Abstract
We propose an algorithm for jointly designing two phase-only masks (POMs) that allow for the encryption and noise-free retrieval of triple images. The images required for optical retrieval are first stored in quick-response (QR) codes for noise-free retrieval and flexible readout. Two sparse POMs are respectively calculated from two different images used as references for authentication based on modified Gerchberg-Saxton algorithm (GSA) and pixel extraction and are then used as support constraints in a modified double-phase retrieval algorithm (MPRA), together with the above-mentioned QR codes. No visible information about the target images or the reference images can be obtained from each of these authenticated POMs. This approach allows users to authenticate the two POMs used for image reconstruction without visual observation of the reference images. It also allows user to friendly access and readout with mobile devices.
Similar content being viewed by others
Introduction
When designing diffractive optical elements that allow for the encryption of data for security applications, phase retrieval algorithms (PRAs) such as the Gerchberg-Saxton algorithm (GSA)1, Fienup method2 and their derivative3 can be used. In 1996, Johnson and Brasher encrypted a biometric image in two phase-only masks (POMs) that together reconstruct an image although neither diffractive element by itself gives any hints as to what is in the image4. Under the framework of linear double-random-phase encoding (DRPE) scheme5, many modified algorithms in Fourier domain6,7, Fresnel domain8,9,10,11,12,13,14 and gyrator domain15 have been proposed to generate POMs for data retrieval. Recently, we have also proposed several methods to produce two POMs for single-image retrieval using iterative nonlinear DRPE16,17. Degrees of freedom to manipulate the physical parameters of optical waves can be used in those algorithms where an image can be encoded into two or more POMs4,5,6,7,8,9,10,11,12,13,14,15,16,17. Optical information hiding with POMs has now been one of the most popular application areas for PRAs18,19,20. However, the identifying and the capacity of those computer-generated POMs and the deteriorated original inputs reconstructed optically are still the major concerns in regards to the PRA-based data security protocols.
In this paper, a method for jointly designing two diffractive optical elements having quasi-random phases that allow for the authentication of the elements themselves, the encryption and noise-free retrieval of triple images is proposed based on modified PRAs. No visible information can be obtained from each of the POMs. The target images are inserted into QR codes via hyperlinks that allow for flexible readout with mobile devices. This approach allows users to authenticate the two POMs without visual observation of those images used as references for authentication. The target images can be revealed without visible loss of information due to the property of high damage tolerance capability of QR codes.
Results
Optical image reconstruction scheme
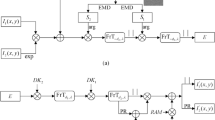
The proposed reconstruction procedure of target images is demonstrates in Fig. 1. When the authenticated POM P1 is illuminated with incident plane wave and then modified by another authenticated POM P2, the approximates of the input QR codes  can be detected in three different object planes. Thus, we have
can be detected in three different object planes. Thus, we have

where the operator | | denotes a modulus operation and FrT[•] represents Fresnel transform17.
Image hiding algorithm with sparsity constrains
The procedure of designing two POMs P1 and P2 that together reconstruct triple images consists of the following steps: 1. Storing three target images (f1, f2, f3) in QR codes (q1, q2, q3). 2. Generating two sparse POMs (p1s, p2s) from two images (g1, g2), which are used as reference for authentication and differ from the target images. 3. Numerical calculation of the two POMs P1 and P2 using the sparse POMs and the QR codes.
To generate two sparse POMs, two secret images g1 and g2 need to be respectively encoded in two different POMs by using a modified Fresnel domain GSA11,12 with the two intensity constraints, i.e., a unit amplitude in the input plane and the image to be encoded in the output plane at a certain distance. Note that the two images used as references are not QR codes used for image encoding. The images g1 and g2 are independently encoded into POMs pm and  in two iterative processes where the propagation distances are d1 and d2. Note that the subscripts m and m′ represent the number of iterations in iterative processes. When pm is illuminated with incident plane wave, an approximation of g1 can be observed in the object plane at distance d1, which can be written by
in two iterative processes where the propagation distances are d1 and d2. Note that the subscripts m and m′ represent the number of iterations in iterative processes. When pm is illuminated with incident plane wave, an approximation of g1 can be observed in the object plane at distance d1, which can be written by

Likewise, we can obtain an approximation of g2 in the output domain at the distance d2, which can be given by  .
.
Sparse representation of the encrypted data can be successfully used for information authentication in some DRPE-based security systems14,21,22,23,24,25. In this step, two sparse phase functions p1s and p2s that used for the calculation of P1 and P2 can be randomly extracted from the outcomes of the iterative processes, i.e., pm,  . Then the following step is numerical calculation of the two authenticated POMs P1 and P2 by using the obtained sparse POMs together with the QR codes. A modified double-phase retrieval algorithm (MDPRA) is proposed to achieve this purpose, where the sparse POMs and the QR codes are used as support constraints. In the MDPRA, let functions
. Then the following step is numerical calculation of the two authenticated POMs P1 and P2 by using the obtained sparse POMs together with the QR codes. A modified double-phase retrieval algorithm (MDPRA) is proposed to achieve this purpose, where the sparse POMs and the QR codes are used as support constraints. In the MDPRA, let functions  and
and  respectively denote the two estimates for P1 and P2, where the superscript n represents the nth iteration of the algorithm. In the initial stage, two random POMs can be used as
respectively denote the two estimates for P1 and P2, where the superscript n represents the nth iteration of the algorithm. In the initial stage, two random POMs can be used as  and
and  , respectively. The QR codes, i.e., q1, q2 and q3, are the three amplitude constraints in the output planes with respect to different distances from the second POM
, respectively. The QR codes, i.e., q1, q2 and q3, are the three amplitude constraints in the output planes with respect to different distances from the second POM  , i.e., z1, z2 and z3.
, i.e., z1, z2 and z3.
Note that the final solutions for P1 and P2 are  and
and  if the iterative stops after N iterations. The obtained two POMs P1 and P2 require authentication before being applied for optical image retrieval. For brevity, only the identifying of P1 is explained. The reconstructed signal from P1 given by
if the iterative stops after N iterations. The obtained two POMs P1 and P2 require authentication before being applied for optical image retrieval. For brevity, only the identifying of P1 is explained. The reconstructed signal from P1 given by  will be compared with the original image g1, by nonlinear correlation in our proposal, where the two parameters d1 and λ can be used as keys for authentication. The authentication method is described as follows25,26:
will be compared with the original image g1, by nonlinear correlation in our proposal, where the two parameters d1 and λ can be used as keys for authentication. The authentication method is described as follows25,26:

where IFT[•] denotes inverse Fourier transform and ω defines the strength of the applied nonlinearity. Function c(μ, v) is given by  , where FT[•] denotes Fourier transform.
, where FT[•] denotes Fourier transform.
Experimental Simulations and performance analyses
Figure 2(a,b) are two 500 × 500 color images, which can be respectively inserted into the QR codes shown in Fig. 2(d,e) via hyperlinks. When a user scans the QR code containing the hyperlink which automatically redirects the user to the image. Figure 2(c) shows input the input text information (NUS stands for National University of Singapore) and its respective QR code is presented in Fig. 2(f). All of the QR Codes have the size of 500 × 500. Due to its fast readability, great storage capacity and high damage tolerance capability, storing data in QR codes during the processes of optical encryption27,28,29 and authentication21,22,23 holds many practical advantages. Once the reconstructed QR codes are scanned by smartphones or tablets, the target images can be successfully revealed.
In our simulations, the pixel dimensions and the illumination wavelength are set as 8μm × 8μm and λ = 633 nm, respectively. Figure 3(a,c) show two 500 × 500 pixels binary images used as references for authentication. The propagation distances are given by d1 = 6 cm and d2 = 8 cm, respectively. Figure 3(b,d) demonstrate two sparse phase functions p1s and p2s that are randomly extracted from the outcomes of the iterative processes, p50 and  , for which both the percentages of the extracted pixels with respect to the pixel size of their originally recovered phase images are 28%.
, for which both the percentages of the extracted pixels with respect to the pixel size of their originally recovered phase images are 28%.
The two sparse POMs are used as two constraints in the proposed MDPRA, together with the three QR codes. The correlation coefficient (CC) is applied to evaluate the similarity between the recovered images  and their original images qi, which is defined by
and their original images qi, which is defined by

where E[] denotes the expected value operator. The CC values get the maximum value of 1 if  are perfectly correlated with qi. Figure 4(a) shows the relation between number of iterations and CC values (between qi and
are perfectly correlated with qi. Figure 4(a) shows the relation between number of iterations and CC values (between qi and  ), where we set the parameters as z0 = 8 cm, z1 = 12 cm, z2 = 20 cm and z3 = 30 cm. It can be seen from Fig. 4(a) that the CC value increases as the number of iterations increases. At the beginning iterations, the three curves shown in Fig. 4(a) overlap almost completely, which implies that the three recovered QR codes have almost identical CC values at the first several iterations. After 100 iterations, the CC values increase very slightly. As expected, two authenticated POMs
), where we set the parameters as z0 = 8 cm, z1 = 12 cm, z2 = 20 cm and z3 = 30 cm. It can be seen from Fig. 4(a) that the CC value increases as the number of iterations increases. At the beginning iterations, the three curves shown in Fig. 4(a) overlap almost completely, which implies that the three recovered QR codes have almost identical CC values at the first several iterations. After 100 iterations, the CC values increase very slightly. As expected, two authenticated POMs  and
and  can be generated after the nth iteration, which require authentication before being used for image reconstruction. Evaluation of the correlation outputs can be implemented by using peak-to-correlation (PCE)23, which is defined as the ratio between the maximum intensity peak value and the total energy of the output plane, usually indicates the sharpness and height of the output correlation peak. Figure 4 shows the two PCE curves obtained by using all correct authentic keys and the nonlinearity strength ω = 0.4. Different from the PCE curve corresponding to P2, the curve with respect to P1 rises rapidly during the first twenty iterations. After that, the PCE values increased slowly and then reaches a plateau (0.2846) at 145 iteration. However, the PCE values obtained with the second POM P2 moves up and down in a limited range. It reaches its maximum (0.0390) at 99 iterations. In order to obtain high-quality correlation peak intensity in authentication, the POMs generated after 99 iterations are chosen as the two POMs used for authentication and image retrieval since the CC values increase very slowly after 100 iterations.
can be generated after the nth iteration, which require authentication before being used for image reconstruction. Evaluation of the correlation outputs can be implemented by using peak-to-correlation (PCE)23, which is defined as the ratio between the maximum intensity peak value and the total energy of the output plane, usually indicates the sharpness and height of the output correlation peak. Figure 4 shows the two PCE curves obtained by using all correct authentic keys and the nonlinearity strength ω = 0.4. Different from the PCE curve corresponding to P2, the curve with respect to P1 rises rapidly during the first twenty iterations. After that, the PCE values increased slowly and then reaches a plateau (0.2846) at 145 iteration. However, the PCE values obtained with the second POM P2 moves up and down in a limited range. It reaches its maximum (0.0390) at 99 iterations. In order to obtain high-quality correlation peak intensity in authentication, the POMs generated after 99 iterations are chosen as the two POMs used for authentication and image retrieval since the CC values increase very slowly after 100 iterations.
The two POMs P1 and P2 designed for triple-image reconstruction and obtained after iteration number of 99 are respectively shown in Fig. 5(a,b). They are required for authentication before being used for image reconstruction. The diffraction patterns of P1 and P2 are shown in Fig. 5(c,d), at the distances of d1 and d2 respectively, from which no information about the two secret binary images can be observed.
When those two visually unrecognizable images [Fig. 5(c,d)] are respectively compared with the references, i.e., Fig. 3(a,c), by nonlinear correlation, sharp correlation peaks could be obtained as shown in Fig. 6(a,b), which implies that the two POMs are successfully authenticated with correct parameters.
The security performance of the two POMs is further investigated. When only one of the POMs is placed in the optical scheme shown in Fig. 1, the diffraction patterns in the three object planes are shown in Fig. 7, from which no valuable information about the QR codes could be observed. Note that Fig. 7 only shows the intensity distributions within the area of 4 mm × 4 mm on the output display. The results shown that neither of the two POMs has the problem of untended information disclosure. The proposed security system can be regard as an information sharing system. Each POM will be sent to different receivers through communication channels. Only when a matched pair of POMs are used for decryption, the primary images can be retrieved by scanning the decrypted QR codes.
Results for the reconstructed images from the two POMs P1 and P2 in different object planes using all the correct physical and geometric parameters are shown in Fig. 8(a–c), which have worse quality than the original images due to the effect of energy loss. The energy of the above three recovered images respectively account for about 85%, 84% and 79% of the total energy in their corresponding object planes. Smartphone was used to display the decrypted images by scanning the reconstructed QR codes. As demonstrated in Fig. 8(d–f), the two target color images and the text information can be retrieved without visible loss of information.
Discussions
We developed an algorithm for jointly designing two POMs that allow for the encryption and noise-free retrieval of triple images. Compared with previous works, the proposed algorithm based on sparsity constraints and QR codes has the following features:
-
This approach allows users to authenticate the two POMs without visual observation of those images used as references for authentication. Since a huge number of differently encoded POMs can be sent out through communication channels14, the identifying and matching of the POMs in a simple and direct manner can help increase efficiency. The MPRA with sparsity constraints may expect to be used in the computation of digital holograms and meta-holograms30,31,32 for image display and information authentication.
-
There is no problem of information disclosure in the proposed method. No information can be visually observed from the two POMs and their respective diffraction patterns. Our method can also be used for encryption of three-dimensional objects.
-
It allows user to friendly access and readout with mobile devices. The target images can be revealed without visible loss of information due to the property of high damage tolerance capability of QR codes. Optically secured information retrieval can be realized when the two designed POMs manufactured by a number of techniques including embossing on plastic films and encoding on photopolymer are placed in the proposed scheme shown in Fig. 1.
Methods
Double-phase retrieval algorithm with sparsity constraints
Let functions  and
and  respectively denote the two solutions for P1 and P2, where the superscript n represents the nth iteration of the algorithm. In the initial stage, two random POMs can be used as
respectively denote the two solutions for P1 and P2, where the superscript n represents the nth iteration of the algorithm. In the initial stage, two random POMs can be used as  and
and  , respectively. The QR codes, i.e., q1, q2 and q3, are the three amplitude constraints in the output planes with respect to different distances from the second POM
, respectively. The QR codes, i.e., q1, q2 and q3, are the three amplitude constraints in the output planes with respect to different distances from the second POM  , i.e., z1, z2 and z3. The process proceeds as follows:
, i.e., z1, z2 and z3. The process proceeds as follows:
(i) The first POM  illuminated with incident plane wave is first Fresnel-transformed at the propagation distance z0. The resultant wave function can be written as
illuminated with incident plane wave is first Fresnel-transformed at the propagation distance z0. The resultant wave function can be written as

which is then multiplied by the second POM  and propagates forward to the output plane through distances zi (i = 1, 2, 3) to obtain new wave functions
and propagates forward to the output plane through distances zi (i = 1, 2, 3) to obtain new wave functions

where the coordinates are omitted for simplicity.
(ii) Replace amplitude parts of the diffraction space wave functions  with amplitude constraints qi. Then the modified functions in the three output planes simultaneously transform back to the plane where the second POM
with amplitude constraints qi. Then the modified functions in the three output planes simultaneously transform back to the plane where the second POM  locates to get a new wave function
locates to get a new wave function  .
.

where IFrT[•] represent inverse Fresnel transform and PR[•] denotes phase reservation, retaining the phase of a complex function but truncating its amplitude part.
(iii) Update the two input POMs  and
and  with
with  and
and  . First, we obtain a POM function
. First, we obtain a POM function  and then update the input POM
and then update the input POM  with
with  using
using  , which can be written as
, which can be written as


where the symbol ⊕ denotes a particular way of data embedding. For clarity, the calculation of  described by Eq. (9) is explained. We first extract the non-zero pixels of POM p1s as the data background for POM
described by Eq. (9) is explained. We first extract the non-zero pixels of POM p1s as the data background for POM  and then embed the pixel values of
and then embed the pixel values of  into
into  pixel by pixel but keep the background unchanged.
pixel by pixel but keep the background unchanged.
To generate another POM used for next iteration, we first compute a POM function  by using
by using  and then obtain POM
and then obtain POM  by
by

where the superscript * denotes conjugation.
(iv) Repeat steps (i)–(iii) until the preset threshold value is satisfied. Suppose the iteration process stop at the Nth iteration. The convergence of the algorithm is demonstrated by the relation between the CC values [between qi and their approximates  obtained by substituting the two POMs computed with Eqs. (9) and (10) into Eq. (1)] and the iteration numbers.
obtained by substituting the two POMs computed with Eqs. (9) and (10) into Eq. (1)] and the iteration numbers.
To sum up, a flowchart of the iterative phase retrieval algorithm is depicted in Fig. 9. So far, we have obtained the two POMs P1 and P2, which require authentication before being applied for optical image retrieval and can be respectively represented by function  and
and  . In general, the amplitude parts of function
. In general, the amplitude parts of function  would be closer to the constraints qi with the increasing of iterations until stagnation. After N iterations, the estimates of qi are denoted by
would be closer to the constraints qi with the increasing of iterations until stagnation. After N iterations, the estimates of qi are denoted by  . From Eqs. (1), (5) and (6), we can readily obtain
. From Eqs. (1), (5) and (6), we can readily obtain  , which implies that the finally recovered images
, which implies that the finally recovered images  could be expected to be closer to their original images qi by increasing the number of iterations before reaching plateau values. It should be pointed out that the MDPRA is designed under the framework of nonlinear double random phase encoding. Different from previously proposed methods of single image encoding16,17, here we encode three QR codes into two POMs in Fresnel domain. Two sparse POMs calculated from two reference images for authentication are used as constraints in the iteration process.
could be expected to be closer to their original images qi by increasing the number of iterations before reaching plateau values. It should be pointed out that the MDPRA is designed under the framework of nonlinear double random phase encoding. Different from previously proposed methods of single image encoding16,17, here we encode three QR codes into two POMs in Fresnel domain. Two sparse POMs calculated from two reference images for authentication are used as constraints in the iteration process.
Additional Information
How to cite this article: Wang, X. et al. Optically secured information retrieval using two authenticated phase-only masks. Sci. Rep. 5, 15668; doi: 10.1038/srep15668 (2015).
References
Gerchberg, R. W. & Saxton, W. O. A practical algorithm for the determination of phase from image and diffraction plane pictures. Optik 35, 237–246 (1972).
Fienup, J. R. Phase retrieval algorithms: a comparison, Appl. Opt. 21, 2758–2769 (1982).
Faulkner, H. M. L. & Rodenburg, J. M. Movable aperture lensless transmission microscopy: a novel phase retrieval algorithm. Phys. Rev. Lett. 93, 023903 (2004).
Johnson, E. G. & Brasher, J. D. Phase encryption of biometrics in diffractive optical elements. Opt. Lett. 21, 1271–1273 (1996).
Refregier, P. & Javidi, B. Optical image encryption based on input plane and Fourier plane random encoding. Opt. Lett. 20, 767–769 (1995).
Situ, G & Zhang, J. A cascaded iterative Fourier transform algorithm for optical security applications. Optik 114, 473–477 (2003).
Alfalou, A. & Mansour, A. Double random phase encryption scheme to multiplex and simultaneous encode multiple images. Appl. Opt. 48, 5933–5947 (2009).
Situ, G & Zhang, J. A lensless optical security system based on computer-generated phase only masks. Opt. Commun. 232, 115–122 (2004).
Shi, Y., Situ, G. & Zhang, J. Multiple-image hiding in the Fresnel domain. Opt. Lett. 32, 1914–1916 (2007).
Shi, Y., Situ, G. & Zhang, J. Multiple-image hiding by information prechoosing. Opt. Lett. 33, 542–544 (2008).
Hwang, H., Chang, H. & Lie, W. Fast double-phase retrieval in Fresnel domain using modified Gerchberg-Saxton algorithm for lensless optical security systems. Opt. Express 17, 13700–13710 (2009).
Huang, J., Hwang. H., Chen, C. & Chen, C. Optical multiple-image encryption based on phase encoding algorithm in the Fresnel transform domain. Opt & Laser Technol 44, 2238–2244 (2012).
Rajput, S. K. & Nishchal, N. K. Fresnel domain nonlinear optical image encryption scheme based on Gerchberg–Saxton phase-retrieval algorithm. Appl. Opt. 53, 418–425 (2014).
Chen, W., Wang, X. & Chen, X. Security-enhanced phase encryption assisted by nonlinear optical correlation via sparse phase. J. Opt. 17, 035702 (2015).
Liu, Z., Xu, L., Gou, Q., Lin, C. & Liu, S. Image watermarking by using phase retrieval algorithm in gyrator transform domain. Opt. Commun. 283, 4923 4927
Wang, X., Chen, W. & Chen, X. Fractional Fourier domain optical image hiding using phase retrieval algorithm based on iterative nonlinear double random phase encoding. Opt. Express 22, 22981–22995 (2014).
Wang, X., Chen, W. & Chen, X. Optical image hiding using double-phase retrieval algorithm based on nonlinear cryptosystem under vortex beam illumination. J. Opt. 17, 035704 (2015).
Alfalou, A. & Brosseau, C. Optical image compression and encryption methods. Adv. Opt. Photon. 1, 589–636 (2009).
Chen, W., Javidi, B. & Chen, X. Advances in optical security systems. Adv. Opt. Photon. 6, 120–155 (2014).
Fienup, J. R. Phase retrieval algorithms: a personal tour [Invited]. Appl. Opt. 52, 45–56 (2013).
Markman, A., Javidi, B. & Tehranipoor, M. Photon-counting security tagging and verification using optically encoded QR codes. IEEE Photon. J. 6, 6800609 (2014).
Markman, A., Wang, J. & Javidi, B. Three-dimensional integral imaging displays using a quick-response encoded elemental image array. Optica 1, 332–335 (2014).
Wang, X., Chen, W. & Chen, X. Optical information authentication using compressed double-random-phase-encoded images and quick-response codes. Opt. Express 23, 6239–6253 (2015).
Wang, X., Chen, W. & Chen, X. Optical Encryption and Authentication Based on Phase Retrieval and Sparse Constraints. IEEE Photon. J. 7, 7800310 (2015).
Pérez-Cabré, E., Cho, M. & Javidi, B. Information authentication using photon-counting double-random-phase encrypted images. Opt. Lett. 36, 22–24 (2011).
Sadjadi, F. & Javidi, B. Physics of Automatic Target Recognition (Springer, New York, 2007).
Barrera, J. F., Mira, A. & Torroba, R. Optical encryption and QR codes: Secure and noise-free information retrieval. Opt. Express 21 5373–5378 (2013).
Barrera, J. F., Mira, A. & Torroba, R. Experimental scrambling and noise reduction applied to the optical encryption of QR codes. Opt. Express 22, 20268–20277 (2014).
Barrera, J. F., Mira, A. & Torroba, R. Experimental QR code optical encryption: noise-free data recovering. Opt. Lett. 39, 3074–3077 (2014).
Yifat, Y. J. et al. Highly efficient and broadband wide-angle Holography Using Patch-Dipole Nano-antenna Reflectarrays, Nano Lett. 14, 2485–2490 (2014).
Huang, L. et al. Three-dimensional optical holography using a plasmonic metasurface, Nat. Commu 4, 2808 (2013).
Huang, Y. D. et al. Aluminum plasmonic multicolor meta-hologram, Nano Lett. 15, 3122–3127 (2015).
Acknowledgements
Acknowledgements This work was supported by the National Natural Science Foundation of China (Grant Nos. 61575178 and 61205006), Singapore MINDEF-NUS Joint Applied R&D Cooperation Programme (JPP) Project: MINDEF/NUS/JPP/14/01/02.
Author information
Authors and Affiliations
Contributions
W.X.G. proposed the method and wrote the main manuscript text. W.X.G. and M.S.T. made the numerical simulations. C.W. and C.X.D. helped revise the manuscript and got involved in the discussions.
Ethics declarations
Competing interests
The authors declare no competing financial interests.
Rights and permissions
This work is licensed under a Creative Commons Attribution 4.0 International License. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in the credit line; if the material is not included under the Creative Commons license, users will need to obtain permission from the license holder to reproduce the material. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/
About this article
Cite this article
Wang, X., Chen, W., Mei, S. et al. Optically secured information retrieval using two authenticated phase-only masks. Sci Rep 5, 15668 (2015). https://doi.org/10.1038/srep15668
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/srep15668
This article is cited by
-
A novel approach for audible acoustic quick response codes
Scientific Reports (2022)
-
Design, fabrication and characterization of Computer Generated Holograms for anti-counterfeiting applications using OAM beams as light decoders
Scientific Reports (2017)
-
Enhancing security of incoherent optical cryptosystem by a simple position-multiplexing technique and ultra-broadband illumination
Scientific Reports (2017)
-
Ciphertext-only attack on optical cryptosystem with spatially incoherent illumination: from the view of imaging through scattering medium
Scientific Reports (2017)
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.





 .
.




