Abstract
Quantum key distribution (QKD) over a point-to-point link enables us to benefit from a genuine quantum effect even with conventional optics tools such as lasers and photon detectors, but its capacity is limited to a linear scaling of the repeaterless bound. Recently, twin-field (TF) QKD was conjectured to beat the limit by using an untrusted central station conducting a single-photon interference detection. So far, the effort to prove the conjecture was confined to the infinite key limit which neglected the time and cost for monitoring an adversary’s act. Here we propose a variant of TF-type QKD protocol equipped with a simple methodology of monitoring to reduce its cost and provide an information-theoretic security proof applicable to finite communication time. We simulate the key rate to show that the protocol beats the linear bound in a reasonable running time of sending 1012 pulses, which positively solves the conjecture.
Similar content being viewed by others
Introduction
Quantum key distribution (QKD)1,2 provides a secret key shared between two remote legitimate parties with information-theoretic security, enabling private communication regardless of an adversary’s computational power and advanced hardware technology. It also has a welcome feature that, for a simple prepare-and-measure type of QKD protocols, the sender’s and the receiver’s device can be implemented with current technology such as lasers, linear optics components, and photon detectors. A drawback is a limitation on the key generation rate stemming from the loss in the channel. For a direct link from the sender to the receiver, the key rate cannot surpass the loss bounds3,4 of \(O(\eta )\), where \(\eta\) is the single-photon transmissivity of the link. Although quantum repeaters5 are known to beat this limitation by placing untrusted intermediate stations to segment the link, the required technology to manipulate quantum states is demanding. Early proposals to mitigate this demand to beat the \(O(\eta )\) scaling still requires quantum memories6 or quantum non-demolition (QND) measurements7, which are currently in the developing stage.
Surprisingly, possibility of achieving an \(O\left( {\sqrt \eta } \right)\) scaling with current technology was recently proposed8 as a protocol called twin-field (TF) QKD, a variant of the measurement-device independent (MDI) protocols9. In this protocol, an untrusted station Charlie sitting midway between Alice and Bob simply conducts an interference measurement to learn the relative phase between the pulse pair sent from Alice and Bob. On the surface, the scaling may be understood from the interpretation that a photon detected by Charlie has traveled either the Alice-Charlie segment or the Bob-Charlie segment with transmissivity \(\sqrt \eta\). But a similar phase encoding scheme was already adopted in an earlier MDI-QKD protocol10, which did not achieve the \(O\left( {\sqrt \eta } \right)\) scaling. The essential point lies elsewhere, in how Alice and Bob can monitor the adversary’s attack on the link and on Charlie’s apparatus. For this purpose, the TF QKD was specifically designed so as to attain the compatibility to the standard decoy-state method11,12,13, which have been successfully used in other QKD protocols.
As the original proposal8 lacked a rigorous security proof, many intensive studies14,15,16,17,18,19,20,21 have been devoted to achieving information-theoretic proofs of variants of TF QKD15,16,17 and a family of similar protocols called phase-matching (PM) QKD14,18,19,20,21. As was the case for other QKD protocols, these first proofs mainly consider the asymptotic regime. All the key rates shown to beat the loss bounds so far are achievable only in the limit of infinitely large number of pulses being sent. Explicit formulation in the finite-size regime is found only in the work of Tamaki et al.15, but this early proposal barely surpasses the loss bounds even in the asymptotic limit, and no numerical values were given for finite-size effect. Hence, at this point, we have totally no clue on how long one must run a QKD protocol on end to beat the loss bounds. It could be hours, days, or even longer.
We should also be aware that the finite-size regime is not a mere appendage to the asymptotic regime. In the latter regime, the fraction of the communication time devoted to the monitoring of the adversary is assumed to be negligible. This implies that one is allowed to invest an infinite resource to the monitoring with no penalty, despite the fact that the monitoring is the main obstacle in the TF-type protocols. In fact, the protocol by Lin and Lütkenhaus20, which attains both the simplest of the proofs and the highest of the asymptotic key rates, adopts a newly proposed generalization of the decoy-state method for a complete characterization of the adversary’s act, by using the set of test states composed of coherent states with every complex amplitude. Although it gives a lucid view on the problem, it is probably not the shortest route to answer the ultimate question of whether one can find a protocol with information-theoretic security to beat the loss bounds with current technology.
Here we positively answer to the above question by proposing a variant of PM-QKD protocol equipped with a simple security proof in the finite-size regime. Our protocol also involves a kind of extension of the standard decoy-state method, but interestingly, its direction is the opposite of the generalization by Lin and Lütkenhaus: we try to learn about the adversary’s act as little as possible except the parameter crucial for the security. For this purpose, we construct a minimal set of test states to satisfy an operator inequality, which we call an operator dominance condition. Our method drastically simplifies the analysis of the finite-size effect to just a double use of classical Bernoulli sampling.
Results
Proposed protocol
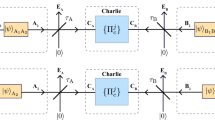
The setup for our proposed protocol is illustrated in Fig. 1. In order to distribute a secure key, Alice and Bob both send optical pulses to Charlie, the central untrusted station. Each of the senders randomly switches between the signal mode and the test mode. They use the signal mode for accumulating raw key bits and the test mode for monitoring the amount of leak.
Illustration of the proposed quantum key distribution protocol. In the signal mode, Alice and Bob each encode their random bits on phase-locked pulses with intensity (mean photon number) μ through phase modulators (PMODs). In the test mode, they independently randomize the optical phase θ and switch among three intensities 0, μ1, and μ2. The central station Charlie, who may be in control of an adversary, announces whether his detection has succeeded and if it has, he further announces whether he has found the pulse pair to be in-phase or anti-phase. Bob flips his bit when anti-phase was announced
The signal mode is based on the PM-QKD protocol14, which is common to previous proposals18,19,20,21. We assume Alice and Bob have phase-locked pulse sources to generate in-phase pulses. Each party encodes a random bit by applying 0 or π phase shift to the pulse with a fixed intensity μ (defined in terms of its mean photon number) and sends it to Charlie. He measures and announces whether the two pulses are in-phase or anti-phase, by using a 50:50 beam-splitter and a pair of photon detectors. Successful detection at Charlie allows Alice and Bob to learn whether their bits have the same or different values. Thus, by appropriately flipping Bob’s bits, Alice, and Bob can accumulate shared random bits by repetition, which we call sifted keys.
As in refs. 19,21, we associate the amount of leak to the phase errors in an equivalent protocol in which Alice and Bob use auxiliary qubits A and B. Let us call \(\left\{ {\left. {|0} \right\rangle ,\left. {|1} \right\rangle } \right\}\) the Z basis of a qubit, and \(\left\{ {\left. {\left| \pm \right.} \right\rangle : = \left( {\left. {\left| 0 \right.} \right\rangle \pm \left. {\left| 1 \right.} \right\rangle } \right)/\sqrt 2 } \right\}\) the X basis. Alice and Bob’s procedure in the signal mode can be equivalently executed by preparing the qubits AB and the optical pulses CACB in a joint quantum state
Suppose that Charlie has declared K0 detected rounds after the repetition. This leaves the corresponding K0 pairs of qubits at Alice and Bob. If they measure the qubits in the Z basis, they obtain K0-bit sifted keys in the actual protocol. To assess the amount of leak in the sifted keys, we consider a virtual protocol in which they measure the qubits in the X basis instead and count the number of phase errors (X errors) among the K0 pairs. Here an X error is defined to be an event where the pair was found in either state \(\left. {| + } \right\rangle \left. {| - } \right\rangle\) or \(\left. {| - } \right\rangle \left. {| + } \right\rangle\). We denote the number of X errors as \(K_0^{({\mathrm{even}})}\) for the reason we clarify later. If there is a promise that the phase error rate \(K_0^{({\mathrm{even}})}/K_0\) is low, it implies that the leak on the sifted keys is small. Hence, the aim of the test mode is to gather data to compute a good upper bound eph on \(K_0^{({\mathrm{even}})}/K_0\). In the asymptotic limit, shortening by fraction h(eph) via privacy amplification achieves the security22,23, where \(h(x) = - x{\mathrm{log}}_2x - (1 - x){\mathrm{log}}_2(1 - x)\) for \(x \le 1\)/2 and \(h(x) = 1\) for \(x > 1\)/2.
To obtain a good intuition on the meaning of the observable \(K_0^{({\mathrm{even}})}\) in the virtual protocol, consider a scenario in which Alice and Bob make the X basis measurements before sending out the optical pulses. Notice that the state (Eq. 1) is rewritten as
where \(c_ + : = {\mathrm{e}}^{ - \mu }{\kern 1pt} {\mathrm{cosh}}{\kern 1pt} \mu\) and \(c_ - : = e^{ - \mu }{\kern 1pt} {\mathrm{sinh}}{\kern 1pt} \mu\). The state \(\left. {|\sqrt{\mu _{{\mathrm{even}}}}} \right\rangle : = \left( {\left. {|\sqrt \mu } \right\rangle + \left. {|\sqrt { - \mu } } \right\rangle } \right)/2\sqrt {c_ + } \) consists of even photon numbers, whereas the state \(\left. {|\sqrt{\mu _{{\mathrm{odd}}}}}\right\rangle : = \left( {\left. {|\sqrt \mu } \right\rangle - \left. {|\sqrt { - \mu } } \right\rangle } \right)/2\sqrt {c_ - } \) consists of odd photon numbers. Then, we may interpret that an X error occurs with probability \(p_{{\mathrm{even}}}: = c_ + ^2 + c_ - ^2 = {\mathrm{e}}^{ - 2\mu }{\kern 1pt} {\mathrm{cosh}}{\kern 1pt} 2\mu\) and the optical pulses are sent in state \(\rho ^{({\mathrm{even}})}\), which is given by
For probability \(p_{{\mathrm{odd}}}: = 1 - p_{{\mathrm{even}}}\), the optical pulses are sent in state \(\rho ^{({\mathrm{odd}})}\), where
We see that for state \(\rho ^{({\mathrm{even}})}\), the total number of photons in the pulse pair is always even. Hence, the number \(K_0^{({\mathrm{even}})}\) can be interpreted as the frequency of detection when the total emitted photon number of the pulse pair was even.
The main question is how we should design the test mode to estimate the number \(K_0^{({\mathrm{even}})}\) in the signal mode. An obvious choice is to prepare actually the state \(\rho ^{({\mathrm{even}})}\) as was proposed recently21, but generation of such a non-classical optical state with a good fidelity will be hard to realize in current technology. For the use of laser pulses, previous approaches18,19 for the asymptotic regime use the standard decoy-state method in which various detection rates labeled by emitted photon numbers are estimated. A bound on the phase error rate is then computed from those rates through a set of inequalities. Lin and Lütkenhaus20 generalized the decoy-state method to a kind of tomography, in which case tight estimation of phase error rate \(K_0^{({\mathrm{even}})}\)/\(K_0\) should be possible. In order to simplify the security argument for the finite-size regime, here we take a more direct approach of constructing a state approximating \(\rho ^{({\mathrm{even}})}\). Of course, \(\rho ^{({\mathrm{even}})}\) is a highly non-classical optical state and thus it is impossible to approximate it by a mixture of coherent states. As the second-best plan, we propose to find a linear combination \(\mathop {\sum}\nolimits_i {{\kern 1pt} \alpha ^{(i)}\rho ^{(i)}(\alpha ^{(i)} \in {\Bbb R})}\) of test states \(\{ \rho ^{(i)}\}\) to approximate \(\rho ^{({\mathrm{even}})}\). The crux is that we allow coefficients \(\{ \alpha ^{(i)}\}\) to include negative values as long as it satisfies an operator inequality,
which we call an operator dominance condition.
Based on the above design policy, we found the following potocol (see Fig. 1).
-
1.
Alice chooses a label from {“0”, “10”, “11”, “2”} with probabilities p0, p10, p11, and p2, respectively. According to the label, Alice performs one of the following procedures.
“0”: She generates a random bit a and sends a pulse with amplitude \(( - 1)^a\sqrt \mu\).
“10”: She sends the vacuum.
“11”: She sends a phase-randomized pulse with intensity μ1.
“2”: She sends a phase-randomized pulse with intensity μ2.
-
2.
Bob independently carries out the same procedure as Alice in Step 1.
-
3.
Alice and Bob repeat Steps 1 and 2 in total of Ntot times.
-
4.
For every pair of pulses received from Alice and Bob, Charlie announces whether the phase difference was successfully detected. When it was detected, he further announces whether it was in-phase or anti-phase.
-
5.
Alice and Bob disclose their label choices. Let K0 be the number of detected rounds for which both Alice and Bob chose “0”. Alice concatenates the random bits for the K0 rounds to define her sifted key. Bob defines his sifted key in the same way except that he flips all the bits for the rounds declared to be anti-phase.
-
6.
Let K10, K11, and K2 be the number of detected rounds for which both Alice and Bob chose the same label “10”, “11”, and “2”, respectively. Let \(K_1: = K_{10} + K_{11}\).
-
7.
For error correction, Alice announces HEC bits of syndrome of a linear code for her sifted key. Bob reconciles his sifted key accordingly. Alice and Bob verify the correction by comparing \(\zeta^\prime\) bits via universal2 hashing24.
-
8.
They apply the privacy amplification to obtain final keys of length
where the parameter \(\zeta\) and the function \(f(K_1,K_2)\) will be specified below.
Security proof
In order to prove the security of the above protocol, we need to construct an upper bound on the phase error rate \(K_0^{({\mathrm{even}})}\)/\(K_0\) in the virtual protocol. To cover the finite-size cases as well, our objective is to construct \(f(K_1,K_2)\) which satisfies
for any attack in the virtual protocol. It is known that it immediately implies that the actual protocol is \(\epsilon _{{\mathrm{sec}}}\)-secure with a small security parameter \(\epsilon _{{\mathrm{sec}}} = \sqrt 2 \sqrt {\epsilon + 2^{ - \zeta }} + 2^{ - \zeta^\prime }\). See methods section for the detailed definition of security.
Let \(\tau (\mu )\) be the phase-randomized coherent state with mean photon number μ,
Our proof method is based on an operator dominance condition which reads
where \({\mathrm{\Gamma }}\) and \({\mathrm{\Lambda }}\) are positive constants. Our security argument below holds for any set of parameters (p10, p11, μ, μ1, μ2, \({\mathrm{\Gamma }}\), \({\mathrm{\Lambda }}\)) satisfying Eq. (9). A simple method of computing \({\mathrm{\Gamma }}\) and \({\mathrm{\Lambda }}\) from (p10, p11, μ, μ1, μ2) is given in methods section.
We first clarify the meaning of numbers K1 and K2 collected in the test mode. By definition of the protocol, K1 is the frequency of detection when the pulse pair CACB was initially prepared in state \(\rho ^{({\mathrm{test}}1)}\), where
Similarly, K2 is the frequency of detection for state
Also recall that \(K_0^{({\mathrm{even}})}\) is the frequency of detection for state \(\rho ^{({\mathrm{even}})}\) defined in Eq. (3).
When Eq. (9) holds, there exists a normalized state \(\rho ^{({\mathrm{junk}})}\), which satisfies
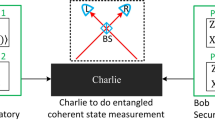
for \({\mathrm{\Delta }}: = p_{10}^2 + p_{11}^2 - {\mathrm{\Gamma }} - {\mathrm{\Lambda }} \ge 0\). Therefore, we can reinterpret the state \(\rho ^{({\mathrm{test}}1)}\) as a mixture of the three states \(\rho ^{({\mathrm{test}}2)}\), \(\rho ^{({\mathrm{junk}})}\), and \(\rho ^{({\mathrm{even}})}\). Let us consider a modified scenario in which the state of the pulse pair is directly prepared in various states with the probabilities specified in Fig. 2. In this scenario, the frequencies \(K_1^{({\mathrm{test}}2)}\) and \(K_1^{({\mathrm{even}})}\) shown in Fig. 2 are also well-defined. Suppose that the adversary’s attack (which may include taking over Charlie’s announcement) is the same as that for the actual/virtual protocols. As the breakdown of the mixed state \(\rho ^{({\mathrm{test}}1)}\) in the actual protocol is revealed only after Charlie has announced all the detections, we see that the following property naturally holds.
-
(i)
The marginal joint probability of the three variables \((K_2,K_1,K_0^{({\mathrm{even}})})\) in the modified scenario is the same as that in the virtual protocol.
This means that if Eq. (7) is true in the modified scenario, it is also true in the virtual protocol.
From comparison between the first and the second rows in Fig. 2, we notice that K2 and \(K_1^{({\mathrm{test}}2)}\) in the modified scenario are detection frequencies of the same initial state \(\rho ^{({\mathrm{test}}2)}\). As the adversary has no clue about whether a pulse pair in state \(\rho ^{({\mathrm{test}}2)}\) belongs to Test1 mode or to Test2 mode, they cannot force Charlie to detect one of the cases preferably over the others. Hence, the ratio of K2 to \(K_1^{({\mathrm{test}}2)}\) is expected to be close to the initial ratio of the two cases, \(p_2^2/{\mathrm{\Gamma }}\). More precisely, K2 is a Bernoulli sampling from a population with \(K_2 + K_1^{({\mathrm{test}}2)}\) elements. This is also the case with \(K_1^{({\mathrm{even}})}\) and \(K_0^{({\mathrm{even}})}\). It leads to the following property of conditional probabilities stated in terms of binomial distribution \(B(K;n,p): = p^K(1 - p)^{n - K}n!/K!(n - K)!\).
-
(ii)
In the modified scenario, it holds that
and similarly,
Relation between the actual/virtual protocol and the modified scenario. Each row is chosen with the initial probability and the pulse pair is prepared in the corresponding quantum state. The detection frequency is the number of times Charlie has declared success. The cases when Alice’s and Bob’s label differ are irrelevant and not shown. In the actual protocol, three detection frequencies, K0, K1, and K2 are determined. In the virtual protocol, K0 is decomposed into a sum of two frequencies, \(K_0^{({\mathrm{even}})}\) and \(K_0^{({\mathrm{odd}})}\). The security of the actual protocol is quantitatively assured if a good upper bound on \(K_0^{({\mathrm{even}})}\) is found. To find such a bound, we consider a modified scenario in which the variables \((K_2,K_1,K_0^{({\mathrm{even}})})\) follows the same statistics as in the virtual protocol. In the modified scenario, K1 is interpreted as a sum of three frequencies corresponding to three different initial quantum states of the pulse pair, \(\rho ^{({\mathrm{test}}2)}\), \(\rho ^{({\mathrm{junk}})}\), and \(\rho ^{({\mathrm{even}})}\). We notice that the first two rows are chosen with probabilities \(p_2^2\) and \({\mathrm{\Gamma }}\) and classified to the Test2 mode and to the Test1 mode accordingly, but the pulse pairs are initially prepared in the same state \(\rho ^{({\mathrm{test}}2)}\). Charlie’s success/failure declaration and the Test2/Test1 mode choice should thus be statistically independent. It follows that the conditional statistics of variable K2 obeys a Binomial distribution given that the sum \(K_2 + K_1^{({\mathrm{test}}2)}\) is a constant. This leads to a lower bound on \(K_1^{({\mathrm{test}}2)}\) in terms of K2. A similar argument holds for variables \(K_1^{({\mathrm{even}})}\) and \(K_0^{({\mathrm{even}})}\), leading to an upper bound on \(K_0^{({\mathrm{even}})}\) in terms of \(K_1^{({\mathrm{even}})}\). Combining these, we obtain an upper bound on \(K_0^{({\mathrm{even}})}\) in terms of K1 and K2, which should be applicable to the virtual protocol
The properties (i) and (ii) reduce the security proof to an elementary problem of classical random sampling. In an asymptotic limit of K1, \(K_2 \to \infty\), a bound on \(K_0^{({\mathrm{even}})}\) is immediately obtained from the relations \(K_1^{({\mathrm{test}}2)}/K_2 = {\mathrm{\Gamma }}/p_2^2\), \(K_0^{({\mathrm{even}})}/K_1^{({\mathrm{even}})} = p_0^2p_{{\mathrm{even}}}/{\mathrm{\Lambda }}\), and \(K_1 \ge K_1^{({\mathrm{test}}2)} + K_1^{({\mathrm{even}})}\). A finite-size bound \(f(K_1,K_2)\) satisfying Eq. (7) can be constructed by the use of the Chernoff bound25. As explained in methods section, we can compute general bounds \(M^ \pm (K,p,\epsilon )\) that satisfy
when \({\mathrm{Prob}}\{ K|M + K = n\} = B(K;n,p)\) holds for all \(n \ge 1\). Then, we can construct the function \(f(K_1,K_2)\) as
with
which obviously satisfies Eq. (7) and hence completes the security proof.
For an intuitive understanding of the amount of the finite-size effect, an approximate expression of the bound \(f(K_1,K_2)\) may be helpful. The general bounds M± are approximated as
when \((1 - p)K \gg - {\mathrm{log}}{\kern 1pt} \epsilon\). Then, we can approximate \(f(K_1,K_2)\) as
with
Numerical simulation
We simulated the key rate G/Ntot as a function of distance L between Alice and Bob when they are fiber-linked to Charlie with a loss of 0.2 dB/km. We assumed a detection efficiency of \(\eta _{\mathrm{d}} = 0.3\) for Charlie’s apparatus. The parameters \((\mu ,\mu _1,\mu _2,p_0,p_{10},p_{11},p_2)\) are optimized for each distance. The detail of the model for determining K0, K1, and K2 is given in methods section.
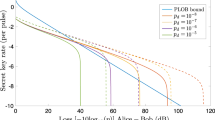
Figure 3 shows the key rates of our protocol in the asymptotic limit and in the finite-size cases with \(N_{{\mathrm{tot}}} = 10^{11}\) and 1012. We have also plotted the PLOB bound4, −\({\mathrm{log}}_2(1 - \eta _{{\mathrm{AB}}})\), for the direct link from Alice to Bob with transmissivity \(\eta _{{\mathrm{AB}}} = \eta _{\mathrm{d}}10^{ - 0.2L/10}\), assuming the same detection efficiency. The asymptotic key rate shows an \(O\left( {\sqrt {\eta _{{\mathrm{AB}}}} } \right)\) scaling. As expected, the asymptotic rate is lower than those of the protocols18,19,20 investing more resources for the monitoring. The main feature of our protocol lies in the provably secure key rate in the finite-size regime. We see that at \(N_{{\mathrm{tot}}} = 10^{11}\) it barely surpasses the PLOB bound, and at \(N_{{\mathrm{tot}}} = 10^{12}\) it clearly beats the bound at ~ 300 km. The dotted line below the PLOB bound is the asymptotic rate for the ideal decoy-state BB84 protocol2,4,13, \(\eta _{{\mathrm{AB}}}\)/\((2\mathrm{e})\), which is surpassed by our protocol beyond 200 km even with \(N_{{\mathrm{tot}}} = 10^{11}\).
The key rate per pulse as a function of distance L between Alice and Bob. We assumed a fiber loss of 0.2 dB/km, a loss-independent misalignment error of em = 0.03, a detector dark counting probability of pd = 10−8, and a detection efficiency of \(\eta _{\mathrm{d}} = 0.3\). The rate in the asymptotic limit and those in the finite-size cases with transmission of \(N_{{\mathrm{tot}}} = 10^{11}\), 1012 pulse pairs are shown. For comparison, we also show the PLOB bound4 and the asymptotic key rate of ideal decoy-BB84 protocol2,4 for the direct link transmissivity \(\eta _{\mathrm{d}}10^{ - 0.2L/10}\)
As an example, we present explict values of the optimized parameters for \(N_{{\mathrm{tot}}} = 10^{12}\) at 340 km. The intensities are \((\mu ,\mu _1,\mu _2) = (0.012,0.23,0.022)\) and the probabilities are \((p_0,p_{10},p_{11},p_2) = (0.73,0.21,0.013,0.049)\). The operator dominance condition (Eq. 9) is satisfied with \({\mathrm{\Gamma }} = 1.2 \times 10^{ - 3}\) and \({\mathrm{\Lambda }} = 1.2 \times 10^{ - 2}\). The observed values expected from the model are \((K_0,K_1,K_2) = (1.6 \times 10^6,1.0 \times 10^5,1.2 \times 10^5)\).
Discussion
We proposed a variation of TF-type QKD protocol by using the signal mode of the PM-QKD protocol and the test mode specifically designed to simplify the estimation process of the amount of information leak. The simulated key rate shows that it beats the PLOB bound when the total number of pulse pairs emitted from Alice and Bob is 1011 to 1012, which corresponds to several to twenty minutes for a system of 1 GHz pulse repetition. It amounts to settling down the conjecture with a comprehensive information-theoretic security proof covering the finite-size key regime.
In the protocol, the events where Alice and Bob have chosen different local labels are simply discarded. It is an interesting question whether we may improve the key rate by incorporating the detection frequencies of such events in the analysis. Conversely, by accepting a lower key rate, we may be able to simplify the protocol to use only three intensities \((0,\mu ,\mu _1)\) instead of four in the current protocol. We leave these questions to future study.
An essential ingredient of our design is the operator dominance method of estimating the detection frequency of one state from those of a combination of different test states. We can identify two instances of binomial distribution in a modified scenario, which simplifies the required statistical analysis in the finite-size regime. As a methodology, the number of test states forming the linear combination to approximate the target state does not affect the simplicity of analysis. As long as the operator dominance condition is satisfied, we can group the states with positive coefficients to define state \(\rho ^{({\mathrm{test}}1)}\) and those with negative to define \(\rho ^{({\mathrm{test}}2)}\). Such a flexibility will be used to improve the finite-size key rate of TF-type protocols further. We also expect that the method can be used to simplify the security analysis of other QKD protocols, especially when the imperfection of practical devices is taken into account.
Methods
Definition of security in the finite-size regime
We evaluate the secrecy of the final key as follows. When the final key length is \(G \ge 1\), we represent Alice’s final key and an adversary’s quantum system as a joint state
and define the corresponding ideal state as
Let \(\left\| \sigma \right\|_1 = {\mathrm{Tr}}\sqrt {\sigma ^{\mathrm{\dagger }}\sigma }\) be the trace norm of an operator σ. We say a protocol is \(\epsilon _{{\mathrm{sct}}}\)-secret when
holds regardless of the adversary’s attack. It is known26 that if the number of phase errors is bounded as in Eq. (7), the protocol is \(\epsilon _{{\mathrm{sct}}}\)-secret with \(\epsilon _{{\mathrm{sct}}} = \sqrt 2 \sqrt {\epsilon + 2^{ - \zeta }}\).
For correctness, we say a protocol is \(\epsilon _{{\mathrm{cor}}}\)-correct if the probability for Alice’s and Bob’s final key to differ is bounded by \(\epsilon _{{\mathrm{cor}}}\). Our protocol achieves \(\epsilon _{{\mathrm{cor}}} = 2^{ - \zeta^\prime }\) via the verification in Step 7.
When the above two conditions are met, the protocol becomes \(\epsilon _{{\mathrm{sec}}}\)-secure with \(\epsilon _{{\mathrm{sec}}} = \epsilon _{{\mathrm{sct}}} + \epsilon _{{\mathrm{cor}}}\) in the sense of universal composability27.
Construction of operator dominance condition
Here we describe a procedure to compute parameter sets fulfilling the operator dominance condition (Eq. 9). Suppose that values of μ1, μ2, p10, and \(p_{11} > 0\) satisfying
are given. Then, we can satisfy Eq. (9) by choosing \({\mathrm{\Gamma }}\) and \({\mathrm{\Lambda }}\) according to the following:
The proof goes as follows. Using the representation \(\tau (\mu ) = {\mathrm{e}}^{ - \mu }\mathop {\sum}\nolimits_k {(\mu ^k/k!)\left. {|k} \right\rangle \left\langle {k|} \right.}\), we see that the lefthand side of Eq. (9) has a diagonal form \(\mathop {\sum}\nolimits_{k,k^\prime } {(q_{k + k^\prime }/k!k^\prime !)\left. {|k,k^\prime } \right\rangle \left\langle {k,k^\prime |} \right.}\) on the Fock basis, where
Substituting Eq. (26), we have
under condition (Eq. 25). Using qm, Eq. (27) is rewritten as
Let \(\pi _{\mathrm{e}} = \mathop {\sum}\nolimits_{k = 0}^\infty {\left. {|2k} \right\rangle \left\langle {2k|} \right.}\) and \(\pi _{\mathrm{o}} = \mathop {\sum}\nolimits_{k = 0}^\infty {\left. {|2k + 1} \right\rangle \left\langle {2k + 1|} \right.}\) be projections to the subspaces with even and odd photon numbers, respectively. We denote \(\pi _{st}: = \pi _s \otimes \pi _t(s,t = {\mathrm{e}},{\mathrm{o}})\). From Eq. (3), we have
Hence, Eq. (9) is equivalent to the following set of conditions:
The condition (Eq. 34) is obviously true from Eq. (29). Since \(q_{k + k^\prime } > 0\) when \(k + k^\prime\) is even, Eq. (32) is true if
with
Since
from Eq. (30), we see that condition Eq. (35) is true and so is condition (Eq. 32). Similarly, for
we have
implying that condition (Eq. 33) is also true.
Bounds for a classical random sampling
Here we give a computable definition of functions \(M^ \pm (K;p,\epsilon )\) and prove the relevant properties. We assume \(p \in (0,1)\) and \(\epsilon > 0\). Let \(\bar p: = 1 - p\), \(M_{p,K}: = K\bar p/p\), \(K_{p,\epsilon }: = {\mathrm{log}}{\kern 1pt} \epsilon /{\mathrm{log}}{\kern 1pt} p\), and
with \(D(q\parallel p): = q{\kern 1pt} {\mathrm{log}}(q/p) + (1 - q){\kern 1pt} {\mathrm{log}}[(1 - q)/(1 - p)]\). Then, for \(K \ge 0\), we have \(g(0,K_{p,\epsilon }) = - {\mathrm{log}}{\kern 1pt} \epsilon\), \(g(M_{p,K},K) = 0\), and \(g(\infty ,K) = \infty\). The partial derivatives satisfy
and
Hence we may uniquely define \(M^ \pm (K;p,\epsilon )\) for \(K \ge 0\) as follows.
Definition 1
M+ is the unique solution of the equation \(g(M,K) = - {\mathrm{log}}{\kern 1pt} \epsilon\) for \(M \in (M_{p,K},\infty )\). For \(K > K_{p,\epsilon }\), M− is the unique solution of the equation \(g(M,K) = - {\mathrm{log}}{\kern 1pt} \epsilon\) for \(M \in (0,M_{p,K})\). For \(K \le K_{p,\epsilon }\), let \(M^ - : = 0\).
Due to the properties of \(g(M,K)\) described above, \(M^ \pm (K)\) is non-decreasing. Using this definition, we can prove the following lemma:
Lemma 1
Let M and K be random variables taking nonnegative integer values. If \({\mathrm{Prob}}\{ K|M + K = n\} = B(K;n,p)\) for all \(n \ge 1\), then
and
Proof: using the Chernoff bound25 for the binominal distribution, we have
for all \(n \ge 1\), leading to
If \(M > M^ + (K) > M_{p,K}\), then \(M > (M + K)\bar p \ge 0\) and \(g(M,K) > g(M^ + (K),K) = - {\mathrm{log}}{\kern 1pt} \epsilon\) hold. Hence Eq. (46) implies \({\mathrm{Prob}}\{ M > M^ + (K)\} \le \epsilon\), leading to Eq. (43). Similarly to Eq. (46), we can also obtain
If \(M < M^ - (K) < M_{p,K}\), then \(M < (M + K)\bar p\), \(K > K_{p,\epsilon } > 0\), and \(g(M,K) > g(M^ + (K),K) = - {\mathrm{log}}{\kern 1pt} \epsilon\) hold. Then, Eq. (47) implies \({\mathrm{Prob}}\{ M < M^ - (K)\} \le \epsilon\), leading to Eq. (44).
Calculation of simulated key rates
For the simulation of the key rate G/Ntot as a function of distance between Alice and Bob, we adopted the following model for the channels and Charlie’s detection apparatus. We assumed a fiber loss of 0.2 dB/km and a detection efficiency of \(\eta _{\mathrm{d}} = 0.3\) for Charlie’s apparatus. The distance between Alice and Bob is denoted by L (in km). The overall transmissivity from Alice to Charlie’s detection is then \(\eta = \eta _{\mathrm{d}}10^{ - 0.2L/20}\). The overall transmissivity from Bob to Charlie is also \(\eta\). We assume that (honest) Charlie declares a success when one or both of the detectors have reported detection. When both have detected, he randomly declares in-phase or anti-phase. We assume that each detector has a dark count probability of \(p_{\mathrm{d}} = 10^{ - 8}\), which amounts to the effective probability \(d: = 2p_{\mathrm{d}} - p_{\mathrm{d}}^2\) from the two detectors. The expected frequencies of detection are then modeled as
For the bit error rate, we use the following model that includes a mode/phase mismatch error of \(e_{\mathrm{m}} = 0.03\):
We assume the cost of error correction HEC to be \(1.1 \times K_0h(e_{{\mathrm{bit}}})\).
For calculation of the key rate with a finite value of Ntot, we chose the security parameters as \(\epsilon = 2^{ - 66}\), \(\zeta = 66\), and \(\zeta^\prime = 32\), which makes the protocol \(\epsilon _{{\mathrm{sec}}}\)-secure with \(\epsilon _{\sec } = 2^{ - 31} < 10^{ - 10}\). The final key length \(G = K_0(1 - h(f(K_1,K_2)/K_0)) - H_{{\mathrm{EC}}} - \zeta - \zeta^\prime\) is then optimized with the Nelder–Mead method over six parameters μ, \(a = \mu _1/\mu\), \(b = \mu _2/\mu\), p2, \(p_1 = p_{10} + p_{11}\), and \(s = p_{10}\)/\((p_{10} + p_{11})\). For every point shown in Fig. 3, we confirmed that the absolute values of the numerical partial derivative at each optimized condition were sufficiently small compared with the parameter values.
For calculation of the asymptotic key rate, we analytically reduced the number of parameters as follows. Using Eq. (20), the phase error rate for \(N_{{\mathrm{tot}}},K_0,K_1,K_2 \to \infty\) is given by
From Eqs. (26), (27), (48), (49), and (50), we see that it can be cast into the form \(f(K_1,K_2)\)/\(K_0 = g(p_{10}^2/p_{11}^2)\) with
where {Cj}j depend only on μ, μ1, μ2, \(\eta\), and d. The function g(λ) takes its minimum at \(\lambda ^ \ast : = C_2 + \sqrt {(C_2 + C_4)/C_3}\) with
Hence, in the limit of \(p_0 \to 1\) and p10, p11, \(p_2 \to 0\) with \(p_{10}^2\)/\(p_{11}^2 = \lambda ^ \ast\), we have
To calculate the asymptotic key rate in Fig. 3, we optimized the above expression over μ, \(a = \mu _1\)/μ and \(b = \mu _2\)/μ with the Nelder–Mead method.
Data availability
Data sharing not applicable to the article as no data sets were generated or analyzed during the current study.
Code availability
Computer codes to calculate the key rates are available from the corresponding author upon reasonable request.
References
Bennett, C. H. & Brassard, G. Quantum cryptography: public key distribution and coin tossing. Proc. IEEE Int. Conf. Comput. Syst. Signal Process. 175–179 (1984)
Scarani, V. et al. The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301–1350 (2009).
Takeoka, M., Guha, S. & Wilde, M. M. Fundamental rate-loss tradeoff for optical quantum key distribution. Nat. Commun. 5, 5235 (2014).
Pirandola, S., Laurenza, R., Ottaviani, C. & Banchi, L. Fundamental limits of repeaterless quantum communications. Nat. Commun. 8, 15043 (2017).
Briegel, H., Dür, W., Cirac, J. I. & Zoller, P. Quantum repeaters: the role of imperfect local operations in quantum communication. Phys. Rev. Lett. 81, 5932–5935 (1998).
Panayi, C., Razavi, M., Ma, X. & Lütkenhaus, N. Memory-assisted measurement-device-independent quantum key distribution. New J. Phys. 16, 043005 (2014).
Azuma, K., Tamaki, K. & Munro, W. J. All-photonic intercity quantum key distribution. Nat. Commun. 6, 10171 (2015).
Lucamarini, M., Yuan, Z. L., Dynes, J. F. & Shields, A. J. Overcoming the rate-distance limit of quantum key distribution without quantum repeaters. Nature 557, 400–403 (2018).
Lo, H.-K., Curty, M. & Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108, 130503 (2012).
Tamaki, K., Lo, H.-K., Fung, C.-H. F. & Qi, B. Phase encoding schemes for measurement-device-independent quantum key distribution with basis-dependent flaw. Phys. Rev. A 85, 042307 (2012).
Wang, X.-B. Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett. 94, 230503 (2005).
Hwang, W. Y. Quantum key distribution with high loss: toward global secure communication. Phys. Rev. Lett. 91, 057901 (2003).
Lo, H.-K., Ma, X. & Chen, K. Decoy state quantum key distribution. Phys. Rev. Lett. 94, 230504 (2005).
Ma, X., Zeng, P. & Zhou, H. Phase-matching quantum key distribution. Phys. Rev. X 8, 31043 (2018).
Tamaki, K., Lo, H.-K., Wang, W. & Lucamarini, M. Information theoretic security of quantum key distribution overcoming the repeaterless secret key capacity bound. Preprint at http://arxiv.org/abs/1805.05511 (2018).
Wang, X.-B., Yu, Z.-W. & Hu, X.-L. Twin-field quantum key distribution with large misalignment error. Phys. Rev. A 98, 062323 (2018).
Yin, H.-L. & Fu, Y. Measurement-device-independent twin-field quantum key distribution. Sci. Rep. 9, 3045 (2019).
Cui, C. et al. Twin-field quantum key distribution without phase post-selection. Phys. Rev. Applied 11, 034053 (2019).
Curty, M., Azuma, K. & Lo, H.-K. Simple security proof of twin-field type quantum key distribution protocol. Preprint at http://arxiv.org/abs/1807.07667 (2018).
Lin, J. & Lütkenhaus, N. Simple security analysis of phase-matching measurement-device-independent quantum key distribution. Phys. Rev. A 98, 42332 (2018).
Yin, H.-L. & Chen, Z.-B. Twin-field quantum key distribution over 1000 km Fibre. Preprint at http://arxiv.org/abs/1901.05009 (2019).
Shor, P. W. & Preskill, J. Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85, 441–444 (2000).
Koashi, M. Simple security proof of quantum key distribution based on complementarity. New J. Phys. 11, 045018 (2009).
Carter, J. L. & Wegman, M. N. Classes of hash functions. J. Comput. Syst. Sci. 18, 143–154 (1979).
Höffding, W. Probability inequalities for sums of bounded random variables. J. Am. Stat. Assoc. 58, 13–30 (1963).
Hayashi, M. & Tsurumaru, T. Concise and tight security analysis of the Bennett-Brassard 1984 protocol with finite key lengths. New J. Phys. 14, 093014 (2012).
Muller-Quade, J. & Renner, R. Composability in quantum cryptography. New J. Phys. 11, 085006 (2009).
Acknowledgements
We thank Kiyoshi Tamaki and Koji Azuma for valuable discussions. This work was supported by Cross-ministerial Strategic Innovation Promotion Program (SIP) (Council for Science, Technology and Innovation (CSTI)); ImPACT Program (CSTI); CREST (Japan Science and Technology Agency) JPMJCR1671; JSPS KAKENHI Grant Number JP18K13469.
Author information
Authors and Affiliations
Contributions
K.M., T.S., and M.K. contributed to the initial conception of the ideas, to the working out of details, and to the writing and editing of the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Peer review information: Nature Communications thanks Xiongfeng Ma, Akihisa Tomita and other anonymous reviewer(s) for their contribution to the peer review of this work. Peer reviewer reports are available.
Publisher’s note: Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary information
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Maeda, K., Sasaki, T. & Koashi, M. Repeaterless quantum key distribution with efficient finite-key analysis overcoming the rate-distance limit. Nat Commun 10, 3140 (2019). https://doi.org/10.1038/s41467-019-11008-z
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41467-019-11008-z
This article is cited by
-
Measurement device-independent quantum key distribution with vector vortex modes under diverse weather conditions
Scientific Reports (2023)
-
Tight finite-key analysis for mode-pairing quantum key distribution
Communications Physics (2023)
-
Machine learning with neural networks for parameter optimization in twin-field quantum key distribution
Quantum Information Processing (2023)
-
Twin-field quantum key distribution over 830-km fibre
Nature Photonics (2022)
-
Satellite-based phase-matching quantum key distribution
Quantum Information Processing (2022)
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.