Abstract
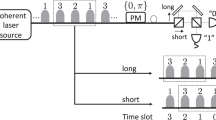
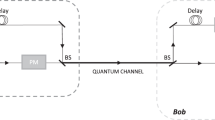
Quantum key distribution (QKD) is a method of realizing private communication securely against an adversary with unlimited power. The QKD protocols proposed and demonstrated over the past 30 years relied on the monitoring of signal disturbance to set an upper limit to the amount of leaked information. Here, we report an experimental realization of the recently proposed round-robin differential-phase-shift protocol. We used a receiver set-up in which photons are randomly routed to one of four interferometers with different delays so that the phase difference is measured uniformly over all pair combinations among five pulses comprising the quantum signal. The amount of leak can be bounded from this randomness alone, and a secure key was extracted even when a finite communication time and the threshold nature of photon detectors were taken into account. This demonstrates the first QKD experiment without signal disturbance monitoring, thus opening up a new direction towards secure communication.
This is a preview of subscription content, access via your institution
Access options
Subscribe to this journal
Receive 12 print issues and online access
$209.00 per year
only $17.42 per issue
Buy this article
- Purchase on Springer Link
- Instant access to full article PDF
Prices may be subject to local taxes which are calculated during checkout




Similar content being viewed by others
References
Gisin, N., Ribordy, G., Tittel, W. & Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 74, 145–195 (2002).
Bennett, C. H. & Brassard, G. in Proceedings of IEEE International Conference on Computers, Systems and Signal Processing 175–179 (IEEE Press, 1984).
Ekert, A. K. Quantum cryptography based on Bell's theorem. Phys. Rev. Lett. 67, 661–663 (1991).
Bennett, C. H. Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68, 3121–3124 (1992).
Huttner, B., Imoto, N., Gisin, N. & Mor, T. Quantum cryptography with coherent states. Phys. Rev. A 51, 1863–1869 (1995).
Jouguet, P., Kunz-Jacques, S., Leverrier, A., Grangier, P. & Diamanti, E. Experimental demonstration of long-distance continuous-variable quantum key distribution. Nature Photon. 14, 378–381 (2013).
Inoue, K., Waks, E. & Yamamoto, Y. Differential phase shift quantum key distribution. Phys. Rev. Lett. 89, 037902 (2002).
Scarani, V., Acin, A., Ribordy, G. & Gisin, N. Quantum cryptography protocols robust against photon number splitting attacks for weak laser pulse implementations. Phys. Rev. Lett. 92, 057901 (2004).
Stucki, D., Brunner, N., Gisin, N., Scarani, V. & Zbinden, H. Fast and simple one-way quantum key distribution. Appl. Phys. Lett. 87, 194108 (2005).
Dixon, A. R., Yuan, Z. L., Dynes, J. F., Sharpe, A. W. & Shields, A. J. Gigahertz decoy quantum key distribution with 1 Mbit/s secure key rate. Opt. Express 16, 18790–18797 (2008).
Zhang, Q. et al. Megabits secure key rate quantum key distribution. New J. Phys. 11, 045010 (2009).
Dixon, A. R., Yuan, Z. L., Dynes, J. F., Sharpe, A. W. & Shields, A. J. Continuous operation of high bit rate quantum key distribution. Appl. Phys. Lett. 96, 161102 (2010).
Tanaka, A. et al. High-speed quantum key distribution system for 1-Mbps real-time key generation. IEEE J. Quantum Electron. 48, 542–550 (2012).
Lucamarini, M. et al. Efficient decoy-state quantum key distribution with quantified security. Opt. Express 21, 24550–24565 (2013).
Gobby, C., Yuan, Z. L. & Shields, A. J. Quantum key distribution over 122 km of standard telecom fiber. Appl. Phys. Lett. 84, 3762–3764 (2004).
Takesue, H. et al. Quantum key distribution over 40 dB channel loss using superconducting single-photon detectors. Nature Photon. 1, 343–348 (2007).
Korzh, B. et al. Provably secure and practical quantum key distribution over 307 km of optical fiber. Nature Photon. 9, 163–168 (2015).
Peev, M. et al. The SECOQC quantum key distribution network in Vienna. New J. Phys. 11, 075001 (2009).
Sasaki, M. et al. Field test of quantum key distribution in the Tokyo QKD network. Opt. Express 19, 10387–10409 (2011).
Scarani, V. et al. The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301–1350 (2009).
Sasaki, T., Yamamoto, Y. & Koashi, M. Practical quantum key distribution protocol without monitoring signal disturbance. Nature 509, 475–478 (2014).
Waks, E., Takesue, H. & Yamamoto, Y. Security of differential-phase-shift quantum key distribution against individual attacks. Phys. Rev. A 73, 012344 (2006).
Wen, K., Tamaki, K. & Yamamoto, Y. Unconditional security of single-photon differential phase shift quantum key distribution. Phys. Rev. Lett. 103, 170503 (2009).
Tamaki, K., Koashi, M. & Kato, G. Unconditional security of coherent-state-based differential phase shift quantum key distribution protocol with block-wise phase randomization. Preprint at http://arxiv.org/abs/1208.1995 (2012).
Honjo, T., Inoue, K. & Takahashi, H. Differential-phase-shift quantum key distribution experiment with a planar light-wave circuit Mach–Zehnder interferometer. Opt. Lett. 29, 2797–2799 (2004).
Honjo, T. & Inoue, K. Differential-phase-shift quantum key distribution with an extended degree of freedom. Opt. Lett. 31, 522–524 (2006).
Kwack, M. J. et al. Compact optical buffer module for intra-packet synchronization based on InP 1×8 switch and silica-based delay line circuit. IEICE Trans. Electron. E96-C, 738–743 (2013).
Najafi, F. et al. On-chip detection of non-classical light by scalable integration of single-photon detectors. Nature Commun. 6, 5873 (2015).
Goh, T. et al. Low-loss and high-extinction ratio silica-based strictly nonblocking 16×16 thermooptic matrix switch. IEEE Photon. Technol. Lett. 10, 810–812 (1998).
Lo, H.-K., Ma, X. & Chen, K. Decoy state quantum key distribution. Phys. Rev. Lett. 94, 230504 (2005).
Yamazaki, H., Yamada, T., Goh, T., Sakamaki, Y. & Kaneko, A. 64QAM modulator with a hybrid configuration of silica PLCs and LiNbO3 phase modulators. IEEE Photon. Technol. Lett. 22, 344–346 (2010).
Gottesman, D., Lo, H.-K., Lütkenhaus, N. & Preskill, J. Security of quantum key distribution with imperfect device. Quant. Inf. Comp. 4, 325–360 (2004).
Acknowledgements
The authors thank Y. Yamamoto, T. Yamada and M. Oguma for discussions. This work was funded in part by the ImPACT Program of the Council for Science, Technology and Innovation (Cabinet Office, Government of Japan) and the Photon Frontier Network Program (MEXT).
Author information
Authors and Affiliations
Contributions
H.T. designed and constructed the experimental set-up and performed the QKD experiments. T.S. and M.K. designed the detailed procedure for secure key generation. H.T., T.S. and K.T. undertook the data analysis. M.K. led the project. All authors discussed the results and wrote the paper.
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing financial interests.
Supplementary information
Supplementary information
Supplementary information (PDF 526 kb)
Rights and permissions
About this article
Cite this article
Takesue, H., Sasaki, T., Tamaki, K. et al. Experimental quantum key distribution without monitoring signal disturbance. Nature Photon 9, 827–831 (2015). https://doi.org/10.1038/nphoton.2015.173
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1038/nphoton.2015.173
This article is cited by
-
Performance analysis of inter-satellite round-robin differential-phase-shift quantum key distribution
Quantum Information Processing (2022)
-
Polarization-insensitive quantum key distribution using planar lightwave circuit chips
Science China Information Sciences (2022)
-
Tight finite-key analysis for quantum key distribution without monitoring signal disturbance
npj Quantum Information (2021)
-
Discrete-phase-randomized twin-field quantum key distribution without phase postselection in the test mode
Quantum Information Processing (2021)
-
A universal simulating framework for quantum key distribution systems
Science China Information Sciences (2020)