctuation. The MMZI can mitigate the random intensity fluctuation from the modulation signal so that the system performance could be improved. Here we demonstrate the MMZI by extending the intensity fluctuation to ref. 13, which is a three-intensity BB84 protocol with a finite-key analysis. (We emphasize that we only analyze the random intensity fluctuation in the simulation since the quantitative theoretical analysis against the correlated intensity fluctuation is still missing at present.).
The protocol definition is same with ref. 13, except that the worst case of the mean photon number in the range of \([{\mu }_{a}^{L},{\mu }_{a}^{U}]\) (a ∈ {s,d, v}) is considered in the parameter estimation. The secret key is extracted from the events whereby Alice and Bob both choose the X basis. The intensities are denoted by μs, μd and μv, respectively, and they satisfy μs > μd + μv and μd > μv≥0. The intensities are selected with probabilties \({p}_{{\mu }_{s}}\), \({p}_{{\mu }_{d}}\) and \({p}_{{\mu }_{v}}\), respectively. In the scenario that the random intensity fluctuation and finite-key effect are considered, the parameters estimation of decoy state method should be modified. The lower-bound on the number of vacuum events sb,0 in basis b (b ∈ {X, Z}) is estimated by:
where nb,a denotes the event number when Alice select basis b and intensity μa, the \({\tau }_{0}({\mu }_{s},{\mu }_{d},{\mu }_{v})={e}^{-{\mu }_{s}}{p}_{{\mu }_{s}}+{e}^{-{\mu }_{d}}{p}_{{\mu }_{d}}+{e}^{-{\mu }_{v}}{p}_{{\mu }_{v}}\) is the probability that Alice sends a 0-photon state and the
is an intermediate variable corresponding to the Hoeffding’s inequality.
In addition, the lower-bound on the number of single-photon events sb,1 in basis b (b ∈ {X, Z}) is estimated by:
where the \({\tau }_{1}({\mu }_{s},{\mu }_{d},{\mu }_{v})={e}^{-{\mu }_{s}}{\mu }_{s}{p}_{{\mu }_{s}}+{e}^{-{\mu }_{d}}{\mu }_{d}{p}_{{\mu }_{d}}+{e}^{-{\mu }_{v}}{\mu }_{v}{p}_{{\mu }_{v}}\) is the probability that Alice sends a single-photon state.
After that, the upper-bound of the number of bit errors associated with the single-photon events in Z-basis νZ,1 is modified as:
where the \({m}_{Z}^{a}\) denotes the number of bit errors when Alice selects Z-basis and intensity μa.
With the modified formulas of the three-intensity decoy-state method, we can estimate a secret key rate when the random intensity fluctuation exists. Here simulate the BB84 protocol with random intensity fluctuation, and compare the system performance between employing commercial MZI and MMZI. The protocol definition and the formulas are same with ref. 13 except for the formulas of the decoy-state method are replaced by Eqs. (11), (13), and (14), in which the intensity fluctuation \([{\mu }_{a}^{L},{\mu }_{a}^{U}]\) is considered. The difference between employing commercial MZI and the DPMZI is that the fluctuation is different. Since the electronic noise, when Alice wants to a voltage corresponding to the relative phase α, she actually loads a random voltage in a range which corresponds to the relative phase in the range of \(\left[{\alpha }^{L},{\alpha }^{U}\right]\). When a commercial MZI is employed, the intensity fluctuation is
where a ∈ {s, d, v} and the αa denotes the corresponding relative phase for intensity \({\mu ^{\prime} }_{a}\). Similarly, when the MMZI (we take the DPMZI as an example) is employed, the intensity fluctuation is
where the α1,a and α2,a are corresponding relative phases for intensity μa and the η should be tuned to be 0.6545 to make μd = 0.2μs. We further assume that the source has a fluctuation of δI, the output μa is in the range of \(\left[{\mu }_{a}^{L},{\mu }_{a}^{U}\right]\), where
where the 10−3 is the extinction ratio of the modulator.
Here, we compare the difference of intensity fluctuation and secret key rate between employing commercial MZI and MMZI. In our simulation, the detection efficiency is 10%, the dark count rate is 6 × 10−7, the after-pulse probability is 4 × 10−2, the misalignment error rate is 5 × 10−3, and the fluctuation of the laser source δI = 1%. The security parameters for finite-key effect are all same with ref. 13 and the block size nX is fixed to 107. The probabilities \({p}_{{\mu }_{s}}=0.7\), \({p}_{{\mu }_{d}}=0.2\), and \({p}_{{\mu }_{v}}=0.1\). The probability of selecting X basis is 0.61. We fix the intensities to μs = 0.44, μd = 0.2μs = 0.088, μv = 10−3μs. The intensity fluctuations are listed in Table 3 and the secret key rates are showed in Fig. 7. The simulation results indicate that the MMZI mitigates the random intensity fluctuation and significantly improves the system performance. When the phase deviation is π/20, the system with DPMZI is nearly ideal while the system with MZI is nearly broken.
The black-dot line denotes the ideal key rate without any intensity fluctuation. The red, yellow, and blue lines denote the maximum phase deviation δα is π/40, π/30, and π/20, respectively. The modulated phase is in the range of [α − δα, α + δα]. The solid line and dash line denote employing MMZI and MZI, respectively.
Data availability
The data that support the findings of this study are available from the corresponding author upon reasonable request.
References
Bennett, C. H. & Brassard, G. Quantum cryptography: public key distribution and coin tossing. In Proc IEEE International Conference on Computers, Systems and Signal Processing, 175–179 (IEEE, 1984).
Shor, P. W. & Preskill, J. Simple proof of security of the bb84 quantum key distribution protocol. Phys. Rev. Lett. 85, 441–444 (2000).
Lo, H.-K. & Chau, H. F. Unconditional security of quantum key distribution over arbitrarily long distances. Science 283, 2050–2056 (1999).
Renner, R. Security of quantum key distribution. Int. Symp. Inf. Theory 6, 1–127 (2008).
Scarani, V. The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301 (2009).
Lo, H.-K., Curty, M. & Tamaki, K. Secure quantum key distribution. Nat. Photonics 8, 595–604 (2014).
Hwang, W.-Y. Quantum key distribution with high loss: toward global secure communication. Phys. Rev. Lett. 91, 057901 (2003).
Wang, X.-B. Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett. 94, 230503 (2005).
Lo, H.-K., Ma, X. & Chen, K. Decoy state quantum key distribution. Phys. Rev. Lett. 94, 230504 (2005).
Lo, H.-K. Quantum key distribution with vacua or dim pulses as decoy states. In Proc International Symposium on information Theory, 2004. ISIT 2004, 137 (IEEE, 2004).
Gottesman, D., Lo, H.-K., Lutkenhaus, N. & Preskill, J. Security of quantum key distribution with imperfect devices. In Proc International Symposium on Information Theory, 2004. ISIT 2004, 136 (IEEE, 2004).
Wang, X.-B. Decoy-state protocol for quantum cryptography with four different intensities of coherent light. Phys. Rev. A 72, 012322 (2005).
Lim, C. C. W., Curty, M., Walenta, N., Xu, F. & Zbinden, H. Concise security bounds for practical decoy-state quantum key distribution. Phys. Rev. A 89, 022307 (2014).
Curty, M. Finite-key analysis for measurement-device-independent quantum key distribution. Nat. Commun. 5, 3732 (2014).
Cui, C. Twin-field quantum key distribution without phase postselection. Phys. Rev. Appl. 11, 034053 (2019).
Lu, F.-Y. Improving the performance of twin-field quantum key distribution. Phys. Rev. A 100, 022306 (2019).
Wang, X.-B. Three-intensity decoy-state method for device-independent quantum key distribution with basis-dependent errors. Phys. Rev. A 87, 012320 (2013).
Yu, Z.-W., Zhou, Y.-H. & Wang, X.-B. Statistical fluctuation analysis for measurement-device-independent quantum key distribution with three-intensity decoy-state method. Phys. Rev. A 91, 032318 (2015).
Zhou, Y.-H., Yu, Z.-W. & Wang, X.-B. Making the decoy-state measurement-device-independent quantum key distribution practically useful. Phys. Rev. A 93, 042324 (2016).
Wang, C. Phase-reference-free experiment of measurement-device-independent quantum key distribution. Phys. Rev. Lett. 115, 160502 (2015).
Xu, F., Xu, H. & Lo, H.-K. Protocol choice and parameter optimization in decoy-state measurement-device-independent quantum key distribution. Phys. Rev. A 89, 052333 (2014).
Ma, X., Qi, B., Zhao, Y. & Lo, H.-K. Practical decoy state for quantum key distribution. Phys. Rev. A 72, 012326 (2005).
Wang, C. Measurement-device-independent quantum key distribution robust against environmental disturbances. Optica 4, 1016–1023 (2017).
Zhao, Y., Qi, B. & Lo, H.-K. Quantum key distribution with an unknown and untrusted source. Phys. Rev. A 77, 052327 (2008).
Wang, X.-B. Decoy-state quantum key distribution with large random errors of light intensity. Phys. Rev. A 75, 052301 (2007).
Mizutani, A., Curty, M., Lim, C. C. W., Imoto, N. & Tamaki, K. Finite-key security analysis of quantum key distribution with imperfect light sources. New J. Phys. 17, 093011 (2015).
Grasselli, F. & Curty, M. Practical decoy-state method for twin-field quantum key distribution. New J. Phys. 21, 073001 (2019).
Lu, F.-Y. Practical issues of twin-field quantum key distribution. New J. Phys. 21, 123030 (2019).
Yoshino, K.-I. Quantum key distribution with an efficient countermeasure against correlated intensity fluctuations in optical pulses. npj Quantum Inf. 4, 8 (2018).
Roberts, G. Patterning-effect mitigating intensity modulator for secure decoy-state quantum key distribution. Opt. Lett. 43, 5110–5113 (2018).
Zhang, C.-M., Zhu, J.-R. & Wang, Q. Practical decoy-state reference-frame-independent measurement-device-independent quantum key distribution. Phys. Rev. A 95, 032309 (2017).
Boaron, A. Secure quantum key distribution over 421 km of optical fiber. Phys. Rev. Lett. 121, 190502 (2018).
Yin, H.-L. Measurement-device-independent quantum key distribution over a 404 km optical fiber. Phys. Rev. Lett. 117, 190501 (2016).
Tang, Z. Experimental demonstration of polarization encoding measurement-device-independent quantum key distribution. Phys. Rev. Lett. 112, 190503 (2014).
Wang, S. 2 GHz clock quantum key distribution over 260 km of standard telecom fiber. Opt. Lett. 37, 1008–1010 (2012).
Takesue, H. Quantum key distribution over a 40-db channel loss using superconducting single-photon detectors. Nat. Photonics 1, 343–348 (2007).
Thew, R. T. Low jitter up-conversion detectors for telecom wavelength ghz qkd. New J. Phys. 8, 32 (2006).
Rubenok, A. Real-world two-photon interference and proof-of-principle quantum key distribution immune to detector attacks. Phys. Rev. Lett. 111, 130501 (2013).
Liu, Y. Experimental measurement-device-independent quantum key distribution. Phys. Rev. Lett. 111, 130502–130502 (2013).
Comandar, Lea Quantum key distribution without detector vulnerabilities using optically seeded lasers. Nat. Photonics 10, 312 (2016).
Liu, H., Wang, J., Ma, H. & Sun, S. Polarization-multiplexing-based measurement-device-independent quantum key distribution without phase reference calibration. Optica 5, 902–909 (2018).
Wang, S. Experimental demonstration of a quantum key distribution without signal disturbance monitoring. Nat. Photonics 9, 832–836 (2015).
Wang, C. Experimental measurement-device-independent quantum key distribution with uncharacterized encoding. Opt. Lett. 41, 5596–5599 (2016).
Minder, M. Experimental quantum key distribution beyond the repeaterless secret key capacity. Nat. Photonics 13, 334–338 (2019).
Wang, S. Beating the fundamental rate-distance limit in a proof-of-principle quantum key distribution system. Phys. Rev. X 9, 021046 (2019).
Liu, Y. Experimental twin-field quantum key distribution through sending or not sending. Phys. Rev. Lett. 123, 100505–100505 (2019).
Zhong, X., Hu, J., Curty, M., Qian, L. & Lo, H. Proof-of-principle experimental demonstration of twin-field type quantum key distribution. Phys. Rev. Lett. 123, 100506 (2019).
Chen, J. Sending-or-not-sending with independent lasers: secure twin-field quantum key distribution over 509 km. Phys. Rev. Lett. 124, 070501 (2020).
Maeda, K., Sasaki, T. & Koashi, M. Repeaterless quantum key distribution with efficient finite-key analysis overcoming the rate-distance limit. Nat. Commun. 10, 3140 (2019).
Ji, Y. A phase stable short pulse generator using a dpmzm and phase modulators for application in 160 gbaud dqpsk systems. Opt. Commun. 285, 1964–1969 (2012).
Li, Y. et al. 160gbaud/s to 40gbaud/s otdm-dqpsk de-multiplex based on a dual parallel mach-zehnder modulator. In OFC/NFOEC, 1–3 (IEEE, 2012).
Wang, H., Kong, D., Li, Y., Wu, J. & Lin, J. Simple asymmetric optical dqpsk modulation and demodulation scheme. Opt. Commun. 288, 17–22 (2013).
Tang, Y.-L. Measurement-device-independent quantum key distribution over 200 km. Phys. Rev. Lett. 113, 190501 (2014).
Wang, X.-B., Yang, L., Peng, C.-Z. & Pan, J.-W. Decoy-state quantum key distribution with both source errors and statistical fluctuations. New J. Phys. 11, 075006 (2009).
Acknowledgements
This work has been supported by the National Key Research and Development Program of China (Grant No. 2018YFA0306400), the National Natural Science Foundation of China (Grants Nos. 61622506, 61575183, 61627820, 61475148, and 61675189), and the Anhui Initiative in Quantum Information Technologies.
Author information
Authors and Affiliations
Contributions
F.-Y.L. and X.L. start the project and design the experiment. F.-Y.L., X.L., S.W., and D.-Y.H. perform the experiment and complete the data analysis. G.-J.F.-Y., R.W., and P.Y. provide the theoretical calculations. Z.-Qi.Y., W.C., G.-C.G. and Z.-F.H. supervise the project.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Lu, FY., Lin, X., Wang, S. et al. Intensity modulator for secure, stable, and high-performance decoy-state quantum key distribution. npj Quantum Inf 7, 75 (2021). https://doi.org/10.1038/s41534-021-00418-x
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41534-021-00418-x