Abstract
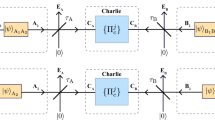
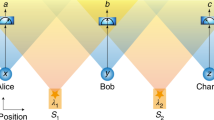
Quantum cryptography achieves a formidable task—the remote distribution of secret keys by exploiting the fundamental laws of physics. Quantum cryptography is now headed towards solving the practical problem of constructing scalable and secure quantum networks. A significant step in this direction has been the introduction of measurement-device independence, where the secret key between two parties is established by the measurement of an untrusted relay. Unfortunately, although qubit-implemented protocols can reach long distances, their key rates are typically very low, unsuitable for the demands of a metropolitan network. Here we show, theoretically and experimentally, that a solution can come from the use of continuous-variable systems. We design a coherent-state network protocol able to achieve remarkably high key rates at metropolitan distances, in fact three orders of magnitude higher than those currently achieved. Our protocol could be employed to build high-rate quantum networks where devices securely connect to nearby access points or proxy servers.
This is a preview of subscription content, access via your institution
Access options
Subscribe to this journal
Receive 12 print issues and online access
$209.00 per year
only $17.42 per issue
Buy this article
- Purchase on Springer Link
- Instant access to full article PDF
Prices may be subject to local taxes which are calculated during checkout





Similar content being viewed by others
References
Gisin, N., Ribordy, G., Tittel, W. & Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 74, 145–196 (2002).
Scarani, V. et al. The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301–1350 (2009).
Wilde, M. M. Quantum Information Theory (Cambridge Univ. Press, 2013).
Weedbrook, C. et al. Gaussian quantum information. Rev. Mod. Phys. 84, 621–669 (2012).
SECOQC (2007); http://www.secoqc.net
Peev, M. et al. The SECOQC quantum key distribution network in Vienna. New J. Phys. 11, 075001 (2009).
Tokyo QKD network (2010); http://www.uqcc.org/QKDnetwork
Sasaki, M. et al. Field test of quantum key distribution in the Tokyo QKD Network. Opt. Express 19, 10387–10409 (2011).
Lydersen, L. et al. Hacking commercial quantum cryptography systems by tailored bright illumination. Nature Photon. 4, 686–689 (2010).
Gerhardt, I. et al. Full-field implementation of a perfect eavesdropper on a quantum cryptography system. Nature Commun. 2, 349 (2011).
Braunstein, S. L. & Pirandola, S. Side-channel-free quantum key distribution. Phys. Rev. Lett. 108, 130502 (2012).
Lo, H.-K., Curty, M. & Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108, 130503 (2012).
Ma, X. & Razavi, M. Alternative schemes for measurement-device-independent quantum key distribution. Phys. Rev. A 86, 062319 (2012).
Wang, X. B. Three-intensity decoy state method for device independent quantum key distribution with basis dependent errors. Phys. Rev. A 87, 012320 (2013).
Branciard, C., Rosset, D., Liang, Y.-C. & Gisin, N. Measurement-device-independent entanglement witnesses for all entangled quantum states. Phys. Rev. Lett. 110, 060405 (2013).
Tomamichel, M., Fehr, S., Kaniewski, J. & Wehner, S. A monogamy-of-entanglement game with applications to device-independent quantum cryptography. New J. Phys. 15, 103002 (2013).
Lim, C. C. W., Portmann, C., Tomamichel, M., Renner, R. & Gisin, N. Device-independent quantum key distribution with local Bell test. Phys. Rev. X 3, 031006 (2013).
Abruzzo, S., Kampermann, H. & Bruß, D. Measurement-device-independent quantum key distribution with quantum memories. Phys. Rev. A 89, 012301 (2014).
Rubenok, A., Slater, J. A., Chan, P., Lucio-Martinez, I. & Tittel, W. Real-world two-photon interference and proof-of-principle quantum key distribution immune to detector attacks. Phys. Rev. Lett. 111, 130501 (2013).
Ferreira da Silva, T. et al. Proof-of-principle demonstration of measurement-device-independent quantum key distribution using polarization qubits. Phys. Rev. A 88, 052303 (2013).
Tang, Y.-L. et al. Measurement-device-independent quantum key distribution over 200 km. Phys. Rev. Lett. 113, 190501 (2013).
Cerf, N. J., Levy, M. & van Assche, G. Quantum distribution of Gaussian keys with squeezed states. Phys. Rev. A 63, 052311 (2001).
Grosshans, F. et al. Quantum key distribution using Gaussian-modulated coherent states. Nature 421, 238–241 (2003).
Lodewyck, J. et al. Quantum key distribution over 25 km with an all-fiber continuous-variable system. Phys. Rev. A 76, 042305 (2007).
Weedbrook, C. et al. Quantum cryptography without switching. Phys. Rev. Lett. 93, 170504 (2004).
Pirandola, S., Mancini, S., Lloyd, S. & Braunstein, S. L. Continuous-variable quantum cryptography with two-way quantum communication. Nature Phys. 4, 726–730 (2008).
Weedbrook, C., Pirandola, S., Lloyd, S. & Ralph, T. C. Quantum cryptography approaching the classical limit. Phys. Rev. Lett. 105, 110501 (2010).
Madsen, L. S., Usenko, V. C., Lassen, M., Filip, R. & Andersen, U. L. Continuous variable quantum key distribution with two-mode squeezed states. Nature Commun. 3, 1083 (2012).
Jouguet, P., Kunz-Jacques, S., Leverrier, A., Grangier, P. & Diamanti, E. Experimental demonstration of long-distance continuous-variable quantum key distribution. Nature Photon. 7, 378–381 (2013).
Saltzer, J. H., Reed, D. P. & Clark, D. D. End-to-end arguments in system design. ACM Trans. Comput. Syst. 2, 277–288 (1984).
Baran, P. On distributed communications networks. IEEE Trans. Commun. Syst. 12, 1–9 (1964).
Chi, Y.-M. et al. A balanced homodyne detector for high-rate Gaussian-modulated coherent-state quantum key distribution. New. J. Phys. 13, 013003 (2011).
Spedalieri, G., Ottaviani, C. & Pirandola, S. Covariance matrices under Bell-like detections. Open Syst. Inf. Dyn. 20, 1350011 (2013).
Renner, R. Symmetry of large physical systems implies independence of subsystems. Nature Phys. 3, 645–649 (2007).
Renner, R. & Cirac, J. I. de Finetti representation theorem for infinite-dimensional quantum systems and applications to quantum cryptography. Phys. Rev. Lett. 102, 110504 (2009).
García-Patrón, R. & Cerf, N. J. Unconditional optimality of Gaussian attacks against continuous-variable quantum key distribution. Phys. Rev. Lett. 97, 190503 (2006).
Jouguet, P., Kunz-Jacques, S. & Leverrier, A. Long-distance continuous-variable quantum key distribution with a Gaussian modulation. Phys. Rev. A 84, 062317 (2011).
Curty, M. et al. Finite-key analysis for measurement-device-independent quantum key distribution. Nature Commun. 5, 3732 (2014).
Leverrier, A. Composable security proof for continuous-variable quantum key distribution with coherent states. Phys. Rev. Lett. 114, 070501 (2015).
Pirandola, S., Braunstein, S. L. & Lloyd, S. Characterization of collective Gaussian attacks and security of coherent-state quantum cryptography. Phys. Rev. Lett. 101, 200504 (2008).
Pirandola, S., Serafini, A. & Lloyd, S. Correlation matrices of two-mode bosonic systems. Phys. Rev. A 79, 052327 (2009).
Pirandola, S. Entanglement reactivation in separable environments. New J. Phys. 15, 113046 (2013).
Pirandola, S. Quantum discord as a resource for quantum cryptography. Sci. Rep. 4, 6956 (2014).
Pirandola, S., García-Patrón, R., Braunstein, S. L. & Lloyd, S. Direct and reverse secret-key capacities of a quantum channel. Phys. Rev. Lett. 102, 050503 (2009).
Takeoka, M., Guha, S. & Wilde, M. M. Fundamental rate-loss tradeoff for optical quantum key distribution. Nature Commun. 5, 5235 (2014).
Acknowledgements
S.P. acknowledges support from the Engineering and Physical Sciences Research Council via the ‘UK Quantum Communications HUB’ (EP/M013472/1) and grants ‘qDATA’ (EP/L011298/1) and ‘HIPERCOM’ (EP/J00796X/1). S.P. also acknowledges the Leverhulme Trust (research fellowship ‘qBIO’). T.G. acknowledges support from the H.C. Ørsted postdoctoral programme. U.L.A. acknowledges the Danish Agency for Science, Technology and Innovation (Sapere Aude project).
Author information
Authors and Affiliations
Contributions
S.P. conceived the theoretical ideas, developed the methodology, derived the main analytical results, and wrote the manuscript and the Supplementary Information. C.O. contributed to the security analysis of the protocol and performed the post-processing of the experimental data. G.S. contributed to theoretical aspects and performed the post-processing of the experimental data. C.S.J., T.G. and U.L.A. designed and performed the experiment, analysed the experimental data, and contributed to writing the description of the experimental set-up. C.W., S.L. and S.L.B. contributed to theoretical aspects and editing of the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing financial interests.
Supplementary information
Supplementary information
Supplementary information (PDF 1129 kb)
Rights and permissions
About this article
Cite this article
Pirandola, S., Ottaviani, C., Spedalieri, G. et al. High-rate measurement-device-independent quantum cryptography. Nature Photon 9, 397–402 (2015). https://doi.org/10.1038/nphoton.2015.83
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1038/nphoton.2015.83
This article is cited by
-
Improving the performance of practical phase-matching quantum key distribution with advantage distillation
Quantum Information Processing (2024)
-
Composable security of CV-MDI-QKD with secret key rate and data processing
Scientific Reports (2023)
-
Surpassing the repeaterless bound with a photon-number encoded measurement-device-independent quantum key distribution protocol
npj Quantum Information (2023)
-
Impact of non-orthogonal measurement in Bell detection on continuous-variable measurement-device-independent quantum key distribution
Quantum Information Processing (2023)
-
Achieving the ultimate end-to-end rates of lossy quantum communication networks
npj Quantum Information (2022)