Abstract
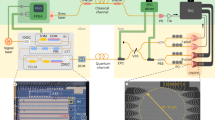
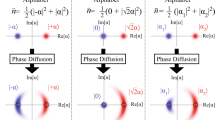
Quantum continuous variables1 are being explored2,3,4,5,6,7,8,9,10,11,12,13,14 as an alternative means to implement quantum key distribution, which is usually based on single photon counting15. The former approach is potentially advantageous because it should enable higher key distribution rates. Here we propose and experimentally demonstrate a quantum key distribution protocol based on the transmission of gaussian-modulated coherent states (consisting of laser pulses containing a few hundred photons) and shot-noise-limited homodyne detection; squeezed or entangled beams are not required13. Complete secret key extraction is achieved using a reverse reconciliation14 technique followed by privacy amplification. The reverse reconciliation technique is in principle secure for any value of the line transmission, against gaussian individual attacks based on entanglement and quantum memories. Our table-top experiment yields a net key transmission rate of about 1.7 megabits per second for a loss-free line, and 75 kilobits per second for a line with losses of 3.1 dB. We anticipate that the scheme should remain effective for lines with higher losses, particularly because the present limitations are essentially technical, so that significant margin for improvement is available on both the hardware and software.
This is a preview of subscription content, access via your institution
Access options
Subscribe to this journal
Receive 51 print issues and online access
$199.00 per year
only $3.90 per issue
Buy this article
- Purchase on Springer Link
- Instant access to full article PDF
Prices may be subject to local taxes which are calculated during checkout




Similar content being viewed by others
References
Braunstein, S. L. & Pati, A. K. Quantum Information Theory with Continuous Variables (Kluwer Academic, Dordrecht, in the press)
Hillery, M. Quantum cryptography with squeezed states. Phys. Rev. A 61, 022309 (2000)
Ralph, T. C. Continuous variable quantum cryptography. Phys. Rev. A 61, 010303(R) (2000)
Ralph, T. C. Security of continuous-variable quantum cryptography. Phys. Rev. A 62, 062306 (2000)
Reid, M. D. Quantum cryptography with a predetermined key, using continuous-variable Einstein-Podolsky-Rosen correlations. Phys. Rev. A 62, 062308 (2000)
Gottesman, D. & Preskill, J. Secure quantum key distribution using squeezed states. Phys. Rev. A 63, 022309 (2001)
Cerf, N. J., Lévy, M. & Van Assche, G. Quantum distribution of Gaussian keys using squeezed states. Phys. Rev. A 63, 052311 (2001)
Van Assche, G., Cardinal, J. & Cerf, N. J. Reconciliation of a quantum-distributed Gaussian key. Preprint cs.CR/0107030 at 〈http://arxiv.org〉 (2001).
Bencheikh, K., Symul, Th., Jankovic, A. & Levenson, J. A. Quantum key distribution with continuous variables. J. Mod. Opt. 48, 1903–1920 (2001)
Cerf, N. J., Iblisdir, S. & Van Assche, G. Cloning and cryptography with quantum continuous variables. Eur. Phys. J. D 18, 211–218 (2002)
Silberhorn, Ch., Korolkova, N. & Leuchs, G. Quantum key distribution with bright entangled beams. Phys. Rev. Lett. 88, 167902 (2002)
Silberhorn, Ch., Ralph, T. C., Lütkenhaus, N. & Leuchs, G. Continuous variable quantum cryptography beating the 3 dB loss limit. Phys. Rev. Lett. 89, 167901 (2002)
Grosshans, F. & Grangier, Ph. Continuous variable quantum cryptography using coherent states. Phys. Rev. Lett. 88, 057902 (2002)
Grosshans, F. & Grangier, Ph. Reverse reconciliation protocols for quantum cryptography with continuous variables. Preprint quant-ph/0204127 at 〈http://arxiv.org〉 (2002).
Gisin, N., Ribordy, G., Tittel, W. & Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 74, 145–195 (2002)
Cerf, N. J., Ipe, A. & Rottenberg, X. Cloning of continuous variables. Phys. Rev. Lett. 85, 1754–1757 (2000)
Cerf, N. J. & Iblisdir, S. Optimal N-to-M cloning of conjugate quantum variables. Phys. Rev. A 62, 040301(R) (2000)
Grosshans, F. & Grangier, Ph. Quantum cloning and teleportation criteria for continuous quantum variables. Phys. Rev. A 64, 010301(R) (2001)
Bennett, C.-H. Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68, 3121–3124 (1992)
Duan, L.-M., Giedke, G., Cirac, J. I. & Zoller, P. Entanglement purification of gaussian continuous variable quantum states. Phys. Rev. Lett. 84, 4002–4005 (2000)
Csiszár, I. & Körner, J. Broadcast channel with confidential messages. IEEE Trans. Inform. Theory 24, 339–348 (1978)
Maurer, U. M. Secret key agreement by public discussion from common information. IEEE Trans. Inform. Theory 39, 733–742 (1993)
Poizat, J.-Ph., Roch, J.-F. & Grangier, Ph. Characterization of quantum non-demolition measurements in optics. Ann. Phys. (Paris) 19, 265–297 (1994)
Grangier, Ph., Levenson, J. A. & Poizat, J.-Ph. Quantum non-demolition measurements in optics. Nature 396, 537–542 (1998)
Shannon, C. E. A mathematical theory of communication. Bell Syst. Tech. J. 27, 623–656 (1948)
Buttler, W. T., Lamoreaux, S. K., Torgerson, J. R., Nickel, G. H. & Peterson, C. G. Fast, efficient error reconciliation for quantum cryptography. Preprint quant-ph/0203096 at 〈http://arxiv.org〉 (2002).
Brassard, G. & Salvail, L. Advances in Cryptology — Eurocrypt '93 Lecture Notes in Computer Science (ed. Helleseth, T.) 411–423 (Springer, New York, 1993)
Nguyen, K. Extension des Protocoles de Réconciliation en Cryptographie Quantique Thesis, Univ. Libre de Bruxelles (2002)
Lo, H.-K. Method for decoupling error correction from privacy amplification. Preprint quant-ph/0201030 at 〈http://arxiv.org〉 (2002)
Bennett, C. H., Brassard, G., Crépeau, C. & Maurer, U. M. Generalized privacy amplification. IEEE Trans. Inform. Theory 41, 1915–1935 (1995)
Acknowledgements
The contributions of J. Gao to the early stages of the experiment, and of K. Nguyen to the software development, are acknowledged. We thank S. Iblisdir for discussions, and Th. Debuisschert for the loan of the 780 nm integrated modulator. This work was supported by the EU programme IST/FET/QIPC (projects “QUICOV” and “EQUIP”), the French programmes ACI Photonique and ASTRE, and by the Belgian programme ARC.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Competing interests
The authors declare that they have no competing financial interests.
Supplementary information
Rights and permissions
About this article
Cite this article
Grosshans, F., Van Assche, G., Wenger, J. et al. Quantum key distribution using gaussian-modulated coherent states. Nature 421, 238–241 (2003). https://doi.org/10.1038/nature01289
Received:
Accepted:
Issue Date:
DOI: https://doi.org/10.1038/nature01289
This article is cited by
-
Withstanding detector attacks in continuous-variable quantum key distribution via mean-restricted unary linear regression
Quantum Information Processing (2024)
-
Gaussian Rényi-2 correlations in a nondegenerate three-level laser
Quantum Information Processing (2024)
-
Quantum secure direct communication with hybrid entanglement
Frontiers of Physics (2024)
-
Practical, high-speed Gaussian coherent state continuous variable quantum key distribution with real-time parameter monitoring, optimised slicing, and post-processed key distillation
Scientific Reports (2023)
-
Recent progress in quantum photonic chips for quantum communication and internet
Light: Science & Applications (2023)
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.